Centos6.5 下Openldap管理各系统账号
一、系统环境
Centos6.5
Ldapserver:172.16.1.183
Ldapclient:172.16.1.162
二、openldap安装及配置
2.1 openldap服务端安装及配置(172.16.1.183)
2.1.1 关闭防火墙及selinux
[root@ldap-test ~]# service iptables stop iptables:将链设置为政策 ACCEPT:filter [确定] iptables:清除防火墙规则: [确定] iptables:正在卸载模块: [确定][root@ldap-test ~]# sed -i 's/SELINUX=.*/SELINUX=disabled/g' /etc/sysconfig/selinux #关闭selinux [root@ldap-test ~]# reboot
2.1.2 yum直接安装Openldap服务(需要访问internet)
[root@ldap-test ~]# yum install openldap-* -y [root@ldap-test ~]# rpm -qa |grep openldap openldap-servers-sql-2.4.40-16.el6.x86_64 openldap-clients-2.4.40-16.el6.x86_64 openldap-2.4.40-16.el6.x86_64 openldap-servers-2.4.40-16.el6.x86_64 openldap-devel-2.4.40-16.el6.x86_64
2.1.3 Openldap服务端配置
1).拷贝LDAP配置文件到LDAP目录
[root@ldap-test ~]# cd /etc/openldap/ [root@ldap-test openldap]# ls certs check_password.conf ldap.conf schema slapd.d [root@ldap-test openldap]# cp /usr/share/openldap-servers/slapd.conf.obsolete slapd.conf2).创建LDAP管理员密码
[root@ldap-test openldap]# slappasswd New password: Re-enter new password: {SSHA}vzvKx0hppVuP+vHMvYesr49Evw5qY+zp输入密码后,密码会被加密成SSHA模式,这串密码要记住,一会需要用到。
3).配置sldap.conf文件
原配置文件内容:
[root@ldap-test openldap]# vim slapd.conf database monitor access to * by dn.exact="gidNumber=0+uidNumber=0,cn=peercred,cn=external,cn=auth" read by dn.exact="cn=Manager,dc=my-domain,dc=com" read by * none database bdb suffix "dc=my-domain,dc=com" checkpoint 1024 15 rootdn "cn=Manager,dc=my-domain,dc=com" # rootpw {crypt}ijFYNcSNctBYg 改成:
database monitor access to * by dn.exact="gidNumber=0+uidNumber=0,cn=peercred,cn=external,cn=auth" read by dn.exact="cn=root,dc=xinguang,dc=com" read by * none database bdb #ldap存储数据的地方 suffix "dc=xinguang,dc=com" #根域名,这个名字可以随意取 checkpoint 1024 15 rootdn "cn=root,dc=xinguang,dc=com" #管理员的账号 rootpw {SSHA}Kiy2vxzxxOdPq8bexNZOBcVICuVTgbof #管理员密码 4).拷贝DB_CONFIG文件
[root@ldap-test openldap]# cp /usr/share/openldap-servers/DB_CONFIG.example /var/lib/ldap/DB_CONFIG5).清除/etc/openldap/slapd.d下安装时默认的配置文件。
[root@ldap-test slapd.d]# rm -rf /etc/openldap/slapd.d/* 6).启动slapd服务,赋予权限并生成新的配置文件。
[root@ldap-test slapd.d]# service slapd restart 停止 slapd: [失败] ls: 无法访问/etc/openldap/slapd.d//cn=config/olcDatabase*.ldif: 没有那个文件或目录 正在启动 slapd: [确定] [root@ldap-test slapd.d]# chkconfig slapd on [root@ldap-test slapd.d]# chown -R ldap:ldap /var/lib/ldap/ [root@ldap-test slapd.d]# chown -R ldap:ldap /etc/openldap/ [root@ldap-test openldap]# slaptest -f /etc/openldap/slapd.conf -F /etc/openldap/slapd.d/ config file testing succeede
7).重新赋权并重启服务。
[root@ldap-test openldap]# ll slapd.d/ #由于是root用户生成的配置文件,所以还需要重新赋权。 总用量 8 drwxr-x---. 3 root root 4096 4月 20 09:06 cn=config -rw-------. 1 root root 1259 4月 20 09:06 cn=config.ldif [root@ldap-test openldap]# chown -R ldap.ldap /etc/openldap/slapd.d/* [root@ldap-test openldap]# service slapd restart 停止 slapd: [确定] 正在启动 slapd: [确定] 7).安装配置phpldapadmin管理界面。
[root@ldap-test openldap]# rpm -ivh http://mirrors.ukfast.co.uk/sites/dl.fedoraproject.org/pub/epel/6/x86_64/epel-release-6-8.noarch.rpm Retrieving http://mirrors.ukfast.co.uk/sites/dl.fedoraproject.org/pub/epel/6/x86_64/epel-release-6-8.noarch.rpm warning: /var/tmp/rpm-tmp.W8rwVa: Header V3 RSA/SHA256 Signature, key ID 0608b895: NOKEY Preparing... ########################################### [100%] 1:epel-release ########################################### [100%] [root@ldap-test openldap]# yum install -y phpldapadmin
[root@ldap-test openldap]# vim /etc/httpd/conf.d/phpldapadmin.conf
Alias /phpldapadmin /usr/share/phpldapadmin/htdocs
Alias /ldapadmin /usr/share/phpldapadmin/htdocs
Order Deny,Allow
# Deny from all
Allow from 127.0.0.1
Allow from ::1
Allow from all #加下这个表示都可以访问管理页面
[root@ldap-test openldap]# vim /etc/phpldapadmin/config.php
$servers->setValue('server','visible',true);
$servers->setValue('login','timeout',30);
$servers->setValue('server','branch_rename',false);
$servers->setValue('server','custom_sys_attrs',array('passwordExpirationTime','passwordAllowChangeTime'));
$servers->setValue('server','custom_attrs',array('nsRoleDN','nsRole','nsAccountLock'));
$servers->setValue('server','force_may',array('uidNumber','gidNumber','sambaSID'));
*/
$servers->setValue('login','attr','dn'); #在结尾处加入
?>
[root@ldap-test openldap]# service httpd start
[root@ldap-test openldap]# chkconfig httpd on
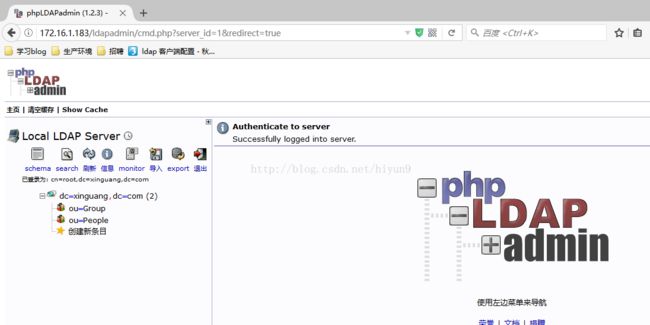
8).接下来我们输入http://172.16.1.183/ldapadmin/来访问管理页面:
9).建立ldap系统相关数据
创建不同组织:
[root@ldap-test data]# pwd
/etc/openldap/data
[root@ldap-test data]# vim o.ldif #在根目录下建立不同组织
dn: o=tuchao,dc=xinguang,dc=com
objectclass: top
objectclass: dcobject
objectclass: organization
dc: xinguang
o: tuchao
description: 兔巢
street: 浙江省杭州近江大厦
#telephone: 13131311313
dn: o=yougo,dc=xinguang,dc=com
objectclass: top
objectclass: dcobject
objectclass: organization
dc: xinguang
o: yougo
description: 游购
street: 浙江省杭州近江大厦
#telephone: 13131311313
[root@ldap-test data]# ldapadd -x -D "cn=root,dc=xinguang,dc=com" -W -f o.ldif #将建好的数据导入ldap
Enter LDAP Password:
adding new entry "o=tuchao,dc=xinguang,dc=com"
adding new entry "o=yougo,dc=xinguang,dc=com"
继续创建数据,待数据全部创建完成之后,再展示最后的目录结构。
不同组织下创建组及用户目录:
[root@ldap-test data]# vim group.ldif #在不同组织下建立组目录
dn: ou=Group,o=tuchao,dc=xinguang,dc=com
ou: Group
objectClass: top
objectClass: organizationalUnit
dn: ou=Group,o=yougo,dc=xinguang,dc=com
ou: Group
objectClass: top
objectClass: organizationalUnit
[root@ldap-test data]# ldapadd -x -D "cn=root,dc=xinguang,dc=com" -W -f group.ldif
Enter LDAP Password:
adding new entry "ou=Group,o=tuchao,dc=xinguang,dc=com"
adding new entry "ou=Group,o=yougo,dc=xinguang,dc=com"
[root@ldap-test data]# vim people.ldif #在不同组织下建立用户目录
dn: ou=People,o=tuchao,dc=xinguang,dc=com
ou: People
objectClass: top
objectClass: organizationalUnit
dn: ou=People,o=yougo,dc=xinguang,dc=com
ou: People
objectClass: top
objectClass: organizationalUnit
[root@ldap-test data]# ldapadd -x -D "cn=root,dc=xinguang,dc=com" -W -f people.ldif
Enter LDAP Password:
adding new entry "ou=People,o=tuchao,dc=xinguang,dc=com"
adding new entry "ou=People,o=yougo,dc=xinguang,dc=com"
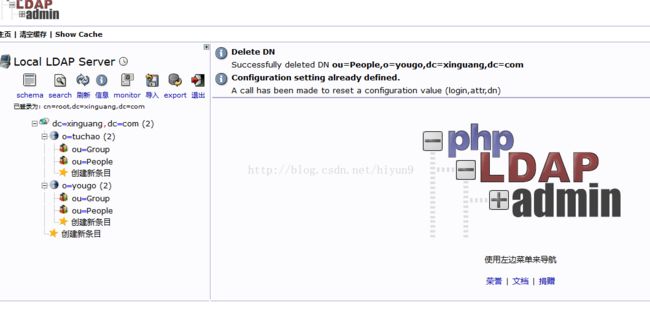
看下最后的目录组织结构:
后面可以自行创建用户组及用户。
2.2 openldap客户端安装及配置(172.16.1.162)
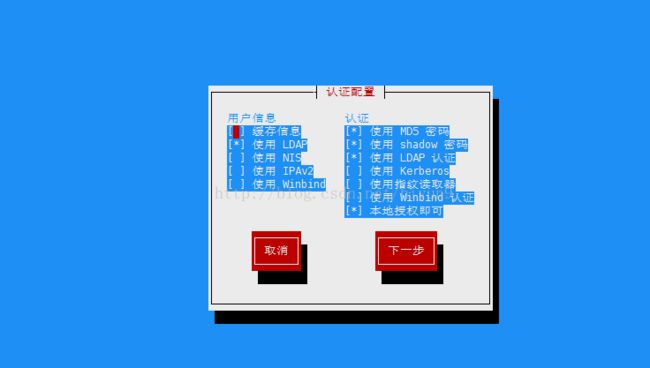
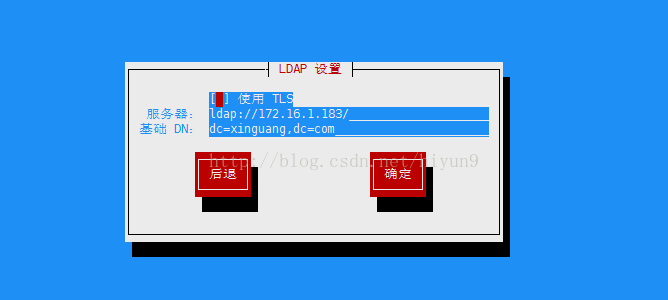
[root@xg-docker-4 ~]# yum install setuptool -y
[root@xg-docker-4 ~]# setup
根据下图配置即可:
[root@xg-docker-4 ~]# getent passwd
nscd:x:28:28:NSCD Daemon:/:/sbin/nologin
nslcd:x:65:55:LDAP Client User:/:/sbin/nologin
petest1:x:10000003:500:petest1:/home/petest1:/bin/bash #这是ldap中的用户
[root@xg-docker-4 ~]# ldapsearch -D cn=root,dc=xinguang,dc=com -W -b dc=xinguang,dc=com
Enter LDAP Password:
# extended LDIF
#
# LDAPv3
# base with scope subtree
# filter: (objectclass=*)
# requesting: ALL
#
# xinguang.com
dn: dc=xinguang,dc=com
dc: xinguang
objectClass: top
objectClass: domain
# tuchao, xinguang.com
dn: o=tuchao,dc=xinguang,dc=com
objectClass: top
objectClass: dcObject
objectClass: organization
o: tuchao
description:: 5YWU5bei
street:: 5rWZ5rGf55yB5p2t5bee6L+R5rGf5aSn5Y6m
telephoneNumber: 15833333333
dc: 10
# yougo, xinguang.com
dn: o=yougo,dc=xinguang,dc=com
objectClass: top
objectClass: dcObject
objectClass: organization
o: yougo
description:: 5ri46LSt
street:: 5rWZ5rGf55yB5p2t5bee6L+R5rGf5aSn5Y6m
dc: 11
telephoneNumber: 15833333334
# Group, tuchao, xinguang.com
dn: ou=Group,o=tuchao,dc=xinguang,dc=com
ou: Group
objectClass: top
objectClass: organizationalUnit
# Group, yougo, xinguang.com
dn: ou=Group,o=yougo,dc=xinguang,dc=com
ou: Group
objectClass: top
objectClass: organizationalUnit
# People, tuchao, xinguang.com
dn: ou=People,o=tuchao,dc=xinguang,dc=com
ou: People
objectClass: top
objectClass: organizationalUnit
# People, yougo, xinguang.com
dn: ou=People,o=yougo,dc=xinguang,dc=com
ou: People
objectClass: top
objectClass: organizationalUnit
# petest1, People, yougo, xinguang.com
dn: uid=petest1,ou=People,o=yougo,dc=xinguang,dc=com
objectClass: posixAccount
objectClass: top
objectClass: inetOrgPerson
objectClass: shadowAccount
givenName: petest1
sn: petest1
displayName: petest1
uid: petest1
homeDirectory: /home/petest1
loginShell: /bin/bash
physicalDeliveryOfficeName: 1001
o: yougo.xinguang.com
title: IT
cn: petest1
uidNumber: 10000003
gidNumber: 500
userPassword:: e1NTSEF9S2l5MnZ4enh4T2RQcThiZXhOWk9CY1ZJQ3VWVGdib2Y=
mail:: cGV0ZXN0MUB4aW5ndWFuZ25ldC5jb20g
# search result
search: 2
result: 0 Success
# numResponses: 9
# numEntries: 8