aliyun搭建ngrok服务器
ngrok的作用和原理可以网上自行搜索查阅。
环境如下:
服务器 aliyun centos7.2
域名 ithinkcry.cn
安装步骤如下:
目录
Go
Git
OpenSSL
编译ngrok
服务端:
客户端:
nginx
启动
服务端
客户端
错误
Go
安装go环境 yum install go
查看go安装情况
[root@jiba ~]# go version
go version go1.11.5 linux/amd64
官方要求go的版本必须是1.1+
Git
下载ngrok源码到服务器上(确保服务器上已经安装git)
[root@jiba zzj]# cd ngrokcode/
[root@jiba ngrokcode]# git clone https://github.com/inconshreveable/ngrok.git
Cloning into 'ngrok'...
remote: Enumerating objects: 2732, done.
remote: Total 2732 (delta 0), reused 0 (delta 0), pack-reused 2732
Receiving objects: 100% (2732/2732), 665.38 KiB | 124.00 KiB/s, done.
Resolving deltas: 100% (1298/1298), done.
OpenSSL
使用openssl 生成ngrok的证书
我的域名是ithinck.cn,我是用的ngrok地址是ngrok.ithinkcry.cn,所以此处domain的地址是ngrok.ithinkcry.cn
[root@jiba ngrok]# pwd
/home/zzj/ngrokcode/ngrok
[root@jiba ngrok]# openssl
OpenSSL> genrsa -out base.key 2048
Generating RSA private key, 2048 bit long modulus
................................................................+++
...........................................+++
e is 65537 (0x10001)
OpenSSL> req -new -x509 -nodes -key base.key -days 10000 -subj "/CN=ngrok.ithinkcry.cn" -out base.pem
OpenSSL> genrsa -out server.key 2048
Generating RSA private key, 2048 bit long modulus
...........................................................................................+++
........................+++
e is 65537 (0x10001)
OpenSSL> req -new -key server.key -subj "/CN=ngrok.ithinkcry.cn" -out server.csr
OpenSSL> x509 -req -in server.csr -CA base.pem -CAkey base.key -CAcreateserial -days 10000 -out server.crt
Signature ok
subject=/CN=ngrok.ithinkcry.cn
Getting CA Private Key
OpenSSL> exit
查看生成的证书文件 base.key base.pem base.srl server.crt server.csr server.key
[root@jiba ngrok]# pwd
/home/zzj/ngrokcode/ngrok
[root@jiba ngrok]# ll
total 56
drwxr-xr-x 4 root root 4096 Sep 16 10:46 assets
-rw-r--r-- 1 root root 1679 Sep 16 10:58 base.key
-rw-r--r-- 1 root root 1119 Sep 16 11:03 base.pem
-rw-r--r-- 1 root root 17 Sep 16 11:04 base.srl
drwxr-xr-x 2 root root 4096 Sep 16 10:46 contrib
-rw-r--r-- 1 root root 199 Sep 16 10:46 CONTRIBUTORS
drwxr-xr-x 2 root root 4096 Sep 16 10:46 docs
-rw-r--r-- 1 root root 551 Sep 16 10:46 LICENSE
-rw-r--r-- 1 root root 1433 Sep 16 10:46 Makefile
-rw-r--r-- 1 root root 2725 Sep 16 10:46 README.md
-rw-r--r-- 1 root root 1001 Sep 16 11:04 server.crt
-rw-r--r-- 1 root root 903 Sep 16 11:04 server.csr
-rw-r--r-- 1 root root 1679 Sep 16 11:03 server.key
drwxr-xr-x 3 root root 4096 Sep 16 10:46 src
复制生成的证书到assets文件夹下
ngrok通过bindata将ngrok源码目录下的assets目录(资源文件)打包到可执行文件(ngrokd和ngrok)中 去,assets/client/tls和assets/server/tls下分别存放着用于ngrok和ngrokd的默认证书文件,我们需要将它们替换成我们自己生成的:(因此这一步务必放在编译可执行文件之前)
[root@jiba ngrok]# pwd
/home/zzj/ngrokcode/ngrok
[root@jiba ngrok]# cp base.pem assets/client/tls/ngrokroot.crt
cp: overwrite ‘assets/client/tls/ngrokroot.crt’? y
[root@jiba ngrok]# cp server.crt assets/server/tls/snakeoil.crt
cp: overwrite ‘assets/server/tls/snakeoil.crt’? y
[root@jiba ngrok]# cp server.key assets/server/tls/snakeoil.key
cp: overwrite ‘assets/server/tls/snakeoil.key’? y
编译ngrok
服务端:
在ngrok目录下执行如下命令,编译ngrokd:
[root@jiba ngrok]# pwd
/home/zzj/ngrokcode/ngrok
[root@jiba ngrok]# make release-server
GOOS="" GOARCH="" go get github.com/jteeuwen/go-bindata/go-bindata
bin/go-bindata -nomemcopy -pkg=assets -tags=release \
-debug=false \
-o=src/ngrok/client/assets/assets_release.go \
assets/client/...
bin/go-bindata -nomemcopy -pkg=assets -tags=release \
-debug=false \
-o=src/ngrok/server/assets/assets_release.go \
assets/server/...
go get -tags 'release' -d -v ngrok/...
github.com/inconshreveable/mousetrap (download)
github.com/rcrowley/go-metrics (download)
Fetching https://gopkg.in/inconshreveable/go-update.v0?go-get=1
Parsing meta tags from https://gopkg.in/inconshreveable/go-update.v0?go-get=1 (status code 200)
get "gopkg.in/inconshreveable/go-update.v0": found meta tag get.metaImport{Prefix:"gopkg.in/inconshreveable/go-update.v0", VCS:"git", RepoRoot:"https://gopkg.in/inconshreveable/go-update.v0"} at https://gopkg.in/inconshreveable/go-update.v0?go-get=1
gopkg.in/inconshreveable/go-update.v0 (download)
github.com/kardianos/osext (download)
github.com/kr/binarydist (download)
Fetching https://gopkg.in/inconshreveable/go-update.v0/check?go-get=1
Parsing meta tags from https://gopkg.in/inconshreveable/go-update.v0/check?go-get=1 (status code 200)
get "gopkg.in/inconshreveable/go-update.v0/check": found meta tag get.metaImport{Prefix:"gopkg.in/inconshreveable/go-update.v0", VCS:"git", RepoRoot:"https://gopkg.in/inconshreveable/go-update.v0"} at https://gopkg.in/inconshreveable/go-update.v0/check?go-get=1
get "gopkg.in/inconshreveable/go-update.v0/check": verifying non-authoritative meta tag
Fetching https://gopkg.in/inconshreveable/go-update.v0?go-get=1
Parsing meta tags from https://gopkg.in/inconshreveable/go-update.v0?go-get=1 (status code 200)
Fetching https://gopkg.in/yaml.v1?go-get=1
Parsing meta tags from https://gopkg.in/yaml.v1?go-get=1 (status code 200)
get "gopkg.in/yaml.v1": found meta tag get.metaImport{Prefix:"gopkg.in/yaml.v1", VCS:"git", RepoRoot:"https://gopkg.in/yaml.v1"} at https://gopkg.in/yaml.v1?go-get=1
gopkg.in/yaml.v1 (download)
github.com/inconshreveable/go-vhost (download)
github.com/alecthomas/log4go (download)
github.com/nsf/termbox-go (download)
github.com/mattn/go-runewidth (download)
github.com/gorilla/websocket (download)
go install -tags 'release' ngrok/main/ngrokd
编译完毕后可以看到生成了bin文件夹,里面有服务端的执行文件
[root@jiba ngrok]# pwd
/home/zzj/ngrokcode/ngrok
[root@jiba ngrok]# ll
total 60
drwxr-xr-x 4 root root 4096 Sep 16 10:46 assets
-rw-r--r-- 1 root root 1679 Sep 16 10:58 base.key
-rw-r--r-- 1 root root 1119 Sep 16 11:03 base.pem
-rw-r--r-- 1 root root 17 Sep 16 11:04 base.srl
drwxr-xr-x 2 root root 4096 Sep 16 11:29 bin
drwxr-xr-x 2 root root 4096 Sep 16 10:46 contrib
-rw-r--r-- 1 root root 199 Sep 16 10:46 CONTRIBUTORS
drwxr-xr-x 2 root root 4096 Sep 16 10:46 docs
-rw-r--r-- 1 root root 551 Sep 16 10:46 LICENSE
-rw-r--r-- 1 root root 1433 Sep 16 10:46 Makefile
-rw-r--r-- 1 root root 2725 Sep 16 10:46 README.md
-rw-r--r-- 1 root root 1001 Sep 16 11:04 server.crt
-rw-r--r-- 1 root root 903 Sep 16 11:04 server.csr
-rw-r--r-- 1 root root 1679 Sep 16 11:03 server.key
drwxr-xr-x 5 root root 4096 Sep 16 11:28 src
[root@jiba ngrok]# cd bin/
[root@jiba bin]# ll
total 11800
-rwxr-xr-x 1 root root 2772750 Sep 16 11:28 go-bindata
-rwxr-xr-x 1 root root 9308318 Sep 16 11:29 ngrokd
[root@jiba bin]#
客户端:
3个选项
GOOS=linux GOARCH=amd64 make release-client #Linux 64位环境
GOOS=windows GOARCH=amd64 make release-client #windows 64位环境
GOOS=linux GOARCH=arm make release-client #Linux arm环境
我生成的是windows64位的客户端
[root@jiba ngrok]# pwd
/home/zzj/ngrokcode/ngrok
[root@jiba ngrok]# GOOS=windows GOARCH=amd64 make release-client
bin/go-bindata -nomemcopy -pkg=assets -tags=release \
-debug=false \
-o=src/ngrok/client/assets/assets_release.go \
assets/client/...
bin/go-bindata -nomemcopy -pkg=assets -tags=release \
-debug=false \
-o=src/ngrok/server/assets/assets_release.go \
assets/server/...
go get -tags 'release' -d -v ngrok/...
go install -tags 'release' ngrok/main/ngrok
[root@jiba ngrok]#
可以看到在bin文件下多了一个windows_amd64文件夹,里面有windows客户端的启动文件
[root@jiba ngrok]# ll
total 60
drwxr-xr-x 4 root root 4096 Sep 16 10:46 assets
-rw-r--r-- 1 root root 1679 Sep 16 10:58 base.key
-rw-r--r-- 1 root root 1119 Sep 16 11:03 base.pem
-rw-r--r-- 1 root root 17 Sep 16 11:04 base.srl
drwxr-xr-x 3 root root 4096 Sep 16 11:34 bin
drwxr-xr-x 2 root root 4096 Sep 16 10:46 contrib
-rw-r--r-- 1 root root 199 Sep 16 10:46 CONTRIBUTORS
drwxr-xr-x 2 root root 4096 Sep 16 10:46 docs
-rw-r--r-- 1 root root 551 Sep 16 10:46 LICENSE
-rw-r--r-- 1 root root 1433 Sep 16 10:46 Makefile
-rw-r--r-- 1 root root 2725 Sep 16 10:46 README.md
-rw-r--r-- 1 root root 1001 Sep 16 11:04 server.crt
-rw-r--r-- 1 root root 903 Sep 16 11:04 server.csr
-rw-r--r-- 1 root root 1679 Sep 16 11:03 server.key
drwxr-xr-x 5 root root 4096 Sep 16 11:28 src
[root@jiba ngrok]# cd bin/
[root@jiba bin]# ll
total 11804
-rwxr-xr-x 1 root root 2772750 Sep 16 11:28 go-bindata
-rwxr-xr-x 1 root root 9308318 Sep 16 11:29 ngrokd
drwxr-xr-x 2 root root 4096 Sep 16 11:34 windows_amd64
[root@jiba bin]# cd windows_amd64/
[root@jiba windows_amd64]# ll
total 11248
-rwxr-xr-x 1 root root 11515904 Sep 16 11:34 ngrok.exe
[root@jiba windows_amd64]#
nginx
nginx.conf配置
server {
listen 80;
server_name *.ngrok.ithinkcry.cn;
location / {
proxy_pass http://172.26.88.76:18015;
proxy_set_header Host $host:18015;
proxy_set_header X-Real-IP $remote_addr;
proxy_redirect off;
client_max_body_size 10m;
client_body_buffer_size 128k;
proxy_connect_timeout 90;
proxy_read_timeout 90;
proxy_buffer_size 4k;
proxy_buffers 6 128k;
proxy_busy_buffers_size 256k;
proxy_temp_file_write_size 256k;
}
location ~ .*\.(gif|jpg|png|bmp|swf)$ {
proxy_pass http://172.26.88.76:18015;
proxy_set_header Host $host:18015;
expires 30d;
}
location ~ .*\.(js|css)?$ {
proxy_pass http://172.26.88.76:18015;
proxy_set_header Host $host:18015;
expires 1d;
}
}
服务器端口配置
服务器开启端口
firewall-cmd --zone=public --add-port=4443/tcp --permanent
firewall-cmd --reload阿里云安全组
域名解析配置
*.ngrok.ithinkcry.cn
ngrok.ithinkcry.cn
启动
服务端
[root@jiba bin]# ll
total 11804
-rwxr-xr-x 1 root root 2772750 Sep 16 11:28 go-bindata
-rwxr-xr-x 1 root root 9308318 Sep 16 11:29 ngrokd
drwxr-xr-x 2 root root 4096 Sep 16 11:34 windows_amd64
手动启动
[root@jiba bin]# ./ngrokd -domain="ngrok.ithinkcry.cn" -httpAddr=":18015" -httpsAddr=":18014" > ngrok.log &
编写脚本:
[root@jiba ngrok]# touch start.sh
[root@jiba ngrok]# vim start.sh
填写脚本内容
/home/zzj/ngrokcode/ngrok/bin/ngrokd -tlsKey=/home/zzj/ngrokcode/ngrok/assets/server/tls/snakeoil.key -tlsCrt=/home/zzj/ngrokcode/ngrok/assets/server/tls/snakeoil.crt -domain="ngrok.ithinkcry.cn" -httpAddr=":18015" -httpsAddr=":18014" -tunnelAddr=":4443" > /home/zzj/ngrokcode/ngrok/bin/ngrok.log &
保存后,更改权限
[root@jiba ngrok]# chmod a+x start.sh
启动
[root@jiba bin]# ./start.sh客户端
客户端是windows,把之前生成的ngrok.exe复制到windows上
[root@jiba windows_amd64]# pwd
/home/zzj/ngrokcode/ngrok/bin/windows_amd64
[root@jiba windows_amd64]# ls
ngrok.exe配置启动文件,或者直接手工启动:
文件ngrok.cfg 内容,端口就是-tunnelAddr 的端口,也是阿里云服务器安全组开启的端口
server_addr: "ngrok.ithinkcry.cn:4443"
trust_host_root_certs: false
启动文件,可以自动化设置的bat文件,内容:
@echo OFF
color 0a
Title Ngrok启动工具
Mode con cols=109 lines=30
:START
Echo.
echo.
echo.
:TUNNEL
Echo 输入需要启动的域名前缀,如“aaa” ,即分配给你的穿透域名为:“aaa.ngrok.ithinkcry.cn”
ECHO.
ECHO.
ECHO.
set /p clientid= 请输入前缀:
echo.
set /p port= 请输入端口:
echo.
ngrok -config=ngrok.cfg -subdomain %clientid% %port%
PAUSE
goto TUNNEL
输入三级域名test 和对应的端口号8080
启动成功
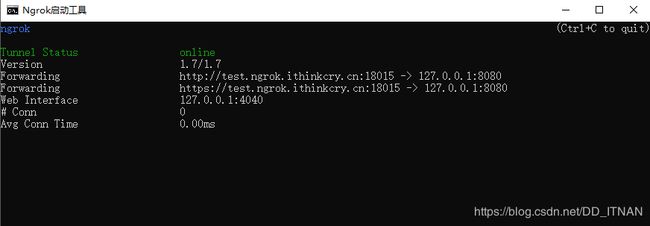
或者手动启动:把本机的8080端口映射到服务器ngrok上面的test.ngrok.ithinkcry.cn去
ngrok -config=ngrok.cfg -subdomain test 8080
此时访问test.ngrok.ithinkcry.cn 就相当于访问本机的服务localhost:8080
错误
期间如果遇到tls: bad certificate 这种错误,可能是在设置openssl的时候出错了,或者服务端的地址和客户端ngrok.cfg中的地址不一样。
我的解决办法是,重新设置openssl,重新生成一遍,使用新的服务端和新的客户端,就可以了。
参考资料:
https://www.pocketdigi.com/20161011/1490.html
https://www.jianshu.com/p/cd937631a88b
https://my.oschina.net/djsoft/blog/1786635
https://aotu.io/notes/2016/02/19/ngrok/index.html
https://blog.csdn.net/ZHJ123CSDN/article/details/87886424
https://blog.csdn.net/u010444106/article/details/80457985



