内容简介
在centos6系统中安装配置openldap服务,通过migrationtools工具生成基于linux系统账户相关的ldap账户信息以及通过nfs共享方式在客户端自动挂接ldap用户的家目录
环境准备
1,准备两台及以上centos6操作系统主机,一台用于部署服务端其它用于部署客户端接入ldap认证
2,关闭selinux
3,清空iptables规则
4,配置好yum源,推荐使用阿里云yum源
ldap服务端安装与配置
安装相关软件包
[root@ldap-server ~]# yum list | grep openldap
openldap.x86_64 2.4.23-20.el6 @anaconda-RedHatEnterpriseLinux-201111171049.x86_64/6.2
compat-openldap.i686 1:2.3.43-2.el6 base
compat-openldap.x86_64 1:2.3.43-2.el6 base
openldap.i686 2.4.40-7.el6_7 updates
openldap.x86_64 2.4.40-7.el6_7 updates
openldap-clients.x86_64 2.4.40-7.el6_7 updates
openldap-devel.i686 2.4.40-7.el6_7 updates
openldap-devel.x86_64 2.4.40-7.el6_7 updates
openldap-servers.x86_64 2.4.40-7.el6_7 updates
openldap-servers-sql.x86_64 2.4.40-7.el6_7 updates
[root@ldap-server ~]# yum install openldap openldap-clients openldap-servers openldap-devel -y
openldap配置主目录在/etc/openldap下,默认文件目录如下
[root@ldap-server ~]# ll /etc/openldap/
total 28
drwxr-xr-x 2 root root 4096 Jan 10 11:07 certs
-rw-r----- 1 root ldap 121 Nov 10 2015 check_password.conf
-rw-r--r-- 1 root root 280 Nov 10 2015 ldap.conf
drwxr-xr-x 2 root root 4096 Jan 10 11:07 schema
drwx------ 2 ldap ldap 4096 Jan 10 11:10 slapd.d
生成hash密码稍后用于配置ldap管理员密码,此处设置的密码为123456
[root@ldap-server ~]# slappasswd
New password:
Re-enter new password:
{SSHA}SpiJ+uf0d1j7bRm6XoLJo9EX3Gk5uzzH
拷贝服务端配置模版至/etc/openldap并配置,主要修改dc=my-domain,dc=com为自己的域名以及配置rootpw用于后续导入系统帐号信息,如下图所示
[root@ldap-server ~]# /bin/cp /usr/share/openldap-servers/slapd.conf.obsolete /etc/openldap/slapd.conf
拷贝DB_SAMPLE模版文件文件至/var/lib/ldap
[root@ldap-server ~]# /bin/cp /usr/share/openldap-servers/DB_CONFIG.example /var/lib/ldap/DB_CONFIG
[root@ldap-server ~]# chown ldap. /var/lib/ldap/ -R
删除默认的ldap配置信息并重新生成相关配置
[root@ldap-server ~]# rm -rf /etc/openldap/slapd.d/*
[root@ldap-server ~]# slaptest -f /etc/openldap/slapd.conf -F /etc/openldap/slapd.d
5c6452d3 bdb_db_open: database "dc=rocshen,dc=com": db_open(/var/lib/ldap/id2entry.bdb) failed: No such file or directory (2).5c6452d3 backend_startup_one (type=bdb, suffix="dc=rocshen,dc=com"): bi_db_open failed! (2)
slap_startup failed (test would succeed using the -u switch)
[root@ldap-server ~]# chown ldap. /etc/openldap/ -R
[root@ldap-server ~]# chown ldap. /var/lib/ldap -R
至此服务配置已经完成,启动ldap服务
[root@ldap-server ~]# service slapd start
Starting slapd: [ OK ]
[root@ldap-server ~]#
生成系统账户并导入ldap
创建/home/ldapuser为ldap用户家目录的上级目录
创建teacher及student组,gid分别为2000和3000(根据实际情况而定) 生成user01-user10归属teacher组
生成user11-users0归属student组
[root@ldap-server ~]# mkdir -p /home/ldapuser
[root@ldap-server ~]# groupadd teacher -g 2000
[root@ldap-server ~]# groupadd student -g 3000
[root@ldap-server ~]# for i in {01..10};do useradd -g teacher -d /home/ldapuser/user$i user$i;done
[root@ldap-server ~]# for i in {11..20};do useradd -g student -d /home/ldapuser/user$i user$i;done
[root@ldap-server ~]# for i in {01..20};do echo user$i | passwd --stdin user$i;done
Changing password for user user01.
passwd: all authentication tokens updated successfully.
Changing password for user user02.
passwd: all authentication tokens updated successfully.
Changing password for user user03.
passwd: all authentication tokens updated successfully.
Changing password for user user04.
passwd: all authentication tokens updated successfully.
Changing password for user user05.
passwd: all authentication tokens updated successfully.
Changing password for user user06.
passwd: all authentication tokens updated successfully.
Changing password for user user07.
passwd: all authentication tokens updated successfully.
Changing password for user user08.
passwd: all authentication tokens updated successfully.
Changing password for user user09.
passwd: all authentication tokens updated successfully.
Changing password for user user10.
passwd: all authentication tokens updated successfully.
Changing password for user user11.
passwd: all authentication tokens updated successfully.
Changing password for user user12.
passwd: all authentication tokens updated successfully.
Changing password for user user13.
passwd: all authentication tokens updated successfully.
Changing password for user user14.
passwd: all authentication tokens updated successfully.
Changing password for user user15.
passwd: all authentication tokens updated successfully.
Changing password for user user16.
passwd: all authentication tokens updated successfully.
Changing password for user user17.
passwd: all authentication tokens updated successfully.
Changing password for user user18.
passwd: all authentication tokens updated successfully.
Changing password for user user19.
passwd: all authentication tokens updated successfully.
Changing password for user user20.
passwd: all authentication tokens updated successfully.
提取上述用户在/etc/passwd及/etc/group中的信息至临时文件
[root@ldap-server ~]# mkdir /tmp/ldap
[root@ldap-server ~]# cat /etc/passwd | grep -E 'user[0-9]{2}' > /tmp/ldap/passwd
[root@ldap-server ~]# cat /etc/group | grep -E 'teacher|student' > /tmp/ldap/group
[root@ldap-server ~]# cat /tmp/ldap/passwd
user01:x:503:2000::/home/ldapuser/user01:/bin/bash
user02:x:504:2000::/home/ldapuser/user02:/bin/bash
user03:x:505:2000::/home/ldapuser/user03:/bin/bash
user04:x:506:2000::/home/ldapuser/user04:/bin/bash
user05:x:507:2000::/home/ldapuser/user05:/bin/bash
user06:x:508:2000::/home/ldapuser/user06:/bin/bash
user07:x:509:2000::/home/ldapuser/user07:/bin/bash
user08:x:510:2000::/home/ldapuser/user08:/bin/bash
user09:x:511:2000::/home/ldapuser/user09:/bin/bash
user10:x:512:2000::/home/ldapuser/user10:/bin/bash
user11:x:513:3000::/home/ldapuser/user11:/bin/bash
user12:x:514:3000::/home/ldapuser/user12:/bin/bash
user13:x:515:3000::/home/ldapuser/user13:/bin/bash
user14:x:516:3000::/home/ldapuser/user14:/bin/bash
user15:x:517:3000::/home/ldapuser/user15:/bin/bash
user16:x:518:3000::/home/ldapuser/user16:/bin/bash
user17:x:519:3000::/home/ldapuser/user17:/bin/bash
user18:x:520:3000::/home/ldapuser/user18:/bin/bash
user19:x:521:3000::/home/ldapuser/user19:/bin/bash
user20:x:522:3000::/home/ldapuser/user20:/bin/bash
[root@ldap-server ~]# cat /tmp/ldap/group
teacher:x:2000:
student:x:3000:
安装migrationtools工具生成相应的ldap信息文件
[root@ldap-server ~]# yum install migrationtools -y
修改/usr/share/migrationtools/migrate_common.ph文件第71和74行信息为自己对应的域名信息,如下图所示
通过migrate_bash.pl生成帐号基础信息文件
通过migrate_passwd.pl和/tmp/ldap/passwd文件生成用户信息文件
通过migrate_group.pl和/tmp/ldap/group文件生成用户信息文件
[root@ldap-server ~]# /usr/share/migrationtools/migrate_base.pl > /tmp/ldap/base.ldif
[root@ldap-server ~]# /usr/share/migrationtools/migrate_passwd.pl /tmp/ldap/passwd > /tmp/ldap/passwd.ldif
[root@ldap-server ~]# /usr/share/migrationtools/migrate_group.pl /tmp/ldap/group > /tmp/ldap/group.ldif
[root@ldap-server ~]# head /tmp/ldap/base.ldif
dn: dc=rocshen,dc=com
dc: rocshen
objectClass: top
objectClass: domain
dn: ou=Hosts,dc=rocshen,dc=com
ou: Hosts
objectClass: top
objectClass: organizationalUnit
[root@ldap-server ~]# head /tmp/ldap/passwd.ldif
dn: uid=user01,ou=People,dc=rocshen,dc=com
uid: user01
cn: user01
objectClass: account
objectClass: posixAccount
objectClass: top
objectClass: shadowAccount
userPassword: {crypt}$6$x9KqVO4x$mZnoUe483eR2X4E8YIfFxWenrWM8IAkyL5TeNomYItsfE7WoMiMhEiKOEySBAPYmqmXqg4G0zzPEuXQ03IvJ4/
shadowLastChange: 17541
shadowMin: 0
[root@ldap-server ~]# head /tmp/ldap/group.ldif
dn: cn=teacher,ou=Group,dc=rocshen,dc=com
objectClass: posixGroup
objectClass: top
cn: teacher
userPassword: {crypt}x
gidNumber: 2000
dn: cn=student,ou=Group,dc=rocshen,dc=com
objectClass: posixGroup
objectClass: top
[root@ldap-server ~]#
通过ldapadd命令添加上述生成的信息,主要用过下述参数;其中-D 参数即为/etc/openldap/slapd.conf中定义的rootdn信息
-w password 中的password为上述使用slappasswd命令时的明文密码(能从命令行看见),不能与-W同时使用
-W 后不跟参数密码在敲下命令后根据提示输入(别人看不见),不能与-w同时使用
-x 使用不加密的协议与ldap服务端通信
-X 使用加密的协议与ldap服务端通信
-f 指定要添加的ldif文件路径
[root@ldap-server ~]# ldapadd --help
......
-D binddn bind DN
-f file read operations from `file'
-w passwd bind password (for simple authentication)
-W prompt for bind password
-x Simple authentication
-X authzid SASL authorization identity ("dn:" or "u:")
......
[root@ldap-server ~]# ldapadd -x -D "cn=Manager,dc=rocshen,dc=com" -w 123456 -f /tmp/ldap/base.ldif
adding new entry "dc=rocshen,dc=com"
adding new entry "ou=Hosts,dc=rocshen,dc=com"
adding new entry "ou=Rpc,dc=rocshen,dc=com"
adding new entry "ou=Services,dc=rocshen,dc=com"
adding new entry "nisMapName=netgroup.byuser,dc=rocshen,dc=com"
adding new entry "ou=Mounts,dc=rocshen,dc=com"
adding new entry "ou=Networks,dc=rocshen,dc=com"
adding new entry "ou=People,dc=rocshen,dc=com"
adding new entry "ou=Group,dc=rocshen,dc=com"
adding new entry "ou=Netgroup,dc=rocshen,dc=com"
adding new entry "ou=Protocols,dc=rocshen,dc=com"
adding new entry "ou=Aliases,dc=rocshen,dc=com"
adding new entry "nisMapName=netgroup.byhost,dc=rocshen,dc=com"
[root@ldap-server ~]# ldapadd -x -D "cn=Manager,dc=rocshen,dc=com" -w 123456 -f /tmp/ldap/passwd.ldif
adding new entry "uid=user01,ou=People,dc=rocshen,dc=com"
adding new entry "uid=user02,ou=People,dc=rocshen,dc=com"
adding new entry "uid=user03,ou=People,dc=rocshen,dc=com"
adding new entry "uid=user04,ou=People,dc=rocshen,dc=com"
adding new entry "uid=user05,ou=People,dc=rocshen,dc=com"
adding new entry "uid=user06,ou=People,dc=rocshen,dc=com"
adding new entry "uid=user07,ou=People,dc=rocshen,dc=com"
adding new entry "uid=user08,ou=People,dc=rocshen,dc=com"
adding new entry "uid=user09,ou=People,dc=rocshen,dc=com"
adding new entry "uid=user10,ou=People,dc=rocshen,dc=com"
adding new entry "uid=user11,ou=People,dc=rocshen,dc=com"
adding new entry "uid=user12,ou=People,dc=rocshen,dc=com"
adding new entry "uid=user13,ou=People,dc=rocshen,dc=com"
adding new entry "uid=user14,ou=People,dc=rocshen,dc=com"
adding new entry "uid=user15,ou=People,dc=rocshen,dc=com"
adding new entry "uid=user16,ou=People,dc=rocshen,dc=com"
adding new entry "uid=user17,ou=People,dc=rocshen,dc=com"
adding new entry "uid=user18,ou=People,dc=rocshen,dc=com"
adding new entry "uid=user19,ou=People,dc=rocshen,dc=com"
adding new entry "uid=user20,ou=People,dc=rocshen,dc=com"
[root@ldap-server ~]# ldapadd -x -D "cn=Manager,dc=rocshen,dc=com" -w 123456 -f /tmp/ldap/group.ldif
adding new entry "cn=teacher,ou=Group,dc=rocshen,dc=com"
adding new entry "cn=student,ou=Group,dc=rocshen,dc=com"
通过ldapsearch查询ldap中的用户组信息
[root@ldap-server ~]# ldapsearch -b "ou=Group,dc=rocshen,dc=com" -x
# extended LDIF
#
# LDAPv3
# base with scope subtree
# filter: (objectclass=*)
# requesting: ALL
#
# Group, rocshen.com
dn: ou=Group,dc=rocshen,dc=com
ou: Group
objectClass: top
objectClass: organizationalUnit
# teacher, Group, rocshen.com
dn: cn=teacher,ou=Group,dc=rocshen,dc=com
objectClass: posixGroup
objectClass: top
cn: teacher
userPassword:: e2NyeXB0fXg=
gidNumber: 2000
# student, Group, rocshen.com
dn: cn=student,ou=Group,dc=rocshen,dc=com
objectClass: posixGroup
objectClass: top
cn: student
userPassword:: e2NyeXB0fXg=
gidNumber: 3000
# search result
search: 2
result: 0 Success
# numResponses: 4
# numEntries: 3
安装nfs设置ldap用户家目录为共享
[root@ldap-server ~]# yum install nfs-utils -y
[root@ldap-server ~]# cat /etc/exports
/home/ldapuser *(rw,no_root_squash)
[root@ldap-server ~]# service rpcbind start
Starting rpcbind: [ OK ]
[root@ldap-server ~]# service nfs start
Starting NFS services: [ OK ]
Starting NFS quotas: [ OK ]
Starting NFS mountd: [ OK ]
Starting NFS daemon: [ OK ]
[root@ldap-server ~]# chkconfig nfs on
[root@ldap-server ~]# chkconfig rpcbind on
ldap客户端安装与配置
安装openldap客户端软件包并配置/etc/openldap/ldap.conf
[root@ldap-client ~]# yum install openldap-clients nss-pam-ldapd pam_ldap -y
[root@ldap-client ~]# vim /etc/openldap/ldap.conf
#
# LDAP Defaults
#
# See ldap.conf(5) for details
# This file should be world readable but not world writable.
#BASE dc=example,dc=com
#URI ldap://ldap.example.com ldap://ldap-master.example.com:666
BASE dc=rocshen,dc=com
URI ldap://10.59.30.94 #此处为ldap服务端ip
#SIZELIMIT 12
#TIMELIMIT 15
#DEREF never
TLS_CACERTDIR /etc/openldap/certs
测试搜索ldap中的用户组信息
[root@ldap-client ~]# ldapsearch -h 10.59.30.94 -x -b "ou=Group,dc=rocshen,dc=com"
# extended LDIF
#
# LDAPv3
# base with scope subtree
# filter: (objectclass=*)
# requesting: ALL
#
# Group, rocshen.com
dn: ou=Group,dc=rocshen,dc=com
ou: Group
objectClass: top
objectClass: organizationalUnit
# teacher, Group, rocshen.com
dn: cn=teacher,ou=Group,dc=rocshen,dc=com
objectClass: posixGroup
objectClass: top
cn: teacher
userPassword:: e2NyeXB0fXg=
gidNumber: 2000
# student, Group, rocshen.com
dn: cn=student,ou=Group,dc=rocshen,dc=com
objectClass: posixGroup
objectClass: top
cn: student
userPassword:: e2NyeXB0fXg=
gidNumber: 3000
# search result
search: 2
result: 0 Success
# numResponses: 4
# numEntries: 3
配置客户端启动ldap验证
配置/etc/sysconfig/authconfig
[root@ldap-client ~]# sed -i '/USESYSNETAUTH/s/no/yes/' /etc/sysconfig/authconfig
[root@ldap-client ~]# sed -i '/USELDAPAUTH/s/no/yes/' /etc/sysconfig/authconfig
[root@ldap-client ~]# sed -i '/USEMKHOMEDIR/s/no/yes/' /etc/sysconfig/authconfig
[root@ldap-client ~]# sed -i '/PASSWDALGORITHM/s/md5/yes/' /etc/sysconfig/authconfig
[root@ldap-client ~]# sed -i '/USELDAP/s/no/yes/' /etc/sysconfig/authconfig
配置/etc/nsswitch.conf,如下图所示
配置pam新增ldap认证
[root@ldap-client ~]# vim /etc/pam.d/system-auth
#%PAM-1.0
# This file is auto-generated.
# User changes will be destroyed the next time authconfig is run.
auth required pam_env.so
auth sufficient pam_fprintd.so
auth sufficient pam_unix.so nullok try_first_pass
auth requisite pam_succeed_if.so uid >= 500 quiet
auth sufficient pam_ldap.so
auth required pam_deny.so
account required pam_unix.so
account sufficient pam_localuser.so
account sufficient pam_succeed_if.so uid < 500 quiet
account [default=bad success=ok user_unknown=ignore] pam_ldap.so
account required pam_permit.so
password requisite pam_cracklib.so try_first_pass retry=3 type=
password sufficient pam_unix.so sha512 shadow nullok try_first_pass use_authtok
password sufficient pam_ldap.so use_authtok
password required pam_deny.so
session optional pam_keyinit.so revoke
session required pam_limits.so
session [success=1 default=ignore] pam_succeed_if.so service in crond quiet use_uid
session required pam_unix.so
session required pam_mkhomedir.so skel=/etc/skel/ umask=0077
session optional pam_ldap.so
使用autoconfig命令配置nscd服务,注意替换命令中的ldapserver的IP及basedb信息
[root@ldap-client ~]# authconfig --enableldap --enableldapauth --ldapserver=10.59.30.94 --ldapbasedn="dc=rocshen,dc=com" --enablemkhomedir --update
Starting nslcd: [ OK ]
[root@ldap-client ~]#
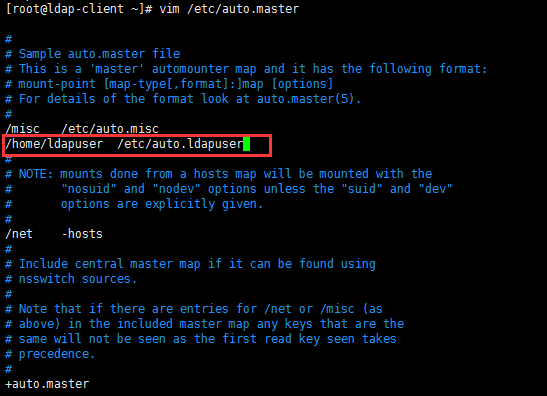
安装autofs挂载ldapserver端的用户目录;按图示操作添加相关配置
[root@ldap-client ~]# yum install autofs -y
[root@ldap-client ~]# vim /etc/auto.master
#
# Sample auto.master file
# This is a 'master' automounter map and it has the following format:
# mount-point [map-type[,format]:]map [options]
# For details of the format look at auto.master(5).
#
/misc /etc/auto.misc
/home/ldapuser /etc/auto.ldapuser
#
# NOTE: mounts done from a hosts map will be mounted with the
# "nosuid" and "nodev" options unless the "suid" and "dev"
# options are explicitly given.
#
/net -hosts
#
# Include central master map if it can be found using
# nsswitch sources.
#
# Note that if there are entries for /net or /misc (as
# above) in the included master map any keys that are the
# same will not be seen as the first read key seen takes
# precedence.
#
+auto.master[root@ldap-client ~]# vim /etc/auto.ldapuser
* -rw,soft,intr 10.59.30.94:/home/ldapuser/&
[root@ldap-client ~]# service autofs start
Loading autofs4: [ OK ]
Starting automount: [ OK ]
[root@ldap-client ~]# ls /home/ldapuser/
[root@ldap-client ~]# cd /home/ldapuser/user01
[root@ldap-client user01]# pwd
/home/ldapuser/user01
[root@ldap-client ~]#
测试使用ldapuser登录
[root@ldap-client user01]# cd
[root@ldap-client ~]#
[root@ldap-client ~]# ssh user01@localhost
Warning: Permanently added 'localhost' (RSA) to the list of known hosts.
user01@localhost's password:
[user01@ldap-client ~]$ id
uid=503(user01) gid=2000(teacher) groups=2000(teacher)
[user01@ldap-client ~]$exit
[root@ldap-client ~]# getent passwd | grep user
saslauth:x:499:76:"Saslauthd user":/var/empty/saslauth:/sbin/nologin
rpcuser:x:29:29:RPC Service User:/var/lib/nfs:/sbin/nologin
user01:x:503:2000:user01:/home/ldapuser/user01:/bin/bash
user02:x:504:2000:user02:/home/ldapuser/user02:/bin/bash
user03:x:505:2000:user03:/home/ldapuser/user03:/bin/bash
user04:x:506:2000:user04:/home/ldapuser/user04:/bin/bash
user05:x:507:2000:user05:/home/ldapuser/user05:/bin/bash
user06:x:508:2000:user06:/home/ldapuser/user06:/bin/bash
user07:x:509:2000:user07:/home/ldapuser/user07:/bin/bash
user08:x:510:2000:user08:/home/ldapuser/user08:/bin/bash
user09:x:511:2000:user09:/home/ldapuser/user09:/bin/bash
user10:x:512:2000:user10:/home/ldapuser/user10:/bin/bash
user11:x:513:3000:user11:/home/ldapuser/user11:/bin/bash
user12:x:514:3000:user12:/home/ldapuser/user12:/bin/bash
user13:x:515:3000:user13:/home/ldapuser/user13:/bin/bash
user14:x:516:3000:user14:/home/ldapuser/user14:/bin/bash
user15:x:517:3000:user15:/home/ldapuser/user15:/bin/bash
user16:x:518:3000:user16:/home/ldapuser/user16:/bin/bash
user17:x:519:3000:user17:/home/ldapuser/user17:/bin/bash
user18:x:520:3000:user18:/home/ldapuser/user18:/bin/bash
user19:x:521:3000:user19:/home/ldapuser/user19:/bin/bash
user20:x:522:3000:user20:/home/ldapuser/user20:/bin/bash
[root@ldap-client ~]# getent group | grep -E 'teacher|student'
teacher:x:2000:
student:x:3000:
[root@ldap-client ~]# cat /etc/group | grep -E 'teacher|student'
[root@ldap-client ~]# cat /etc/passwd | grep user
saslauth:x:499:76:"Saslauthd user":/var/empty/saslauth:/sbin/nologin
rpcuser:x:29:29:RPC Service User:/var/lib/nfs:/sbin/nologin
[root@ldap-client ~]#