HAproxy
实验环境:rhel6.5 selinux and iptables disabled
实验主机: 172.25.23.1 server1.example.com haproxy
172.25.23.4 server4.example.com web1
172.25.23.5 server5.example.com web2
1.安装软件
rpm 包方式:
rpmbuild -tb haproxy-1.4.23.tar.gz
rpm -ivh /root/rpmbuild/RPMS/x86_64/haproxy-1.4.23-1.x86_64.rpm
源码方式:
tar zxf haproxy-1.4.23.tar.gz
cd haproxy-1.4.23
make TARGET=linux26 ARCH=x86_64 USE_PCRE=1 PREFIX=/usr/local/haproxy install
下载压缩包haproxy-1.4.24.tar.gz
[root@server1 ~]# rpmbuild -tb haproxy-1.4.24.tar.gz
[root@server1 ~]# yum install pcre-devel -y
[root@server1 ~]# rpmbuild -tb haproxy-1.4.24.tar.gz
[root@server1 ~]# cd rpmbuild/RPMS/x86_64/
[root@server1 ~]# rpm -ivh haproxy-1.4.24-1.x86_64.rpm
[root@server1 ~]# cd /etc/haproxy/
2.编译配置文件
[root@server1 ~]# cp haproxy.cfg haproxy.cfg.bak #做备份
[root@server1 ~]# vim haproxy.cfg
---->
# this config needs haproxy-1.1.28 or haproxy-1.2.1
global
log 127.0.0.1 local0#指定日志设备
#log 127.0.0.1 local1 notice
log loghost local0 info#指定日志类型,还有 err warning debug
maxconn 4096#并发最大连接数量
chroot /usr/share/haproxy#jail 目录
uid 99#用户
gid 99#组
daemon#后台运行
#debug
#quiet
defaults
log global
mode http#默认使用 http 的 7 层模式 tcp: 4 层
option httplog#http 日志格式
option dontlognull#禁用空链接日志
retries 3#重试 3 次失败认为服务器不可用
option redispatch#当 client 连接到挂掉的机器时,重新分配到健康的主机!
maxconn 2000
contimeout 5000#连接超时
clitimeout 50000#客户端超时
srvtimeout 50000 #服务器端超时
stats uri /status#haproxy 监控页面
listen westos *:80#监听的实例名称,地址和端口
balance roundrobin#负载均衡算法
server web1 172.25.23.4:80 check inter 2000 rise 2 fall 3
server web2 172.25.23.5:80 check inter 2000 rise 2 fall 3
#check inter 2000:检测心跳频率
#rise 2:表示 2 次正确认为服务器可用
#fall 5:表示 5 次失败认为服务器不可用
[root@server1 ~]# mkdir /usr/share/haproxy
[root@server1 ~]# /etc/init.d/haproxy start
3.测试
在两台real server即web1 web2 上安装httpd,创建测试页并且启动服务
测试访问 172.25.23.1 会发现两个测试页轮询显示
健康检查
defaults 模块中加入 stats uri /status重启服务
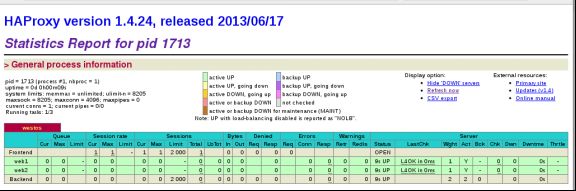
访问 haproxy 监控页面:http://172.25.23.1/status
4.监控页面添加认证:
listen stats_auth 172.25.23.1:80
stats enable
stats uri /status #监控页面地址
stats auth admin:westos #管理帐号和密码
stats refresh 5s #刷新频率
5.haproxy 日志:
vim /etc/rsyslog.conf #接受 haproxy 日志
13 $ModLoad imudp
14 $UDPServerRun 514
42*.info;mail.none;authpriv.none;cron.none;local0.none /var/log/messages
63 local0.* /var/log/haproxy.log#日志文件位置
/etc/init.d/rsyslog restart
vim /etc/haproxy/haproxy.cfg
...
#log loghost local0 info#注释掉该行
...
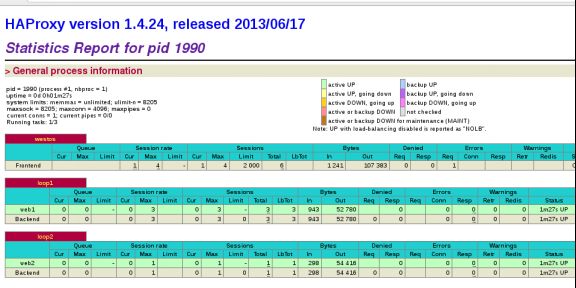
6.前后台显示健康检查信息
vim /etc/haproxy/haproxy.cfg
...
frontend westos *:80
default_backendloop1
backend loop1
balance roundrobin
server web1 172.25.23.4:80 check inter 2000 rise 2 fall 3
server web2 172.25.23.5:80 check inter 2000 rise 2 fall 3
/etc/init.d/haproxy restart
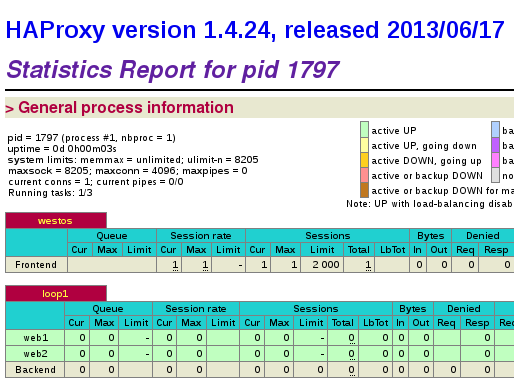
访问 172.25.23.1/status
7.
加了权重,并且当两个real server都挂掉时,显示自己的测试页
修改自己的http监听端口为8080,避免和haproxy的80 端口冲突
vim /etc/haproxy/haproxy.cfg
...
frontend westos *:80
default_backendloop1
backend loop1
balance roundrobin
server web1 172.25.23.4:80 check inter 2000 rise 2 fall 3 weight 1
server web2 172.25.23.5:80 check inter 2000 rise 2 fall 3 weight 1
server backup 127.0.0.1:8080 backup
/etc/init.d/haproxy restart
8.ACL
vim /etc/haproxy/haproxy.cfg
...
frontend westos *:80
acl badhost src 172.25.23.250#拒绝172.25.23.250访问,也可以是一个网段
block if badhost
default_backendloop1
backend loop1
balance roundrobin
server web1 172.25.23.4:80 check inter 2000 rise 2 fall 3 weight 1
server web2 172.25.23.5:80 check inter 2000 rise 2 fall 3 weight 1
server backup 127.0.0.1:8080 backup
/etc/init.d/haproxy restart
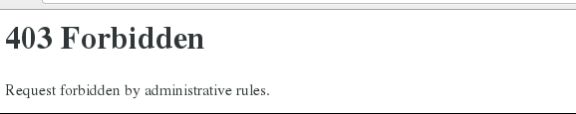
在172.25.23.250上访问172.25.23.1
9.通过错误代码403重定向,定向到 http://172.25.23.1:8080
vim /etc/haproxy/haproxy.cfg
...
frontend westos *:80
acl badhost src 172.25.23.250#拒绝172.25.23.250访问,也可以是一个网段
block if badhost
errorloc 403 http://172.25.23.1:8080
default_backendloop1
backend loop1
balance roundrobin
server web1 172.25.23.4:80 check inter 2000 rise 2 fall 3 weight 1
server web2 172.25.23.5:80 check inter 2000 rise 2 fall 3 weight 1
server backup 127.0.0.1:8080 backup
/etc/init.d/haproxy restart
10.根据来源重定向
vim /etc/haproxy/haproxy.cfg
...
frontend westos *:80
acl badhost src 172.25.23.250#拒绝172.25.23.250访问,也可以是一个网段
#block if badhost
#errorloc 403 http://172.25.23.1:8080
redirect location http://172.25.23.1:8080 if badhost
default_backendloop1
backend loop1
balance roundrobin
server web1 172.25.23.4:80 check inter 2000 rise 2 fall 3 weight 1
server web2 172.25.23.5:80 check inter 2000 rise 2 fall 3 weight 1
server backup 127.0.0.1:8080 backup
/etc/init.d/haproxy restart
11.动静分离
Server1
vim /etc/haproxy/haproxy.cfg
...
frontend westos *:80
acl badhost src 172.25.23.250#拒绝172.25.23.250访问,也可以是一个网段
#block if badhost
#errorloc 403 http://172.25.23.1:8080
#redirect location http://172.25.23.1:8080 if badhost
acl url_static path_beg -i /p_w_picpaths
acl url_static path_end -i .jpg$ .png$ .jpeg$ .gif$
use_backend loop2 if url_static
default_backendloop1
backend loop1
balance roundrobin
server web1 172.25.23.4:80 check inter 2000 rise 2 fall 3 weight 1
backend loop2
balance roundrobin
server web2 172.25.23.5:80 check inter 2000 rise 2 fall 3 weight 1
/etc/init.d/haproxy restart
Server 4 建立php测试页
yum install php -y
/var/www/html 目录下新建index.php测试页
/etc/init.d/httpd restart
访问172.25.23.1
Server5
mkdir /var/www/html/p_w_picpaths
get redhat.jpg
/etc/init.d/httpd restart
访问 172.25.23.1/p_w_picpaths/redhat.jpg
172.25.23.1/status
12.读写分离
Server1
vim /etc/haproxy/haproxy.cfg
...
frontend westos *:80
acl badhost src 172.25.23.250#拒绝172.25.23.250访问,也可以是一个网段
#block if badhost
#errorloc 403 http://172.25.23.1:8080
#redirect location http://172.25.23.1:8080 if badhost
acl url_static path_beg -i /p_w_picpaths
acl url_static path_end -i .jpg$ .png$ .jpeg$ .gif$
acl read method GET
acl read method HEAD
acl write method PUT
acl write method POST
use_backend loop2 if write
default_backendloop1
backend loop1
balance roundrobin
server web1 172.25.23.4:80 check inter 2000 rise 2 fall 3 weight 1
backend loop2
balance roundrobin
server web2 172.25.23.5:80 check inter 2000 rise 2 fall 3 weight 1
/etc/init.d/haproxy restart
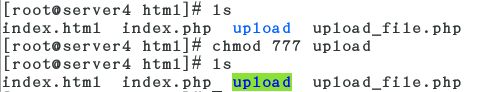
server4 server5
yum install -y php
cd /var/www/html
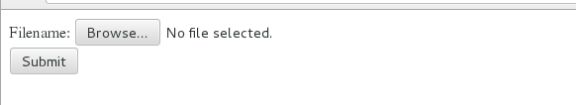
访问 172.25.23.1