上一篇中防火墙上下行业务口工作在二层,VGMP可以通过VRRP来监控接口状态。那么如果上下行接口工作在三层,那么VGMP显然不能通过VRRP来监控接口状态此时就需要VGMP直接监控接口状态。
实验拓扑
环境描述
全网运行OSPF宣告在区域0中,将FW1和FW2的G0/0/0的接口加入到VRRP 1中,G0/0/1接口加入到DMZ区域G0/0/2接口加入到untrust区域。
IP地址:R1 loopback:1.1.1.1/32
R2 loopback:2.2.2.2/32
FW1 loopback:100.100.100.100/32
FW2 loopback:200.200.200.200/32
由于主要讲防火墙所以IP地址和OSPF配置省略
FW1配置
-----------------------------将接口加入对应的区域----------------------------
[FW1]firewall zone trust
[FW1-zone-trust]add int g0/0/0
[FW1-zone-trust]quit
[FW1]firewall zone dmz
[FW1-zone-dmz]add int g0/0/1
[FW1-zone-dmz]quit
[FW1]firewall zone untrust
[FW1-zone-untrust]add int g0/0/2
[FW1-zone-untrust]quit
------------------------------------配置接口IP-------------------------------
[FW1]int g0/0/0
[FW1-GigabitEthernet0/0/0]ip add 11.0.0.1 24
[FW1-GigabitEthernet0/0/0]int g0/0/1
[FW1-GigabitEthernet0/0/1]ip add 10.10.10.1 24
[FW1-GigabitEthernet0/0/1]int g0/0/2
[FW1-GigabitEthernet0/0/2]ip add 13.0.0.1 24
[FW1-GigabitEthernet0/0/2]quit
[FW1-LoopBack0]ip add 100.100.100.100 32
[FW1-LoopBack0]quit
---------------------------配置OSPF------------------------------------------------
[FW1]ospf 1 router-id 100.100.100.100
[FW1-ospf-1]area 0
[FW1-ospf-1-area-0.0.0.0]network 100.100.100.100 0.0.0.0
[FW1-ospf-1-area-0.0.0.0]network 11.0.0.0 0.0.0.255
[FW1-ospf-1-area-0.0.0.0]network 13.0.0.0 0.0.0.255
[FW1-ospf-1-area-0.0.0.0]quit
[FW1-ospf-1]quit
----------------------------配置区域间策略--------------------------------------------
[FW1]policy interzone local untrust inbound
[FW1-policy-interzone-local-untrust-inbound]policy 1
[FW1-policy-interzone-local-untrust-inbound-1]policy source 192.168.20.0 0.0.0.255
[FW1-policy-interzone-local-untrust-inbound-1]action permit
[FW1-policy-interzone-local-untrust-inbound-1]quit
[FW1-policy-interzone-local-untrust-inbound]quit
[FW1]policy interzone trust untrust outbound
[FW1-policy-interzone-trust-untrust-outbound]policy 1
[FW1-policy-interzone-trust-untrust-outbound-1]action permit
[FW1-policy-interzone-trust-untrust-outbound-1]quit
[FW1-policy-interzone-trust-untrust-outbound]quit
----------------------------配置双机热备-------------------------------------------
[FW1]hrp enable //开启HRP功能
[FW1]hrp mirror session enable //开启会话快速备份
[FW1]hrp int g0/0/1 //指定心跳接口
[FW1-GigabitEthernet0/0/2]hrp track master //配置VGMP监听端口并配置为主
HRP_M[FW1-GigabitEthernet0/0/2]int g0/0/1
HRP_M[FW1-GigabitEthernet0/0/1]hrp track master
FW2配置
[FW2]firewall zone trust
[FW2-zone-trust]add int g0/0/0
[FW2-zone-trust]quit
[FW2]firewall zone dmz
[FW2-zone-dmz]add int g0/0/1
[FW2-zone-dmz]quit
[FW2]firewall zone untrust
[FW2-zone-untrust]add int g0/0/2
[FW2-zone-untrust]quit
[FW2]int g0/0/0
[FW2-GigabitEthernet0/0/0]ip add 12.0.0.1 24
[FW2-GigabitEthernet0/0/0]int g0/0/1
[FW2-GigabitEthernet0/0/1]ip add 10.10.10.2 24
[FW2-GigabitEthernet0/0/1]int g0/0/2
[FW2-GigabitEthernet0/0/2]ip add 22.0.0.1 24
[FW2-GigabitEthernet0/0/2]quit
[FW2]int loo 0
[FW2-LoopBack0]ip add 200.200.200.200 32
[FW2-LoopBack0]quit
[FW2]ospf 1 router-id 200.200.200.200
[FW2-ospf-1]area 0
[FW2-ospf-1-area-0.0.0.0]net 200.200.200.200 0.0.0.0
[FW2-ospf-1-area-0.0.0.0]net 12.0.0.0 0.0.0.255
[FW2-ospf-1-area-0.0.0.0]net 22.0.0.0 0.0.0.255
[FW2-ospf-1-area-0.0.0.0]quit
[FW2-ospf-1]quit
[FW2]policy interzone trust untrust outbound
[FW2-policy-interzone-trust-untrust-outbound]policy 1
[FW2-policy-interzone-trust-untrust-outbound-1]action permit
[FW2-policy-interzone-trust-untrust-outbound-1]quit
[FW2-policy-interzone-trust-untrust-outbound]quit
[FW2]policy interzone local untrust inbound
[FW2-policy-interzone-local-untrust-inbound]policy 1
[FW2-policy-interzone-local-untrust-inbound-1]policy source 192.168.20.0 0.0.0.255
[FW2-policy-interzone-local-untrust-inbound-1]action permit
[FW2-policy-interzone-local-untrust-inbound-1]quit
[FW2-policy-interzone-local-untrust-inbound]quit
[FW2]hrp enable
[FW2]hrp mirror session enable
[FW2]hrp auto-sync
[FW2]hrp int g0/0/1
HRP_S[FW2-GigabitEthernet0/0/0]hrp track slave
HRP_S[FW2-GigabitEthernet0/0/0]hrp track
HRP_S[FW2-GigabitEthernet0/0/0]int g0/0/2
HRP_S[FW2-GigabitEthernet0/0/2]hrp track slave
HRP_S[FW2-GigabitEthernet0/0/2]quit
由于在这个图中R1学习R2的路由开销都是一样的,所以默认学到的R1的路由都会负载均衡(如图)。这样会出现数据包来回路径不一致的问题,解决这个问题有2种办法一种是手动修改R1和R2的cost值还一种是通过配置防火墙来动态的修改OSPF的cost值。
修改前的路由表
通过修改防火墙的配置来动态调整cost值
在FW1和FW2上分别加入这条命令
HRP_M[FW1]hrp ospf-cost adjust-enable //动态调整OSPF值,默认情况下备用设备的COST值将自动修改为65500
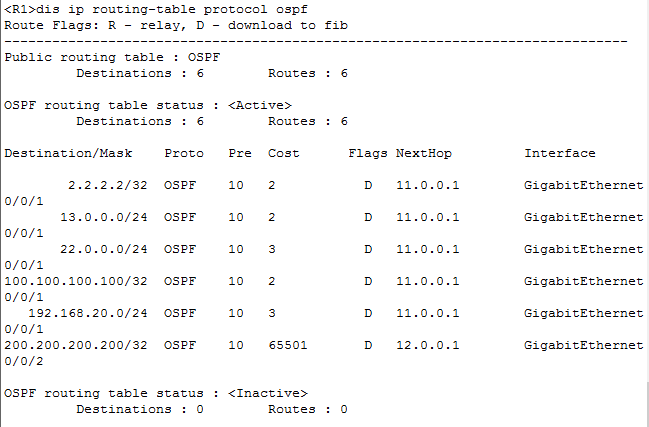
修改后的路由表
会发现所有到R2的流量都走FW1走,到FW2的流量cost都为65501
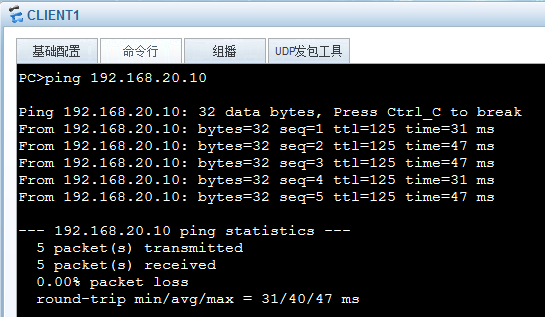
流量测试
C1 ping C2
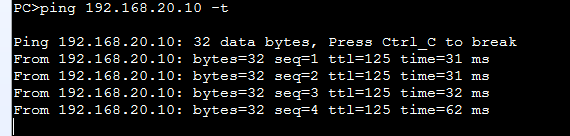
流量倒换测试
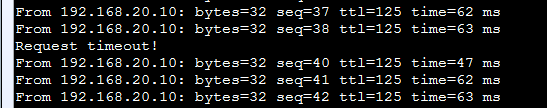
关闭FW1上行口
会发现丢了一个包后业务恢复正常
总结:和上下行连接交换机相比,网关不用在做在防火墙上了,防火墙上只是做了一个会话的快速备份。
![_Q%54(Q96TY3~7]4}U}Z57G.png 华为USG防火墙双机热备(业务口工作在三层上下行连接路由器)_第1张图片](http://img.e-com-net.com/image/info3/83a22b35c7254902b89c13c157a1ca8e.jpg)
![76]GO1LGSD9([TXOQTS83M6.png 华为USG防火墙双机热备(业务口工作在三层上下行连接路由器)_第2张图片](http://img.e-com-net.com/image/info3/d3de6ac156b74a458ece437b82fa50c3.png)