openssl 自签发证书及ssl 原理简介(一)
提纲:
1、使用openssl自签发证书
2、配置apache
3、配置客户端
4、使用自签发证书访问apache
一、使用Openssl自签发证书
首先装openssl 。编辑配置文件/etc/ssl/openssl.conf ,配置TSA root dir 等以下配置
[ tsa_config1 ]
# These are used by the TSA reply generation only.
dir = ./demoCA # TSA root directory
serial = $dir/serial # The current serial number (mandatory)
crypto_device = builtin # OpenSSL engine to use for signing
signer_cert = $dir/cacert.pem # The TSA signing certificate
# (optional)
certs = $dir/cacert.pem # Certificate chain to include in reply
# (optional)
signer_key = $dir/private/cakey.pem # The TSA private key (optional)
然后就可以生成CA以及server、user的证书了。
1、建立cert文件结构。
root@ubuntu:~/certs# mkdir -p ./demoCA/{private,newcerts}
root@ubuntu:~/certs# touch ./demoCA/index.txt
root@ubuntu:~/certs# echo 01 > ./demoCA/serial2、生成CA私钥与CA证书。
openssl genrsa -des3 -out ./demoCA/private/cakey.pem 2048
Generating RSA private key, 2048 bit long modulus
.+++
............+++
e is 65537 (0x10001)
Enter pass phrase for ./demoCA/private/cakey.pem:
Verifying - Enter pass phrase for ./demoCA/private/cakey.pem:
root@ubuntu:~/certs# openssl req -new -x509 -days 365 -key ./demoCA/private/cakey.pem -out ./demoCA/cacert.pem
Enter pass phrase for ./demoCA/private/cakey.pem:
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
-----
Country Name (2 letter code) [AU]:cn
State or Province Name (full name) [Some-State]:Asia
Locality Name (eg, city) []:bj
Organization Name (eg, company) [Internet Widgits Pty Ltd]:
Organizational Unit Name (eg, section) []:
Common Name (e.g. server FQDN or YOUR name) []:lyw
Email Address []:
4、生成user 私钥、证书。
root@ubuntu:~/certs# openssl genrsa -des3 -out userkey.pem
Generating RSA private key, 2048 bit long modulus
................................................+++
...+++
e is 65537 (0x10001)
Enter pass phrase for userkey.pem:
Verifying - Enter pass phrase for userkey.pem:
root@ubuntu:~/certs# openssl req -new -days 365 -key userkey.pem -out userreq.pem
Enter pass phrase for userkey.pem:
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
-----
Country Name (2 letter code) [AU]:cn
State or Province Name (full name) [Some-State]:Asia
Locality Name (eg, city) []:BJ
Organization Name (eg, company) [Internet Widgits Pty Ltd]:
Organizational Unit Name (eg, section) []:abc
Common Name (e.g. server FQDN or YOUR name) []:abc
Email Address []:
Please enter the following 'extra' attributes
to be sent with your certificate request
A challenge password []:
An optional company name []:
root@ubuntu:~/certs# openssl ca -in userreq.pem -out usercert.pem
Using configuration from /usr/lib/ssl/openssl.cnf
Enter pass phrase for ./demoCA/private/cakey.pem:
Check that the request matches the signature
Signature ok
Certificate Details:
Serial Number: 1 (0x1)
Validity
Not Before: Jul 17 19:14:18 2015 GMT
Not After : Jul 16 19:14:18 2016 GMT
Subject:
countryName = cn
stateOrProvinceName = Asia
organizationName = Internet Widgits Pty Ltd
organizationalUnitName = abc
commonName = abc
X509v3 extensions:
X509v3 Basic Constraints:
CA:FALSE
Netscape Comment:
OpenSSL Generated Certificate
X509v3 Subject Key Identifier:
DE:90:9F:7B:A3:58:0C:D4:32:5A:2E:E0:40:BC:6B:25:3B:F9:3D:28
X509v3 Authority Key Identifier:
keyid:DD:E5:B1:AA:36:1F:F2:95:A8:0A:DD:51:2E:3D:BB:9A:F3:7B:8C:57
Certificate is to be certified until Jul 16 19:14:18 2016 GMT (365 days)
Sign the certificate? [y/n]:y
1 out of 1 certificate requests certified, commit? [y/n]y
Write out database with 1 new entries
Data Base Updated
5. 生成server 私钥与证书
openssl genrsa -des3 -out serverkey.pem
Generating RSA private key, 2048 bit long modulus
.........................................................................................+++
....+++
e is 65537 (0x10001)
Enter pass phrase for serverkey.pem:
Verifying - Enter pass phrase for serverkey.pem:
root@ubuntu:~/certs# openssl req -new -days 365 -key serverkey.pem -out serverreq.pem
Enter pass phrase for serverkey.pem:
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.-----Country Name (2 letter code) [AU]:cnState or Province Name (full name) [Some-State]:AsiaLocality Name (eg, city) []:BJOrganization Name (eg, company) [Internet Widgits Pty Ltd]:Organizational Unit Name (eg, section) []:Common Name (e.g. server FQDN or YOUR name) []:lywEmail Address []:Please enter the following 'extra' attributesto be sent with your certificate requestA challenge password []:An optional company name []:root@ubuntu:~/certs# openssl ca -in serverreq.pem -out servercert.pemUsing configuration from /usr/lib/ssl/openssl.cnfEnter pass phrase for ./demoCA/private/cakey.pem:Check that the request matches the signatureSignature okCertificate Details: Serial Number: 2 (0x2) Validity Not Before: Jul 17 19:25:24 2015 GMT Not After : Jul 16 19:25:24 2016 GMT Subject: countryName = cn stateOrProvinceName = Asia organizationName = Internet Widgits Pty Ltd commonName = lyw X509v3 extensions: X509v3 Basic Constraints: CA:FALSE Netscape Comment: OpenSSL Generated Certificate X509v3 Subject Key Identifier: 5D:F4:01:21:6A:2D:28:58:24:0E:DC:66:10:4D:65:40:72:C4:04:22 X509v3 Authority Key Identifier: keyid:DD:E5:B1:AA:36:1F:F2:95:A8:0A:DD:51:2E:3D:BB:9A:F3:7B:8C:57Certificate is to be certified until Jul 16 19:25:24 2016 GMT (365 days)Sign the certificate? [y/n]:y1 out of 1 certificate requests certified, commit? [y/n]yWrite out database with 1 new entriesData Base Updated二、apache服务器。
首先装apache。更改配置文件 /usr/local/apache2/conf/extra/httpd-ssl.conf
更改:
SSLCertificateFile "/root/certs/server.crt"
SSLCertificateKeyFile "/root/certs/server.key"SSLCACertificatePath "/root/certs/demoCA/"
SSLCACertificateFile "/root/certs/demoCA/cacert.pem"
启动apache服务器。
/usr/local/apache2/bin/apachectl start
httpd: Could not reliably determine the server's fully qualified domain name, using 127.0.1.1 for ServerName
Apache/2.2.29 mod_ssl/2.2.29 (Pass Phrase Dialog)
Some of your private key files are encrypted for security reasons.
In order to read them you have to provide the pass phrases.
Server lyw:443 (RSA)
Enter pass phrase:
OK: Pass Phrase Dialog successful.为客户生成可以导入浏览器的格式。
openssl pkcs12 -export -clcerts -in usercert.pem -inkey userkey.pem -out user.p12
Enter pass phrase for userkey.pem:
Enter Export Password:
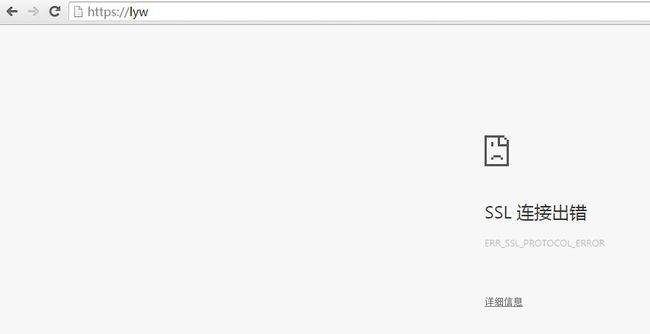
Verifying - Enter Export Password:不导入证书时访问。
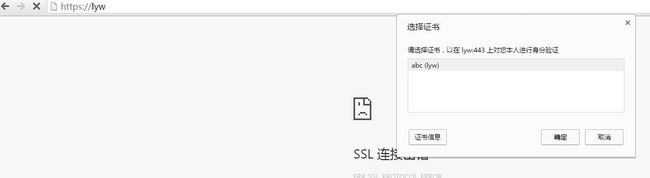
此时可以查看证书的信息,和生成证书请求时填的信息一样,点击确定。
由于此证书的颁发者不是浏览器信任的CA,所以会有这个告警,点击高级,继续前往。
至此,已经可以使用自己生成的CA、客户端证书访问服务器了。
当然要设置本地Host文件。
下一节,我们根据ssl访问过程分析SSL原理。
参考:http://netkiller.github.io/cryptography/openssl/email.html