升级Https前的可行性验证(一)
升级Https之前的可行性验证
注意:自签证书和Nginx的安装都基于ContOS 6
一、如何申请OpenSSL自签证书
1、安装OpenSSL
(一)OpenSSL 工具下载
下载地址
(二)OpenSSL 安装
参考博客
查看服务器是否安装有OpenSSL
openssl version -a将下载的OpenSSL源码上传至Linux服务器
可以使用Xshell的Xftp工具。
解压上传的.tar.gz压缩包
tar -zxvf openssl-1.1.1-pre8.tar.gz安装gcc编译器,如果已经安装请略过
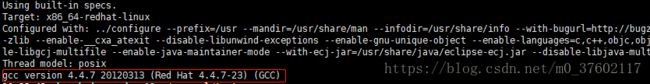
#如果系统安装了gcc编译器,如下图所示的gcc version gcc -v #安装gcc yum install gcc-c++
安装zlib库,如果已经安装请略过
#检查是否安装zlib,如果安装如下图所示 whereis zlib #获取zlib源码包 wget http://zlib.net/zlib-1.2.11.tar.gz #切换到zlib源码包中 cd zlib-1.2.11 #安装zlib ./configure && make && make install
安装OpenSSL工具
#首先进入OpenSSL工具解压之后的目录 cd openssl-1.1.1-pre8 #--prefix=指定的安装路径 ./config shared zlib --prefix=/usr/local/openssl && make && make install #安装完成之后再当前目录再执行下面命令 ./config -t make depend #然后进入OpenSSL的安装目录 cd /usr/local #建立文件链接 ln -s openssl ssl #打开etc下的这个ld.so.conf配置文件,然后再文本中添加/usr/local/openssl/lib vim /etc/ld.so.conf #执行命令使文件链接共享生效 ldconfig环境变量配置
#打开etc目录下的profile文件 vim /etc/profile #然后再文件的末尾添加如下内容 export OPENSSL=/usr/local/openssl/bin export PATH=$OPENSSL:$PATH:$HOME/bin重开命令窗口,加载环境变量
2、自签证书
参考博客
(一)生成根证书
生成.key后缀私钥
#生成私钥到指定目录 openssl genrsa -out /usr/local/nginx/conf/rootca.key生成.csr后缀的证书申请文件
#通过私钥生成申请文件到指定目录 openssl req -new -key /usr/local/nginx/conf/rootca.key -out /usr/local/nginx/conf/rootca.csr生成.crt后缀的证书文件
#通过私钥和证书申请文件,来自签证书 openssl x509 -req -days 3650 -in /usr/local/nginx/conf/rootca.csr -signkey /usr/local/nginx/conf/rootca.key -out /usr/local/nginx/conf/rootca.crt
(二)通过根证书签发服务端证书
生成.key后缀私钥
#生成服务端私钥 openssl genrsa -out /usr/local/nginx/conf/server.key生成.csr后缀的证书申请文件
#生成服务端证书申请文件 openssl req -new -key /usr/local/nginx/conf/server.key -out /usr/local/nginx/conf/server.csr生成.crt后缀的证书文件
#签发服务端证书文件 openssl ca -in /usr/local/nginx/conf/server.csr -cert /usr/local/nginx/conf/rootca.crt -keyfile /usr/local/nginx/conf/rootca.key -out /usr/local/nginx/conf/server.crt
二、Nginx 安装
1、安装Nginx
参考博客
(一)下载相关源码包
下载Nginx源码包
#通过wget命令来远程获取源码包到当前目录 wget http://nginx.org/download/nginx-1.15.2.tar.gz ./下载Pcre源码包
#通过wget命令来远程获取源码包到当前目录 wget ftp://ftp.csx.cam.ac.uk/pub/software/programming/pcre/pcre-8.40.tar.gz ./
(二)安装
安装Pcre
#解压压缩包 tar -zxvf pcre-8.40.tar.gz #切换到解压的目录中 cd ./pcre-8.40 #安装 ./configure && make && make install安装Nginx
#解压压缩包 tar -zxvf nginx-1.15.2.tar.gz #切换到解压的目录中 cd ./nginx-1.15.2 #安装 ./configure && make && make install
2、安装Https模块
参考博客
如果之前有安装过Nginx并且配置过nginx.conf,那么一定先做备份
#备份配置文件,前面是文件名,后面携带备份时间 cp nginx.conf ./nginx.conf.2018816 #备份安装目录sbin中 nginx运行文件 cp ./nginx/sbin/nginx ./nginx/sbin/nginx2018816在源码目录下安装Https模块
#备份安装目录sbin中 nginx运行文件 cp ./nginx/sbin/nginx ./nginx/sbin/nginx2018816 #先cd到源码包中 #获取https模块到指定目录 ./configure --prefix=./nginx --with-http_stub_status_module --with-http_ssl_module #编译 make #将编译好的nginx运行文件复制到安装目录的sbin中 cp ./objs/nginx /usr/local/nginx/sbin/验证Https模块是否安装成功
#通过命令查看Https模块是否安装成功,如果安装成功如下图所示 /usr/local/nginx/sbin/nginx -V
3、启动Nginx验证是否安装成功
Nginx 常用的一些命令
#测试nginx.conf文件是否配置正确 ./sbin/nginx -t #启动nginx ./sbin/nginx #重启 ./sbin/nginx -s reload启动Nginx
访问Nginx部署的服务器ip地址,出现如下图所示页面则表示安装成功。
三、Nginx 配置
1、Nginx 配置Https
(一)配置端口监听
listen 443 ssl;
server_name 10.3.1.2;(二)配置证书
ssl_certificate /usr/local/nginx/conf/server.crt;
ssl_certificate_key /usr/local/openssl/bin/nopass-server.key;(三)其他参数配置
ssl_session_cache shared:SSL:1m;
ssl_session_timeout 5m;
server_tokens off;
ssl_ciphers HIGH:!aNULL:!MD5;
ssl_prefer_server_ciphers on;
2、Nginx 配置请求重定向和代理
location = /xxx {
return 302 http://10.3.1.2:18080/bms_core;
}
location = /bms_core/ {
proxy_set_header Host $host:$server_port;
proxy_set_header X-Real-IP $remote_addr;
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for;
proxy_pass http://10.3.1.1:18080;
}
3、Nginx 配置项目静态资源
location ~ \.(gif|jpg|png|js|css)$ {
proxy_set_header Host $host:$server_port;
proxy_set_header X-Real-IP $remote_addr;
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for;
proxy_pass http://10.3.1.1:18080;
}4、Nginx Http和Https共存
server {
listen 80;
server_name 10.3.1.2;
location / {
root html;
index index.html index.htm;
}
location = /bms_core/ {
proxy_set_header X-Real-IP $remote_addr;
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for;
proxy_set_header Host $host:$server_port;
proxy_pass http://10.3.1.1:18080;
#return 302 http://10.3.1.2:18080/bms_core;
}
location ~ \.(gif|jpg|png|js|css)$ {
proxy_set_header Host $host:$server_port;
proxy_set_header X-Real-IP $remote_addr;
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for;
proxy_pass http://10.3.1.1:18080;
}
location = /bms {
return 302 http://10.3.1.2:18080/bms_core;
}
}
5、我的nginx.conf配置文件的完整配置
worker_processes 4;
events {
worker_connections 1024;
}
http {
include mime.types;
default_type application/octet-stream;
log_format main '$remote_addr - $remote_user [$time_local] "$request" '
'$status $body_bytes_sent "$http_referer" '
'"$http_user_agent" "$http_x_forwarded_for"';
access_log /usr/local/nginx/logs/access.log main;
sendfile on;
keepalive_timeout 65;
upstream my_server{
server 10.3.1.2:3128 weight=5 ;
server 10.3.1.2:80 weight=1;
}
server {
listen 80;
server_name 10.3.1.2;
location / {
root html;
index index.html index.htm;
}
location = /bms_core/ {
proxy_set_header X-Real-IP $remote_addr;
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for;
proxy_set_header Host $host:$server_port;
proxy_pass http://10.3.1.1:18080;
#return 302 http://10.3.1.2:18080/bms_core;
}
location ~ \.(gif|jpg|png|js|css)$ {
proxy_set_header Host $host:$server_port;
proxy_set_header X-Real-IP $remote_addr;
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for;
proxy_pass http://10.3.1.1:18080;
}
location = /bms {
return 302 http://10.3.1.2:18080/bms_core;
}
}
server {
listen 443 ssl;
server_name 10.3.1.2;
ssl_certificate /usr/local/nginx/conf/server.crt;
ssl_certificate_key /usr/local/openssl/bin/nopass-server.key;
ssl_session_cache shared:SSL:1m;
ssl_session_timeout 5m;
server_tokens off;
ssl_ciphers HIGH:!aNULL:!MD5;
ssl_prefer_server_ciphers on;
location / {
root html;
index index.html index.htm;
}
location = /xxx {
return 302 http://10.3.1.2:18080/bms_core;
}
location = /bms_core/ {
proxy_set_header Host $host:$server_port;
proxy_set_header X-Real-IP $remote_addr;
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for;
proxy_pass http://10.3.1.1:18080;
}
location ~ \.(gif|jpg|png|js|css)$ {
proxy_set_header Host $host:$server_port;
proxy_set_header X-Real-IP $remote_addr;
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for;
proxy_pass http://10.3.1.1:18080;
}
}
}
四、验证Client到Nginx Https请求是否生效,Https请求中是否建立SSL握手
1、验证Https模块和Https Server配置是否生效
(一)通过使用Https请求Nginx
(二)需要注意的点
使用OpenSSL进行自签证书,所得证书是不能被浏览器所信任的。
如果实际业务并没有浏览器与服务端交互,那么就可以使用OpenSSL进行自签证书,签发证书的目的只是为了单纯的使用Https请求来提高数据安全性,关于Https为什么安全,请参考下面博客。
Https参考博客
SSL/TLS握手参考博客
如果需要使用到受浏览器信任的CA证书,可以参考下面博客对CA证书签发机构的介绍,自己选择哪个签来机构来签发自己的受信任CA证书。
收费证书申请推荐
免费证书签发机构参考博客
2、Tcpdump使用
参考博客
#查看网卡名命令
ifconfig
#通过tcpdump抓包
#eth0为网卡名
#host 10.2.1.254为发起请求的客户端ip地址
#-w ./eth1.cap是将抓包信息输出到指定目录下指定文件中
tcpdump -i eth0 host 10.2.1.254 -w ./eth1.cap3、Wireshark使用
参考博客
(一)查看抓包信息
在Wireshark中点击文件,然后打开抓包文件。
(二)查看TCP传输流
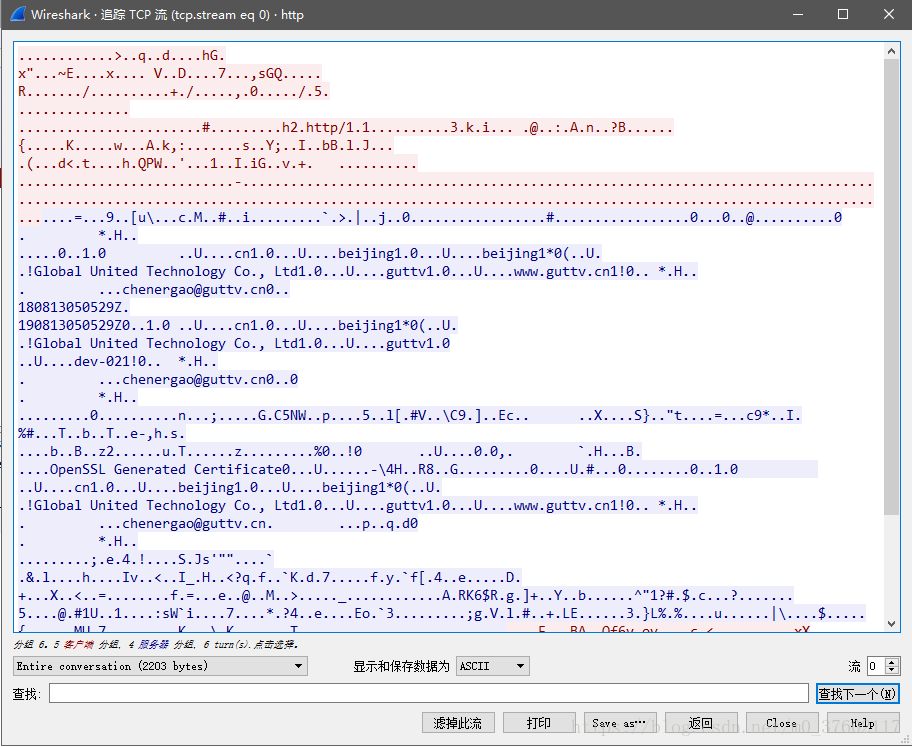
点击请求,然后右键追踪TCP流。
4、抓取Http请求
(一)查看是否发起Http请求
(二)追踪TCP流,查看数据包在TCP传输过程中是否是明文
5、抓取Https请求
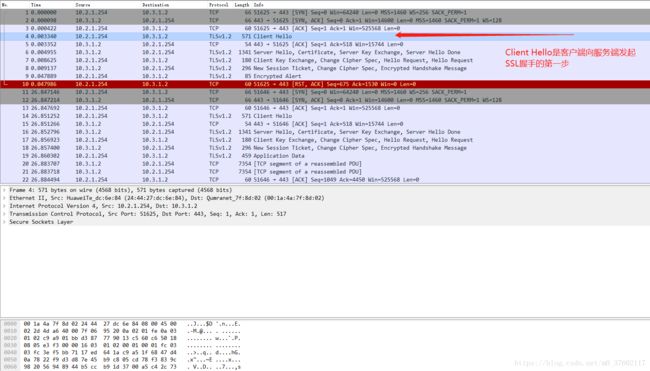
(一)查看是否建立握手
(二)追踪TCP流,查看数据包是否加密
6、结论
(一)Http
通过Client向服务端发起的Http请求看到,客户端向服务端发起Http请求,并且通过追踪TCP流可以看到数据是明文传输没有被加密。
(二)Https
通过Client向服务端发起的Https请求看到,中间建立了TLS握手,并且通过追踪TCP流可以看到数据是使用对称加密后的数据。