安全框架shiro(二):shiro进阶
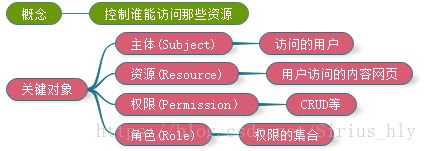
一.shiro授权
1.1.概念
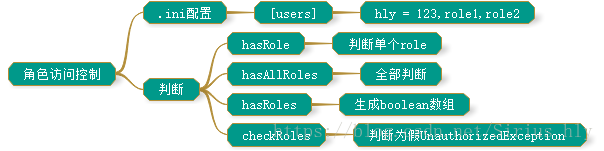
1.2.角色访问控制
控制那些角色可以进行访问,.ini文件配置如下:
[users]
hly = 123,role1,role2
abc = 123,role1用户hly拥有角色role1,role2,所验证的代码如下
@Test
public void testHasRole(){
iniConfig("classpath:shiro/authorization/shiro-role.ini","hly","123");
Assert.assertTrue(subject().hasRole("role1"));
Assert.assertTrue(subject().hasAllRoles(Arrays.asList("role1", "role2")));
boolean [] result = subject().hasRoles(Arrays.asList("role1","role2","role3"));
Assert.assertEquals(true,result[0]);
Assert.assertEquals(true,result[1]);
Assert.assertEquals(false,result[2]);
}根据hasRole,hasAllRoles等方法可以判断用户是否拥有相关的权限。
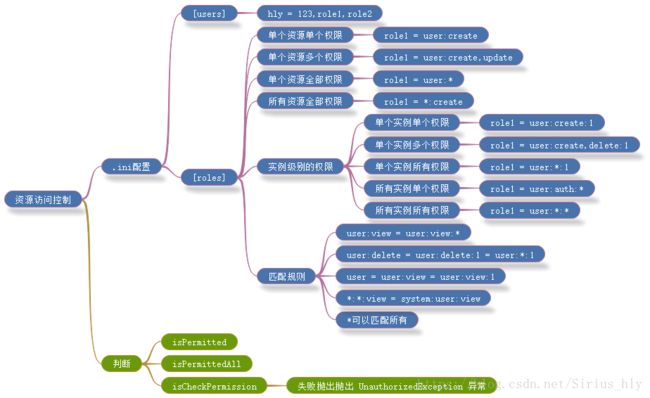
1.3.资源访问控制
控制用户可以进行的相关操作,如CRUD等.
.ini文件配置主体和角色所拥有的权限,如下,具体配置方法如思维导图所示.
[users]
hly = 123,role1,role2
abc = 123,role1
[roles]
role1 = user:create,user:update
role2 = user:create,user:delete接下来,我们可以用isPermitted,isPermittedAll等方法对主体所拥有的权限进行测试,如下:
@Test
public void testPermission(){
iniConfig("classpath:shiro/authorization/shiro-permission.ini","hly","123");
Assert.assertTrue(subject().isPermitted("user:create"));
Assert.assertTrue(subject().isPermittedAll("user:create","user:delete"));
Assert.assertFalse(subject().isPermitted("user:view"));
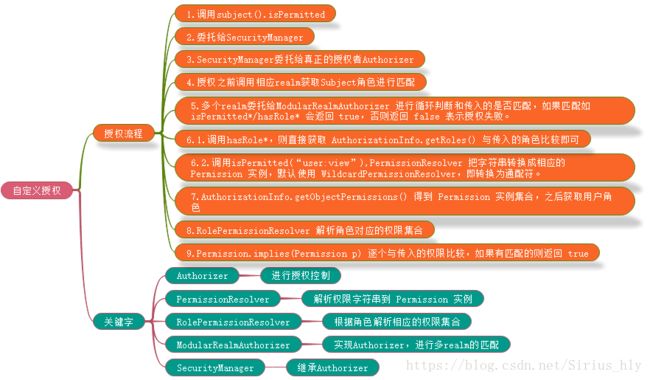
}1.4.自定义授权规则
自定义授权.ini文件配置
[main]
#自定义authorizer
authorizer=org.apache.shiro.authz.ModularRealmAuthorizer
#自定义permissionResolver
#permissionResolver=org.apache.shiro.authz.permission.WildcardPermissionResolver
permissionResolver=com.hly.shiro.authorization.BitAndWildPermissionResolver
#解析权限字符串到 Permission 实例
authorizer.permissionResolver=$permissionResolver
#自定义rolePermissionResolver
rolePermissionResolver=com.hly.shiro.authorization.MyRolePermissionResolver
#根据角色解析相应的权限集合
authorizer.rolePermissionResolver=$rolePermissionResolver
#进行授权控制
securityManager.authorizer=$authorizer
#自定义realm 一定要放在securityManager.authorizer赋值之后(因为调用setRealms会将realms设置给authorizer,并给各个Realm设置permissionResolver和rolePermissionResolver)
realm=com.hly.shiro.realm.MyRealm
securityManager.realms=$realm1.解析权限字符串到 Permission 实例,得到相应配置规则的字符串。
permissionResolver=com.hly.shiro.authorization.BitAndWildPermissionResolver
#解析权限字符串到 Permission 实例
authorizer.permissionResolver=$permissionResolver如配置中的BitAndWildPermissionResolver,BitPermission为自定义匹配方法,WildcardPermission为默认通配符匹配。
public class BitAndWildPermissionResolver implements PermissionResolver {
@Override
//“+” 开头来解析权限字符串为 BitPermission 或 WildcardPermission。
public Permission resolvePermission(String permissionString) {
if(permissionString.startsWith("+")){
return new BitPermission(permissionString);
}
return new WildcardPermission(permissionString);
}
}2.根据角色解析相应的权限集合,判断角色是否拥有相应的权限,在自定义realm中,如果添加了role1角色,则可匹配memu:*。
#自定义rolePermissionResolver
rolePermissionResolver=com.hly.shiro.authorization.MyRolePermissionResolver
#根据角色解析相应的权限集合
authorizer.rolePermissionResolver=$rolePermissionResolver
public class MyRolePermissionResolver implements RolePermissionResolver {
@Override
public Collection resolvePermissionsInRole(String roleString) {
if("role1".equals(roleString)){
return Arrays.asList((Permission) new WildcardPermission("menu:*"));
}
return null;
}
} 3.自定义realm,AuthorizationInfo进行授权和添加角色,AuthenticationInfo进行身份验证.
package com.hly.shiro.realm;
import com.hly.shiro.authorization.BitPermission;
import org.apache.shiro.authc.*;
import org.apache.shiro.authz.AuthorizationInfo;
import org.apache.shiro.authz.SimpleAuthorizationInfo;
import org.apache.shiro.authz.permission.WildcardPermission;
import org.apache.shiro.realm.AuthorizingRealm;
import org.apache.shiro.subject.PrincipalCollection;
/**
* @author :hly
* @github :github.com/SiriusHly
* @blog :blog.csdn.net/Sirius_hly
* @date :2018/9/3
*/
/**
* 自定义Realm
*/
public class MyRealm extends AuthorizingRealm {
@Override
//表示根据用户身份获取授权信息
protected AuthorizationInfo doGetAuthorizationInfo(PrincipalCollection principalCollection) {
SimpleAuthorizationInfo authorizationInfo = new SimpleAuthorizationInfo();
//添加角色
authorizationInfo.addRole("role1");
authorizationInfo.addRole("role2");
//添加权限
authorizationInfo.addObjectPermission(new BitPermission("+user1+10+1+1"));
authorizationInfo.addObjectPermission(new BitPermission("+user1+4"));
authorizationInfo.addObjectPermission(new BitPermission("+user1+2"));
authorizationInfo.addObjectPermission(new BitPermission("+user1+8"));
authorizationInfo.addObjectPermission(new WildcardPermission("user1:*"));
authorizationInfo.addStringPermission("+user2+10");
authorizationInfo.addStringPermission("user2:*");
return authorizationInfo;
}
@Override
//表示获取身份验证信息
protected AuthenticationInfo doGetAuthenticationInfo(AuthenticationToken authenticationToken) throws AuthenticationException {
String username = (String)authenticationToken.getPrincipal();//用户名
String password = new String((char[])authenticationToken.getCredentials());//密码
if(!"hly".equals(username)) {
throw new UnknownAccountException(); //如果用户名错误
}
if(!"123".equals(password)) {
throw new IncorrectCredentialsException(); //如果密码错误
}
//如果身份认证验证成功,返回一个AuthenticationInfo实现;
return new SimpleAuthenticationInfo(username, password, getName());
}
}
4.进行权限测试
@Test
public void testAuthorizerTest(){
iniConfig("classpath:shiro/authorization/shiro-authorizer.ini","hly","123");
//判断拥有权限
Assert.assertTrue(subject().hasRole("role1"));
Assert.assertTrue(subject().hasRole("role2"));
Assert.assertTrue(subject().isPermitted("user1:delete"));
Assert.assertTrue(subject().isPermitted("user2:view"));
Assert.assertTrue(subject().isPermitted("+user1+2"));
Assert.assertTrue(subject().isPermitted("+user1+8"));
Assert.assertTrue(subject().isPermitted("+user2+10"));
Assert.assertTrue(subject().isPermitted("+user1+10+1+1"));
Assert.assertTrue(subject().isPermitted("+user1+4"));
Assert.assertTrue(subject().isPermitted("menu:view"));
}
以上完整代码可在笔者github中找到,参考shiro授权。