iptables规则备份与还原
1.iptables-save > filename:保存备份规则
[root@weixing01 ~]# iptables-save > /tmp/ipt.txt
[root@weixing01 ~]# cat /tmp/ipt.txt
# Generated by iptables-save v1.4.21 on Fri Jan 26 22:05:20 2018
*filter
:INPUT ACCEPT [0:0]
:FORWARD ACCEPT [0:0]
:OUTPUT ACCEPT [117:14215]
-A INPUT -m state --state RELATED,ESTABLISHED -j ACCEPT
-A INPUT -p icmp -j ACCEPT
-A INPUT -i lo -j ACCEPT
-A INPUT -p tcp -m state --state NEW -m tcp --dport 22 -j ACCEPT
-A INPUT -j REJECT --reject-with icmp-host-prohibited
-A FORWARD -j REJECT --reject-with icmp-host-prohibited
COMMIT
# Completed on Fri Jan 26 22:05:20 2018
2.iptables-restore < filename :恢复备份规则
[root@weixing01 ~]# iptables -F
[root@weixing01 ~]# iptables -nvL
Chain INPUT (policy ACCEPT 33 packets, 2828 bytes)
pkts bytes target prot opt in out source destination
Chain FORWARD (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
Chain OUTPUT (policy ACCEPT 19 packets, 2328 bytes)
pkts bytes target prot opt in out source destination
[root@weixing01 ~]# iptables-restore < /tmp/ipt.txt
[root@weixing01 ~]# iptables -nvL
Chain INPUT (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
6 500 ACCEPT all -- * * 0.0.0.0/0 0.0.0.0/0 state RELATED,ESTABLISHED
0 0 ACCEPT icmp -- * * 0.0.0.0/0 0.0.0.0/0
0 0 ACCEPT all -- lo * 0.0.0.0/0 0.0.0.0/0
0 0 ACCEPT tcp -- * * 0.0.0.0/0 0.0.0.0/0 state NEW tcp dpt:22
0 0 REJECT all -- * * 0.0.0.0/0 0.0.0.0/0 reject-with icmp-host-prohibited
Chain FORWARD (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
0 0 REJECT all -- * * 0.0.0.0/0 0.0.0.0/0 reject-with icmp-host-prohibited
Chain OUTPUT (policy ACCEPT 4 packets, 528 bytes)
pkts bytes target prot opt in out source destination
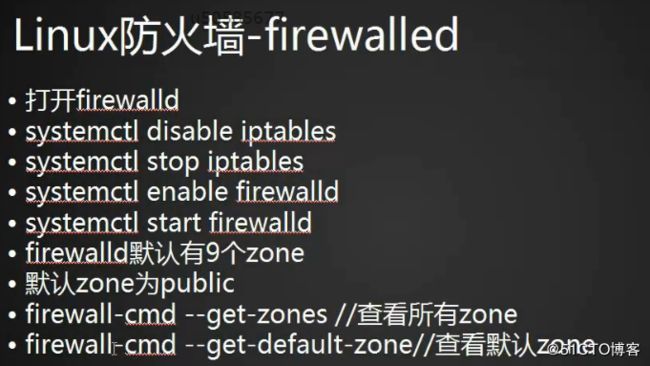
firewalld
[root@weixing01 ~]# systemctl disable iptables
Removed symlink /etc/systemd/system/basic.target.wants/iptables.service.
[root@weixing01 ~]# systemctl stop iptables
[root@weixing01 ~]# systemctl enable firewalld
Created symlink from /etc/systemd/system/dbus-org.fedoraproject.FirewallD1.service to /usr/lib/systemd/system/firewalld.service.
Created symlink from /etc/systemd/system/multi-user.target.wants/firewalld.service to /usr/lib/systemd/system/firewalld.service.
[root@weixing01 ~]# systemctl start firewalld
2.查看所有zone以及默认zone:共九个,默认public
[root@weixing01 ~]# firewall-cmd --get-zones
block dmz drop external home internal public trusted work
[root@weixing01 ~]# firewall-cmd --get-default-zone
public
firewalld的一些操作
[root@weixing01 ~]# firewall-cmd --set-default-zone=work
success
[root@weixing01 ~]# firewall-cmd --get-default-zone
work
2.查看指定网卡:
[root@weixing01 ~]# firewall-cmd --get-zone-of-interface=ens33
work
[root@weixing01 ~]# firewall-cmd --get-zone-of-interface=ens37
work
[root@weixing01 ~]# firewall-cmd --get-zone-of-interface=lo
no zone
3.给指定网卡增加zone:
[root@weixing01 ~]# firewall-cmd --zone=dmz --add-interface=ens37
The interface is under control of NetworkManager, setting zone to 'dmz'.
success
[root@weixing01 ~]# firewall-cmd --get-zone-of-interface=ens37
dmz
[root@weixing01 ~]# firewall-cmd --zone=public --add-interface=lo
success
[root@weixing01 ~]# firewall-cmd --get-zone-of-interface=lo
public
4.给指定网卡修改zone:
[root@weixing01 ~]# firewall-cmd --zone=block --change-interface=ens37
The interface is under control of NetworkManager, setting zone to 'block'.
success
5.给指定网卡删除zone:删除后变成默认
[root@weixing01 ~]# firewall-cmd --zone=block --remove-interface=ens37
The interface is under control of NetworkManager, setting zone to default.
success
[root@weixing01 ~]# firewall-cmd --get-zone-of-interface=ens37
work
6.查看系统所有网卡所在zone:
[root@weixing01 ~]# firewall-cmd --get-active-zones
work
interfaces: ens33 ens37
public
interfaces: lo
firewalld关于service的一些操作
1.查看所有services:
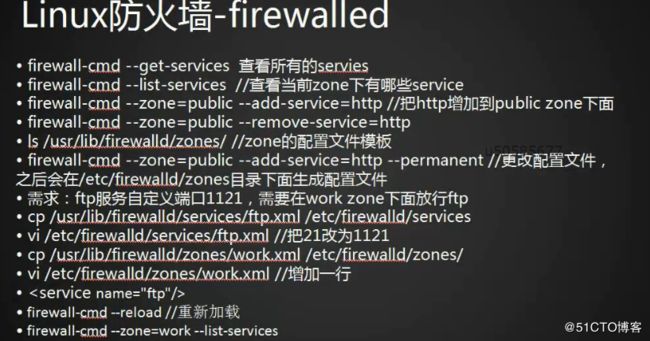
[root@weixing01 ~]# firewall-cmd --get-services
RH-Satellite-6 amanda-client amanda-k5-client bacula bacula-client bitcoin bitcoin-rpc bitcoin-testnet bitcoin-testnet-rpc ceph ceph-mon cfengine condor-collector ctdb dhcp dhcpv6 dhcpv6-client dns docker-registry dropbox-lansync elasticsearch freeipa-ldap freeipa-ldaps freeipa-replication freeipa-trust ftp ganglia-client ganglia-master high-availability http https imap imaps ipp ipp-client ipsec iscsi-target kadmin kerberos kibana klogin kpasswd kshell ldap ldaps libvirt libvirt-tls managesieve mdns mosh mountd ms-wbt mssql mysql nfs nrpe ntp open*** ovirt-imageio ovirt-storageconsole ovirt-vmconsole pmcd pmproxy pmwebapi pmwebapis pop3 pop3s postgresql privoxy proxy-dhcp ptp pulseaudio puppetmaster quassel radius rpc-bind rsh rsyncd samba samba-client sane sip sips smtp smtp-submission smtps snmp snmptrap spideroak-lansync squid ssh synergy syslog syslog-tls telnet tftp tftp-client tinc tor-socks transmission-client vdsm vnc-server wbem-https xmpp-bosh xmpp-client xmpp-local xmpp-server
2.查看当前zone下有哪些service:
[root@weixing01 ~]# firewall-cmd --list-services
ssh dhcpv6-client
3.查看指定zone下有哪些service
[root@weixing01 ~]# firewall-cmd --zone=public --list-services
ssh dhcpv6-client
[root@weixing01 ~]# firewall-cmd --zone=block --list-services
[root@weixing01 ~]# firewall-cmd --zone=trusted --list-services 4.把一些服务增加到指定zone下面:
[root@weixing01 ~]# firewall-cmd --zone=public --add-service=http
success
[root@weixing01 ~]# firewall-cmd --zone=public --list-services
ssh dhcpv6-client http
[root@weixing01 ~]# firewall-cmd --zone=public --add-service=https
success
[root@weixing01 ~]# firewall-cmd --zone=public --add-service=ftp
success
[root@weixing01 ~]# firewall-cmd --zone=public --list-services
ssh dhcpv6-client http https ftp
5.将修改写入配置文件:
[root@weixing01 ~]# firewall-cmd --zone=public --add-service=ftp --permanent success
[root@weixing01 ~]# ls /etc/firewalld/zones #配置文件路径
public.xml public.xml.old
[root@weixing01 ~]# cat /etc/firewalld/zones/public.xml #查看文件内容
Public
For use in public areas. You do not trust the other computers on networks to not harm your computer. Only selected incoming connections are accepted.
6.模板文件存在路径:
[root@weixing01 ~]# ls /usr/lib/firewalld/zones/
block.xml drop.xml home.xml public.xml work.xml
dmz.xml external.xml internal.xml trusted.xml
[root@weixing01 ~]# ls /usr/lib/firewalld/services/
amanda-client.xml kadmin.xml quassel.xml
amanda-k5-client.xml kerberos.xml radius.xml
bacula-client.xml kibana.xml RH-Satellite-6.xml
bacula.xml klogin.xml rpc-bind.xml
bitcoin-rpc.xml kpasswd.xml rsh.xml
bitcoin-testnet-rpc.xml kshell.xml rsyncd.xml
bitcoin-testnet.xml ldaps.xml samba-client.xml
bitcoin.xml ldap.xml samba.xml
ceph-mon.xml libvirt-tls.xml sane.xml
ceph.xml libvirt.xml sips.xml
7.图片中需求的实现:
(1)复制service下ftp模板到/etc/firewalld/services下
(2)修改该文件端口21为1121
(3)复制zone下work模板到 /etc/firewalld/zones下
(4)修改该文件,增加ftp服务
[root@weixing01 ~]# cp /usr/lib/firewalld//services/ftp.xml /etc/firewalld/services/
[root@weixing01 ~]# vim /etc/firewalld/services/ftp.xml
[root@weixing01 ~]# cp /usr/lib/firewalld/zones/work.xml /etc/firewalld/zones/
[root@weixing01 ~]# vim /etc/firewalld/zones/work.xml
[root@weixing01 ~]# firewall-cmd reload
usage: see firewall-cmd man page
firewall-cmd: error: unrecognized arguments: reload
[root@weixing01 ~]# firewall-cmd --reload
success
[root@weixing01 ~]# firewall-cmd --zone=work --list-services
ssh ftp dhcpv6-client