- java8的stream流常用用法sorted
l1o3v1e4ding
后端开发热点代码java开发语言
java8的stream流常用用法持续更新~~,用法案例,项目开发中方便寻找一.排序stream().sorted()1.缺省排序字段:以类属性一升序排序2.带排序字段:以类属性一升序排序,推荐Comparator.reverseOrder()2.1.升序:不加参数即可2.2.降序:reversed()和Comparator.reverseOrder(),有区别:2.3.案例:注意两种写法3.多属
- Django学习笔记:(五)模板过滤器
码农葫芦侠
Djangodjango学习笔记
模板过滤器1简介2语法3常见过滤器3.1add3.2addslashes3.3center3.4cut3.6date3.6default3.7default_if_none3.8dictsort3.9dictsortreversed3.10lower3.11filesizeformat3.12upper3.13first3.14last3.15floatformat3.16iriencode3.1
- 前端-VUE-页面布局-flex布局整理-傻瓜教学
偏偏潇洒程序员
1.flex-direction:设置容器内部元素的排列方向row:定义排列方向从左到右row-reverse:从右到左column:从上到下column-reverse:从下到上图片介绍flex-direction:rowflex-direction:row-reverseflex-direction:columnflex-direction:column-reverse2.flex-:定义fl
- react实现全选和反选_react实现全选和反选
classCheckboxcomponentextendsReact.Component{constructor(props){super(props);this.state={chooseList:['apple','lemon','melon','orange'],chooseCheck:0,Allchoose:false,reverseCheck:false,isAuto:false}}Al
- STL的stack和queue(二):反向迭代器的实现(了解)
目录list的反向迭代器节点模板list模板正向迭代器的类模板反向迭代器的类模板完整代码list.h文件ReverseIterator.h文件test.cpp文件list的反向迭代器迭代器的适配器模式:编写一个通用的反向迭代器类模板,传递不同容器的正向迭代器,编译器将自动生成这些容器的反向迭代器,减少代码的重复实现,简化编程节点模板templatestructListNode{ListNode*_
- 通过“逆向侦测”驾驭涌现复杂性的认知架构与技术实现
由数入道
架构认知框架人工智能思维模型
摘要(ExecutiveSummary)我们正处在一个由人工智能驱动的“寒武纪大爆发”时代,复杂性本身正在经历一次相变。面对这一现实,渐进式的分析优化已然失效,唯有通过构建一种全新的认知架构——“逆向侦测”(ReverseDetection),才能在混沌中驾驭涌现的力量。本报告旨在提供该架构的终极蓝图,涵盖从哲学基石到技术实现,再到组织重塑的完整路径。一个基本的理论内核:“前兆复合体”(Precu
- PostgreSQL - PostgreSQL 反向查询策略(使用 ORDER BY、使用游标、使用窗口函数、使用 LIMIT 与 OFFSET 组合)
我命由我12345
数据库postgresql数据库后端mybatisjava-eejavaintellij-idea
概述PostgreSQL反向查询,指的从尾开始查询,即按照与默认顺序相反的顺序查询一、使用ORDERBY反向查询所有数据SELECT*FROM【表名】ORDERBYidDESC;反向查询1条数据SELECT*FROM【表名】ORDERBYidDESCLIMIT1;二、使用游标1、具体实现BEGIN;DECLAREreverse_cursorSCROLLCURSORFORSELECT*FROM【表名
- 力扣-206.反转链表
এ᭄画画的北北
java二刷力扣hot100leetcode链表算法
题目链接206.反转链表publicclassListNode{intval;ListNodenext;ListNode(){}ListNode(intval){this.val=val;}ListNode(intval,ListNodenext){this.val=val;this.next=next;}classSolution{publicListNodereverseList(ListNo
- 四旋翼无人机SIMULINK建模
四旋翼无人机SIMULINK建模,PSO_SA优化PID参数reverse.m作用:将History表中的string形式的key值转换为赋给九个全局变量temp00,…,temp08运行sum1.slx,可以直接观察此组参数的波形。History作用:映射表,将一组参数(temp00,…,temp08)映射到这组参数的ITAE指标。trojectory.m作用:定义一条路径并进行路径压缩,通过不
- python 排序函数
weixin_30256505
python
1、sorted()函数:内建函数,适用于所有类型,返回排序后的对象,原对象不改变,sorted(a,key=,reversed=True)>>>sorted((3,1,4,2))[1,2,3,4]>>>a=[4111,1,52,46,200,6,7]>>>sorted(a)[1,6,7,46,52,200,4111]2、sort()函数:>>>a.sort()>>>a[1,6,7,46,52,2
- 【数据结构】PTA 单链表分段逆转 C语言
小纭在努力
PTA数据结构c语言开发语言
给定一个带头结点的单链表和一个整数K,要求你将链表中的每K个结点做一次逆转。例如给定单链表1→2→3→4→5→6和K=3,你需要将链表改造成3→2→1→6→5→4;如果K=4,则应该得到4→3→2→1→5→6。函数接口定义:voidK_Reverse(ListL,intK);其中List结构定义如下:typedefstructNode*PtrToNode;structNode{ElementTyp
- Centos系统及国产麒麟系统设置自己写的go服务的开机启动项完整教程
二当家的素材网
运维centoslinux运维
1、创建服务文件在/etc/systemd/system/下新建服务配置文件(需sudo权限),例如:sudonano/etc/systemd/system/mygo.service如下图,创建的mygo.service2、创建内容如下:Description=ThegoHTTPandreverseproxyserverAfter=network.targetremote-fs.targetnss
- 网络安全-反弹shell详解(攻击,检测与防御)
程序员鱼
web安全网络安全单片机服务器linuxuni-app
反弹Shell:详解、攻击、检测与防御反弹Shell(ReverseShell)是一种网络安全领域中常见的攻击技术,通常用于远程控制受害者的计算机。本文旨在从网络安全的角度详细介绍反弹Shell的工作原理,实施方法以及如何检测和防御这类攻击。一、Shell的简介与原理1.1什么是Shell?Shell在计算机系统中指的是一个用户界面,用于访问操作系统的服务。在网络安全中,攻击者常利用Shell来控
- 科研:diffusion生成MNIST程序实现
Menger_Wen
科研:diffusion人工智能机器学习stablediffusionpython
科研:diffusion生成MNIST程序实现第一部分:填写部分的详细解释1.`diffusion.py`中的`batch_extend_like`方法2.`diffusion.py`中的`ode_reverse`方法3.`sde_schedule.py`中的`sde_forward`方法第二部分:逐行解释两个程序1.`diffusion.py`(Diffusion类)`__init__`方法`b
- 力扣 hot100 Day37
25.K个一组翻转链表给你链表的头节点head,每k个节点一组进行翻转,请你返回修改后的链表。k是一个正整数,它的值小于或等于链表的长度。如果节点总数不是k的整数倍,那么请将最后剩余的节点保持原有顺序。你不能只是单纯的改变节点内部的值,而是需要实际进行节点交换。//抄的classSolution{public:ListNode*reverseKGroup(ListNode*head,intk){i
- 陈强《计量经济学及Stata应用》学习笔记——持续更新
WangSoooCute
学习笔记
1导论1.1什么是计量经济学econometrics几种关系:相关关系、因果关系、逆向因果关系reversecausality、双向因果关系被解释变量dependentvariable解释变量explanatoryvariable=regressor=自变量independentvariable=协变量covariateunobservable的误差项errorterm=随机扰动项stochast
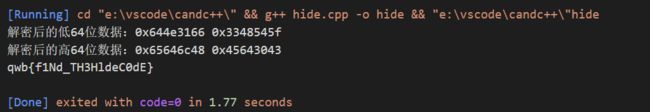
- CTF-reverse逆向分析解题常用脚本汇总
晴友读钟
#逆向ctfreverse
注:本篇用于记录一些CTF-reverse中可能用上的脚本,脚本都来源于博主解出某道题后留下,如果遇上类似的题目,根据脚本中注释的提示更改对应的密文密钥或条件即可快速解题!持续更新!!点个收藏关注不迷路~常见解密系列这块是烂大街的各种加密,可以说这里任何一个加密都八成会出现在题目中的脚本只是模板,重点是学会找到密文密钥并套入进去,因此需要对脚本的原理(比如调用函数的方式和密文密钥的格式之类)稍微有
- 【算法训练营Day07】字符串part1
文章目录反转字符串反转字符串II替换数字反转字符串题目链接:344.反转字符串双指针法,两个指针的元素直接调转即可classSolution{publicvoidreverseString(char[]s){inthead=0;intend=s.length-1;while(head=k){reverseString(charArray,head,head+k-1);}else{reverseSt
- DAY08 算法训练营| 字符串part01
天空的孩子
算法
344.反转字符串-力扣(LeetCode)字符串和数组算法题目思路类似反转字符串是经典双指针法(回忆反转链表,有序数组的平方,三数之和,四数之和)classSolution{public:voidreverseString(vector&s){len=s.length();for(inti=0,j=s.size()-1;iusingnamespacestd;intmain(){strings;/
- Python内置函数--reversed()
它将一个序列作为输入,并返回另一个序列,其中元素的顺序与给定输入序列的顺序相反。它不会对原始序列产生任何影响。也就是在原列表的基础上返回一个新的反向列表。粗略的看看classreversed(Iterator[_T],Generic[_T]):@overloaddef__init__(self,__sequence:Reversible[_T])->None:...@overloaddef__in
- python内置函数reversed_python必备内置函数- reversed(seq)
weixin_39923599
python必备内置函数-abs()https://developer.aliyun.com/ask/280547python必备内置函数-all()https://developer.aliyun.com/ask/280560python必备内置函数-any()https://developer.aliyun.com/ask/280561python必备内置函数-ascii()https://d
- python模拟内置函数reversed_Python内置函数reversed
weixin_39594895
{"moduleinfo":{"card_count":[{"count_phone":1,"count":1}],"search_count":[{"count_phone":4,"count":4}]},"card":[{"des":"阿里技术人对外发布原创技术内容的最大平台;社区覆盖了云计算、大数据、人工智能、IoT、云原生、数据库、微服务、安全、开发与运维9大技术领域。","link1":
- python内置函数reversed_Python3内置函数——reversed() = 翻转我的世界
大龙说学区
v.颠倒(reverse的过去式和过去分词);翻转help(reversed)Helponclassreversedinmodulebuiltins:classreversed(object)|reversed(sequence)->reverseiteratorovervaluesofthesequence||Returnareverseiterator||Methodsdefinedhere:
- 百度识图API
weixin_34191845
pythonpostman
http://stu.baidu.com/http://www.360doc.com/content/14/0801/17/21412_398653199.shtmlhttp://download.csdn.net/download/namelijian/3449001http://icodon.com/reverse-image-search.htmlhttp://www.cnblogs.com
- 深入解析Linux分页机制:从虚拟内存到物理地址的魔法转换
pengdott
运维监控linux运维服务器
目录引言:为什么需要分页机制?一、分页机制基础概念1.1虚拟地址与物理地址1.2页与页框1.3为什么是4KB?二、多级页表结构2.1为什么需要多级页表?2.2x86_64的四级页表结构2.3页表项详解三、Linux分页实现机制3.1内核中的页表管理数据结构3.2地址转换过程3.3缺页异常处理四、高级话题与优化技术4.1大页(HugePage)支持4.2反向映射(ReverseMapping)4.3
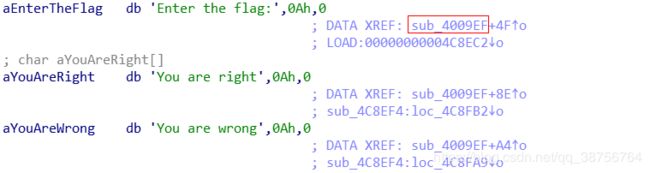
- iOS安全和逆向系列教程 第1篇: iOS逆向工程概述与学习路线图
自学不成才
iOS安全和逆向系列教程ios学习cocoa
iOS安全和逆向系列教程第1篇:iOS逆向工程概述与学习路线图欢迎各位加入我的iOS逆向工程专栏!在这个系列的第一篇文章中,我将为大家介绍iOS逆向工程的基本概念、应用场景以及完整的学习路线图,帮助大家建立清晰的学习框架。什么是iOS逆向工程?逆向工程(ReverseEngineering)是一种通过分析已有产品(如软件、硬件)来理解其设计、功能和工作原理的过程。在iOS领域,逆向工程特指通过各种
- 【蓝桥杯】第十五届省赛大学真题组真题解析
Jyywww121
蓝桥杯javascript职场和发展
【蓝桥杯】第十五届省赛大学真题组真题解析一、智能停车系统1、知识点(1)flex-wrap控制子元素的换行方式属性值有:no-wrap不换行wrap伸缩容器不够则自动往下换行wrap-reverse伸缩容器不够则自动往上换行(2)align-content调整多行侧轴对齐方式align-items调整单行侧轴对齐方式控制子元素在交叉轴上的对齐方式属性值有:flex-start侧轴的起始位置对齐fl
- Qt:QCustomPlot库的QCPAxis
十秒耿直拆包选手
CandC++QtandPysideQCustomPlotupqtQCustomPlotc++
在QCustomPlot中,QCPAxis是图表坐标系的核心组件,负责管理坐标轴的所有视觉和功能特性。它提供了丰富的定制选项,使开发者能够创建高度专业化的数据可视化图表。核心功能概述功能类别关键特性相关方法基本结构坐标轴位置、方向axisType(),setVisible()范围控制数据范围设置setRange(),setRangeReversed()刻度系统主/副刻度、格式setTicker()
- 字符串反转
伊欧温
C语言刷题记录c语言算法
题目描述字符串反转,如将字符串“www.runoob.com”反转为“moc.boonur.www”。程序分析:先通过指针遍历字符串计算其长度,确定参与交换的字符范围,再利用循环,以对称位置(从两端向中间)的方式,借助临时变量交换对应字符,实现字符串的反转。源代码#includevoidreverse(char*s){intlen=0;char*p=s;while(*p!=0){len++;p++
- 使用FRP 0.58版本进行内网穿透的详细教程
搬砖的小熊猫
frp
什么是FRP?FRP(FastReverseProxy)是一款高性能的反向代理应用,主要用于内网穿透。通过FRP,您可以将内网服务暴露给外网用户,无需进行复杂的网络配置。准备工作服务器:一台具备公网IP的服务器,用于部署FRP服务端。客户端:需要进行内网穿透的设备。FRP程序:可以从FRP官方GitHub页面下载最新版本。部署步骤服务器A(具有公共IP地址)解压并放置frps二进制文件和frps.
- 统一思想认识
永夜-极光
思想
1.统一思想认识的基础,才能有的放矢
原因:
总有一种描述事物的方式最贴近本质,最容易让人理解.
如何让教育更轻松,在于找到最适合学生的方式.
难点在于,如何模拟对方的思维基础选择合适的方式. &
- Joda Time使用笔记
bylijinnan
javajoda time
Joda Time的介绍可以参考这篇文章:
http://www.ibm.com/developerworks/cn/java/j-jodatime.html
工作中也常常用到Joda Time,为了避免每次使用都查API,记录一下常用的用法:
/**
* DateTime变化(增减)
*/
@Tes
- FileUtils API
eksliang
FileUtilsFileUtils API
转载请出自出处:http://eksliang.iteye.com/blog/2217374 一、概述
这是一个Java操作文件的常用库,是Apache对java的IO包的封装,这里面有两个非常核心的类FilenameUtils跟FileUtils,其中FilenameUtils是对文件名操作的封装;FileUtils是文件封装,开发中对文件的操作,几乎都可以在这个框架里面找到。 非常的好用。
- 各种新兴技术
不懂事的小屁孩
技术
1:gradle Gradle 是以 Groovy 语言为基础,面向Java应用为主。基于DSL(领域特定语言)语法的自动化构建工具。
现在构建系统常用到maven工具,现在有更容易上手的gradle,
搭建java环境:
http://www.ibm.com/developerworks/cn/opensource/os-cn-gradle/
搭建android环境:
http://m
- tomcat6的https双向认证
酷的飞上天空
tomcat6
1.生成服务器端证书
keytool -genkey -keyalg RSA -dname "cn=localhost,ou=sango,o=none,l=china,st=beijing,c=cn" -alias server -keypass password -keystore server.jks -storepass password -validity 36
- 托管虚拟桌面市场势不可挡
蓝儿唯美
用户还需要冗余的数据中心,dinCloud的高级副总裁兼首席营销官Ali Din指出。该公司转售一个MSP可以让用户登录并管理和提供服务的用于DaaS的云自动化控制台,提供服务或者MSP也可以自己来控制。
在某些情况下,MSP会在dinCloud的云服务上进行服务分层,如监控和补丁管理。
MSP的利润空间将根据其参与的程度而有所不同,Din说。
“我们有一些合作伙伴负责将我们推荐给客户作为个
- spring学习——xml文件的配置
a-john
spring
在Spring的学习中,对于其xml文件的配置是必不可少的。在Spring的多种装配Bean的方式中,采用XML配置也是最常见的。以下是一个简单的XML配置文件:
<?xml version="1.0" encoding="UTF-8"?>
<beans xmlns="http://www.springframework.or
- HDU 4342 History repeat itself 模拟
aijuans
模拟
来源:http://acm.hdu.edu.cn/showproblem.php?pid=4342
题意:首先让求第几个非平方数,然后求从1到该数之间的每个sqrt(i)的下取整的和。
思路:一个简单的模拟题目,但是由于数据范围大,需要用__int64。我们可以首先把平方数筛选出来,假如让求第n个非平方数的话,看n前面有多少个平方数,假设有x个,则第n个非平方数就是n+x。注意两种特殊情况,即
- java中最常用jar包的用途
asia007
java
java中最常用jar包的用途
jar包用途axis.jarSOAP引擎包commons-discovery-0.2.jar用来发现、查找和实现可插入式接口,提供一些一般类实例化、单件的生命周期管理的常用方法.jaxrpc.jarAxis运行所需要的组件包saaj.jar创建到端点的点到点连接的方法、创建并处理SOAP消息和附件的方法,以及接收和处理SOAP错误的方法. w
- ajax获取Struts框架中的json编码异常和Struts中的主控制器异常的解决办法
百合不是茶
jsjson编码返回异常
一:ajax获取自定义Struts框架中的json编码 出现以下 问题:
1,强制flush输出 json编码打印在首页
2, 不强制flush js会解析json 打印出来的是错误的jsp页面 却没有跳转到错误页面
3, ajax中的dataType的json 改为text 会
- JUnit使用的设计模式
bijian1013
java设计模式JUnit
JUnit源代码涉及使用了大量设计模式
1、模板方法模式(Template Method)
定义一个操作中的算法骨架,而将一些步骤延伸到子类中去,使得子类可以不改变一个算法的结构,即可重新定义该算法的某些特定步骤。这里需要复用的是算法的结构,也就是步骤,而步骤的实现可以在子类中完成。
- Linux常用命令(摘录)
sunjing
crondchkconfig
chkconfig --list 查看linux所有服务
chkconfig --add servicename 添加linux服务
netstat -apn | grep 8080 查看端口占用
env 查看所有环境变量
echo $JAVA_HOME 查看JAVA_HOME环境变量
安装编译器
yum install -y gcc
- 【Hadoop一】Hadoop伪集群环境搭建
bit1129
hadoop
结合网上多份文档,不断反复的修正hadoop启动和运行过程中出现的问题,终于把Hadoop2.5.2伪分布式安装起来,跑通了wordcount例子。Hadoop的安装复杂性的体现之一是,Hadoop的安装文档非常多,但是能一个文档走下来的少之又少,尤其是Hadoop不同版本的配置差异非常的大。Hadoop2.5.2于前两天发布,但是它的配置跟2.5.0,2.5.1没有分别。 &nb
- Anychart图表系列五之事件监听
白糖_
chart
创建图表事件监听非常简单:首先是通过addEventListener('监听类型',js监听方法)添加事件监听,然后在js监听方法中定义具体监听逻辑。
以钻取操作为例,当用户点击图表某一个point的时候弹出point的name和value,代码如下:
<script>
//创建AnyChart
var chart = new AnyChart();
//添加钻取操作&quo
- Web前端相关段子
braveCS
web前端
Web标准:结构、样式和行为分离
使用语义化标签
0)标签的语义:使用有良好语义的标签,能够很好地实现自我解释,方便搜索引擎理解网页结构,抓取重要内容。去样式后也会根据浏览器的默认样式很好的组织网页内容,具有很好的可读性,从而实现对特殊终端的兼容。
1)div和span是没有语义的:只是分别用作块级元素和行内元素的区域分隔符。当页面内标签无法满足设计需求时,才会适当添加div
- 编程之美-24点游戏
bylijinnan
编程之美
import java.util.ArrayList;
import java.util.Arrays;
import java.util.HashSet;
import java.util.List;
import java.util.Random;
import java.util.Set;
public class PointGame {
/**编程之美
- 主页面子页面传值总结
chengxuyuancsdn
总结
1、showModalDialog
returnValue是javascript中html的window对象的属性,目的是返回窗口值,当用window.showModalDialog函数打开一个IE的模式窗口时,用于返回窗口的值
主界面
var sonValue=window.showModalDialog("son.jsp");
子界面
window.retu
- [网络与经济]互联网+的含义
comsci
互联网+
互联网+后面是一个人的名字 = 网络控制系统
互联网+你的名字 = 网络个人数据库
每日提示:如果人觉得不舒服,千万不要外出到处走动,就呆在床上,玩玩手游,更不能够去开车,现在交通状况不
- oracle 创建视图 with check option
daizj
视图vieworalce
我们来看下面的例子:
create or replace view testview
as
select empno,ename from emp where ename like ‘M%’
with check option;
这里我们创建了一个视图,并使用了with check option来限制了视图。 然后我们来看一下视图包含的结果:
select * from testv
- ToastPlugin插件在cordova3.3下使用
dibov
Cordova
自己开发的Todos应用,想实现“
再按一次返回键退出程序 ”的功能,采用网上的ToastPlugins插件,发现代码或文章基本都是老版本,运行问题比较多。折腾了好久才弄好。下面吧基于cordova3.3下的ToastPlugins相关代码共享。
ToastPlugin.java
package&nbs
- C语言22个系统函数
dcj3sjt126com
cfunction
C语言系统函数一、数学函数下列函数存放在math.h头文件中Double floor(double num) 求出不大于num的最大数。Double fmod(x, y) 求整数x/y的余数。Double frexp(num, exp); double num; int *exp; 将num分为数字部分(尾数)x和 以2位的指数部分n,即num=x*2n,指数n存放在exp指向的变量中,返回x。D
- 开发一个类的流程
dcj3sjt126com
开发
本人近日根据自己的开发经验总结了一个类的开发流程。这个流程适用于单独开发的构件,并不适用于对一个项目中的系统对象开发。开发出的类可以存入私人类库,供以后复用。
以下是开发流程:
1. 明确类的功能,抽象出类的大概结构
2. 初步设想类的接口
3. 类名设计(驼峰式命名)
4. 属性设置(权限设置)
判断某些变量是否有必要作为成员属
- java 并发
shuizhaosi888
java 并发
能够写出高伸缩性的并发是一门艺术
在JAVA SE5中新增了3个包
java.util.concurrent
java.util.concurrent.atomic
java.util.concurrent.locks
在java的内存模型中,类的实例字段、静态字段和构成数组的对象元素都会被多个线程所共享,局部变量与方法参数都是线程私有的,不会被共享。
- Spring Security(11)——匿名认证
234390216
Spring SecurityROLE_ANNOYMOUS匿名
匿名认证
目录
1.1 配置
1.2 AuthenticationTrustResolver
对于匿名访问的用户,Spring Security支持为其建立一个匿名的AnonymousAuthenticat
- NODEJS项目实践0.2[ express,ajax通信...]
逐行分析JS源代码
Ajaxnodejsexpress
一、前言
通过上节学习,我们已经 ubuntu系统搭建了一个可以访问的nodejs系统,并做了nginx转发。本节原要做web端服务 及 mongodb的存取,但写着写着,web端就
- 在Struts2 的Action中怎样获取表单提交上来的多个checkbox的值
lhbthanks
javahtmlstrutscheckbox
第一种方法:获取结果String类型
在 Action 中获得的是一个 String 型数据,每一个被选中的 checkbox 的 value 被拼接在一起,每个值之间以逗号隔开(,)。
所以在 Action 中定义一个跟 checkbox 的 name 同名的属性来接收这些被选中的 checkbox 的 value 即可。
以下是实现的代码:
前台 HTML 代码:
- 003.Kafka基本概念
nweiren
hadoopkafka
Kafka基本概念:Topic、Partition、Message、Producer、Broker、Consumer。 Topic: 消息源(Message)的分类。 Partition: Topic物理上的分组,一
- Linux环境下安装JDK
roadrunners
jdklinux
1、准备工作
创建JDK的安装目录:
mkdir -p /usr/java/
下载JDK,找到适合自己系统的JDK版本进行下载:
http://www.oracle.com/technetwork/java/javase/downloads/index.html
把JDK安装包下载到/usr/java/目录,然后进行解压:
tar -zxvf jre-7
- Linux忘记root密码的解决思路
tomcat_oracle
linux
1:使用同版本的linux启动系统,chroot到忘记密码的根分区passwd改密码 2:grub启动菜单中加入init=/bin/bash进入系统,不过这时挂载的是只读分区。根据系统的分区情况进一步判断. 3: grub启动菜单中加入 single以单用户进入系统. 4:用以上方法mount到根分区把/etc/passwd中的root密码去除 例如: ro
- 跨浏览器 HTML5 postMessage 方法以及 message 事件模拟实现
xueyou
jsonpjquery框架UIhtml5
postMessage 是 HTML5 新方法,它可以实现跨域窗口之间通讯。到目前为止,只有 IE8+, Firefox 3, Opera 9, Chrome 3和 Safari 4 支持,而本篇文章主要讲述 postMessage 方法与 message 事件跨浏览器实现。postMessage 方法 JSONP 技术不一样,前者是前端擅长跨域文档数据即时通讯,后者擅长针对跨域服务端数据通讯,p