小序:
经过前面两个实验的介绍,我们已经基本了解了IPSec×××的有两种安全联盟的方式:一种是Manual(手工方式);另一种IKE(自动协商)。相比于Manual方式,IKE自动协商方式更加的方便。今天就利用IKE方式来实现总、两个分公司之间的IPSec ×××。
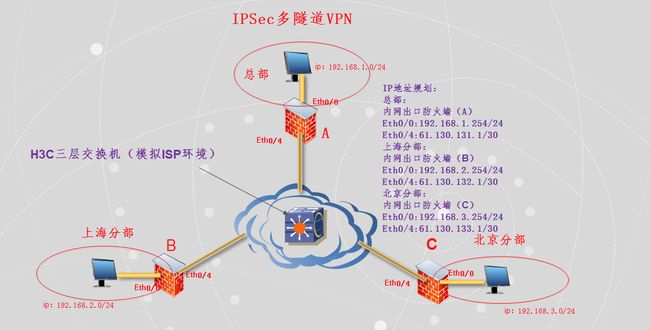
实验拓扑:
配置步骤:
Step1:定义被保护的数据流(acl)
Step2:定义安全提议
①IPSec工作方式选择:transport(传输方式)/tunnel(隧道方式)【默认】
②选择安全协议类型:AH(认证头)/ESP(封装安全载荷)
③在选择的协议类型下选择相应的加密算法和认证算法。
AH----> authentication-algorithm MD5/SHA1
ESP---->authentication-algorithm MD5/SHA1
----->encryption-algorithm DES/3DES/AES
Step3:定义安全策略(安全策略组) ------>实现acl和安全提议的绑定
Step4: 接口应用安全策略 ----->在接口上应用策略
配置参考:
ISP的配置
sysname ISP
vlan 10
port e0/1
ip add 61.130.131.2 255.255.255.252
vlan 20
port e0/2
ip add 61.130.132.2 255.255.255.252
vlan 30
port e0/3
ip add 61.130.133.2 255.255.255.252
A防火墙配置
sysname A
inter e0/0
ip add 192.168.1.254 24
inter e0/4
ip add 61.130.131.1 30
ip route-static 0.0.0.0 0 61.130.131.2
add inter e0/0
firewall zone trust
add inter e0/0
quit
firewall zone untrust
add inter e0/4
①流控制
acl number 3000 match-order auto
rule 10 permit ip source 192.168.1.0 0.0.0.255 destination 192.168.2.0 0.0.0.255
acl number 3001 match-order auto
rule 10 permit ip source 192.168.1.0 0.0.0.255 destination 192.168.3.0 0.0.0.255
rule 20 deny ip any destination any
②安全提议
ipsec proposal A
encapsulation-mode tunnel
transform esp
esp authentication-algorithm md5
esp encryption-algorithm des
③A-B(10),A-C(20)策略
ipsec policy a 10 isakmp
security acl 3000
proposal A
ipsec policy a 20 isakmp
security acl 3001
proposal A
quit
ike peer B
local-address 61.130.131.1
remote-address 61.130.132.1
pre-shared-key simple ab
ipsec policy a 10 isakmp
ike peer-peer B
ike peer C
local-address 61.130.131.1
remote-address 61.130.133.1
pre-shared-key simple ac
ipsec policy a 20 isakmp
ike peer-peer C
④接口应用策略
inter e0/4
ipsec policy a
B防火墙配置
sysname B
inter e0/0
ip add 192.168.2.254 24
inter e0/4
ip add 61.130.132.1 30
ip route-static 0.0.0.0 0 61.130.132.2
add inter e0/0
firewall zone trust
add inter e0/0
quit
firewall zone untrust
add inter e0/4
①流控制
acl number 3000 match-order auto
rule 10 permit ip source 192.168.2.0 0.0.0.255 destination 192.168.1.0 0.0.0.255
rule 20 deny ip any destination any
②安全提议
ipsec proposal B
encapsulation-mode tunnel
transform esp
esp authentication-algorithm md5
esp encryption-algorithm des
③策略
ipsec policy b 10 isakmp
security acl 3000
proposal B
quit
ike peer A
local-address 61.130.132.1
remote-address 61.130.131.1
pre-shared-key simple ab
ipsec policy b 10 isakmp
ike peer-peer A
④接口应用策略
inter e0/4
ipsec policy b
C防火墙配置
sysname C
inter e0/0
ip add 192.168.3.254 24
inter e0/4
ip add 61.130.133.1 30
ip route-static 0.0.0.0 0 61.130.133.2
add inter e0/0
firewall zone trust
add inter e0/0
quit
firewall zone untrust
add inter e0/4
①流控制
acl number 3000 match-order auto
rule 10 permit ip source 192.168.3.0 0.0.0.255 destination 192.168.1.0 0.0.0.255
rule 20 deny ip any destination any
②安全提议
ipsec proposal C
encapsulation-mode tunnel
transform esp
esp authentication-algorithm md5
esp encryption-algorithm des
③策略
ipsec policy c 10 isakmp
security acl 3000
proposal C
quit
ike peer A
local-address 61.130.133.1
remote-address 61.130.131.1
pre-shared-key simple ac
ipsec policy c 10 isakmp
ike peer-peer A
④接口应用策略
inter e0/4
ipsec policy c