DM×××
一.典型×××的缺点... 2
二.DM×××概述... 3
三.DM×××实验... 4
1.实验目的... 4
2.实验拓扑... 4
3.实验步骤... 5
3.1.基本网络配置... 5
3.2.mGRE与NHRP配置... 7
3.3.启用IGP协议... 9
3.4.IPSec配置... 13
3.5.验证... 14
四.实验总结... 26
一.典型×××的缺点
根据前面的几个IPSec ×××经典实验、GRE oover IPSec ×××实验我们知道,对于典型的站点到站点的×××存在高扩展性问题。对于下图的拓扑,典型×××的使用会出现问题。
图1:IPSec ×××的星形拓扑
星形拓扑会出现以下问题:
1.中心站点和分支站点之间配置繁杂
按照典型×××的配置,两个对等体之间的连接需在两个设备上都配置。对等体少的话还好,但是对于分支站点众多的拓扑图来说(如上图),×××的配置需要很多。HUB到Spoken1之间要配置一遍,HUB到Spoken2之间要配置一遍。这样就导致了每个站点要配置两遍。而现在的图是只有三个站点之间互联。如果是10个,20个,甚至100个呢(对于大型的公司来说不夸张,因为它们的分公司遍布全国甚至全世界)?每个站点岂不是要配置N遍。这样的结果肯定是不行的。
2.中心站点流量紧张
典型×××中,分支站点都要与中心站点建立对等体关系。分支站点之间的流量也是先到达中心站点解密再加密发送到目的分支站点来实现通信。这样就加重了中心站点的流量处理负担,如果分支站点众多,势必给中心站点带来“灭顶之灾”。
3.分支站点之间流量延迟大
分支站点之间的流量都通过中心站点实现转发。当两个分支站点需要通信时,流量先到达中心站点,在通过中心站点转发到目的分支站点,这样造成了两个分支站点之间的流量处理存在较大的延迟。就好比说:中国的两个宝马分公司之间需要通信,流量要先转发到德国再回到中国,这样岂不是多此一举。
基于此,引入了DM×××,解决了典型×××的高扩展性问题。
二.DM×××概述
DM×××(Dynamic Multipoint×××,动态多点×××)。再典型×××的基础上加以扩展,完美解决了上面提到的种种问题。提到DM×××,我们需要介绍它的有点和几大组成协议。
优点:
1.简单的星形拓扑配置,提供虚拟网状连通性;
2.分支站点支持动态IP地址;
3.增加新的分支站点,无需更改中心站点配置;
4.分支站点间流量,通过动态产生的站点间隧道进行封装。
组成协议:
1.动态多点GRE(MultipointGRE,mGRE)
mGRE是一种特殊的GRE技术。与多点帧中继技术类似,是典型的NBMA网络。设计中,一般所有站点的mGRE隧道接口都处于同一个网段,所有站点间都可以互通,这也就体现了一个虚拟网状连通性。
2.NHRP(Next Hop Resolution Protocol,下一跳解析协议)
并不是配置了mGRE就可以实现所有站点间的通信了。再tunnel网络中,站点间是通过tunnel地址找到对方的,仅仅这样的话,内部网络之间是不能实现通信的,因为站点之间的实际通信时通过公网地址。如同以太网中,主机之间的通信是通过物理地址(MAC来通信的),IP地址只不过是一个逻辑地址。要实现两者的通信,必须知道对方逻辑地址对应的物理地址、mGRRE网络中,NHRP协议就是利用这个原理来解决通信问题。管理员要映射逻辑地址到物理地址。mGRE隧道的地址就是逻辑地址,而物理地址就是站点所用的公网地址。
每一个分支站点需要通过本协议映射中心站点的地址,所以中心站点需要使用固定地址。映射之后就可以与中心站点实现通信。并且,分支站点映射中心站点地址的同时,也向中心站点注册了自己的映射关系(自己的隧道地址所对应的公网IP)。
当两个分支站点需要实现通信时。其中一个会向中心站点询问另一个的站点地址对应关系,然后两个中心站点之间协商建立安全隧道实现通信,不用再通过中心站点,节省了中心站点的流量,同时两个站点之间的回话延迟减小了。
注:分支站点向中心站点注册自己的地址之后,分支站点与中心站点之间的SA是永久建立的,除非故障,否则不会中断。分支站点之间的SA是临时建立的,需要通信时才建立。
3.IPSec技术
本实验中,IPSec技术只是起到保护隧道流量的作用,与GRE over IPSec技术中的原理一样。所以配置大体相同。
三.DM×××实验
1.实验目的
理解DM×××的原理;
理解DM×××的特点及优势;
掌握DM×××的配置;
学会灵活使用DM×××。
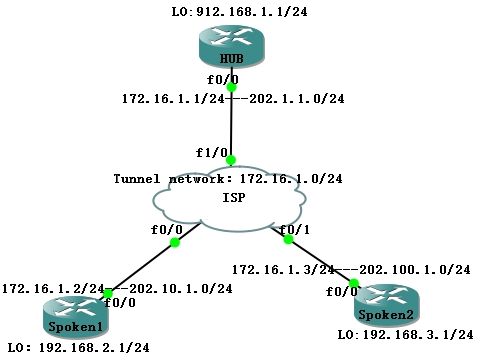
2.实验拓扑
说明:如图,三个站点之间的×××互联,HUB为中心站点(模拟总公司),Spoken1和Spoken2为两个分支站点(模拟两个分公司)。三个站点之间通过GRE Tunnel(本实验用的是mGRE)来连接,tunnel网段为172.16.1.0/24。使用IPSec来保护Tunnel的数据。ISP路由器上只有自己连接的各网段的路由,没有站点内部网络的路由。三个路由器上设置loopback0模拟内部网络。最终的结果是实现三个站点内部网络之间的流量互通,但是Spoken1和Spoken2之间的流量不通过中心站点,而是通过它们自己建立的SA实现通信。
3.实验步骤
3.1.基本网络配置
本部分配置的主要任务是为后续的技术做准备,搭建好几本的网络拓扑环境
HUB配置
HUB#config t HUB(config)#inter loo0 HUB(config-if)#ip add 192.168.1.1 255.255.255.0 HUB(config-if)#no shut HUB(config)#inter fa0/0 HUB(config-if)#ip add 202.1.1.1 255.255.255.0 HUB(config-if)#ip route 0.0.0.0 0.0.0.0 202.1.1.254 |
Spoken1配置
Spoken1#config t Enter configuration commands, one per line. End with CNTL/Z. Spoken1(config)#inter loo0 Spoken1(config-if)#ip add 192.168.2.1 255.255.255.0 Spoken1(config-if)#no shut Spoken1(config-if)#inter fa0/0 Spoken1(config-if)#ip add 202.10.1.1 255.255.255.0 Spoken1(config-if)#no shut Spoken1(config-if)#ip route 0.0.0.0 0.0.0.0 202.10.1.254 |
Spoken2配置
Spoken2#config t Enter configuration commands, one per line. End with CNTL/Z. Spoken2(config-if)#ip add 192.168.3.1 255.255.255.0 Spoken2(config-if)#no shut Spoken2(config-if)#inter fa0/0 Spoken2(config-if)#ip add 202.100.1.1 255.255.255.0 Spoken2(config-if)#no shut Spoken2(config-if)#ip route 0.0.0.0 0.0.0.0 202.100.1.254 |
ISP配置
ISP#conf t Enter configuration commands, one per line. End with CNTL/Z. ISP(config)#inter fa0/0 ISP(config-if)#ip add 202.10.1.254 255.255.255.0 ISP(config-if)#no shut ISP(config-if)#inter fa1/0 ISP(config-if)#ip add 202.1.1.254 255.255.255.0 ISP(config-if)#no shut ISP(config-if)#inter fa0/1 ISP(config-if)#ip add 202.100.1.254 255.255.255.0 ISP(config-if)#no shut |
验证连通性
HUB#ping 202.10.1.1 //HUB向Spoken1发ping包 Type escape sequence to abort. Sending 5, 100-byte ICMP Echos to 202.10.1.1, timeout is 2 seconds: .!!!! Success rate is 80 percent (4/5), round-trip min/avg/max = 48/86/168 ms HUB#ping 202.100.1.1 //HUB向Spoken2发ping包 Type escape sequence to abort. Sending 5, 100-byte ICMP Echos to 202.100.1.1, timeout is 2 seconds: .!!!! Success rate is 80 percent (4/5), round-trip min/avg/max = 40/79/128 ms |
各站点之间连通性正常
3.2.mGRE与NHRP配置
说明:mGRE和NHRP的配置最好是从HUB开始。因为Spoken要向HUB注册地址的映射关系。
HUB配置
--------------------------------------------------mGRE配置------------------------------------- HUB(config)#inter tunnel 1 <创建隧道> HUB(config-if)#ip add 172.16.1.1 255.255.255.0 <>为隧道设置地址> HUB(config-if)#tunnel source fa0/0 <隧道源设置为自己的公网地址> HUB(config-if)#tunnel key 123456 <设置隧道秘钥。相当于为NHRP设置一个管理范围,具有一样秘钥的才能加入进来向服务端注册> --------------------------------------------------NHRP配置--------------------------------------- HUB(config-if)#ip nhrp network-id 10 <激活NHRP,ID为10,所有站点的ID建议相同> HUB(config-if)#ip nhrp authentication cisco <为NHRP配置认证,认证密码:cisco> HUB(config-if)#ip nhrp map multicast dynamic <动态接收NHRP组播映射> |
Spoken1配置
--------------------------------------------------mGRE配置------------------------------------- Spoken1(config)#inter tunnel 1 Spoken1(config-if)#ip add 172.16.1.2 255.255.255.0 Spoken1(config-if)#tunnel mode gre multipoint Spoken1(config-if)#tunnel source fa0/0 Spoken1(config-if)#tunnel key 123456 --------------------------------------------------NHRP配置--------------------------------------- Spoken1(config-if)#ip nhrp network-id 10 Spoken1(config-if)#ip nhrp authentication cisco Spoken1(config-if)#ip nhrp map 172.16.1.1 202.1.1.1 <手动配置NHRP映射,将中心站点的隧道地址映射为公网地址。有了此映射,分支站点才能访问中心站点> Spoken1(config-if)#ip nhrp map multicast 202.1.1.1 Spoken1(config-if)#ip nhrp nhs 172.16.1.1 |
Spoken2配置
--------------------------------------------------mGRE配置------------------------------------- Spoken2(config)#inter tunnel 1 Spoken2(config-if)#ip add 172.16.1.3 255.255.255.0 Spoken2(config-if)#tunnel mode gre multipoint Spoken2(config-if)#tunnel source fa0/0 Spoken2(config-if)#tunnel key 123456 --------------------------------------------------NHRP配置--------------------------------------- Spoken2(config-if)#ip nhrp network-id 10 Spoken2(config-if)#ip nhrp authentication cisco Spoken2(config-if)#ip nhrp map 172.16.1.1 202.1.1.1 Spoken2(config-if)#ip nhrp map multicast 202.1.1.1 Spoken2(config-if)#ip nhrp nhs 172.16.1.1 |
设置完成后查看nhrp的注册
HUB#sho ip nhrp brief Target Via NBMA Mode Intfc Claimed 172.16.1.2/32 172.16.1.2 202.10.1.1 dynamic Tu1 < > 172.16.1.3/32 172.16.1.3 202.100.1.1 dynamic Tu1 < > //HUB路由器上通过NHRP协议动态注册了两个分支站点的信息 HUB#show ip nhrp 172.16.1.2/32 via 172.16.1.2 Tunnel1 created 00:41:06, expire 01:58:52 Type: dynamic, Flags: unique registered NBMA address: 202.10.1.1 172.16.1.3/32 via 172.16.1.3 Tunnel1 created 00:41:06, expire 01:58:52 Type: dynamic, Flags: unique registered NBMA address: 202.100.1.1
Spoken1#sho ip nhrp brief Target Via NBMA Mode Intfc Claimed 172.16.1.1/32 172.16.1.1 202.1.1.1 static Tu1 < > Spoken1#sho ip nhrp 172.16.1.1/32 via 172.16.1.1 Tunnel1 created 00:42:22, never expire Type: static, Flags: used NBMA address: 202.1.1.1
Spoken2#sho ip nhrp bri Target Via NBMA Mode Intfc Claimed 172.16.1.1/32 172.16.1.1 202.1.1.1 static Tu1 < > Spoken2#sho ip nhrp 172.16.1.1/32 via 172.16.1.1 Tunnel1 created 00:42:33, never expire Type: static, Flags: used NBMA address: 202.1.1.1 //分支站点只有中心站点的信息,而且是通过手动映射的。 |
注:NHRP配置完成之后。HUB维护着一张Spoken地址注册表。当spoken之间需要通信时,一端要通过NHRP协议向HUB复制注册表,从而得知目的地址。这样spoken之间就可以自行协商建立×××,不用通过HUB站点来转发。
3.3.启用IGP协议
说明:本实验可以使用静态路由协议,页可以使用动态路由协议。使用路由协议的目的是让每个站点都学习到其他站点的身后网络路由。
但,动态路由协议多用组播传输路由更新。而mGRE是NBMA网络,不支持组播传输。故需配置组播映射,转换组播为单播。
本实验中,只有中心站点有固定IP,所以默认只能配置分支站点到中心站点的组播映射,故邻居关系的形成也只是分支与中心之间。
mGRE支持的动态路由协议:RIP、EIGRP、OSPF、BGP、ODR
本实验启用OSPF协议
HUB配置
HUB(config)#router ospf 110 //启用OSPF进程 HUB(config-router)#inter tunnel 1 HUB(config-if)#ip ospf 110 area 0 //把tunnel1的地址宣告到ospf area 0 HUB(config-if)#ip ospf priority 2 //修改HUB的tunnel接口ospf优先级为2,让HUB称为DR。 HUB(config-if)#inter loo0 HUB(config-if)#ip ospf 110 area 0 //把tunnel1的地址宣告到ospf area 0 HUB(config-if)#exit |
Spoken1配置
Spoken1(config)#router ospf 110 Spoken1(config-router)#inter tunnel 1 Spoken1(config-if)#ip ospf 110 area 0 Spoken1(config-if)#inter loo0 Spoken1(config-if)#ip ospf 110 are 0 Spoken1(config-if)#exit |
Spoken2配置
Spoken2(config)#router ospf 110 Spoken2(config-router)#inter tunnel 1 Spoken2(config-if)#ip ospf 110 area 0 Spoken2(config-if)#inter loo0 Spoken2(config-if)#ip ospf 110 area 0 Spoken2(config-if)#exit |
配置完成后,两个分支站点与中心站点之间的邻居关系建立时建时断,如下所示:
*Nov 12 21:56:12.303: %OSPF-5-ADJCHG: Process 110, Nbr 192.168.2.1 on Tunnel1 from FULL to DOWN, Neighbor Down: Adjacency forced to reset HUB(config-if)# *Nov 12 21:56:14.443: %OSPF-5-ADJCHG: Process 110, Nbr 192.168.3.1 on Tunnel1 from EXSTART to DOWN, Neighbor Down: Adjacency forced to reset *Nov 12 21:56:14.555: %OSPF-5-ADJCHG: Process 110, Nbr 192.168.2.1 on Tunnel1 from EXCHANGE to DOWN, Neighbor Down: Adjacency forced to reset *Nov 12 21:56:14.883: %OSPF-5-ADJCHG: Process 110, Nbr 192.168.3.1 on Tunnel1 from LOADING to FULL, Loading Done HUB(config-if)# *Nov 12 21:56:18.815: %OSPF-5-ADJCHG: Process 110, Nbr 192.168.3.1 on Tunnel1 from FULL to DOWN, Neighbor Down: Adjacency forced to reset *Nov 12 21:56:19.819: %OSPF-5-ADJCHG: Process 110, Nbr 192.168.2.1 on Tunnel1 from LOADING to FULL, Loading Done |
查看tunnel接口类型
HUB#sho ip ospf interface tunn HUB#sho ip ospf interface tunnel 1 Tunnel1 is up, line protocol is up Internet Address 172.16.1.1/24, Area 0 Process ID 110, Router ID 192.168.1.1, Network Type POINT_TO_POINT, Cost: 1000 Enabled by interface config, including secondary ip addresses Transmit Delay is 1 sec, State POINT_TO_POINT Timer intervals configured, Hello 10, Dead 40, Wait 40, Retransmit 5 oob-resync timeout 40 Hello due in 00:00:04 Supports Link-local Signaling (LLS) Cisco NSF helper support enabled IETF NSF helper support enabled Index 1/1, flood queue length 0 Next 0x0(0)/0x0(0) Last flood scan length is 1, maximum is 1 Last flood scan time is 0 msec, maximum is 4 msec Neighbor Count is 1, Adjacent neighbor count is 0 Suppress hello for 0 neighbor(s) |
如上图:tunnel接口的网络类型为点到点,所以HUB只能与一个ospf邻居建立邻居关系。而在本实验中,有两个分支站点要与中心站点建立OSPF的邻居关系,所以就导致了邻居关系的时建时断,不稳定。要解决此问题,就要把端口网络内省改为Broadcast或NBMA。
--------------------------------------------------HUB配置--------------------------------------- HUB(config)#inter tunnel 1 HUB(config-if)#ip ospf network broadcast --------------------------------------------------Spoken1配置--------------------------------------- Spoken1(config)#inter tunnel 1 Spoken1(config-if)#ip ospf network broadcast --------------------------------------------------Spoken2配置--------------------------------------- Spoken2(config)#inter tunnel 1 Spoken2(config-if)#ip ospf network broadcast |
待稳定之后查看路由表
--------------------------------------------------HUB路由表--------------------------------------- HUB#show ip route ……前面部分省略 Gateway of last resort is 202.1.1.254 to network 0.0.0.0
172.16.0.0/24 is subnetted, 1 subnets C 172.16.1.0 is directly connected, Tunnel1 C 202.1.1.0/24 is directly connected, FastEthernet0/0 C 192.168.1.0/24 is directly connected, Loopback0 192.168.2.0/32 is subnetted, 1 subnets O 192.168.2.1 [110/1001] via 172.16.1.2, 00:07:57, Tunnel1 192.168.3.0/32 is subnetted, 1 subnets O 192.168.3.1 [110/1001] via 172.16.1.3, 00:07:47, Tunnel1 S* 0.0.0.0/0 [1/0] via 202.1.1.254 --------------------------------------------------Spoken1路由表--------------------------------------- Spoken1#show ip route Gateway of last resort is 202.10.1.254 to network 0.0.0.0
172.16.0.0/24 is subnetted, 1 subnets C 172.16.1.0 is directly connected, Tunnel1 C 202.10.1.0/24 is directly connected, FastEthernet0/0 192.168.1.0/32 is subnetted, 1 subnets O 192.168.1.1 [110/1001] via 172.16.1.1, 00:10:31, Tunnel1 C 192.168.2.0/24 is directly connected, Loopback0 192.168.3.0/32 is subnetted, 1 subnets O 192.168.3.1 [110/1001] via 172.16.1.3, 00:10:11, Tunnel1 S* 0.0.0.0/0 [1/0] via 202.10.1.254 --------------------------------------------------Spoken2路由表--------------------------------------- Spoken2#show ip route Gateway of last resort is 202.100.1.254 to network 0.0.0.0
172.16.0.0/24 is subnetted, 1 subnets C 172.16.1.0 is directly connected, Tunnel1 C 202.100.1.0/24 is directly connected, FastEthernet0/0 192.168.1.0/32 is subnetted, 1 subnets O 192.168.1.1 [110/1001] via 172.16.1.1, 00:11:35, Tunnel1 192.168.2.0/32 is subnetted, 1 subnets O 192.168.2.1 [110/1001] via 172.16.1.2, 00:11:35, Tunnel1 C 192.168.3.0/24 is directly connected, Loopback0 S* 0.0.0.0/0 [1/0] via 202.100.1.254 |
如上:三个站点都学到了其他站点的路由。
注:ospf不存在水平分割和下一跳问题。如果使用的是EIGRP、RIP等路由协议,还涉及到水平分割、下一跳问题。也就是说,两个分支站点只有中心站点的地址,中心站点学到的一端分支站点的地址,由于水平分割的限制不会发送地址给另一端的分支站点,这样就导致了分支站点之间的路由学不到,只能学到中心站点的路由。然而,即使关闭水平分割,分支站点之间学到彼此的地址,还是会存在问题。一端分支站点学到的另一端的地址的下一跳是中心站点,也就是说,一个分支站点与另一个分支站点通信要经过中心站点转发。所以,使用EIGRP、RIP等协议时要同时关闭水平分割(no ip split-horizon eigrp 110)、下一跳为自己(no ipnext-hop-self eigrp 110)。
3.4.IPSec配置
本实验中,IPSec的任务就是保护Tunnel内的数据,对mGRE流量进行加密。
HUB配置
------------------------------------第一阶段配置----------------------------- HUB(config)#crypto isakmp policy 10 HUB(config-isakmp)#authentication pre-share HUB(config-isakmp)#group 2 HUB(config-isakmp)#encryption 3des HUB(config-isakmp)#hash md5 HUB(config-isakmp)#exit HUB(config)#crypto isakmp key freeit address 0.0.0.0 0.0.0.0 ----------------------------------第二阶段配置--------------------------------- HUB(config)#crypto ipsec transform-set l2l-ipsec esp-3des esp-md5-hmac HUB(cfg-crypto-trans)#exit HUB(config)#crypto ipsec profile dm***-profile HUB(ipsec-profile)#set tr HUB(ipsec-profile)#set transform-set l2l-ipsec -----------------------------------接口调用--------------------------------------- HUB(ipsec-profile)#inter tunnel 1 HUB(config-if)#tunnel protection ipsec profile dm***-profil |
Spoken1配置
Spoken1(config)#crypto isakmp policy 10 Spoken1(config-isakmp)# encr 3des Spoken1(config-isakmp)# hash md5 Spoken1(config-isakmp)# authentication pre-share Spoken1(config-isakmp)# group 2 Spoken1(config-isakmp)#crypto isakmp key freeit address 0.0.0.0 0.0.0.0 Spoken1(config)#crypto ipsec transform-set l2l-ipsec esp-3des esp-md5-hmac Spoken1(cfg-crypto-trans)#exit Spoken1(config)#crypto ipsec profile dm***-profile Spoken1(ipsec-profile)# set transform-set l2l-ipsec Spoken1(ipsec-profile)#exit Spoken1(config)#inter tunnel 1 Spoken1(config-if)#tunnel protection ipsec profile dm***-profile Spoken1(config-if)#exit |
Spoken2配置
Spoken2(config)#crypto isakmp policy 10 Spoken2(config-isakmp)# encr 3des Spoken2(config-isakmp)# hash md5 Spoken2(config-isakmp)# authentication pre-share Spoken2(config-isakmp)# group 2 Spoken2(config-isakmp)#crypto isakmp key freeit address 0.0.0.0 0.0.0.0 Spoken2(config)#crypto ipsec transform-set l2l-ipsec esp-3des esp-md5-hmac Spoken2(cfg-crypto-trans)#exit Spoken2(config)#crypto ipsec profile dm***-profile Spoken2(ipsec-profile)# set transform-set l2l-ipsec Spoken2(ipsec-profile)#exit Spoken2(config)#inter tunnel 1 Spoken2(config-if)#tunnel protection ipsec profile dm***-profile Spoken2(config-if)#exit |
3.5.验证
查看ipsec sa
----------------------------------------查看HUB的ipsec sa-------------------------------- HUB#sho crypto ipsec sa
interface: Tunnel1 Crypto map tag: Tunnel1-head-0, local addr 202.1.1.1
protected vrf: (none) local ident (addr/mask/prot/port): (202.1.1.1/255.255.255.255/47/0) remote ident (addr/mask/prot/port): (202.100.1.1/255.255.255.255/47/0) //HUB到Spoken1 current_peer 202.100.1.1 port 500 PERMIT, flags={origin_is_acl,} #pkts encaps: 16, #pkts encrypt: 16, #pkts digest: 16 #pkts decaps: 15, #pkts decrypt: 15, #pkts verify: 15 //Spoken与HUB之间是通过NHRP动态注册地址,所以SA是永久建立的(只要NHRP协议不出问题) #pkts compressed: 0, #pkts decompressed: 0 #pkts not compressed: 0, #pkts compr. failed: 0 #pkts not decompressed: 0, #pkts decompress failed: 0 #send errors 0, #recv errors 0
local crypto endpt.: 202.1.1.1, remote crypto endpt.: 202.100.1.1 path mtu 1500, ip mtu 1500, ip mtu idb FastEthernet0/0 current outbound spi: 0x93253648(2468689480)
inbound esp sas: spi: 0x48FF2360(1224680288) transform: esp-3des esp-md5-hmac , in use settings ={Tunnel, } conn id: 3, flow_id: SW:3, crypto map: Tunnel1-head-0 sa timing: remaining key lifetime (k/sec): (4467553/3538) IV size: 8 bytes replay detection support: Y Status: ACTIVE
inbound ah sas:
inbound pcp sas:
outbound esp sas: spi: 0x93253648(2468689480) transform: esp-3des esp-md5-hmac , in use settings ={Tunnel, } conn id: 4, flow_id: SW:4, crypto map: Tunnel1-head-0 sa timing: remaining key lifetime (k/sec): (4467553/3538) IV size: 8 bytes replay detection support: Y Status: ACTIVE
outbound ah sas:
outbound pcp sas:
protected vrf: (none) local ident (addr/mask/prot/port): (202.1.1.1/255.255.255.255/47/0) remote ident (addr/mask/prot/port): (202.10.1.1/255.255.255.255/47/0) //HUB到Spoken2 current_peer 202.10.1.1 port 500 PERMIT, flags={origin_is_acl,} #pkts encaps: 29, #pkts encrypt: 29, #pkts digest: 29 #pkts decaps: 26, #pkts decrypt: 26, #pkts verify: 26 #pkts compressed: 0, #pkts decompressed: 0 #pkts not compressed: 0, #pkts compr. failed: 0 #pkts not decompressed: 0, #pkts decompress failed: 0 #send errors 0, #recv errors 0
local crypto endpt.: 202.1.1.1, remote crypto endpt.: 202.10.1.1 path mtu 1500, ip mtu 1500, ip mtu idb FastEthernet0/0 current outbound spi: 0x3BF0C970(1005635952)
inbound esp sas: spi: 0x903C2D02(2419862786) transform: esp-3des esp-md5-hmac , in use settings ={Tunnel, } conn id: 1, flow_id: SW:1, crypto map: Tunnel1-head-0 sa timing: remaining key lifetime (k/sec): (4396432/3457) IV size: 8 bytes replay detection support: Y Status: ACTIVE
inbound ah sas:
inbound pcp sas:
outbound esp sas: spi: 0x3BF0C970(1005635952) transform: esp-3des esp-md5-hmac , in use settings ={Tunnel, } conn id: 2, flow_id: SW:2, crypto map: Tunnel1-head-0 sa timing: remaining key lifetime (k/sec): (4396432/3457) IV size: 8 bytes replay detection support: Y Status: ACTIVE
outbound ah sas:
outbound pcp sas: -------------------------------------------查看Spoken到HUB的IPSEC SA------------------------------------ Spoken1#show crypto ipsec sa
interface: Tunnel1 Crypto map tag: Tunnel1-head-0, local addr 202.10.1.1
protected vrf: (none) local ident (addr/mask/prot/port): (202.10.1.1/255.255.255.255/47/0) remote ident (addr/mask/prot/port): (202.1.1.1/255.255.255.255/47/0) //Spoken1到HUB current_peer 202.1.1.1 port 500 PERMIT, flags={origin_is_acl,} #pkts encaps: 48, #pkts encrypt: 48, #pkts digest: 48 #pkts decaps: 52, #pkts decrypt: 52, #pkts verify: 52 #pkts compressed: 0, #pkts decompressed: 0 #pkts not compressed: 0, #pkts compr. failed: 0 #pkts not decompressed: 0, #pkts decompress failed: 0 #send errors 0, #recv errors 0
local crypto endpt.: 202.10.1.1, remote crypto endpt.: 202.1.1.1 path mtu 1500, ip mtu 1500, ip mtu idb FastEthernet0/0 current outbound spi: 0x903C2D02(2419862786)
inbound esp sas: spi: 0x3BF0C970(1005635952) transform: esp-3des esp-md5-hmac , in use settings ={Tunnel, } conn id: 1, flow_id: SW:1, crypto map: Tunnel1-head-0 sa timing: remaining key lifetime (k/sec): (4529058/3242) IV size: 8 bytes replay detection support: Y Status: ACTIVE
inbound ah sas:
inbound pcp sas:
outbound esp sas: spi: 0x903C2D02(2419862786) transform: esp-3des esp-md5-hmac , in use settings ={Tunnel, } conn id: 2, flow_id: SW:2, crypto map: Tunnel1-head-0 sa timing: remaining key lifetime (k/sec): (4529059/3242) IV size: 8 bytes replay detection support: Y Status: ACTIVE
outbound ah sas:
outbound pcp sas:
Spoken2#show crypto ipse sa
interface: Tunnel1 Crypto map tag: Tunnel1-head-0, local addr 202.100.1.1
protected vrf: (none) local ident (addr/mask/prot/port): (202.100.1.1/255.255.255.255/47/0) remote ident (addr/mask/prot/port): (202.1.1.1/255.255.255.255/47/0) //spoken2到HUB current_peer 202.1.1.1 port 500 PERMIT, flags={origin_is_acl,} #pkts encaps: 50, #pkts encrypt: 50, #pkts digest: 50 #pkts decaps: 52, #pkts decrypt: 52, #pkts verify: 52 #pkts compressed: 0, #pkts decompressed: 0 #pkts not compressed: 0, #pkts compr. failed: 0 #pkts not decompressed: 0, #pkts decompress failed: 0 #send errors 0, #recv errors 0
local crypto endpt.: 202.100.1.1, remote crypto endpt.: 202.1.1.1 path mtu 1500, ip mtu 1500, ip mtu idb FastEthernet0/0 current outbound spi: 0x48FF2360(1224680288)
inbound esp sas: spi: 0x93253648(2468689480) transform: esp-3des esp-md5-hmac , in use settings ={Tunnel, } conn id: 1, flow_id: SW:1, crypto map: Tunnel1-head-0 sa timing: remaining key lifetime (k/sec): (4387930/3201) IV size: 8 bytes replay detection support: Y Status: ACTIVE
inbound ah sas:
inbound pcp sas:
outbound esp sas: spi: 0x48FF2360(1224680288) transform: esp-3des esp-md5-hmac , in use settings ={Tunnel, } conn id: 2, flow_id: SW:2, crypto map: Tunnel1-head-0 sa timing: remaining key lifetime (k/sec): (4387931/3201) IV size: 8 bytes replay detection support: Y Status: ACTIVE
outbound ah sas:
outbound pcp sas:
//从上可以看出,spoken之间没有通信时是不会建立IPSec SA的,spoken站点正常情况下只与HUB站点之间建立IPSec |
接下来我们让两个Spoken之间通信
-----------------让spoken1向spoken2发送ICMP包--------------- Spoken1#ping 192.168.3.1 source loopback 0
Type escape sequence to abort. Sending 5, 100-byte ICMP Echos to 192.168.3.1, timeout is 2 seconds: Packet sent with a source address of 192.168.2.1 !!!!! Success rate is 100 percent (5/5), round-trip min/avg/max = 144/192/260 ms -----------------------查看Ipsec sa----------------- Spoken1#show crypto ipsec sa
interface: Tunnel1 Crypto map tag: Tunnel1-head-0, local addr 202.10.1.1
protected vrf: (none) local ident (addr/mask/prot/port): (202.10.1.1/255.255.255.255/47/0) remote ident (addr/mask/prot/port): (202.100.1.1/255.255.255.255/47/0) //Spoken1到Spoken2 current_peer 202.100.1.1 port 500 PERMIT, flags={origin_is_acl,} #pkts encaps: 0, #pkts encrypt: 0, #pkts digest: 0 #pkts decaps: 2, #pkts decrypt: 2, #pkts verify: 2 #pkts compressed: 0, #pkts decompressed: 0 #pkts not compressed: 0, #pkts compr. failed: 0 #pkts not decompressed: 0, #pkts decompress failed: 0 #send errors 0, #recv errors 0
local crypto endpt.: 202.10.1.1, remote crypto endpt.: 202.100.1.1 path mtu 1500, ip mtu 1500, ip mtu idb FastEthernet0/0 current outbound spi: 0xD2C3F01F(3536056351)
inbound esp sas: spi: 0x2A42D7FD(709023741) transform: esp-3des esp-md5-hmac , in use settings ={Tunnel, } conn id: 3, flow_id: SW:3, crypto map: Tunnel1-head-0 sa timing: remaining key lifetime (k/sec): (4418814/3528) IV size: 8 bytes replay detection support: Y Status: ACTIVE
inbound ah sas:
inbound pcp sas:
outbound esp sas: spi: 0xD2C3F01F(3536056351) transform: esp-3des esp-md5-hmac , in use settings ={Tunnel, } conn id: 4, flow_id: SW:4, crypto map: Tunnel1-head-0 sa timing: remaining key lifetime (k/sec): (4418815/3528) IV size: 8 bytes replay detection support: Y Status: ACTIVE
outbound ah sas:
outbound pcp sas:
protected vrf: (none) local ident (addr/mask/prot/port): (202.10.1.1/255.255.255.255/47/0) remote ident (addr/mask/prot/port): (202.1.1.1/255.255.255.255/47/0) current_peer 202.1.1.1 port 500 PERMIT, flags={origin_is_acl,} #pkts encaps: 103, #pkts encrypt: 103, #pkts digest: 103 #pkts decaps: 105, #pkts decrypt: 105, #pkts verify: 105 #pkts compressed: 0, #pkts decompressed: 0 #pkts not compressed: 0, #pkts compr. failed: 0 #pkts not decompressed: 0, #pkts decompress failed: 0 #send errors 0, #recv errors 0
local crypto endpt.: 202.10.1.1, remote crypto endpt.: 202.1.1.1 path mtu 1500, ip mtu 1500, ip mtu idb FastEthernet0/0 current outbound spi: 0x903C2D02(2419862786)
inbound esp sas: spi: 0x3BF0C970(1005635952) transform: esp-3des esp-md5-hmac , in use settings ={Tunnel, } conn id: 1, flow_id: SW:1, crypto map: Tunnel1-head-0 sa timing: remaining key lifetime (k/sec): (4529049/2798) IV size: 8 bytes replay detection support: Y Status: ACTIVE
inbound ah sas:
inbound pcp sas:
outbound esp sas: spi: 0x903C2D02(2419862786) transform: esp-3des esp-md5-hmac , in use settings ={Tunnel, } conn id: 2, flow_id: SW:2, crypto map: Tunnel1-head-0 sa timing: remaining key lifetime (k/sec): (4529050/2798) IV size: 8 bytes replay detection support: Y Status: ACTIVE
outbound ah sas:
outbound pcp sas: 如上,两个spoken站点之间通信后,IPSec SA临时建立 |
验证各站点之间的通信状况
--------------------------------HUB向Spoken----------------- HUB#ping 192.168.2.1 source loo0
Type escape sequence to abort. Sending 5, 100-byte ICMP Echos to 192.168.2.1, timeout is 2 seconds: Packet sent with a source address of 192.168.1.1 !!!!! Success rate is 100 percent (5/5), round-trip min/avg/max = 80/112/124 ms HUB#ping 192.168.3.1 source loo0
Type escape sequence to abort. Sending 5, 100-byte ICMP Echos to 192.168.3.1, timeout is 2 seconds: Packet sent with a source address of 192.168.1.1 !!!!! Success rate is 100 percent (5/5), round-trip min/avg/max = 80/110/144 ms ---------------------------------Spoken1向其他站点---------------------- Spoken1#ping 192.168.1.1 source loo0
Type escape sequence to abort. Sending 5, 100-byte ICMP Echos to 192.168.1.1, timeout is 2 seconds: Packet sent with a source address of 192.168.2.1 !!!!! Success rate is 100 percent (5/5), round-trip min/avg/max = 84/108/140 ms
Spoken1#ping 192.168.3.1 source loo0
Type escape sequence to abort. Sending 5, 100-byte ICMP Echos to 192.168.3.1, timeout is 2 seconds: Packet sent with a source address of 192.168.2.1 !!!!! Success rate is 100 percent (5/5), round-trip min/avg/max = 92/111/144 ms ---------------------------------Spoken2向其他站点---------------------- Spoken2#ping 192.168.1.1 source loo0
Type escape sequence to abort. Sending 5, 100-byte ICMP Echos to 192.168.1.1, timeout is 2 seconds: Packet sent with a source address of 192.168.3.1 !!!!! Success rate is 100 percent (5/5), round-trip min/avg/max = 84/117/136 ms Spoken2#ping 192.168.2.1 source loo0
Type escape sequence to abort. Sending 5, 100-byte ICMP Echos to 192.168.2.1, timeout is 2 seconds: Packet sent with a source address of 192.168.3.1 !!!!! Success rate is 100 percent (5/5), round-trip min/avg/max = 84/111/128 ms |
各站点IPSec ×××通信正常
最终命令配置
HUB配置
cryptoisakmp policy 10
encr 3des
hash md5
authentication pre-share
group 2
cryptoisakmp key freeit address 0.0.0.0 0.0.0.0
!
!
cryptoipsec transform-set l2l-ipsec esp-3des esp-md5-hmac
!
cryptoipsec profile dm***-profile
set transform-set l2l-ipsec
!
!
interfaceLoopback0
ip address 192.168.1.1 255.255.255.0
ip ospf 110 area 0
!
interfaceTunnel1
ip address 172.16.1.1 255.255.255.0
no ip redirects
ip nhrp authentication cisco
ip nhrp map multicast dynamic
ip nhrp network-id 10
ip ospf network broadcast
ip ospf priority 2
ip ospf 110 area 0
tunnel source FastEthernet0/0
tunnel mode gre multipoint
tunnel key 123456
tunnel protection ipsec profile dm***-profile
!
interfaceFastEthernet0/0
ip address 202.1.1.1 255.255.255.0
duplex auto
speed auto
!
routerospf 110
log-adjacency-changes
!
iproute 0.0.0.0 0.0.0.0 202.1.1.254
!
end
Spoken1配置
cryptoisakmp policy 10
encr 3des
hash md5
authentication pre-share
group 2
cryptoisakmp key freeit address 0.0.0.0 0.0.0.0
!
!
cryptoipsec transform-set l2l-ipsec esp-3des esp-md5-hmac
!
cryptoipsec profile dm***-profile
set transform-set l2l-ipsec
!
!
!
!
iptcp synwait-time 5
!
!
!
!
interfaceLoopback0
ip address 192.168.2.1 255.255.255.0
ip ospf 110 area 0
!
interfaceTunnel1
ip address 172.16.1.2 255.255.255.0
no ip redirects
ip nhrp authentication cisco
ip nhrp map 172.16.1.1 202.1.1.1
ip nhrp map multicast 202.1.1.1
ip nhrp network-id 10
ip nhrp nhs 172.16.1.1
ip ospf network broadcast
ip ospf 110 area 0
tunnel source FastEthernet0/0
tunnel mode gre multipoint
tunnel key 123456
tunnel protection ipsec profile dm***-profile
!
interfaceFastEthernet0/0
ip address 202.10.1.1 255.255.255.0
duplex auto
speed auto
iproute 0.0.0.0 0.0.0.0 202.10.1.254
!
End
Spoken2配置
cryptoisakmp policy 10
encr 3des
hash md5
authentication pre-share
group 2
cryptoisakmp key freeit address 0.0.0.0 0.0.0.0
!
!
cryptoipsec transform-set l2l-ipsec esp-3des esp-md5-hmac
!
cryptoipsec profile dm***-profile
set transform-set l2l-ipsec
!
!
!
!
iptcp synwait-time 5
!
!
!
!
interfaceLoopback0
ip address 192.168.3.1 255.255.255.0
ip ospf 110 area 0
!
interfaceTunnel1
ip address 172.16.1.3 255.255.255.0
no ip redirects
ip nhrp authentication cisco
ip nhrp map 172.16.1.1 202.1.1.1
ip nhrp map multicast 202.1.1.1
ip nhrp network-id 10
ip nhrp nhs 172.16.1.1
ip ospf network broadcast
ip ospf 110 area 0
tunnel source FastEthernet0/0
tunnel mode gre multipoint
tunnel key 123456
tunnel protection ipsec profile dm***-profile
!
interfaceFastEthernet0/0
ip address 202.100.1.1 255.255.255.0
duplex auto
speed auto
!
ipforward-protocol nd
iproute 0.0.0.0 0.0.0.0 202.100.1.254
end
四.实验总结
典型×××对于星形、环形网络存在缺点:各站点配置繁杂、分支站点占用中心站点流量导致中心站点流量紧张、分支站点之间的通信延迟大;所以引入DM×××来解决这些问题;
DM×××具有四大优点:.简单的星形拓扑配置,提供虚拟网状连通性;分支站点支持动态IP地址;增加新的分支站点,无需更改中心站点配置;分支站点间流量,通过动态产生的站点间隧道进行封装;
DM×××靠四大技术支撑:mGRE、NHRP、IGP协议、IPSec ×××。