vsftp 服务端安装
1、执行命令
[root@ftp-server vsftpd]# yum install vsftpd
# yum -y install libdb-utils
#CentOS7是libdb-utils
创建宿主用户,即guest_username,所有虚拟用户都是映射宿主用户的目录权限。
useradd是添加用户的。后面应该还要添加一个用户名。
-d是指定用户的家目录
-s是指定用户的登录shell
# useradd -d /home/vsftp -s /sbin/nologin vsftp
2、执行命令
[root@ftp-server vsftpd]# cp vsftpd.conf vsftpd.conf.bak
[root@ftp-server vsftpd]# vi vsftpd.con
[root@ftp-server vsftpd]# cat vsftpd.conf
# Example config file /etc/vsftpd/vsftpd.conf
#
# The default compiled in settings are fairly paranoid. This sample file
# loosens things up a bit, to make the ftp daemon more usable.
# Please see vsftpd.conf.5 for all compiled in defaults.
#
# READ THIS: This example file is NOT an exhaustive list of vsftpd options.
# Please read the vsftpd.conf.5 manual page to get a full idea of vsftpd's
# capabilities.
#
# Allow anonymous FTP? (Beware - allowed by default if you comment this out).
#anonymous_enable=YES
anonymous_enable=NO
#
# Uncomment this to allow local users to log in.
# When SELinux is enforcing check for SE bool ftp_home_dir
local_enable=YES
#
# Uncomment this to enable any form of FTP write command.
write_enable=YES
#
# Default umask for local users is 077. You may wish to change this to 022,
# if your users expect that (022 is used by most other ftpd's)
local_umask=022
#
# Uncomment this to allow the anonymous FTP user to upload files. This only
# has an effect if the above global write enable is activated. Also, you will
# obviously need to create a directory writable by the FTP user.
# When SELinux is enforcing check for SE bool allow_ftpd_anon_write, allow_ftpd_full_access
#anon_upload_enable=YES
#
# Uncomment this if you want the anonymous FTP user to be able to create
# new directories.
#anon_mkdir_write_enable=YES
#
# Activate directory messages - messages given to remote users when they
# go into a certain directory.
dirmessage_enable=YES
#
# Activate logging of uploads/downloads.
xferlog_enable=YES
#
# Make sure PORT transfer connections originate from port 20 (ftp-data).
#connect_from_port_20=YES
connect_from_port_20=NO
#
# If you want, you can arrange for uploaded anonymous files to be owned by
# a different user. Note! Using "root" for uploaded files is not
# recommended!
#chown_uploads=YES
#chown_username=whoever
#
# You may override where the log file goes if you like. The default is shown
# below.
#xferlog_file=/var/log/xferlog
#
# If you want, you can have your log file in standard ftpd xferlog format.
# Note that the default log file location is /var/log/xferlog in this case.
xferlog_std_format=YES
#
# You may change the default value for timing out an idle session.
#idle_session_timeout=600
#
# You may change the default value for timing out a data connection.
#data_connection_timeout=120
#
# It is recommended that you define on your system a unique user which the
# ftp server can use as a totally isolated and unprivileged user.
#nopriv_user=ftpsecure
#
# Enable this and the server will recognise asynchronous ABOR requests. Not
# recommended for security (the code is non-trivial). Not enabling it,
# however, may confuse older FTP clients.
#async_abor_enable=YES
#
# By default the server will pretend to allow ASCII mode but in fact ignore
# the request. Turn on the below options to have the server actually do ASCII
# mangling on files when in ASCII mode. The vsftpd.conf(5) man page explains
# the behaviour when these options are disabled.
# Beware that on some FTP servers, ASCII support allows a denial of service
# attack (DoS) via the command "SIZE /big/file" in ASCII mode. vsftpd
# predicted this attack and has always been safe, reporting the size of the
# raw file.
# ASCII mangling is a horrible feature of the protocol.
#ascii_upload_enable=YES
#ascii_download_enable=YES
#
# You may fully customise the login banner string:
#ftpd_banner=Welcome to blah FTP service.
#
# You may specify a file of disallowed anonymous e-mail addresses. Apparently
# useful for combatting certain DoS attacks.
#deny_email_enable=YES
# (default follows)
#banned_email_file=/etc/vsftpd/banned_emails
#
# You may specify an explicit list of local users to chroot() to their home
# directory. If chroot_local_user is YES, then this list becomes a list of
# users to NOT chroot().
# (Warning! chroot'ing can be very dangerous. If using chroot, make sure that
# the user does not have write access to the top level directory within the
# chroot)
#chroot_local_user=YES
#chroot_list_enable=YES
# (default follows)
#chroot_list_file=/etc/vsftpd/chroot_list
chroot_local_user=YES
chroot_list_enable=UES
chroot_list_file=/etc/vsftpd/chroot_list
#
# You may activate the "-R" option to the builtin ls. This is disabled by
# default to avoid remote users being able to cause excessive I/O on large
# sites. However, some broken FTP clients such as "ncftp" and "mirror" assume
# the presence of the "-R" option, so there is a strong case for enabling it.
#ls_recurse_enable=YES
#
# When "listen" directive is enabled, vsftpd runs in standalone mode and
# listens on IPv4 sockets. This directive cannot be used in conjunction
# with the listen_ipv6 directive.
#listen=NO
listen=YES
#
# This directive enables listening on IPv6 sockets. By default, listening
# on the IPv6 "any" address (::) will accept connections from both IPv6
# and IPv4 clients. It is not necessary to listen on *both* IPv4 and IPv6
# sockets. If you want that (perhaps because you want to listen on specific
# addresses) then you must run two copies of vsftpd with two configuration
# files.
# Make sure, that one of the listen options is commented !!
#listen_ipv6=YES
listen_ipv6=NO
pam_service_name=vsftpd
userlist_enable=YES
tcp_wrappers=YES
virtual_use_local_privs=NO
guest_enable=YES
guest_username=vsftp
user_config_dir=/etc/vsftpd/vuser_conf
pasv_enable=YES
pasv_min_port=10000
pasv_max_port=15000
3、创建chroot_list
chroot()会检查chroot_list文件,创建文件
# touch /etc/vsftpd/chroot_list
4、设置虚拟用户
虚拟用户列表
奇行为用户名,偶行为密码
# vi /etc/vsftpd/vuser
ftphuawei
12#$
虚拟用户认证文件
# db_load -T -t hash -f /etc/vsftpd/vuser /etc/vsftpd/vuser.db
# chmod 600 /etc/vsftpd/vuser.db
虚拟用户认证配置
注释掉其他本地用户认证的内容,因为启用了guest_enable后,本地用户将失效,所有非匿名用户变成虚拟用户
# cp /etc/pam.d/vsftpd{,.bak}
# vi /etc/pam.d/vsftpd
auth required /lib64/security/pam_userdb.so db=/etc/vsftpd/vuser
account required /lib64/security/pam_userdb.so db=/etc/vsftpd/vuser
虚拟用户配置文件
# mkdir /etc/vsftpd/vuser_conf/
# vi /etc/vsftpd/vuser_conf/ftphuawei #文件名与对应FTP虚拟用户一致
local_root=/home/vsftp/ftphuawei #虚拟用户主目录,用户和组必须指定为宿主用户vsftp
#vsftpd主配置文件中已规定虚拟用户权限与匿名用户一致,因此以下针对匿名用户的权限配置即为虚拟用户的权限
anon_umask=077
anon_world_readable_only=NO
anon_upload_enable=YES
anon_mkdir_write_enable=YES
anon_other_write_enable=YES
4、设置 虚拟用户主目录和权限
最新版vsftpd不允许用户主目录有w权限,因此在主目录下新建一个子目录,赋予700权限。所有上传、下载、删除、重命名等操作只能在子目录中进行
# mkdir -p /home/vsftp/ftphuawei/newdir
# chown -R vsftp.vsftp /home/vsftp
# chmod -R 500 /home/vsftp
# chmod -R 700 /home/vsftp/ftphuawei/newdir
# setsebool -P ftpd_full_access on
加入防火墙 或关闭防火墙
# iptables -I INPUT -p tcp --dport 21 -j ACCEPT #FTP连接端口
# iptables -I INPUT -p tcp --dport 10000:15000 -j ACCEPT #pasv模式下的随机端口
# iptables-save >/etc/sysconfig/iptables #保存防火墙配置
重启
# systemctl restart iptables.service
# systemctl restart vsftpd.service
5、报错处理
报错
Sep 21 01:32:42 ftp-server systemd: Starting Vsftpd ftp daemon...
Sep 21 01:32:42 ftp-server vsftpd: 500 OOPS: bad bool value in config file for: chroot_list_enable
Sep 21 01:32:42 ftp-server systemd: vsftpd.service: control process exited, code=exited status=2
Sep 21 01:32:42 ftp-server systemd: Failed to start Vsftpd ftp daemon.
Sep 21 01:32:42 ftp-server systemd: Unit vsftpd.service entered failed state.
Sep 21 01:32:42 ftp-server systemd: vsftpd.service failed.
重新检查配置文件,去掉以#开头的行和空行
grep -Ev '^[[:space:]].*|^#' filename
sed -e '/^[[:space:]].*/d' filename -e '/^#/d'
[root@ftp-server vsftpd]# grep -Ev '^[[:space:]].*|^#' vsftpd.conf
anonymous_enable=NO
local_enable=YES
write_enable=YES
local_umask=022
dirmessage_enable=YES
xferlog_enable=YES
connect_from_port_20=NO
xferlog_std_format=YES
chroot_local_user=YES
chroot_list_enable=YES
chroot_list_file=/etc/vsftpd/chroot_list
listen=YES
listen_ipv6=NO
pam_service_name=vsftpd
userlist_enable=YES
tcp_wrappers=YES
virtual_use_local_privs=NO
guest_enable=YES
guest_username=vsftp
user_config_dir=/etc/vsftpd/vuser_conf
pasv_enable=YES
pasv_min_port=10000
pasv_max_port=150000
新建虚拟用户
[root@ftp-server /]# cat /etc/vsftpd/vuser
ftphuawei
12#$
userftp
12#$
[root@ftp-server /]# cat /etc/vsftpd/vuser_conf/userftp
local_root=/home/vsftp/userftp
anon_umask=077
anon_world_readable_only=NO
anon_upload_enable=YES
anon_mkdir_write_enable=YES
anon_other_write_enable=YES
[root@ftp-server /]# mkdir -p /home/vsftp/userftp/datafile
# chmod -R 700 /home/vsftp/userftp/datafile
[root@ftp-server /]# chown -R vsftp:vsftp /home/vsftp/userftp
[root@ftp-server /]# chmod -R 500 /home/vsftp/userftp
# chmod -R 700 /home/vsftp/userftp/datafile
6、简单介绍下ftp主动模式与ftp被动模式
主动模式下,FTP客户端从任意的非特殊的端口(N > 1023)连入到FTP服务器的命令端口--21端口。然后客户端在N+1(N+1 >= 1024)端口监听,并且通过N+1(N+1 >= 1024)端口发送命令给FTP服务器。服务器会反过来连接用户本地指定的数据端口,比如20端口。
以服务器端防火墙为立足点,要支持主动模式FTP需要打开如下交互中使用到的端口:
- FTP服务器命令(21)端口接受客户端任意端口(客户端初始连接)
- FTP服务器命令(21)端口到客户端端口(>1023)(服务器响应客户端命令)
- FTP服务器数据(20)端口到客户端端口(>1023)(服务器初始化数据连接到客户端数据端口)
FTP服务器数据(20)端口接受客户端端口(>1023)(客户端发送ACK包到服务器的数据端口)
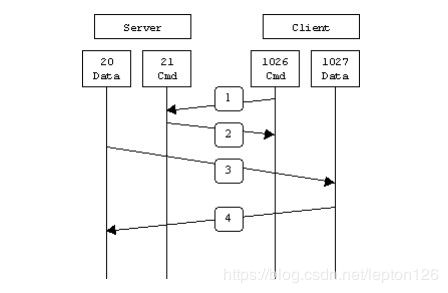
在第1步中,客户端的命令端口与FTP服务器的命令端口建立连接,并发送命令“PORT 1027”。然后在第2步中,FTP服务器给客户端的命令端口返回一个"ACK"。在第3步中,FTP服务器发起一个从它自己的数据端口(20)到客户端先前指定的数据端口(1027)的连接,最后客户端在第4步中给服务器端返回一个"ACK"。
主动方式FTP的主要问题实际上在于客户端。FTP的客户端并没有实际建立一个到服务器数据端口的连接,它只是简单的告诉服务器自己监听的端口号,服务器再回来连接客户端这个指定的端口。对于客户端的防火墙来说,这是从外部系统建立到内部客户端的连接,这是通常会被阻塞的。
被动模式FTP
为了解决服务器发起到客户的连接的问题,人们开发了一种不同的FTP连接方式。这就是所谓的被动方式,或者叫做PASV,当客户端通知服务器它处于被动模式时才启用。
在被动方式FTP中,命令连接和数据连接都由客户端,这样就可以解决从服务器到客户端的数据端口的入方向连接被防火墙过滤掉的问题。当开启一个FTP连接时,客户端打开两个任意的非特权本地端口(N >; 1024和N+1)。第一个端口连接服务器的21端口,但与主动方式的FTP不同,客户端不会提交PORT命令并允许服务器来回连它的数据端口,而是提交PASV命令。这样做的结果是服务器会开启一个任意的非特权端口(P >; 1024),并发送PORT P命令给客户端。然后客户端发起从本地端口N+1到服务器的端口P的连接用来传送数据。
对于服务器端的防火墙来说,必须允许下面的通讯才能支持被动方式的FTP:
- FTP服务器命令(21)端口接受客户端任意端口(客户端初始连接)
- FTP服务器命令(21)端口到客户端端口(>1023)(服务器响应客户端命令)
- FTP服务器数据端口(>1023)接受客户端端口(>1023)(客户端初始化数据连接到服务器指定的任意端口)
FTP服务器数据端口(>1023)到客户端端口(>1023)(服务器发送ACK响应和数据到客户端的数据端口)
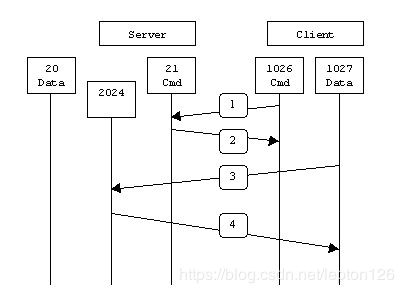
在第1步中,客户端的命令端口与服务器的命令端口建立连接,并发送命令“PASV”。然后在第2步中,服务器返回命令"PORT 2024",告诉客户端(服务器)用哪个端口侦听数据连接。在第3步中,客户端初始化一个从自己的数据端口到服务器端指定的数据端口的数据连接。最后服务器在第4 步中给客户端的数据端口返回一个"ACK"响应。