DES 算法实现
DES 算法实现
一、DES算法原理概述
DES算法是一种对称加密算法,这种特性使得,利用明文和密钥,我们加密一次能得到密文,然后利用密文和密钥再次经过DES加密,得到原文。
简要介绍对称加密算法。一个对称加密由明文(原始信息或数据,作为算法的输入)、 加密算法(对明文进行各种替换和转换)、 密钥(算法的另一个输入,决定算法进行的具体替换和转换)、 密文(已被打乱的消息输出)、 解密算法(加密算法的反向执行)5部分组成。
算法首先需要两样数据,一个是64位bits的明文Plain_Text,另一个是64位bits的密钥Key_64。在选定密钥的情况下,我们就能通过DES算法加密明文了。下面详细介绍DES的加密步骤。
1.第一步:IP置换。我们已有一个公开确定的IP矩阵,它是一个大小为64,里面的数据分别是1到64的矩阵,用来初步混淆明文。原理是让明文的每一位对应上IP矩阵的每一位,取其中的数据作为新的下标,重新排列得到一串64位长的数据M0。这里提醒,整个算法过程用到的矩阵的里面存的下标都是从一开始的,并不是我们熟悉的从0开始。
2.第二步:T迭代。这是整套算法里最关键的部分,里面会有多种处理手法。首先将上一步得到的M0断开成两个32位长的串L和R。然后将L和R经过16轮的迭代。其中每轮的L会重新赋值为上一轮的R,而R则会赋值为上一轮的L 异或上 Feistel函数返回值的值。
3.接下来顺势详细谈谈Feistel函数。它接收两个参数,一个是上一轮迭代而来的32位长的R,一个是后面会提到的48位长的子密钥Key_Sub。先要扩展32位的R到48位的E_R,用于与Key_Sub异或得到一个命名为result的48位长变量。然后result每连续6位就经过一次S_Box映射,每次都从6位压缩成4位。这样的映射会循环8次,那么最后映射结果连起来,又得到一个32位长的串F_S。将F_S经过一次P置换得到F_P。最后它会返回32位长的F_P用于赋值给下一轮的R。
4.上面提到的扩展32位的R到48位的E_R,用的是大小为48的矩阵E,里面存着对应R的下标,类似前面的置换过程。这也是一个公开确定的矩阵。
5.上面提到的S_Box映射,用的是8个给定的大小为4*16的矩阵S_Box,里面存的每一个元素都是能用4位二进制表示的数。这是一系列公开确定的矩阵,这也是整个算法里最让人摸不清的地方。但是我们先这样用吧。我们将上面的result每连续6位取出,分别表示为b1b2b3b4b5b6,然后令行号row=b1b6,列号col=b2b3b4b5,这样刚好能从一个S_Box中确定出一个4位长的数据。这样的过程会循环8次,分别从不同S_Box中得到一个4位数据,连接起来就得到了32位长的F_S。
6.上面提到的P置换,用的是大小为32的矩阵P,同样存着新的下标,同样类似前面的置换过程。这也是一个公开确定的矩阵。
7.T迭代的最后,我们再将最终的32位的L和R换个位置,存进一个64位长的变量RL里并返回RL,才结束这一步。
8.第三步,也就是加密过程的最后一步,IP逆置换。同样,我们给定了IP的逆矩阵,然后模仿第一步再做一次一样的映射,我们就得到密文Cipher_Text了。这一步看似简陋不必要,但其实是为了维护DES算法的对称性。只有保持了对称性,我们才能利用密文和密钥经过又一轮加密从而解密得到原文。
9.然后就要谈谈16个48位长的Key_Sub的产生了。64位密钥的先要经过一轮PC_1置换,得到56位的Key_56,然后将其分成左右各28位的C和D。对C和D按规则进行16轮的循环左移,每次得到的结果拼接回Key_56,然后进行PC_2置换得到48位的串,即一个Key_Sub。这16个Key_Sub在加密过程中分别用于上述的16次的T迭代,而在解密过程中,顺序需要反过来才能正确解密。
10.上面提到的PC_1置换和PC_2置换也是类似上面的映射,只不过PC_1置换是64位压缩为56位,PC_2置换是56位再映射成48位。PC_1矩阵和PC_2矩阵也已给出。
二、总体结构
下面开始介绍我对这个算法的实现。实现用的是C++,原因有二。一是我打算用面向对象将DES算法封装成一个类,用一个密钥创建一个DES对象,并只对外提供加密和解密两个函数接口。其余的实现细节(如用到的矩阵、T迭代、Feistel函数和子密钥生成等)对用户隐藏,较好地保证安全性。二是C++有bitset这个标准库,能直观地操作一个个bit,比C语言方便实现。
类DES是这次需要实现的类,我需要实现的功能很简单,给定一串64位的密钥,用密钥创建一个DES对象,提供64位的明文串,加密返回一串64位的密文,然后解密密文,使得解密结果和原文完全一致。
三、模块分解
类DES的声明放在文件”DES.h”中,并包含了静态常量的初始化。
实现的函数则放在文件”DES.cpp”中,测试用的主函数在”main.cpp”中。
首先DES的构造函数需要传入64位的bitset类型数据,赋值给私有变量Key_64,即我们后来用到的密钥。
然后DES的加密函数Encrypt和解密函数Decrypt也需要传入64位的bitset类型数据,这是分别我们需要加密的明文和需要解密的密文。
IP_Substitute函数是加密第一步的IP置换。传入的参数是明文,返回初步混淆后的64位密文。
IP_Inv_Substitute函数是加密最后一步的IP逆置换。传入T迭代后的密文,返回最终的64位密文。
T_Iteration函数是加密第一步的T迭代,传入第一步IP置换后的密文以及子密钥的引用,返回迭代后的64位密文。
Feistel函数是T迭代里用到的Feistel函数,用于将密文和密钥混合加密。
E_Expand函数是将32位的R扩展成48位的E_R。
P_Substitute函数是将32位的F_S映射为32位的F_P。
Key_64_To_56和Key_56_To_48以及Key_28_Shift_Left都是对上面所说的密钥处理拆分的过程,而函数Key_Gen调用这些函数从而得到16个48位的子密钥。
Key_Inv函数反转子密钥序列,用在解密函数当中。
四、数据结构
bitset是主要用到的数据结构,用来表示给定位数的bit串。过程中用到的矩阵如S_BOX,IP, PC_1等,用数组储存,作为DES类的静态私有常量。另外在测试用的主函数里,用到string类型的字符串来初始化bitset类型数据如明文和密钥。
类DES中我尽量不留变量,这样的话只靠函数计算并返回数值就比较安全,不容易泄露对象内的信息。但是初始化所需的密钥不能没有,所以用一个64位的bitset存着。另外子密钥序列的生成和解密所需的反转顺序的子密钥序列都能通过函数参数传引用的方法而避免用私有变量保存。故只需有一个私有变量即可。
五、C++算法过程
DES.h
#include DES.cpp
#include main.cpp
#include 六、算法运行情况
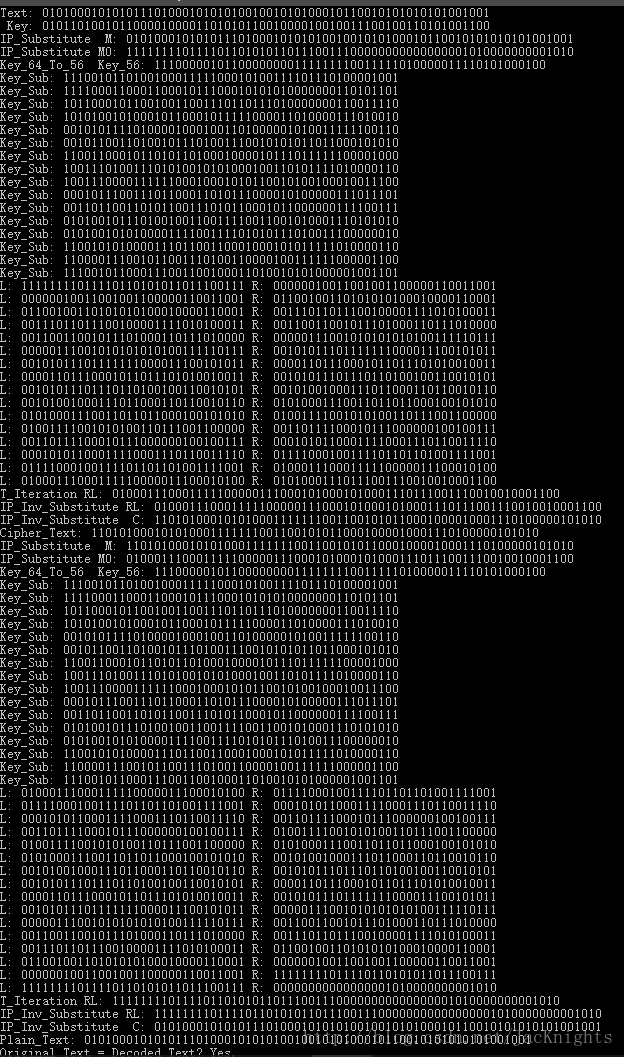
下图是运行的情况的截图以及打印的文本.
可以看到最下面两行的显示是”Plain_Text: 0101000101010111010001010101001001010100010110010101010101001001 Original Text = Decoded Text? Yes.”。这说明解密后的密文和原文匹配上了,说明DES算法成功实现了。
Text: 0101000101010111010001010101001001010100010110010101010101001001
Key: 0101101001011000010000110101011001000010010011100100110101001100
IP_Substitute M: 0101000101010111010001010101001001010100010110010101010101001001
IP_Substitute M0: 1111111101111011010101101110011100000000000000001010000000001010
Key_64_To_56 Key_56: 11100000101100000000111111110011111010000011110101000100
Key_Sub: 111001011010010001111100010100111101110100001001
Key_Sub: 111100011000110001011100010101010000000110101101
Key_Sub: 101100010110010011001110110111010000000110011110
Key_Sub: 101010010100010110001011111000011010000111010010
Key_Sub: 001010111101000010001001101000001010011111100110
Key_Sub: 001011001101001011101001110010101011011000101010
Key_Sub: 110011000101101011010001000010111011111100001000
Key_Sub: 100111010011101010010101000100110101111010000110
Key_Sub: 100111000011111100010001010110010100100010011100
Key_Sub: 000101110011101100011010111000010100000111011101
Key_Sub: 001101100110101100111010110001011000000111100111
Key_Sub: 010100101110100100110011110011001010001110101010
Key_Sub: 010100101010000111100111101010111010011100000010
Key_Sub: 110010101000011101100110001000101011111010000110
Key_Sub: 110000111001011001110100110000100111111000001100
Key_Sub: 111001011000111001100100011010010101000001001101
L: 11111111011110110101011011100111 R: 00000010011001001100000110011001
L: 00000010011001001100000110011001 R: 01100100110101010100010000110001
L: 01100100110101010100010000110001 R: 00111011011100100001111010100011
L: 00111011011100100001111010100011 R: 00110011001011101000110111010000
L: 00110011001011101000110111010000 R: 00000111001010101010100111110111
L: 00000111001010101010100111110111 R: 00101011101111111000011100101011
L: 00101011101111111000011100101011 R: 00001101110001011011101010010011
L: 00001101110001011011101010010011 R: 00101011101110110100100110010101
L: 00101011101110110100100110010101 R: 00101001000111011000110110010110
L: 00101001000111011000110110010110 R: 01010001110011011011000100101010
L: 01010001110011011011000100101010 R: 01001111001010100110111001100000
L: 01001111001010100110111001100000 R: 00110111100010111000000100100111
L: 00110111100010111000000100100111 R: 00010101100011110001110110011110
L: 00010101100011110001110110011110 R: 01111000100111101101101001111001
L: 01111000100111101101101001111001 R: 01000111000111110000011100010100
L: 01000111000111110000011100010100 R: 01010001110111001110010010001100
T_Iteration RL: 0100011100011111000001110001010001010001110111001110010010001100
IP_Inv_Substitute RL: 0100011100011111000001110001010001010001110111001110010010001100
IP_Inv_Substitute C: 1101010001010100011111110011001010110001000010001110100000101010
Cipher_Text: 1101010001010100011111110011001010110001000010001110100000101010
IP_Substitute M: 1101010001010100011111110011001010110001000010001110100000101010
IP_Substitute M0: 0100011100011111000001110001010001010001110111001110010010001100
Key_64_To_56 Key_56: 11100000101100000000111111110011111010000011110101000100
Key_Sub: 111001011010010001111100010100111101110100001001
Key_Sub: 111100011000110001011100010101010000000110101101
Key_Sub: 101100010110010011001110110111010000000110011110
Key_Sub: 101010010100010110001011111000011010000111010010
Key_Sub: 001010111101000010001001101000001010011111100110
Key_Sub: 001011001101001011101001110010101011011000101010
Key_Sub: 110011000101101011010001000010111011111100001000
Key_Sub: 100111010011101010010101000100110101111010000110
Key_Sub: 100111000011111100010001010110010100100010011100
Key_Sub: 000101110011101100011010111000010100000111011101
Key_Sub: 001101100110101100111010110001011000000111100111
Key_Sub: 010100101110100100110011110011001010001110101010
Key_Sub: 010100101010000111100111101010111010011100000010
Key_Sub: 110010101000011101100110001000101011111010000110
Key_Sub: 110000111001011001110100110000100111111000001100
Key_Sub: 111001011000111001100100011010010101000001001101
L: 01000111000111110000011100010100 R: 01111000100111101101101001111001
L: 01111000100111101101101001111001 R: 00010101100011110001110110011110
L: 00010101100011110001110110011110 R: 00110111100010111000000100100111
L: 00110111100010111000000100100111 R: 01001111001010100110111001100000
L: 01001111001010100110111001100000 R: 01010001110011011011000100101010
L: 01010001110011011011000100101010 R: 00101001000111011000110110010110
L: 00101001000111011000110110010110 R: 00101011101110110100100110010101
L: 00101011101110110100100110010101 R: 00001101110001011011101010010011
L: 00001101110001011011101010010011 R: 00101011101111111000011100101011
L: 00101011101111111000011100101011 R: 00000111001010101010100111110111
L: 00000111001010101010100111110111 R: 00110011001011101000110111010000
L: 00110011001011101000110111010000 R: 00111011011100100001111010100011
L: 00111011011100100001111010100011 R: 01100100110101010100010000110001
L: 01100100110101010100010000110001 R: 00000010011001001100000110011001
L: 00000010011001001100000110011001 R: 11111111011110110101011011100111
L: 11111111011110110101011011100111 R: 00000000000000001010000000001010
T_Iteration RL: 1111111101111011010101101110011100000000000000001010000000001010
IP_Inv_Substitute RL: 1111111101111011010101101110011100000000000000001010000000001010
IP_Inv_Substitute C: 0101000101010111010001010101001001010100010110010101010101001001
Plain_Text: 0101000101010111010001010101001001010100010110010101010101001001
Original Text = Decoded Text? Yes.