如今×××应用已经非常广泛了,之前就写过一篇关于PPTPD的博文。链接是http://cyr520.blog.51cto.com/714067/1161788。
家里最近新换了一个宽带。居然没办法用拨上公司的Pptpd×××,一直拨号状态一直停留在正在验证用户名和密码这一步。百度谷歌了一大圈,也没解决这个问题。貌似是因为宽带运营商屏蔽GRE协议的原因。作为运维人员,不能及时的连上公司的内部网络是一件很让人不爽的事情。
干脆再搞一套Open×××吧,据说Open×××非常强大,可以适应很复杂的网络环境,并且配置也非常灵活。
服务端系统环境:
1、Centos6.4 x86_64
2、单网卡
网络架构:
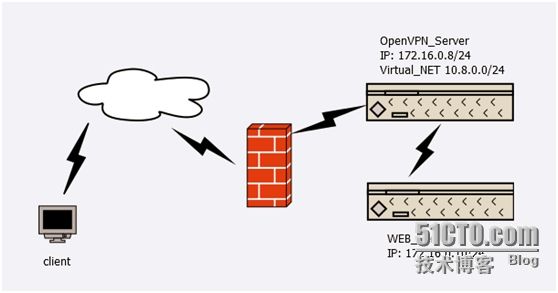
环境说明:Open×××采用公司内网的一台单网卡服务器部署,通过路由器做端口映射到外网,客户端连上×××服务器需要实现能连上公司内部的其他服务器。
安装方法分两种,编译安装和使用YUM安装,因为本文讲的是快速构建,所以使用YUM来安装。
服务端操作步骤:
添加EPEL仓库:
yum install http://mirrors.zju.edu.cn/epel/6/i386/epel-release-6-8.noarch.rpm
检查TUN模块:
modinfo tun
安装Open×××:
yum install open*** openssl -y
下载密钥制作工具easy_rsa 2:
wget https://github.com/Open×××/easy-rsa/archive/release/2.x.zip
解压easy_rsa并拷贝到/etc/open***:
unzip 2.x.zip
mv easy-rsa-release-2.x/ /etc/open***/
编辑easy-rsa的vars文件,设定相关变量信息:
cd /etc/open***/easy-rsa-release-2.x/easy-rsa/2.0
vim vars
export KEY_COUNTRY="CN"
export KEY_PROVINCE="BEIJING"
export KEY_CITY="BEIJING"
export KEY_ORG="XIAOCUI"
export KEY_EMAIL="[email protected]"
export KEY_OU="MyOpen×××"
编辑完之后,保存退出。
将刚才编辑的vars文件,执行如下命令:
source vars
./clean-all
./build-ca
创建服务器的证书和密钥:
./build-key-server Open×××_Server
[root@cloud 2.0]# ./build-key-server Open×××_Server
Generating a 2048 bit RSA private key
.................................+++
............+++
writing new private key to 'Open×××_Server.key'
-----
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
-----
Country Name (2 letter code) [CN]:
State or Province Name (full name) [BEIJING]:
Locality Name (eg, city) [BEIJING]:
Organization Name (eg, company) [XIAOCUI]:
Organizational Unit Name (eg, section) [MyOpen×××]:
Common Name (eg, your name or your server's hostname) [Open×××_Server]:
Name [EasyRSA]:
Email Address [ADMIN@ XIAOCUI.COM]:
Please enter the following 'extra' attributes
to be sent with your certificate request
A challenge password []:
An optional company name []:
Using configuration from /etc/open***/easy-rsa-release-2.x/easy-rsa/2.0/openssl-1.0.0.cnf
Check that the request matches the signature
Signature ok
The Subject's Distinguished Name is as follows
countryName :PRINTABLE:'CN'
stateOrProvinceName :PRINTABLE:'BEIJING'
localityName :PRINTABLE:'BEIJING'
organizationName :PRINTABLE:' XIAOCUI '
organizationalUnitName:PRINTABLE:'MyOpen×××'
commonName :T61STRING:'Open×××_Server'
name :PRINTABLE:'EasyRSA'
emailAddress :IA5STRING:'ADMIN@ XIAOCUI.COM'
Certificate is to be certified until May 2 07:49:13 2025 GMT (3650 days)
Sign the certificate? [y/n]:y
1 out of 1 certificate requests certified, commit? [y/n]y
Write out database with 1 new entries
Data Base Updated
创建客户端的证书和密钥:
./build-key client-user-test1
[root@cloud 2.0]# ./build-key client-user-test1
Generating a 2048 bit RSA private key
....................+++
...............................................................................+++
writing new private key to 'client-user-cuiyuanrong.key'
-----
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
-----
Country Name (2 letter code) [CN]:
State or Province Name (full name) [BEIJING]:
Locality Name (eg, city) [BEIJING]:
Organization Name (eg, company) [XIAOCUI]:
Organizational Unit Name (eg, section) [MyOpen×××]:
Common Name (eg, your name or your server's hostname) [client-user-test1]:
Name [EasyRSA]:
Email Address [[email protected]]:
Please enter the following 'extra' attributes
to be sent with your certificate request
A challenge password []:
An optional company name []:
Using configuration from /etc/open***/easy-rsa-release-2.x/easy-rsa/2.0/openssl-1.0.0.cnf
Check that the request matches the signature
Signature ok
The Subject's Distinguished Name is as follows
countryName :PRINTABLE:'CN'
stateOrProvinceName :PRINTABLE:'BEIJING'
localityName :PRINTABLE:'BEIJING'
organizationName :PRINTABLE:'XIAOCUI'
organizationalUnitName:PRINTABLE:'MyOpen×××'
commonName :PRINTABLE:'client-user-test1'
name :PRINTABLE:'EasyRSA'
emailAddress :IA5STRING:'[email protected]'
Certificate is to be certified until May 2 07:53:17 2025 GMT (3650 days)
Sign the certificate? [y/n]:y
1 out of 1 certificate requests certified, commit? [y/n]y
Write out database with 1 new entries
Data Base Updated
创建Diffie Hellman 参数:
./build-dh
创建Open×××服务端配置文件:
cd /etc/open***/
vim server.conf
local 0.0.0.0
port 1194
proto tcp
dev tun
ca /etc/open***/easy-rsa-release-2.x/easy-rsa/2.0/keys/ca.crt
cert /etc/open***/easy-rsa-release-2.x/easy-rsa/2.0/keys/Open×××_Server.crt
key /etc/open***/easy-rsa-release-2.x/easy-rsa/2.0/keys/Open×××_Server.key
dh /etc/open***/easy-rsa-release-2.x/easy-rsa/2.0/keys/dh2048.pem
server 10.8.0.0 255.255.255.0
ifconfig-pool-persist /var/log/ipp.txt
push "route 10.0.0.0 255.255.255.0"
client-to-client
keepalive 10 120
comp-lzo
persist-key
persist-tun
status open***-status.log
log /var/log/open***.log
log-append /var/log/open***.log
verb 3
script-security 3 system
auth-user-pass-verify /etc/open***/checkpsw.sh via-env
client-cert-not-required
username-as-common-name
创建checkpsw.sh脚本:
cd /etc/open***
vim checkpsw.sh
#!/bin/sh
###########################################################
# checkpsw.sh (C) 2004 Mathias Sundman
#
# This script will authenticate Open××× users against
# a plain text file. The passfile should simply contain
# one row per user with the username first followed by
# one or more space(s) or tab(s) and then the password.
PASSFILE="/etc/open***/psw-file"
LOG_FILE="/var/log/open***/open***-password.log"
TIME_STAMP=`date "+%Y-%m-%d %T"`
###########################################################
if [ ! -r "${PASSFILE}" ]; then
echo "${TIME_STAMP}: Could not open password file \"${PASSFILE}\" for reading." >> ${LOG_FILE}
exit 1
fi
CORRECT_PASSWORD=`awk '!/^;/&&!/^#/&&$1=="'${username}'"{print $2;exit}' ${PASSFILE}`
if [ "${CORRECT_PASSWORD}" = "" ]; then
echo "${TIME_STAMP}: User does not exist: username=\"${username}\", password=\"${password}\"." >> ${LOG_FILE}
exit 1
fi
if [ "${password}" = "${CORRECT_PASSWORD}" ]; then
echo "${TIME_STAMP}: Successful authentication: username=\"${username}\"." >> ${LOG_FILE}
exit 0
fi
echo "${TIME_STAMP}: Incorrect password: username=\"${username}\", password=\"${password}\"." >> ${LOG_FILE}
exit 1
chmod +x checkpsw.sh
创建psw-file文件:
cd /etc/open***
echo "test1 test1" > psw-file
chmod 400 psw-file
加入开机启动项:
chkconfig open*** on
启动open***服务端:
/etc/init.d/open*** start
打包客户端需要的证书和密钥:
cd /etc/open***/easy-rsa-release-2.x/easy-rsa/2.0/keys/
tar zcvf client_key.tar.gz ca.crt client-user-test1.*
防火墙策略
cat /etc/sysconfig/iptables
# Generated by iptables-save v1.4.7 on Tue May 5 11:25:43 2015
*nat
:PREROUTING ACCEPT [74:10890]
:POSTROUTING ACCEPT [1:156]
:OUTPUT ACCEPT [1:156]
-A POSTROUTING -s 10.8.0.0/24 -o eth0 -j MASQUERADE
COMMIT
# Completed on Tue May 5 11:25:43 2015
# Generated by iptables-save v1.4.7 on Tue May 5 11:25:43 2015
*filter
:INPUT ACCEPT [0:0]
:FORWARD ACCEPT [0:0]
:OUTPUT ACCEPT [24:3392]
-A INPUT -i lo -j ACCEPT
-A INPUT -p icmp -m icmp --icmp-type any -j ACCEPT
-A INPUT -m state --state RELATED,ESTABLISHED -j ACCEPT
-A INPUT -s 10.8.0.0/24 -j ACCEPT
-A INPUT -p tcp -m state --state NEW -m tcp --dport 22 -j ACCEPT
-A INPUT -p tcp -m state --state NEW -m tcp --dport 1194 -j ACCEPT
-A INPUT -p udp -m state --state NEW -m udp --dport 1194 -j ACCEPT
-A INPUT -i tun+ -j ACCEPT
-A FORWARD -d 10.8.0.0/24 -j ACCEPT
-A FORWARD -i tun+ -j ACCEPT
-A INPUT -j DROP
COMMIT
# Completed on Tue May 5 11:25:43 2015
客户端已windows为例:
客户端操作步骤:
下载windows客户端:
http://open***.ustc.edu.cn/open***-install-2.3.6-I603-x86_64.exe
安装好客户端软件之后,把之前从服务端打包的客户端需要的证书解压到客户端安装目录下的config目录中。
并且创建客户端配置文件:
client.o***
client
dev tun
proto tcp
remote 115.183.9.106 1194
nobind
user nobody
group nobody
persist-key
persist-tun
ca ca.crt
;cert client-user-test1.crt
;key client-user-test1.key
comp-lzo
verb 3
auth-user-pass
reneg-sec 360000
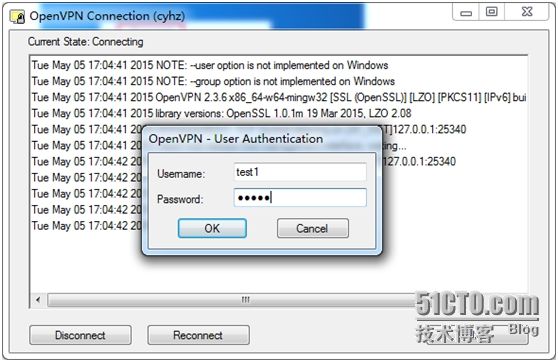
测试连接:
到此基于用户名密码的验证方式就部署好了,需要单独证书验证或证书和密码组合验证的,请参考网上其它教程,实际上只需要在客户端和服务端的两个配置文件稍微做下调整即可。
======================================================================================
下面是一些网友客户端链接时遇到的问题:
There are no TAP-Win32 adapters on this system. You should be able to create a TAP-Win32 adapter by going to Start -> All Programs -> Open××× -> Add a new TAP-Win32 virtual ethernet adapter.
这个问题是客户端没有安装TAP-Windows Adapter V9虚拟网卡。
Wed May 20 17:40:44 2015 TLS: Initial packet from [AF_INET]10.176.190.148:1194, sid=45a0da91 b5384f05
Wed May 20 17:40:44 2015 VERIFY ERROR: depth=1, error=self signed certificate in certificate chain: C=CN, ST=BEIJING, L=BEIJING, O=XIAOCUI, OU=MyOpen×××, CN=XIAOCUI CA, name=EasyRSA, [email protected]
Wed May 20 17:40:44 2015 TLS_ERROR: BIO read tls_read_plaintext error: error:14090086:SSL routines:SSL3_GET_SERVER_CERTIFICATE:certificate verify failed
Wed May 20 17:40:44 2015 TLS Error: TLS object -> incoming plaintext read error
Wed May 20 17:40:44 2015 TLS Error: TLS handshake failed
Wed May 20 17:40:44 2015 Fatal TLS error (check_tls_errors_co), restarting
Wed May 20 17:40:44 2015 SIGUSR1[soft,tls-error] received, process restarting
Wed May 20 17:40:44 2015 MANAGEMENT: >STATE:1432114844,RECONNECTING,tls-error,,
Wed May 20 17:40:44 2015 Restart pause, 5 second(s)
这个大概有两个问题存在:
证书生成的有问题
服务端和客户端时间不一致
Thu Feb 10 11:13:07 2015 us=3362 61.4.***.**:45771 TLS: Initial packet from 61.4.***.**:45771, sid=eec450eb 8673ceef
Thu Feb 10 11:13:10 2015 us=798063 61.4.***.**:45771 open***_execve: external program may not be called unless '--script-secur ity 2' or higher is enabled. Use '--script-security 3 system' for backward compatibility with 2.1_rc8 and earlier. See --help t ext or man page for detailed info.
Thu Feb 10 11:13:10 2015 us=798127 61.4.***.**:45771 TLS Auth Error: user-pass-verify script failed to execute: /usr/bin/php - q /home/xiaohui/open***-manager/admin/open***-auth.php
Thu Feb 10 11:13:10 2015 us=798141 61.4.***.**:45771 TLS Auth Error: Auth Username/Password verification failed for peer
这个问题多半是试用用户名密码验证的时候回出现的问题,需要在服务端配置文件加如下参数:
script-security 3 system