- Linux驱动开发: USB驱动开发
DS小龙哥
Linux系统编程与驱动开发linuxUSB驱动嵌入式
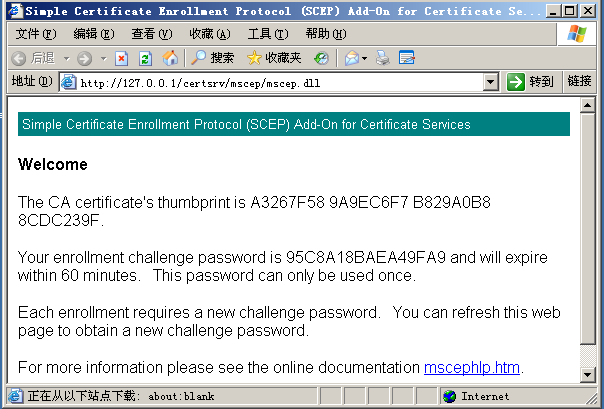
一、USB简介1.1什么是USB?USB是连接计算机系统与外部设备的一种串口总线标准,也是一种输入输出接口的技术规范,被广泛地应用于个人电脑和移动设备等信息通讯产品,USB就是简写,中文叫通用串行总线。最早出现在1995年,伴随着奔腾机发展而来。自微软在Windows98中加入对USB接口的支持后,USB接口才推广开来,USB设备也日渐增多,如数码相机、摄像头、扫描仪、游戏杆、打印机、键盘、鼠标等
- 使用 Microsoft OneDrive 加载文档的指南
shuoac
microsoftonedrivepython
技术背景介绍MicrosoftOneDrive(以前称为SkyDrive)是由微软运营的文件托管服务。通过OneDrive,你可以在云端存储和共享文档、照片、视频等数据。本文将介绍如何从OneDrive加载文档,目前支持的文件格式包括docx、doc和pdf。核心原理解析为了能够从OneDrive加载文档,需要进行以下几个步骤:注册应用程序以获取客户端ID和密钥。获取OneDrive的DriveI
- Azure AI Search Retriever 深度指南
bBADAS
azure人工智能flaskpython
技术背景介绍AzureAISearch(前称AzureCognitiveSearch)是微软提供的云端搜索服务,为开发者提供了强大的基础设施、API和工具,以扩展性地进行向量、关键词和混合查询的信息检索。AzureAISearchRetriever是一个集成模块,能够从非结构化查询中返回文档。它基于BaseRetriever类,并针对AzureAISearch的2023-11-01稳定RESTAP
- 阿里重磅模型深夜开源;DeepSeek宣布开源DeepGEMM;微软开源多模态AI Agent基础模型Magma...|网易数智日报
网易数智
网易数智日报开源人工智能大数据业界资讯aiAIGC
阿里重磅模型深夜开源:表现超越Sora、Pika,消费级显卡就能跑2月26日,25日深夜阿里云视频生成大模型万相2.1(Wan)正式宣布开源,此次开源采用Apache2.0协议,14B和1.3B两个参数规格的全部推理代码和权重全部开源,同时支持文生视频和图生视频任务。据阿里云官方介绍,14B版本万相模型在指令遵循、复杂运动生成、物理建模、文字视频生成等方面表现突出,在权威评测集Vbench中,万相
- ZeRO分布式训练策略
AIGC_ZY
大模型分布式
ZeRO分布式训练策略详解一、核心设计原理ZeRO(ZeroRedundancyOptimizer)是微软提出的分布式训练优化框架,与传统数据并行方法不同,ZeRO通过将模型的参数、梯度和优化器状态分散到多个设备上,从而实现内存和计算资源的高效利用。ZeRO通过三级分片策略消除内存冗余,实现超大规模模型训练。其核心演进路线分为三个阶段:1.1ZeRO-1:优化器状态分片分片对象:优化器参数(如Ad
- DeepSeek超强搭档!这8款免费神器让你的效率翻倍
a小胡哦
Deepseekvscodegithub
作为AI领域的效率神器,DeepSeek凭借其强大的智能问答、文件解读和代码生成能力,已成为学习办公的必备工具。但如何让它发挥「1+1>2」的效果?我整理了8款免费软件,搭配DeepSeek让你的效率原地起飞!建议收藏⭐一、办公效率组合拳:告别加班,秒变职场达人WPSOffice推荐理由:免费+全功能办公套件,搭配DeepSeek的文档解析功能,可快速提取合同/报告重点,自动生成摘要。神级用法:用
- 考证好像真的能改变一个人‼️
小猫椰椰
探潜数据分析数据分析职场和发展大数据
考完这些证书,我真的感觉自己变样了。BDA初级数据分析师、BDA中级数据分析师、CPBA商业分析师3个方向,文科生的我,原本没有听过这些证书,但进入职场才知道,多一项技能,多一份优势刚毕业的时候,我考了BDA初级数据分析师,那个时候就尝到了甜头,不仅让简历更漂亮了,自己也掌握了数据分析技能后来的几年,我又陆陆续续考了BDA中级数据分析师和CPBA商业分析师3个方向的证书,看着这些证真的有满满的成就
- 远程办公2.0:如何通过技术实现全球化团队协作?
远程办公2.0时代:从“被迫适应”到“主动进化”的未来工作革命——前沿技术与趋势预测全解析引言:一场不可逆的全球工作革命2020年的一场疫情,让全球职场人第一次大规模体验了远程办公的“生存模式”,而五年后的今天,远程办公已从“权宜之计”进化为“战略选择”。根据《2022年未来办公调研报告》,到2025年,全球53%的企业将永久开放远程办公选项。与此同时,技术的爆发式迭代正推动远程办公迈入2.0时代
- 清华大学:DeepSeek+DeepResearch 让科研像聊天一样简单(86 页 PDF)
伟贤AI之路
AI技术pdf
第一弹:《DeepSeek:从入门到精通(100页PDF)》第二弹:《DeepSeek如何赋能职场应用?从提示语技巧到多场景应用》第三弹:《普通人如何抓住DeepSeek红利?》现在是《DeepSeek+DeepResearch让科研像聊天一样简单》PDF阅读地址:https://tcnsnwj3d31i.feishu.cn/wiki/CkbJw0pm5i5uAEkiijrcGGHrnGhPDF中
- 你好,我是冴羽,我写了一套《前端大佬成长之路》
你好,我是冴羽。这么正式的开头说明我有了一个大动作。是的,我创建了自己的知识星球:“冴羽·前端大佬成长之路”。重点一:新的一年,我会在知识星球更新一套“前端大佬成长之路”的课程。包含目标规划篇、学习方法篇、前端学习篇、个人管理篇、职场发展篇、面试技巧篇、健康养生篇共7大篇章、40节文章。总结了我近十年的工作生活经验,让大家少走一些弯路,节省一些时间。重点二:但是帮助你全面成长,一套课程是不够的,必
- 如果你干了1年多前端,接下来的路该怎么走?
前端后端程序员
我知道在很多中大型公司,其实有好多领导前辈、以及师傅会给那些校招生,以及应届生规划一定的学习成长路线。有些皮于表面,有些醍醐灌顶。其实如果职场上有那么一个领路人,个人的成长是飞速的。我入职了一家新单位,这家单位的没有太多规范,没有太多的组件封装积累,还会考核每周的代码量,我发现有些阶段代码量(测试阶段、需求阶段等)不够的时候大家都是往项目中塞没用的代码,还有些同学会复制公共组件的代码进自己的模块充
- AI取代的不是人类,而是不会使用AI的人
xiaocang668888
人工智能
面对人工智能对职场的深度渗透,职场人需从技能升级、能力重构、思维转型三个维度构建核心竞争力。以下是具体策略:一、技能升级:掌握AI协同工具AI工具链学习掌握主流AI工具(如Claude、Midjourney)的操作逻辑,将重复性工作(数据分析、文档处理)交由AI完成,释放时间用于高阶任务。例如,市场营销人员用AI生成广告初稿后,再注入人性化洞察。技术门槛公式:CAI=任务重复度工具掌握度×业务理解
- 使用linux抛弃Windows,抛弃Windows选Linux?这些原因告诉你为何要这么做
e o
本文由腾讯数码独家发布不想再用Windows系统了?如果你安装了Windows7(微软将于2020年1月14日停止对Windows7的支持),然后之后又不想再用Windows系统,那么你面前有两个选择。要么有闲钱换一台苹果设备,否则除了Linux操作系统之外,没有多少其他的操作系统可供选择。有些人可能会说如果更换操作系统的话还要去花时间适应新的操作系统,很麻烦。的确虽然在更换系统时可能会遇到不适应
- 程序员如何选择操作系统 Mac、Windows还是Linux
开发者每周简报
windowslinuxmac
曾几何时,有一位程序员站在科技的十字路口,面临着职业生涯中最重要的决定:选择哪一个操作系统——Mac、Windows还是Linux。每一个选择都将带来截然不同的后果。程序员知道,选择Windows意味着加入庞大的“Windows集体”,一个由公司控制的用户群体。只要点击“同意”条款,自己便成为了微软计划的一部分。而打开那台崭新的MacBook,表面上看似美好,但实际上是无意识地加入了“苹果教派”,
- 除了特斯拉还有哪些大厂招聘.net
dotNET跨平台
.net
以下是除特斯拉外招聘.NET的部分大厂:-软件/咨询类:微软、Infosys、Tata、AONHewitt等。-项目外包/IT外派类:Accenture、Avanade、华钦科技CLPS等。-ERP类:用友、聚水潭等。-互联网类:智联招聘、58同城等。-游戏类:网易游戏、EA等。-运输物流类:顺丰快递等。-建筑/安防/环境类:霍尼韦尔、博世等。-金融类:东方财富、万得等。-银行类:摩根斯坦利、招商
- 《看板工具与高效学习:案例与方法分享》
从零开始:用看板工具打造高效学习管理系统在当今这个信息爆炸的时代,知识更新换代的速度快得惊人,无论是学生、职场人士还是终身学习者,都面临着如何有效管理学习过程、提升学习效率的难题。而板栗看板这款软件,或许能为我们提供一种全新的解决方案。今天,就让我们一起深入探讨如何利用看板工具构建一个高效的学习管理系统。[]()一、学习管理的痛点与需求在开始使用任何工具之前,我们首先要明确自己在学习管理方面究竟遇
- 微软CEO-纳德拉访谈-AGI计划
数据分析能量站
机器学习人工智能
在与知名科技播客主播DwarkeshPatel的深度访谈中,微软CEO萨提亚・纳德拉围绕AI、量子计算、微软发展等多方面分享深刻见解,下面是针对访谈内容的介绍,其中还是有很多值得我们学习的地方。1AI领域见解影响力评估:纳德拉直言行业所标榜的AGI里程碑是“无意义的基准测试游戏”。他认为AI真正价值在于推动经济增长与生产力提升,当全球经济增速达10%,才是AI发挥巨大影响力的标志。当前经济增长面临
- 分享详细的VS2022安装速成指南
日记成书
反正看不懂系列学习
以下是详细的VisualStudio2022(VS2022)安装速成指南,涵盖从下载到验证安装的全流程:一、下载VS2022安装包获取官方安装程序访问微软官网VisualStudio下载页面,选择“Community2022”(社区版,免费使用),点击下载引导程序(.exe文件)。若需企业版或专业版,需对应许可证。网络优化(可选)若下载速度慢,可修改DNS服务器为微软推荐地址(如4.2.2.1)或
- 都在这,DeepSeek完整版学习手册【清华大学1-5弹】(无套路,免费下载)
2501_90658343
学习AIGC人工智能AI写作AI编程
DeepSeek课程链接:https://pan.quark.cn/s/517afdb4419c前段时间,清华大学发布了一份AI教学课程—《DeepSeek从入门到精通》,课程以浅显易懂的方式讲解了DeepSeek的相关知识,比如提示词的应用技巧、调教AI的秘籍等,课程发布当天就在网络上迅速走红,被誉为“清华第一版”。紧接着,清华大学又推出了第二弹课程—《DeepSeek如何赋能职场应用?》。很快
- 解决npm/yarn等包管理工具在vscode中使用出现系统禁止运行脚本的情况
AlgorithmAce
npm前端node.js
一.问题描述报错提示如下:系统禁止运行脚本。二.问题出现原因该问题大概率会出现在windows新系统上,PowerShell执行策略是一项安全功能,用于控制PowerShell加载配置文件和运行脚本的条件。此功能有助于防止恶意脚本的执行,这算是新系统对于恶意脚本的一种防护措施。三.如何解决实际上报错提示中给的链接详细解释了问题及解决办法,微软官方做了解释,链接直达感兴趣可以看看。这里对解决办法做下
- python中from import 所有内容都执行_彻底搞懂Python 中的 import 与 from import
沃特JS
python中fromimport所有内容都执行
你好,我是谢乾坤,前网易高级数据挖掘工程师。现任微软最有价值专家(Python方向),有6年Python开发经验,善于解决各种业务场景下的棘手问题,进一步提升代码质量。对不少Python初学者来说,Python导入其他模块的方式让他们很难理解。什么时候用importxxx?什么时候用fromxxximportyyy?什么时候用fromxxx.yyyimportzzz?什么时候用fromxxximp
- 如何制作电子名片二维码?
无代码开发平台二维码
随着智能手机的普及,传统纸质名片由于易丢失、难管理、携带不便以及信息更新困难等问题,逐渐被现代化的电子名片所取代。微信电子名片作为一种便捷高效的名片形式,已被越来越多的职场人士广泛使用。尤其是在销售人员、律师、HR和业务员等职业群体中,电子名片不仅提供了更高效的交流方式,还能展现个人和企业的专业形象。本文将详细介绍如何通过草料二维码制作微信电子名片,帮助您快速创建属于自己的电子名片二维码,并最大化
- ChatGPT生成的大模型竞品分析报告
Forbesdytto
chatgpt语言模型
AI大模型产品竞品分析报告1.报告概述本报告旨在分析国内外主要的AI大模型产品,包括其功能、市场定位、技术优势和劣势。通过对比这些竞品,我们可以更好地了解市场格局,制定自身产品的战略。2.主要竞争对手概述国内百度-文心一言(ErnieBot)阿里巴巴-M6腾讯-HunYuan华为-PanGu国外OpenAI-GPT-4Google-Bard(LaMDA)微软-AzureOpenAI(基于OpenA
- 【集宁师范学院毕业论文】小区物业管理系统的设计与实现
毕设指导Martin
数据库智能手机springbootjavaoracle后端科技
注:仅展示部分文档内容和系统截图,需要完整的视频、代码、文章和安装调试环境请私信up主。摘要本文主要展示了小区物业管理系统的设计与开发过程。小区物业管理系统是将所涉及到的小区管理事务利用计算机技术组织起来,实现小区事务方便高效的管理,同时极大地方便了小区住户的日常生活.本系统采用近几年新兴的C#语言作为编程语言和发展日趋成熟的ASP.NET技术作为创建应用程序的方式,并且使用微软公司的SQLSer
- 专访微软CEO:AGI并非真正基准,AI行业也不会“赢家通吃”
AI大模型头条
人工智能那些事儿microsoftagi人工智能游戏aigpt语言模型
【编者按】日前,微软首席执行官SatyaNadella在参加由知名科技播客主持人DwarkeshPatel主持的播客节目DwarkeshPodcast时,谈到了他对当前人工智能(AI)/通用人工智能(AGI)的前景、量子计算的革命性进展,以及科技如何推动全球经济变革的看法。当各家公司都在争先恐后地追逐AGI时,Nadella在访谈中却语出惊人,“我们自己宣称达成某个AGI的里程碑,对我来说,那只是
- Python 爬虫实战案例 - 获取BOSS直聘网招聘职位信息
西攻城狮北
python爬虫BOSS直聘招聘信息
引言在当今竞争激烈的职场环境中,无论是求职者渴望找到理想工作,还是企业力求招揽优秀人才,精准、及时的招聘信息都至关重要。BOSS直聘作为国内知名的在线招聘平台,汇聚了海量的职位资源,涵盖各行各业、各个层级。对于求职者,这里宛如一座蕴藏无限机会的宝库,能助其快速锚定契合自身发展的岗位;对于企业,它则是发现千里马的优质猎场,可精准匹配所需人才。而Python爬虫技术恰似一把神奇钥匙,能开启这座宝库的大
- AccountsRt.dll出现0xc0000020未被指定在Windows运行
用户7756535831965
windows
AccountsRt.dll为MicrosoftWindows的一个动态链接库。由于很多常用软件都是采用MicrosoftVisualStudio编写的,所以这类软件的运行需要依赖微软VisualC++运行库,比如像QQ、迅雷、Adobe软件等等,如果没有安装VC++运行库或者安装的版本不完整,就可能会导致这些软件启动时报错,提示缺少库文件。下面从解决实际问题的角度上,推荐几种有效方法!方法1:下
- 【WPF应用35】深度解析WPF中的TreeView控件:功能、用法、特性与最佳实践
白话Learning
WPFwpf
WPF(WindowsPresentationFoundation)是微软推出的一个用于构建桌面应用程序的图形子系统。在WPF中,TreeView是一种常用的树形控件,用于显示层次结构的数据显示。本文将详细介绍WPF中的TreeView控件,并提供一个简单的示例。一、TreeView控件的基本概念TreeView控件用于显示一个层次结构的列表,通常用于显示文件系统、组织结构或其他任何可以表示为树形
- 26届校招流程全解析:应届生的求职“逆袭秘籍”
校招,你真的了解吗[]()对于26届毕业生来说,校招堪称毕业前的头等大事,是迈向职场的关键一步。它不仅是众多企业集中选拔人才的重要途径,对于咱们毕业生而言,更是一次不可多得的就业契机。错过校招,后续再想进入心仪的企业,难度可能会大大增加。校招一般分为提前批、秋招和春招。提前批通常在每年的6-7月开启,这个阶段的招聘周期短、流程快,最重要的是竞争相对较小,对于有实力、准备充分的同学来说,是一个提前锁
- Deepseek 高效使用指南,1 分钟学会
茂茂在长安
AI大模型人工智能机器学习语言模型知识图谱
2025Deepseek爆火全球,会用的人说巨好用,差距就在提问方式,教你用1个公式让Deepseek变身“职场军师”“学霸外挂”“流量引擎”。凝炼出一套方法论,按万能公式「4步提问法」【明确身份+具体任务+细节约束+输出格式】公式拆解身份:你是谁?(学生/打工人/新手妈妈…)任务:要解决什么问题?(写报告/做计划/分析数据…)细节:限制条件是什么?(时间/场景/禁忌…)格式:要什么形式结果?(表
- java责任链模式
3213213333332132
java责任链模式村民告县长
责任链模式,通常就是一个请求从最低级开始往上层层的请求,当在某一层满足条件时,请求将被处理,当请求到最高层仍未满足时,则请求不会被处理。
就是一个请求在这个链条的责任范围内,会被相应的处理,如果超出链条的责任范围外,请求不会被相应的处理。
下面代码模拟这样的效果:
创建一个政府抽象类,方便所有的具体政府部门继承它。
package 责任链模式;
/**
*
- linux、mysql、nginx、tomcat 性能参数优化
ronin47
一、linux 系统内核参数
/etc/sysctl.conf文件常用参数 net.core.netdev_max_backlog = 32768 #允许送到队列的数据包的最大数目
net.core.rmem_max = 8388608 #SOCKET读缓存区大小
net.core.wmem_max = 8388608 #SOCKET写缓存区大
- php命令行界面
dcj3sjt126com
PHPcli
常用选项
php -v
php -i PHP安装的有关信息
php -h 访问帮助文件
php -m 列出编译到当前PHP安装的所有模块
执行一段代码
php -r 'echo "hello, world!";'
php -r 'echo "Hello, World!\n";'
php -r '$ts = filemtime("
- Filter&Session
171815164
session
Filter
HttpServletRequest requ = (HttpServletRequest) req;
HttpSession session = requ.getSession();
if (session.getAttribute("admin") == null) {
PrintWriter out = res.ge
- 连接池与Spring,Hibernate结合
g21121
Hibernate
前几篇关于Java连接池的介绍都是基于Java应用的,而我们常用的场景是与Spring和ORM框架结合,下面就利用实例学习一下这方面的配置。
1.下载相关内容: &nb
- [简单]mybatis判断数字类型
53873039oycg
mybatis
昨天同事反馈mybatis保存不了int类型的属性,一直报错,错误信息如下:
Caused by: java.lang.NumberFormatException: For input string: "null"
at sun.mis
- 项目启动时或者启动后ava.lang.OutOfMemoryError: PermGen space
程序员是怎么炼成的
eclipsejvmtomcatcatalina.sheclipse.ini
在启动比较大的项目时,因为存在大量的jsp页面,所以在编译的时候会生成很多的.class文件,.class文件是都会被加载到jvm的方法区中,如果要加载的class文件很多,就会出现方法区溢出异常 java.lang.OutOfMemoryError: PermGen space.
解决办法是点击eclipse里的tomcat,在
- 我的crm小结
aijuans
crm
各种原因吧,crm今天才完了。主要是接触了几个新技术:
Struts2、poi、ibatis这几个都是以前的项目中用过的。
Jsf、tapestry是这次新接触的,都是界面层的框架,用起来也不难。思路和struts不太一样,传说比较简单方便。不过个人感觉还是struts用着顺手啊,当然springmvc也很顺手,不知道是因为习惯还是什么。jsf和tapestry应用的时候需要知道他们的标签、主
- spring里配置使用hibernate的二级缓存几步
antonyup_2006
javaspringHibernatexmlcache
.在spring的配置文件中 applicationContent.xml,hibernate部分加入
xml 代码
<prop key="hibernate.cache.provider_class">org.hibernate.cache.EhCacheProvider</prop>
<prop key="hi
- JAVA基础面试题
百合不是茶
抽象实现接口String类接口继承抽象类继承实体类自定义异常
/* * 栈(stack):主要保存基本类型(或者叫内置类型)(char、byte、short、 *int、long、 float、double、boolean)和对象的引用,数据可以共享,速度仅次于 * 寄存器(register),快于堆。堆(heap):用于存储对象。 */ &
- 让sqlmap文件 "继承" 起来
bijian1013
javaibatissqlmap
多个项目中使用ibatis , 和数据库表对应的 sqlmap文件(增删改查等基本语句),dao, pojo 都是由工具自动生成的, 现在将这些自动生成的文件放在一个单独的工程中,其它项目工程中通过jar包来引用 ,并通过"继承"为基础的sqlmap文件,dao,pojo 添加新的方法来满足项
- 精通Oracle10编程SQL(13)开发触发器
bijian1013
oracle数据库plsql
/*
*开发触发器
*/
--得到日期是周几
select to_char(sysdate+4,'DY','nls_date_language=AMERICAN') from dual;
select to_char(sysdate,'DY','nls_date_language=AMERICAN') from dual;
--建立BEFORE语句触发器
CREATE O
- 【EhCache三】EhCache查询
bit1129
ehcache
本文介绍EhCache查询缓存中数据,EhCache提供了类似Hibernate的查询API,可以按照给定的条件进行查询。
要对EhCache进行查询,需要在ehcache.xml中设定要查询的属性
数据准备
@Before
public void setUp() {
//加载EhCache配置文件
Inpu
- CXF框架入门实例
白糖_
springWeb框架webserviceservlet
CXF是apache旗下的开源框架,由Celtix + XFire这两门经典的框架合成,是一套非常流行的web service框架。
它提供了JAX-WS的全面支持,并且可以根据实际项目的需要,采用代码优先(Code First)或者 WSDL 优先(WSDL First)来轻松地实现 Web Services 的发布和使用,同时它能与spring进行完美结合。
在apache cxf官网提供
- angular.equals
boyitech
AngularJSAngularJS APIAnguarJS 中文APIangular.equals
angular.equals
描述:
比较两个值或者两个对象是不是 相等。还支持值的类型,正则表达式和数组的比较。 两个值或对象被认为是 相等的前提条件是以下的情况至少能满足一项:
两个值或者对象能通过=== (恒等) 的比较
两个值或者对象是同样类型,并且他们的属性都能通过angular
- java-腾讯暑期实习生-输入一个数组A[1,2,...n],求输入B,使得数组B中的第i个数字B[i]=A[0]*A[1]*...*A[i-1]*A[i+1]
bylijinnan
java
这道题的具体思路请参看 何海涛的微博:http://weibo.com/zhedahht
import java.math.BigInteger;
import java.util.Arrays;
public class CreateBFromATencent {
/**
* 题目:输入一个数组A[1,2,...n],求输入B,使得数组B中的第i个数字B[i]=A
- FastDFS 的安装和配置 修订版
Chen.H
linuxfastDFS分布式文件系统
FastDFS Home:http://code.google.com/p/fastdfs/
1. 安装
http://code.google.com/p/fastdfs/wiki/Setup http://hi.baidu.com/leolance/blog/item/3c273327978ae55f93580703.html
安装libevent (对libevent的版本要求为1.4.
- [强人工智能]拓扑扫描与自适应构造器
comsci
人工智能
当我们面对一个有限拓扑网络的时候,在对已知的拓扑结构进行分析之后,发现在连通点之后,还存在若干个子网络,且这些网络的结构是未知的,数据库中并未存在这些网络的拓扑结构数据....这个时候,我们该怎么办呢?
那么,现在我们必须设计新的模块和代码包来处理上面的问题
- oracle merge into的用法
daizj
oraclesqlmerget into
Oracle中merge into的使用
http://blog.csdn.net/yuzhic/article/details/1896878
http://blog.csdn.net/macle2010/article/details/5980965
该命令使用一条语句从一个或者多个数据源中完成对表的更新和插入数据. ORACLE 9i 中,使用此命令必须同时指定UPDATE 和INSE
- 不适合使用Hadoop的场景
datamachine
hadoop
转自:http://dev.yesky.com/296/35381296.shtml。
Hadoop通常被认定是能够帮助你解决所有问题的唯一方案。 当人们提到“大数据”或是“数据分析”等相关问题的时候,会听到脱口而出的回答:Hadoop! 实际上Hadoop被设计和建造出来,是用来解决一系列特定问题的。对某些问题来说,Hadoop至多算是一个不好的选择,对另一些问题来说,选择Ha
- YII findAll的用法
dcj3sjt126com
yii
看文档比较糊涂,其实挺简单的:
$predictions=Prediction::model()->findAll("uid=:uid",array(":uid"=>10));
第一个参数是选择条件:”uid=10″。其中:uid是一个占位符,在后面的array(“:uid”=>10)对齐进行了赋值;
更完善的查询需要
- vim 常用 NERDTree 快捷键
dcj3sjt126com
vim
下面给大家整理了一些vim NERDTree的常用快捷键了,这里几乎包括了所有的快捷键了,希望文章对各位会带来帮助。
切换工作台和目录
ctrl + w + h 光标 focus 左侧树形目录ctrl + w + l 光标 focus 右侧文件显示窗口ctrl + w + w 光标自动在左右侧窗口切换ctrl + w + r 移动当前窗口的布局位置
o 在已有窗口中打开文件、目录或书签,并跳
- Java把目录下的文件打印出来
蕃薯耀
列出目录下的文件文件夹下面的文件目录下的文件
Java把目录下的文件打印出来
>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>
蕃薯耀 2015年7月11日 11:02:
- linux远程桌面----VNCServer与rdesktop
hanqunfeng
Desktop
windows远程桌面到linux,需要在linux上安装vncserver,并开启vnc服务,同时需要在windows下使用vnc-viewer访问Linux。vncserver同时支持linux远程桌面到linux。
linux远程桌面到windows,需要在linux上安装rdesktop,同时开启windows的远程桌面访问。
下面分别介绍,以windo
- guava中的join和split功能
jackyrong
java
guava库中,包含了很好的join和split的功能,例子如下:
1) 将LIST转换为使用字符串连接的字符串
List<String> names = Lists.newArrayList("John", "Jane", "Adam", "Tom");
- Web开发技术十年发展历程
lampcy
androidWeb浏览器html5
回顾web开发技术这十年发展历程:
Ajax
03年的时候我上六年级,那时候网吧刚在小县城的角落萌生。传奇,大话西游第一代网游一时风靡。我抱着试一试的心态给了网吧老板两块钱想申请个号玩玩,然后接下来的一个小时我一直在,注,册,账,号。
彼时网吧用的512k的带宽,注册的时候,填了一堆信息,提交,页面跳转,嘣,”您填写的信息有误,请重填”。然后跳转回注册页面,以此循环。我现在时常想,如果当时a
- 架构师之mima-----------------mina的非NIO控制IOBuffer(说得比较好)
nannan408
buffer
1.前言。
如题。
2.代码。
IoService
IoService是一个接口,有两种实现:IoAcceptor和IoConnector;其中IoAcceptor是针对Server端的实现,IoConnector是针对Client端的实现;IoService的职责包括:
1、监听器管理
2、IoHandler
3、IoSession
- ORA-00054:resource busy and acquire with NOWAIT specified
Everyday都不同
oraclesessionLock
[Oracle]
今天对一个数据量很大的表进行操作时,出现如题所示的异常。此时表明数据库的事务处于“忙”的状态,而且被lock了,所以必须先关闭占用的session。
step1,查看被lock的session:
select t2.username, t2.sid, t2.serial#, t2.logon_time
from v$locked_obj
- javascript学习笔记
tntxia
JavaScript
javascript里面有6种基本类型的值:number、string、boolean、object、function和undefined。number:就是数字值,包括整数、小数、NaN、正负无穷。string:字符串类型、单双引号引起来的内容。boolean:true、false object:表示所有的javascript对象,不用多说function:我们熟悉的方法,也就是
- Java enum的用法详解
xieke90
enum枚举
Java中枚举实现的分析:
示例:
public static enum SEVERITY{
INFO,WARN,ERROR
}
enum很像特殊的class,实际上enum声明定义的类型就是一个类。 而这些类都是类库中Enum类的子类 (java.l