密钥算法
OpenSSL 支持 RSA、DSA 和 ECDSA 密钥,但是在实际场景中只是用 RSA 和 ECDSA 密钥。例如 Web 服务器的密钥,都使用RSA或ECDSA,因为DSA效率问题会限制在1024位(相对旧版本浏览器不支持更长的DSA密钥),ECDSA还没有全面范围的普及。比如SSH,一般都是使用DSA和RSA,而不是所有的客户端(不只是浏览器)都支持ECDSA算法。
密钥长度
默认的密钥长度一般都不够安全,老版本的 OpenSSL 默认 RSA 私钥是1024位,所以我们需要指定密钥长度,2048位是效率和安全的平衡点。如果 RSA 密钥的长度是512位,非常不安全,***者可以先获取你的证书,再使用暴力方式来算出对应的私钥,之后就可以冒充你的网站了。现在,一般认为2048位的 RSA 密钥是安全的,所以你应该采用这个长度的密钥。DSA 密钥也应该不少于2048位,ECDSA密钥则应该是256位或以上。
[root@localhost ~]# openssl req -help
req [options] outfile
-x509 output a x509 structure instead of a cert. req. #表示生成一个自签证书(如果是向CA服务器申请证书,就不要用这个选项)
-new new request. #生成一个新证书
-key file use the private key contained in file #表示私钥的文件 后面跟具体的私钥文件
-days number of days a certificate generated by -x509 is valid for. #表示证书的有效时间
-out arg output file #表示证书生成的路径和名字(一般是以.crt结尾 不要乱改)
-subj arg set or modify request subject #subj 指定证书信息(国家、省份、城市、公司、CN(common name)管理员邮箱) 客户端得到一个证书之后会检验一下证书,是使用客户端保存的根证书去验证证书的真伪,从根证书中获取公钥,解密证书上的签名,然后使用证书上标明的散列算法,计算出证书信息的散列值,对比解密后的值与计算出的散列值,如果二者相等,那么说明证书是CA(权威机构,根证书的发布者)签发的,是合法的。
我们自签的证书不是CA签发的,发给用户端之后,用户端是验证不通过的,想要验证通过就要添加一个根证书,这个根证书也是我们自己签发的,可以使用它验证我们的自签证书。
经过上面的论述,可以看出实际上是两套证书系统,一套是各个服务商的证书,这些证书发给用户,用于保密通信;另一套是检验证书合法性的根证书系统,用来验证各个服务商的证书。
所以我们要让我们自签的证书能顺利使用,也要建立自签的根证书和普通证书。
创建一个自签的根证书
- 创建私钥
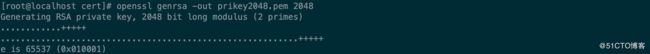
[root@localhost cert]# openssl genrsa -out prikey2048.pem 2048 Generating RSA private key, 2048 bit long modulus (2 primes) ............+++++ ...........................................................+++++ e is 65537 (0x010001) [root@localhost cert]# ll 总用量 4 -rw-------. 1 root root 1679 10月 27 22:15 prikey2048.pem - 使用私钥生成根证书
[root@localhost cert]# openssl req -new -x509 -key prikey2048.pem -out ca_cert_server2048.crt -days 365
Country Name (2 letter code) [AU]:CN
State or Province Name (full name) [Some-State]:BeiJing
Locality Name (eg, city) []:BeiJing
Organization Name (eg, company) [Internet Widgits Pty Ltd]:Devops
Organizational Unit Name (eg, section) []:certDevops
Common Name (e.g. server FQDN or YOUR name) []:www.linuxplus.com
Email Address []:[email protected]
[root@localhost cert]# openssl x509 -in ca_cert_server2048.crt -text
Certificate:
Data:
Version: 3 (0x2)
Serial Number:
74:fc:00:d8:9a:32:26:7b:16:e0:d4:c1:91:b3:13:80:8e:db:74:dc
Signature Algorithm: sha256WithRSAEncryption
Issuer: C = CN, ST = BeiJing, L = BeiJing, O = Devops, OU = certDevops, CN = www.linuxplus.com, emailAddress = [email protected]
Validity
Not Before: Oct 27 14:25:51 2018 GMT
Not After : Oct 27 14:25:51 2019 GMT
Subject: C = CN, ST = BeiJing, L = BeiJing, O = Devops, OU = certDevops, CN = www.linuxplus.com, emailAddress = [email protected]
Subject Public Key Info:
Public Key Algorithm: rsaEncryption
RSA Public-Key: (2048 bit)
Modulus:
00:c3:8d:e2:52:8d:ac:5f:a8:2e:b6:c8:ae:ca:6f:
be:aa:a6:0f:10:73:f6:15:90:53:02:db:48:29:77:
7f:ef:73:d1:22:0d:8f:b8:e9:25:55:a5:2c:96:c5:
f7:6d:a3:b6:c3:0b:9d:b9:9f:78:49:83:9d:d2:dd:
a2:ac:c6:04:2f:6d:af:d8:0d:ed:04:e2:e8:ac:88:
6f:3b:33:06:69:bc:45:78:d4:47:d4:17:bf:f2:62:
00:d6:aa:94:30:b0:7e:bd:a0:5c:b1:fb:77:98:f3:
ff:2c:52:0f:89:76:86:f1:4a:38:36:9f:07:34:99:
da:a8:29:ff:34:3e:a0:82:13:06:cc:33:ca:45:34:
77:82:0c:5f:51:5e:2b:57:9b:3d:30:63:2d:19:5f:
30:29:31:82:52:9e:bb:26:09:29:d7:05:89:31:e9:
61:7c:eb:9d:9b:87:21:53:ad:5b:f9:80:f1:64:07:
ac:9e:9c:1b:43:96:45:ae:3e:07:d3:89:a9:5d:e6:
1d:78:01:a8:7f:df:af:11:d2:96:29:80:9b:6e:96:
4d:c7:e2:26:cf:db:6b:bf:20:52:14:e2:f0:4d:97:
ea:69:07:9e:de:7e:b2:1a:27:c8:fe:09:9f:f3:bd:
a4:4f:63:7e:26:56:65:d4:fa:e8:85:3f:0a:26:68:
cc:93
Exponent: 65537 (0x10001)
X509v3 extensions:
X509v3 Subject Key Identifier:
E4:CE:A0:91:5A:DE:55:60:FA:C9:FB:9B:CF:2B:47:87:4B:DD:98:60
X509v3 Authority Key Identifier:
keyid:E4:CE:A0:91:5A:DE:55:60:FA:C9:FB:9B:CF:2B:47:87:4B:DD:98:60
X509v3 Basic Constraints: critical
CA:TRUE
Signature Algorithm: sha256WithRSAEncryption
96:17:f6:f9:91:c4:49:cd:e8:3a:b6:5d:3c:60:33:1e:38:d6:
71:81:f2:c0:33:43:46:98:6e:b7:36:87:92:15:61:12:96:79:
b9:a4:9e:47:2c:54:bf:ed:10:f3:21:ac:a6:cf:15:76:86:d7:
93:e9:4c:4f:f3:bc:61:5c:80:db:9f:52:6d:44:20:c6:ef:dd:
8b:b6:9e:09:e7:ff:51:6a:ea:e1:7c:e3:78:8b:16:9f:75:5c:
c6:95:34:e8:84:7b:d3:5b:fd:1f:78:a6:f3:a7:15:68:7b:71:
07:ce:8f:cd:5e:8b:73:d3:6e:73:df:45:18:ba:16:33:a8:41:
53:6c:7a:28:10:cf:e3:00:e7:ec:35:fd:1f:4b:05:2b:04:03:
8f:49:7d:3a:1e:6a:b6:c8:02:f2:ba:f3:23:0a:d0:dd:87:39:
d1:fe:5d:51:7d:9f:fc:67:e8:90:36:e7:ea:22:35:85:fd:96:
01:7a:d5:1c:89:7b:13:e4:67:51:fb:87:c2:f4:76:3a:b2:71:
bb:88:59:89:9a:ab:f8:ce:66:ad:85:f6:ae:e0:78:15:ff:c7:
6f:ed:34:34:39:e6:e5:d7:f7:73:26:2c:e9:dd:c5:34:04:d6:
82:09:28:d4:8d:71:58:ce:82:7d:86:74:6f:76:e1:73:54:0d:
9a:e1:b4:5f
-----BEGIN CERTIFICATE-----
MIIEETCCAvmgAwIBAgIUdPwA2JoyJnsW4NTBkbMTgI7bdNwwDQYJKoZIhvcNAQEL
BQAwgZcxCzAJBgNVBAYTAkNOMRAwDgYDVQQIDAdCZWlKaW5nMRAwDgYDVQQHDAdC
ZWlKaW5nMQ8wDQYDVQQKDAZEZXZvcHMxEzARBgNVBAsMCmNlcnREZXZvcHMxGjAY
BgNVBAMMEXd3dy5saW51eHBsdXMuY29tMSIwIAYJKoZIhvcNAQkBFhNhZG1pbkBs
aW51eHBsdXMuY29tMB4XDTE4MTAyNzE0MjU1MVoXDTE5MTAyNzE0MjU1MVowgZcx
CzAJBgNVBAYTAkNOMRAwDgYDVQQIDAdCZWlKaW5nMRAwDgYDVQQHDAdCZWlKaW5n
MQ8wDQYDVQQKDAZEZXZvcHMxEzARBgNVBAsMCmNlcnREZXZvcHMxGjAYBgNVBAMM
EXd3dy5saW51eHBsdXMuY29tMSIwIAYJKoZIhvcNAQkBFhNhZG1pbkBsaW51eHBs
dXMuY29tMIIBIjANBgkqhkiG9w0BAQEFAAOCAQ8AMIIBCgKCAQEAw43iUo2sX6gu
tsiuym++qqYPEHP2FZBTAttIKXd/73PRIg2PuOklVaUslsX3baO2wwuduZ94SYOd
0t2irMYEL22v2A3tBOLorIhvOzMGabxFeNRH1Be/8mIA1qqUMLB+vaBcsft3mPP/
LFIPiXaG8Uo4Np8HNJnaqCn/ND6gghMGzDPKRTR3ggxfUV4rV5s9MGMtGV8wKTGC
Up67Jgkp1wWJMelhfOudm4chU61b+YDxZAesnpwbQ5ZFrj4H04mpXeYdeAGof9+v
EdKWKYCbbpZNx+Imz9trvyBSFOLwTZfqaQee3n6yGifI/gmf872kT2N+JlZl1Pro
hT8KJmjMkwIDAQABo1MwUTAdBgNVHQ4EFgQU5M6gkVreVWD6yfubzytHh0vdmGAw
HwYDVR0jBBgwFoAU5M6gkVreVWD6yfubzytHh0vdmGAwDwYDVR0TAQH/BAUwAwEB
/zANBgkqhkiG9w0BAQsFAAOCAQEAlhf2+ZHESc3oOrZdPGAzHjjWcYHywDNDRphu
tzaHkhVhEpZ5uaSeRyxUv+0Q8yGsps8VdobXk+lMT/O8YVyA259SbUQgxu/di7ae
Cef/UWrq4XzjeIsWn3VcxpU06IR701v9H3im86cVaHtxB86PzV6Lc9Nuc99FGLoW
M6hBU2x6KBDP4wDn7DX9H0sFKwQDj0l9Oh5qtsgC8rrzIwrQ3Yc50f5dUX2f/Gfo
kDbn6iI1hf2WAXrVHIl7E+RnUfuHwvR2OrJxu4hZiZqr+M5mrYX2ruB4Ff/Hb+00
NDnm5df3cyYs6d3FNATWggko1I1xWM6CfYZ0b3bhc1QNmuG0Xw==
-----END CERTIFICATE-----创建一个证书申请
- 先创建一个私钥
[root@localhost cert]# openssl genrsa -out cert_prikey2048.pem 2048
Generating RSA private key, 2048 bit long modulus (2 primes)
....+++++
............................................+++++
e is 65537 (0x010001)- 再生成一个证书申请
[root@localhost cert]# openssl req -new -key cert_prikey2048.pem -out cert.csr -subj /C=CN/ST=GuangZhou/L=ShenZhen/O=Devops01/OU=certDevops01/CN=www.linuxplus01.com/[email protected]- 使用自签的根证书对证书申请进行签署
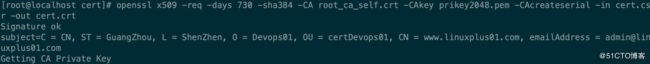
[root@localhost cert]# openssl x509 -req -days 730 -sha384 -CA root_ca_self.crt -CAkey prikey2048.pem -CAcreateserial -in cert.csr -out cert.crt
Signature ok
subject=C = CN, ST = GuangZhou, L = ShenZhen, O = Devops01, OU = certDevops01, CN = www.linuxplus01.com, emailAddress = [email protected]
Getting CA Private Key- 查看自签证书
[root@localhost cert]# openssl x509 -in cert.crt -text Certificate: Data: Version: 1 (0x0) Serial Number: 1c:cf:18:ba:93:87:53:2a:e8:98:15:59:17:a3:8b:bf:7a:35:9d:46 Signature Algorithm: sha384WithRSAEncryption Issuer: C = CN, ST = BeiJing, L = BeiJing, O = Devops, OU = certDevops, CN = www.linuxplus.com, emailAddress = [email protected] Validity Not Before: Oct 27 15:02:36 2018 GMT Not After : Oct 26 15:02:36 2020 GMT Subject: C = CN, ST = GuangZhou, L = ShenZhen, O = Devops01, OU = certDevops01, CN = www.linuxplus01.com, emailAddress = [email protected] Subject Public Key Info: Public Key Algorithm: rsaEncryption RSA Public-Key: (2048 bit) Modulus: 00:cd:dc:0d:85:7e:a0:67:81:e7:15:c5:8f:b8:13: 13:58:56:4e:dd:44:a9:10:d3:37:cd:6b:f7:3a:b2: 11:0c:19:af:48:0c:45:fa:31:29:d8:f7:8c:48:61: 5a:ff:26:b9:4f:f9:3c:af:1c:97:04:cf:c2:fb:da: 95:95:d6:15:4f:e4:45:30:c0:95:14:dc:8e:61:60: 2b:a1:0a:f9:02:c6:58:99:52:d7:21:d3:b2:5b:5a: 36:19:61:85:4c:c1:2a:d3:34:70:0b:ff:52:6b:b2: 00:7a:1a:3e:26:2f:30:b0:c3:30:25:59:b4:2a:c2: d6:ec:48:e8:f9:30:13:9e:a8:17:e8:e2:eb:0f:ed: 89:37:38:23:60:1c:97:b6:7f:71:56:33:52:b4:f4: 24:ba:ed:34:4c:d8:cc:fd:bf:1c:16:bd:cb:a9:a0: fe:8a:71:33:8c:f1:c4:b6:5b:87:39:48:0c:3f:d8: aa:d3:0e:fd:40:ca:0e:de:37:13:6c:78:af:84:f4: 07:75:ce:98:95:0f:05:9b:6a:3d:66:ff:e9:6d:f1: 0c:10:9e:d9:5d:bb:53:a8:d7:41:8d:50:b5:5f:a0: ac:59:39:88:9c:83:76:cb:b0:7b:7a:9c:2f:d9:80: f4:b7:20:8d:43:e5:40:44:fa:5c:71:45:0c:91:92: 9f:4d Exponent: 65537 (0x10001) Signature Algorithm: sha384WithRSAEncryption 95:2e:db:03:32:1b:aa:e5:be:e1:2e:42:65:a2:05:f1:e6:b0: 1f:98:d8:94:2b:c0:27:77:90:89:fc:83:82:51:af:3b:54:3e: ce:2d:a8:1b:5e:08:4a:41:a2:db:7c:d1:25:98:a0:1b:59:9b: 7e:e7:35:50:d0:eb:87:aa:25:a2:24:ac:91:0c:6b:a8:31:a8: a9:36:73:9c:23:c9:96:95:08:f3:56:b1:98:69:f0:38:e6:fc: 83:30:d2:2c:11:12:79:60:d9:dc:40:cf:92:5d:5b:f5:10:db: 90:0c:83:6a:c8:de:f1:91:11:36:28:f2:62:ee:65:64:46:8a: be:18:48:20:d1:c7:e8:73:fa:ea:bf:8e:e4:bb:9c:e0:8f:91: 11:39:f1:e8:a7:1a:5e:10:a7:0c:b8:c9:5b:07:d0:c2:d5:48: c8:58:1f:50:d7:67:98:2a:5a:69:3f:fa:99:c5:5b:f7:20:d3: 83:7b:82:49:d2:e9:9f:e2:6b:b1:78:5e:30:44:ec:02:af:b2: e8:a5:75:e2:0f:dc:66:80:84:50:b8:aa:2e:93:59:f6:91:42: a8:0d:8a:a1:c3:ee:ce:7c:55:7e:3b:9c:2f:4e:54:20:c6:78: 02:9f:4a:3e:b7:f1:5c:b7:0b:14:34:45:5a:6e:0c:92:f2:84: ad:35:bc:a3 -----BEGIN CERTIFICATE----- MIIDwjCCAqoCFBzPGLqTh1Mq6JgVWReji796NZ1GMA0GCSqGSIb3DQEBDAUAMIGX MQswCQYDVQQGEwJDTjEQMA4GA1UECAwHQmVpSmluZzEQMA4GA1UEBwwHQmVpSmlu ZzEPMA0GA1UECgwGRGV2b3BzMRMwEQYDVQQLDApjZXJ0RGV2b3BzMRowGAYDVQQD DBF3d3cubGludXhwbHVzLmNvbTEiMCAGCSqGSIb3DQEJARYTYWRtaW5AbGludXhw bHVzLmNvbTAeFw0xODEwMjcxNTAyMzZaFw0yMDEwMjYxNTAyMzZaMIGiMQswCQYD VQQGEwJDTjESMBAGA1UECAwJR3VhbmdaaG91MREwDwYDVQQHDAhTaGVuWmhlbjER MA8GA1UECgwIRGV2b3BzMDExFTATBgNVBAsMDGNlcnREZXZvcHMwMTEcMBoGA1UE AwwTd3d3LmxpbnV4cGx1czAxLmNvbTEkMCIGCSqGSIb3DQEJARYVYWRtaW5AbGlu dXhwbHVzMDEuY29tMIIBIjANBgkqhkiG9w0BAQEFAAOCAQ8AMIIBCgKCAQEAzdwN hX6gZ4HnFcWPuBMTWFZO3USpENM3zWv3OrIRDBmvSAxF+jEp2PeMSGFa/ya5T/k8 rxyXBM/C+9qVldYVT+RFMMCVFNyOYWAroQr5AsZYmVLXIdOyW1o2GWGFTMEq0zRw C/9Sa7IAeho+Ji8wsMMwJVm0KsLW7Ejo+TATnqgX6OLrD+2JNzgjYByXtn9xVjNS tPQkuu00TNjM/b8cFr3LqaD+inEzjPHEtluHOUgMP9iq0w79QMoO3jcTbHivhPQH dc6YlQ8Fm2o9Zv/pbfEMEJ7ZXbtTqNdBjVC1X6CsWTmInIN2y7B7epwv2YD0tyCN Q+VARPpccUUMkZKfTQIDAQABMA0GCSqGSIb3DQEBDAUAA4IBAQCVLtsDMhuq5b7h LkJlogXx5rAfmNiUK8And5CJ/IOCUa87VD7OLagbXghKQaLbfNElmKAbWZt+5zVQ 0OuHqiWiJKyRDGuoMaipNnOcI8mWlQjzVrGYafA45vyDMNIsERJ5YNncQM+SXVv1 ENuQDINqyN7xkRE2KPJi7mVkRoq+GEgg0cfoc/rqv47ku5zgj5EROfHopxpeEKcM uMlbB9DC1UjIWB9Q12eYKlppP/qZxVv3INODe4JJ0umf4muxeF4wROwCr7LopXXi D9xmgIRQuKouk1n2kUKoDYqhw+7OfFV+O5wvTlQgxngCn0o+t/FctwsUNEVabgyS 8oStNbyj -----END CERTIFICATE-----创建私钥 CA 管理机构
[root@localhost ~]# touch .rnd
[root@localhost openssl]# pwd
/usr/local/openssl
[root@localhost openssl]# mkdir CA
[root@localhost openssl]# ll -d CA
drwxr-xr-x. 2 root root 6 10月 28 13:51 CA
[root@localhost openssl]# cd CA
[root@localhost CA]# mkdir crl newcerts private #newcerts:新证书存放目录
[root@localhost CA]# touch index.txt serial crlnumber crl.pem index.txt.attr
#crl.pem:证书吊销列表
[root@localhost CA]# openssl rand -hex 16 > serial #初始化证书序号
[root@localhost CA]# cat serial
3bf9bc72544e25a7072d924206a76154
[root@localhost CA]# ll
总用量 0
drwxr-xr-x. 2 root root 6 10月 28 13:52 crl
-rw-r--r--. 1 root root 0 10月 28 13:54 crlnumber
-rw-r--r--. 1 root root 0 10月 28 13:54 crl.pem
-rw-r--r--. 1 root root 0 10月 28 13:54 index.txt
-rw-r--r--. 1 root root 0 10月 28 13:54 index.txt.attr
drwxr-xr-x. 2 root root 6 10月 28 13:52 newcerts
drwxr-xr-x. 2 root root 6 10月 28 13:52 private
-rw-r--r--. 1 root root 0 10月 28 13:54 serial
[root@localhost openssl]# vim openssl.cnf
[ CA_default ]
dir = /usr/local/openssl/CA # Where everything is kept
unique_subject = no # Set to 'no' to allow creation of
# several certs with same subject.
certificate = $dir/root_cacert_ecc.pem # The CA certificate
private_key = $dir/private/root_prikey_ecdsa.pem # The private key
# For the CA policy
# match表示必须匹配,optional表示可选,supplied表示必须提供
[ policy_match ]
countryName = match
stateOrProvinceName = optional
localityName = optional
organizationName = optional
organizationalUnitName = optional
commonName = supplied
emailAddress = optional
[root@localhost openssl]# cd CA
[root@localhost CA]# openssl ecparam -genkey -name prime256v1 -out root_prikey_ecdsa.pem #创建私钥
[root@localhost CA]# openssl ec -in root_prikey_ecdsa.pem -aes128 -passout pass:redhat -out root_prikey_ecdsa.pem #加密证书
read EC key
writing EC key
[root@localhost CA]# openssl req -new -x509 -key root_prikey_ecdsa.pem -out root_cacert_ecc.pem -days 730 -subj /C=CN/ST=BeiJing/L=BeiJing/O=CAdevops/OU=CAdevops/CN=root_ca/[email protected] #生成自签根证书
Enter pass phrase for root_prikey_ecdsa.pem:
[root@localhost CA]# mv root_prikey_ecdsa.pem private/
[root@localhost CA]# ll private/
总用量 4
-rw-------. 1 root root 314 10月 28 14:12 root_prikey_ecdsa.pem
[root@localhost CA]# mkdir test
[root@localhost CA]# cd test
[root@localhost test]# openssl genrsa -out rsa_01prikey.pem 2048 #生成私钥
Generating RSA private key, 2048 bit long modulus (2 primes)
......................................................................................................+++++
...............+++++
e is 65537 (0x010001)
[root@localhost test]# ll
总用量 4
-rw-------. 1 root root 1675 10月 28 14:27 rsa_01prikey.pem
[root@localhost test]# openssl req -new -key rsa_01prikey.pem -out rsa_01cert.csr -subj /C=CN/ST=ShangHai/L=ShangHai/O=CAdevops01/OU=CAdevops01/CN=www.linuxplus01.com/[email protected] #生成自签的根证书
[root@localhost test]# openssl ca -in rsa_01cert.csr -days 100 -md sha1 -out rsa_01cert.crt -batch -notext #使用私有CA结构签署一个证书
Using configuration from /usr/local/openssl/openssl.cnf
Enter pass phrase for /usr/local/openssl/CA/private/root_prikey_ecdsa.pem:
Check that the request matches the signature
Signature ok
Certificate Details:
Serial Number:
3b:f9:bc:72:54:4e:25:a7:07:2d:92:42:06:a7:61:55
Validity
Not Before: Oct 28 06:53:07 2018 GMT
Not After : Feb 5 06:53:07 2019 GMT
Subject:
countryName = CN
stateOrProvinceName = ShangHai
organizationName = CAdevops01
organizationalUnitName = CAdevops01
commonName = www.linuxplus01.com
emailAddress = [email protected]
X509v3 extensions:
X509v3 Basic Constraints:
CA:FALSE
Netscape Comment:
OpenSSL Generated Certificate
X509v3 Subject Key Identifier:
4E:1E:57:79:64:DD:E0:71:43:9F:85:A7:EB:9B:22:20:AB:03:8C:58
X509v3 Authority Key Identifier:
keyid:9F:7A:42:AF:E4:36:0D:01:CD:FF:27:57:18:2A:3E:CC:8A:77:C0:D7
Certificate is to be certified until Feb 5 06:53:07 2019 GMT (100 days)
Write out database with 1 new entries
Data Base Updated
[root@localhost test]# ll
总用量 12
-rw-r--r--. 1 root root 1229 10月 28 14:53 rsa_01cert.crt
-rw-r--r--. 1 root root 1082 10月 28 14:52 rsa_01cert.csr
-rw-------. 1 root root 1679 10月 28 14:49 rsa_01prikey.pem![]()
- 签署一个 ECC 证书
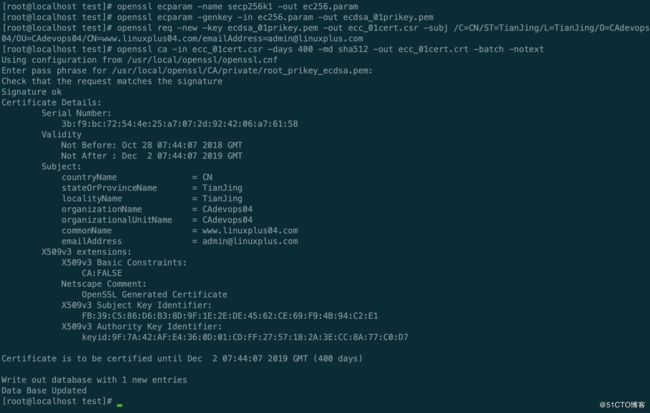
[root@localhost test]# openssl ecparam -name secp256k1 -out ec256.param
[root@localhost test]# openssl ecparam -genkey -in ec256.param -out ecdsa_01prikey.pem
[root@localhost test]# openssl req -new -key ecdsa_01prikey.pem -out ecc_01cert.csr -subj /C=CN/ST=TianJing/L=TianJing/O=CAdevops04/OU=CAdevops04/CN=www.linuxplus04.com/[email protected]
[root@localhost test]# openssl ca -in ecc_01cert.csr -days 400 -md sha512 -out ecc_01cert.crt -batch -notext
Using configuration from /usr/local/openssl/openssl.cnf
Enter pass phrase for /usr/local/openssl/CA/private/root_prikey_ecdsa.pem:
Check that the request matches the signature
Signature ok
Certificate Details:
Serial Number:
3b:f9:bc:72:54:4e:25:a7:07:2d:92:42:06:a7:61:58
Validity
Not Before: Oct 28 07:44:07 2018 GMT
Not After : Dec 2 07:44:07 2019 GMT
Subject:
countryName = CN
stateOrProvinceName = TianJing
localityName = TianJing
organizationName = CAdevops04
organizationalUnitName = CAdevops04
commonName = www.linuxplus04.com
emailAddress = [email protected]
X509v3 extensions:
X509v3 Basic Constraints:
CA:FALSE
Netscape Comment:
OpenSSL Generated Certificate
X509v3 Subject Key Identifier:
FB:39:C5:86:D6:B3:8D:9F:1E:2E:DE:45:62:CE:69:F9:4B:94:C2:E1
X509v3 Authority Key Identifier:
keyid:9F:7A:42:AF:E4:36:0D:01:CD:FF:27:57:18:2A:3E:CC:8A:77:C0:D7
Certificate is to be certified until Dec 2 07:44:07 2019 GMT (400 days)
Write out database with 1 new entries
Data Base Updated证书吊销与管理
[root@localhost test]# openssl x509 -in ecc_01cert.crt -noout -serial
serial=3BF9BC72544E25A7072D924206A76158
[root@localhost test]# openssl x509 -in ecc_01cert.crt -noout -serial -subject #查看证书的序列号和所有者信息
serial=3BF9BC72544E25A7072D924206A76158
subject=C = CN, ST = TianJing, L = TianJing, O = CAdevops04, OU = CAdevops04, CN = www.linuxplus04.com, emailAddress = [email protected]
[root@localhost test]# openssl x509 -in ecc_01cert.crt -noout -serial -subject -issuer #查看证书的发布者
serial=3BF9BC72544E25A7072D924206A76158
subject=C = CN, ST = TianJing, L = TianJing, O = CAdevops04, OU = CAdevops04, CN = www.linuxplus04.com, emailAddress = [email protected]
issuer=C = CN, ST = BeiJing, L = BeiJing, O = CAdevops, OU = CAdevops, CN = root_ca, emailAddress = [email protected]
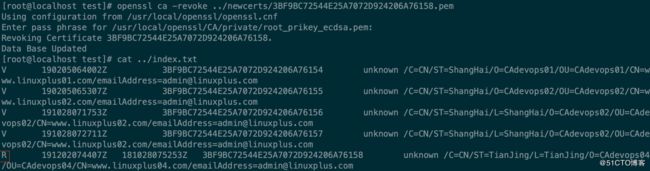
[root@localhost test]# openssl ca -revoke ../newcerts/3BF9BC72544E25A7072D924206A76158.pem
Using configuration from /usr/local/openssl/openssl.cnf
Enter pass phrase for /usr/local/openssl/CA/private/root_prikey_ecdsa.pem:
Revoking Certificate 3BF9BC72544E25A7072D924206A76158.
Data Base Updated
[root@localhost test]# cat ../index.txt
V 190205064002Z 3BF9BC72544E25A7072D924206A76154 unknown /C=CN/ST=ShangHai/O=CAdevops01/OU=CAdevops01/CN=www.linuxplus01.com/[email protected]
V 190205065307Z 3BF9BC72544E25A7072D924206A76155 unknown /C=CN/ST=ShangHai/O=CAdevops02/OU=CAdevops02/CN=www.linuxplus02.com/[email protected]
V 191028071753Z 3BF9BC72544E25A7072D924206A76156 unknown /C=CN/ST=ShangHai/L=ShangHai/O=CAdevops02/OU=CAdevops02/CN=www.linuxplus02.com/[email protected]
V 191028072711Z 3BF9BC72544E25A7072D924206A76157 unknown /C=CN/ST=ShangHai/L=ShangHai/O=CAdevops02/OU=CAdevops02/CN=www.linuxplus02.com/[email protected]
R 191202074407Z 181028075253Z 3BF9BC72544E25A7072D924206A76158 unknown /C=CN/ST=TianJing/L=TianJing/O=CAdevops04/OU=CAdevops04/CN=www.linuxplus04.com/[email protected]
[root@localhost test]# openssl ca -status 3BF9BC72544E25A7072D924206A76157
Using configuration from /usr/local/openssl/openssl.cnf
3BF9BC72544E25A7072D924206A76157=Valid (V)
[root@localhost test]# openssl ca -status 3BF9BC72544E25A7072D924206A76158
Using configuration from /usr/local/openssl/openssl.cnf
3BF9BC72544E25A7072D924206A76158=Revoked (R)- 生成吊销列表
[root@localhost CA]# echo 100001 > crlnumber #设置初始值
[root@localhost CA]# cat crlnumber
100001
[root@localhost CA]# openssl ca -gencrl -out /usr/local/openssl/CA/crl.pem
Using configuration from /usr/local/openssl/openssl.cnf
Enter pass phrase for /usr/local/openssl/CA/private/root_prikey_ecdsa.pem:
[root@localhost CA]# ll crl.pem
-rw-r--r--. 1 root root 508 10月 28 16:12 crl.pem
[root@localhost CA]# openssl crl -in crl.pem -text
Certificate Revocation List (CRL):
Version 2 (0x1)
Signature Algorithm: ecdsa-with-SHA256
Issuer: C = CN, ST = BeiJing, L = BeiJing, O = CAdevops, OU = CAdevops, CN = root_ca, emailAddress = [email protected]
Last Update: Oct 28 08:12:17 2018 GMT
Next Update: Nov 27 08:12:17 2018 GMT
CRL extensions:
X509v3 CRL Number:
1048577
Revoked Certificates:
Serial Number: 3BF9BC72544E25A7072D924206A76158
Revocation Date: Oct 28 07:52:53 2018 GMT
Signature Algorithm: ecdsa-with-SHA256
30:45:02:20:0f:41:7d:50:d1:ff:d3:98:d8:d9:07:00:17:8d:
55:53:b0:c5:04:0f:7a:a1:5c:95:02:88:9d:c4:be:ab:df:85:
02:21:00:ac:d6:bd:4e:5c:f0:4d:cf:6f:64:21:f3:78:a5:29:
dc:68:fa:71:5b:56:ff:27:97:31:a1:c6:10:43:63:2a:63
-----BEGIN X509 CRL-----
MIIBTTCB9AIBATAKBggqhkjOPQQDAjCBjTELMAkGA1UEBhMCQ04xEDAOBgNVBAgM
B0JlaUppbmcxEDAOBgNVBAcMB0JlaUppbmcxETAPBgNVBAoMCENBZGV2b3BzMREw
DwYDVQQLDAhDQWRldm9wczEQMA4GA1UEAwwHcm9vdF9jYTEiMCAGCSqGSIb3DQEJ
ARYTYWRtaW5AbGludXhwbHVzLmNvbRcNMTgxMDI4MDgxMjE3WhcNMTgxMTI3MDgx
MjE3WjAjMCECEDv5vHJUTiWnBy2SQganYVgXDTE4MTAyODA3NTI1M1qgEDAOMAwG
A1UdFAQFAgMQAAEwCgYIKoZIzj0EAwIDSAAwRQIgD0F9UNH/05jY2QcAF41VU7DF
BA96oVyVAoidxL6r34UCIQCs1r1OXPBNz29kIfN4pSncaPpxW1b/J5cxocYQQ2Mq
Yw==
-----END X509 CRL-----
default_crl_days= 30 # how long before next CRL
[root@localhost CA]# cat crlnumber #下一个吊销证书序号
100002
[root@localhost CA]# cat crlnumber.old #已吊销证书序号
100001- 证书过期测试
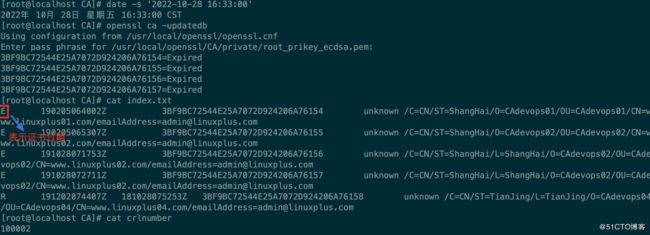
[root@localhost CA]# date -s '2022-10-28 16:33:00'
2022年 10月 28日 星期五 16:33:00 CST
[root@localhost CA]# openssl ca -updatedb
Using configuration from /usr/local/openssl/openssl.cnf
Enter pass phrase for /usr/local/openssl/CA/private/root_prikey_ecdsa.pem:
3BF9BC72544E25A7072D924206A76154=Expired
3BF9BC72544E25A7072D924206A76155=Expired
3BF9BC72544E25A7072D924206A76156=Expired
3BF9BC72544E25A7072D924206A76157=Expired
[root@localhost CA]# cat index.txt
E 190205064002Z 3BF9BC72544E25A7072D924206A76154 unknown /C=CN/ST=ShangHai/O=CAdevops01/OU=CAdevops01/CN=www.linuxplus01.com/[email protected]
E 190205065307Z 3BF9BC72544E25A7072D924206A76155 unknown /C=CN/ST=ShangHai/O=CAdevops02/OU=CAdevops02/CN=www.linuxplus02.com/[email protected]
E 191028071753Z 3BF9BC72544E25A7072D924206A76156 unknown /C=CN/ST=ShangHai/L=ShangHai/O=CAdevops02/OU=CAdevops02/CN=www.linuxplus02.com/[email protected]
E 191028072711Z 3BF9BC72544E25A7072D924206A76157 unknown /C=CN/ST=ShangHai/L=ShangHai/O=CAdevops02/OU=CAdevops02/CN=www.linuxplus02.com/[email protected]
R 191202074407Z 181028075253Z 3BF9BC72544E25A7072D924206A76158 unknown /C=CN/ST=TianJing/L=TianJing/O=CAdevops04/OU=CAdevops04/CN=www.linuxplus04.com/[email protected]