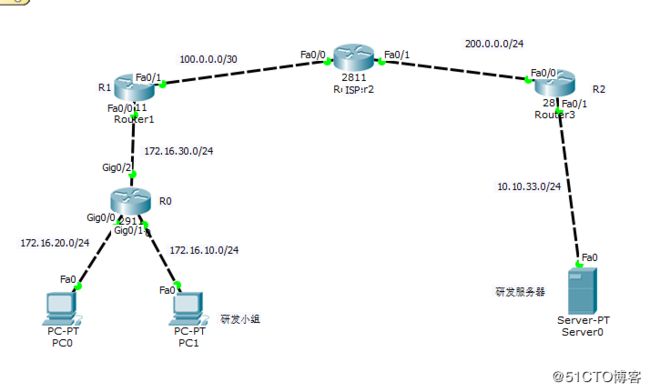
实验:某软件公司在中小城市建立分公司,分支公司开发项目小组所网络地址为
172.16.10.0/24 该网络主机可以通过×××访问总公司开发数据服务器
(10.10.33.0/24)
![]()
思路与配置:
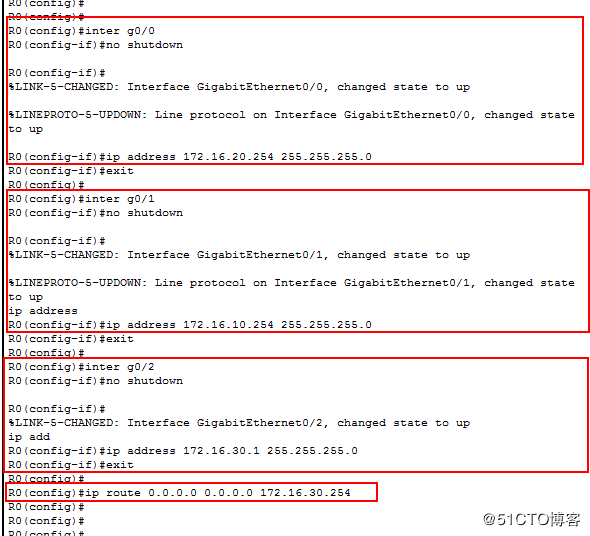
1.配置R0:
0端口ip:172.16.20.254 255.255.255.0
1端口ip:172.16.10.254 255.255.255.0
2端口ip:172.16.30.1 255.255.255.0
配置默认路由
ip route 0.0.0.0 0.0.0.0 172.16 30.254
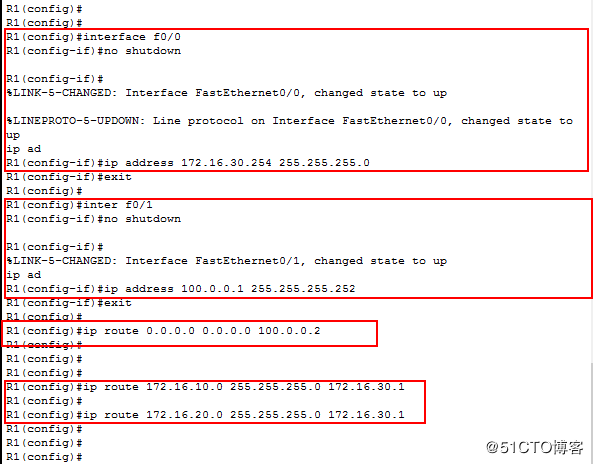
2.配置R1:
0端口ip:172.16.30.254 255.255.255.0
1端口ip:100.0.0.1 255.255.255.252
配置默认路由
ip route 0.0.0.0 0.0.0.0 100.0.0.2
配置静态路由
ip route 172.16.10.0 255.255.255. 0 172.16.30.1
ip route 172.16.20.0 255.255.255. 0 172.16.30.1
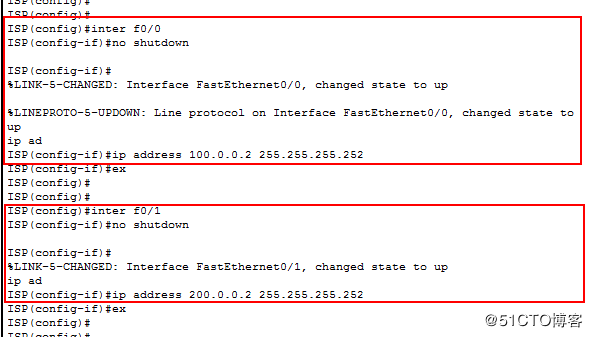
3.配置ISP:
0端口ip:100.0.0.2 255.255.255.252
1端口ip:200.0.0.2 255.255.255.252
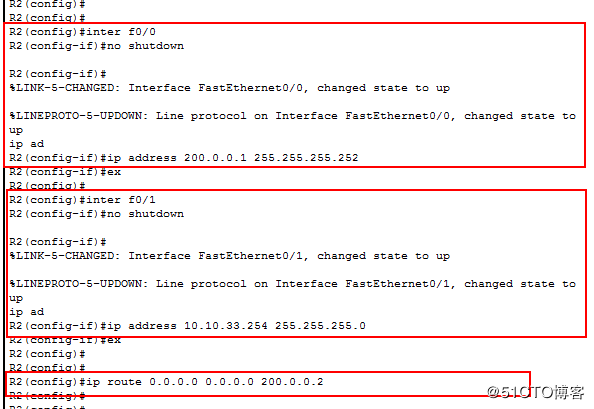
4.配置R2:
0端口ip:200.0.0.1 255.255.255.252
1端口ip:10.10.33.254 255.255.255.0
配置默认路由
ip route 0.0.0.0 0.0.0.0 200.0.0.2
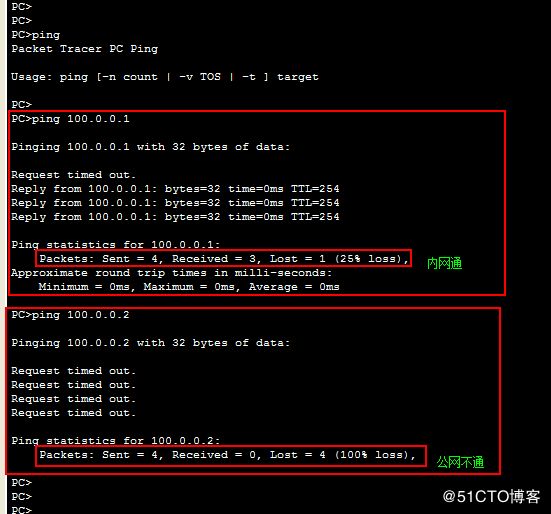
5.此时pc机只能ping到R1 而不能到达外网
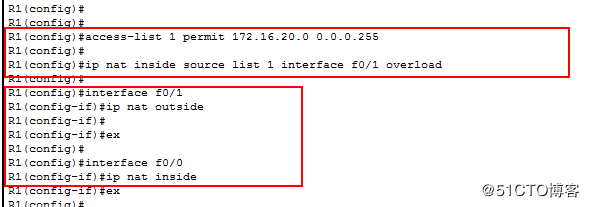
在R1上配置NAT 使pc0可以访问外网
access-list 1 permit 172.16.20.0 0.0.0.255
ip nat inside sourse list 1 interface f0/1 overload
interface f0/1
ip nat outside
interface f0/0
ip nat inside
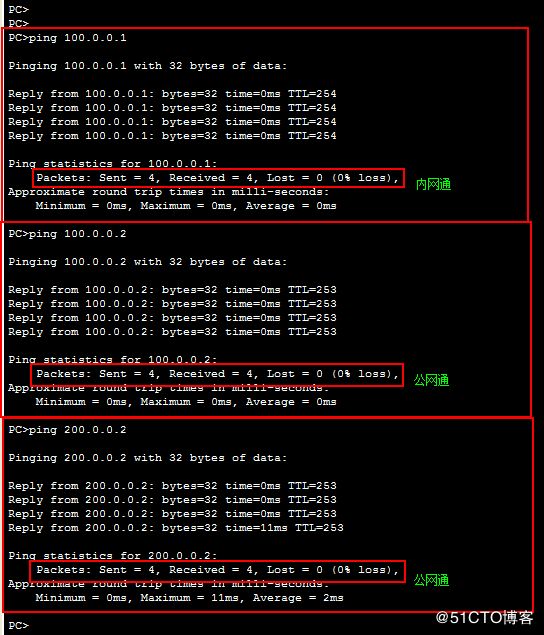
此时pc0可以访问外网 即 ping同外网
6.在R1和R2上配置××× 是研发小组可以ping 通研发服务器
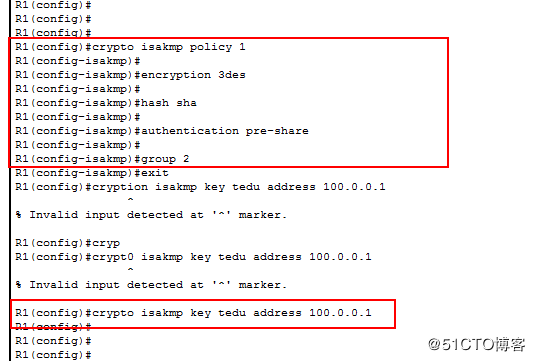
配置R1
配置ISKMP策略
cryption isakmp policy 1
encryption 3des
hash sha
authentication pre-share
group 2
cryption isakmp key tedu address 200.0.0.1
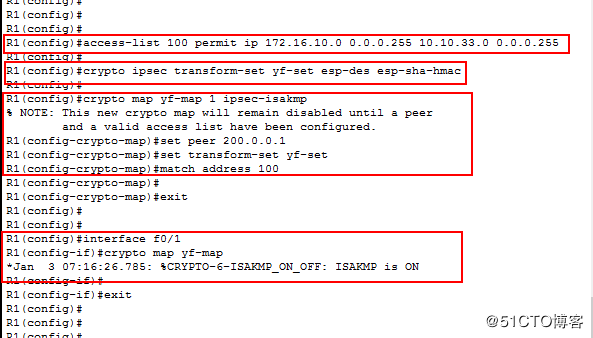
配置ACL
access-list 100 permit ip 176.16.10.0 0.0.0.255 10.10.33.0 0.0.0.255
配置IPsec策略(转换集)
crypto ipsec transform-set yf-set esp-des esp-sha-hmac
配置加密映像集
crypto map yf-map 1 ipsec-isakmp
set peer 200.0.0.1
set transform-set yf-set
match address 100
将映射集应用在接口
interface f0/1
crypto map yf-map
![]()
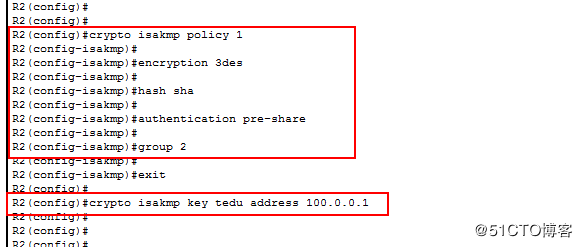
配置R2
配置ISKMP策略
cryption isakmp policy 1
encryption 3des
hash sha
authentication pre-share
group 2
crypto isakmp key tedu address 100.0.0.1
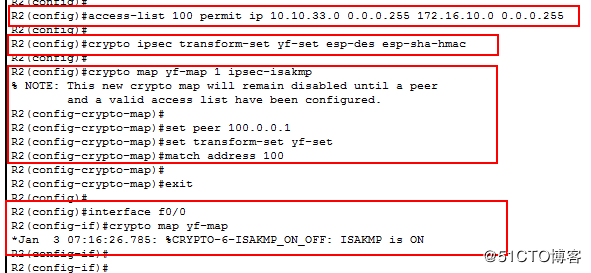
配置ACL
access-list 100 permit ip 10.10.33.0 0.0.0.255 172.16.10.0 0.0.0.255
配置IPsec策略(转换集)
crypto ipsec transform-set yf-set esp-des esp-sha-hmac
配置加密映像集
crypto map yf-map 1 ipsec-isakmp
set peer 100.0.0.1
set transform-set yf-set
match address 100
将映射集应用在接口
interface f0/0
crypto map yf-map
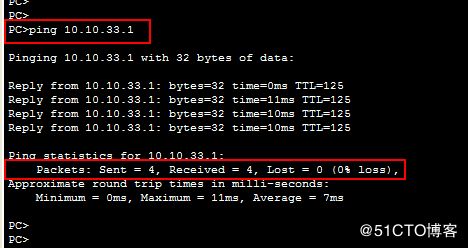
此时pc1研发小组 可以 ping 通 server0研发服务器
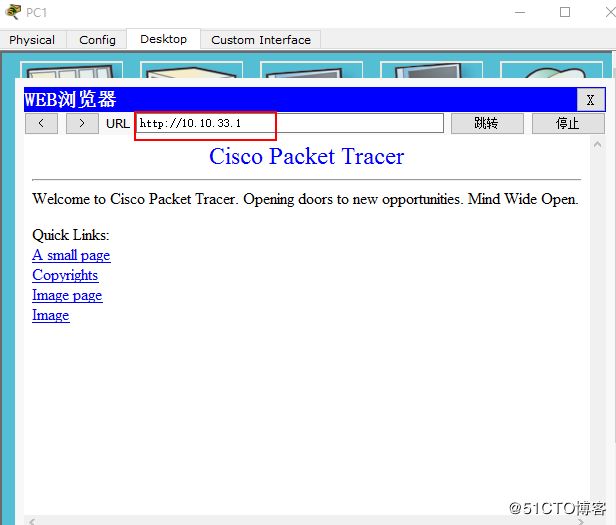
此时pc1研发小组 可以 访问 server0研发服务器的web
==========================================================
1.流量走PAT 不走×××
配置R1
accecc-list 1 permit 172.16.10.0 0.0.0.255
ip nat inside source list 1 interface f0/1 overload
interface f0/1
ip nat outside
interface f0/0
ip nat inside
2.流量可以走PAT, 也可以走×××
配置R1
access-list 110 deny ip 172.16.10.0 0.0.0.255 10.10.33.0 0.0.0.255
access-list 110 permit ip any any
ip nat inside source list 110 interface f0/1 overload
interface f0/1
ip nat outside
interface f0/0
ip nat inside