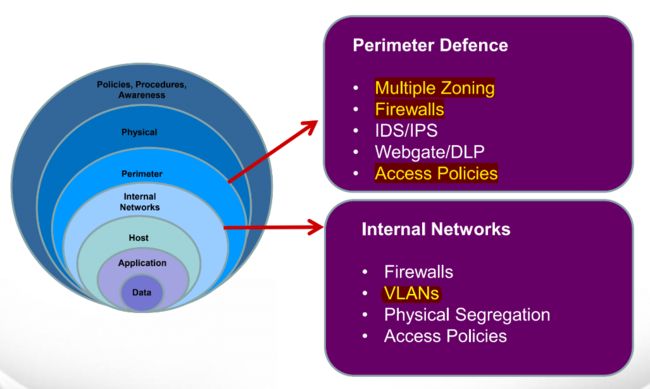
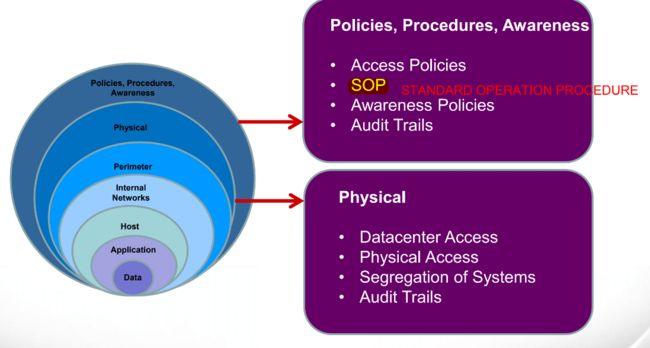
- 爬虫小知识(二)网页进行交互
AI 嗯啦
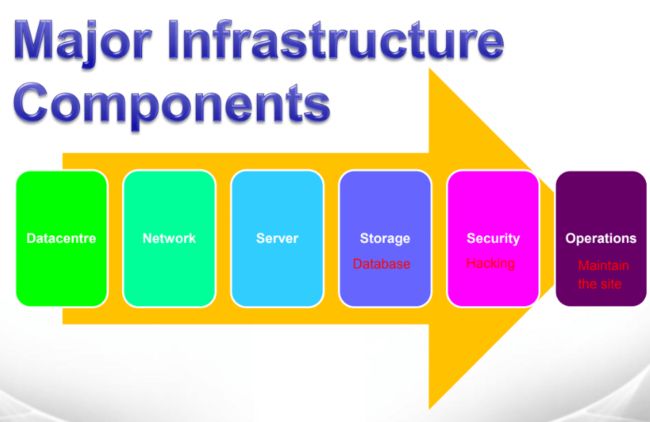
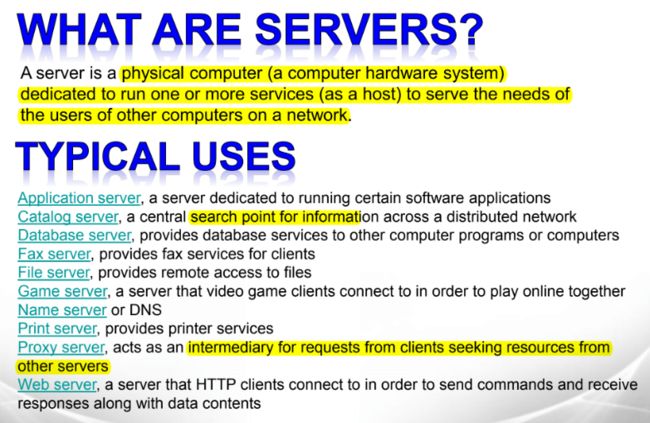
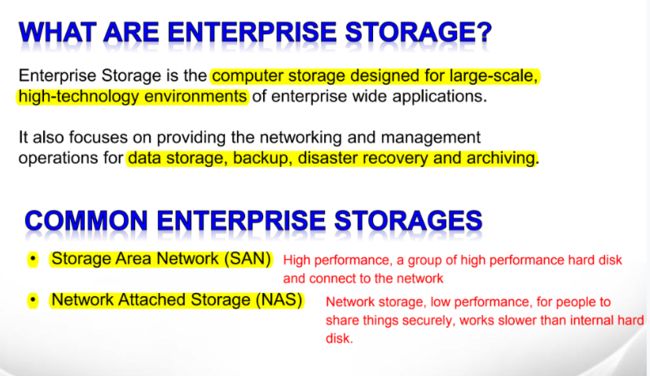
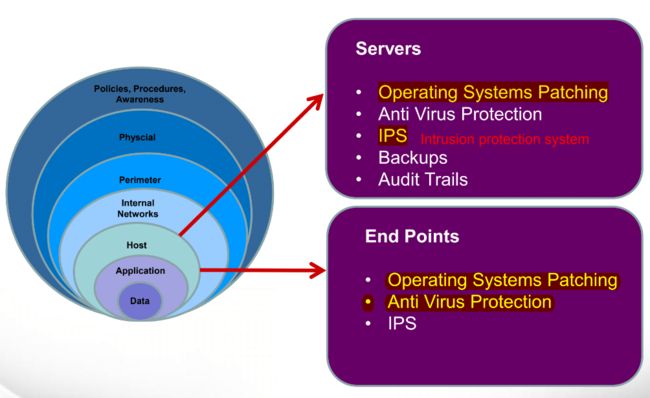
服务器运维python爬虫交互开发语言
一、提交信息到网页1、模块核心逻辑“提交信息到网页”是网络交互关键环节,借助requests库的post()函数,能模拟浏览器向网页发数据(如表单、文件),实现信息上传,让我们能与网页背后的服务器“沟通”,像改密码、传文件等操作,都可通过它完成。2、浏览器提交请求流程(以改密码为例)操作触发:登录账户进改密码页面,填“当前密码”“新密码”等表单。抓包分析:网页空白处右键→检查→Network窗口,
- Docker-Compose配置文件docker-compose.yml详解
高压锅_1220
dockerdockerdocker-compose容器配置文件容器
一份标准的docker-compose.yml文件应该包含version、services、networks三大部分,其中最关键的就是services和networks两个部分。Compose和Docker兼容性:Compose文件格式有3个版本,分别为1,2.x和3.x目前主流的为3.x其支持docker1.13.0及其以上的版本#目前主流的为3.x其支持docker1.13.0及其以上的版本,
- PVE固定网卡名称防止增减PCIE设备失联
牧子与羊
运维服务器虚拟机pve
【关键词】:新PCIE网卡改变、新PCIE管理页面无法登录、新PCIE网口灯不亮在ProxmoxVE(PVE)环境中,新增PCIe设备可能导致网卡PCIID变化,进而引发网卡名称改变(如enp5s0→enp6s0),最终导致PVE管理界面无法访问。本文提供两种一劳永逸的解决方案:MAC地址绑定法(推荐):仅需在/etc/network/interfaces中添加hwaddress行,无需重命名网卡
- NQA_路由自动切换实验(H3C)
李李网工日记
NQA可靠性路由切换
引言NQA全称是NetworkQualityAnalysis(网络质量分析),它是一种用于监测和评估网络性能的技术,通过发送探测报文(如ICMPEcho、TCP连接等)来检测网络的连通性、延迟、丢包率等指标,帮助实现网络优化和故障排查。在现代数据中心网络中,路由的高可用性和可靠性至关重要。网络质量分析(NQA)技术通过实时监测网络性能(如延时、丢包率),结合路由跟踪(Track)功能,可实现路由的
- 交换机配置VLAN及Access接口
蒋慧慧
网络交换机VLAN
交换机VLAN配置VLAN原理VLAN配置实验内容实验拓扑实验步骤VLAN原理VLAN(VirtualLocalAreaNetwork,虚拟局域网),VLAN是一种比较新的技术,工作在OSI参考模型的第2层和第3层,一个VLAN就是一个广播域,VLAN之间的通信是通过第3层的路由器来完成的。与传统的局域网技术相比较,VLAN技术更加灵活,它具有以下优点:网络设备的移动、添加和修改的管理开销减少;可
- 【Oracle】删除 Oracle 19c 的监听器和数据库实例同时保留数据库软件
瑞琪姐
大数据模块数据库oracle
要删除Oracle19c的监听器和数据库实例,同时保留数据库软件,请按以下步骤操作:1.停止监听器lsnrctlstop2.删除监听器配置手动删除配置文件:cd$ORACLE_HOME/network/adminrmlistener.orasqlnet.oratnsnames.ora#删除网络配置文件或使用netca工具:netca选择“Listenerconfiguration”→“Delete
- 高效能人士的学习法,期待对你有所帮助
廖斋笔谈
学习美国物理学费曼(RichardDFeynman)在大学教授物理学时,他总是能够深入浅出地将复杂的专业理论讲得通俗易懂,无论多么抽象、晦涩的概念,都能用非常生活化的例子表达出来,非常风趣幽默。后来,越来越多的人便采用他的这种方法学习,最终形成了人们众所周知的「费曼学习法」。具体步骤「费曼学习法」可以用四个关键词来概括:概念(Concept)、以教代学(Teach)、评价(Review)、简化(S
- 零信任产品联合宁盾泛终端网络准入,打造随需而变、精准贴合业务的网络安全访问体系
宁盾Nington
安全
零信任网络访问控制(ZeroTrustNetworkAccess,ZTNA,文中零信任皆指ZTNA)基于“永不信任,持续验证”的理念,打破了企业基于传统网络边界进行防护的固有模式。在当前日趋复杂的网络环境下,内部威胁与外部攻击加剧,零信任能够为企业构建一个动态的安全访问体系。通过持续身份验证、权限动态调整等机制,确保合法用户在安全的环境下访问企业资源,有效防止未授权访问与数据泄露,提升企业整体信息
- Jenkins pipeline 部署docker通用模板
longze_7
jenkinsdockerJenkinsfilejenkinspipeline
Jenkinsfile:Docker的NETWORK_NAME不要使用bridge默认网络,要使用自定义的网络如test默认bridge网络:容器间不能用名字互相访问,只能用IP。自定义网络:容器间可以用名字互相访问,Docker自动做了DNS解析。pipeline{agentanyenvironment{//定义镜像名称和标签作为环境变量IMAGE_NAME='my-application'IM
- Synergizing RAG and Reasoning: A Systematic Review-RAG与推理能力深度结合-新方向
数据分析能量站
机器学习人工智能
欢迎关v:数据分析能量站0论文小结一、研究背景与核心问题大语言模型(LLM)在处理复杂任务时面临两大瓶颈:知识局限性:纯LLM存在“知识幻觉”(编造事实)和“领域知识缺口”;推理浅度:传统检索增强生成(RAG)仅通过关键词匹配获取信息,无法处理多跳推理、语义歧义等复杂需求。核心主张:RAG与推理的深度整合(RAG+Reasoning)是突破上述瓶颈的关键,通过“检索提供实时知识,推理赋予逻辑能力”
- Tcpdump使用
一介绍tcpdump,是Linux/Unix系统下强大的网络抓包工具,能够捕获和分析网络流量。用简单的语言概括就是dumpthetrafficonanetwork,是一个运行在linux平台可以根据使用者需求对网络上传输的数据包进行捕获的抓包工具,windows平台有sniffer等工具,tcpdump可以将网络中传输的数据包的“包头”全部捕获过来进程分析,其支持网络层、特定的传输协议、数据发送和
- HPE携手迈阿密自由公园,为迈阿密国际足球俱乐部打造极致球迷体验
近日,慧与科技(NYSE:HPE)宣布与迈阿密自由公园(MiamiFreedomPark)及迈阿密国际足球俱乐部(InterMiamiCF,后简称迈阿密国际)正式达成合作协议。HPE将成为迈阿密自由公园的首个创始合作伙伴和官方技术合作伙伴,及迈阿密国际在网络基础设施、解决方案、混合云等领域的独家合作伙伴。届时,HPE将凭借HPEArubaNetworking、HPEAlletraStorage、H
- 如何解决 NPM proxy, 当我们在终端nodejs应用程序时出现代理相关报错
Thisisaproblemrelatedtonetworkconnectivity.npmERR!networkInmostcasesyouarebehindaproxyorhavebadnetworksettings.在使用npminstall下载包的时候总是报以下错误:在控制台或VisualStudioCode终端中运行以下命令:npmconfigrmproxynpmconfigrmhttp
- Docker指定网桥和指定网桥IP
$dockernetworklsNETWORKIDNAMEDRIVER7fca4eb8c647bridgebridge9f904ee27bf5nonenullcf03ee007fb4hosthostBridge默认bridge网络,我们可以使用dockernetworkinspect命令查看返回的网络信息,我们使用dockerrun命令是将网络自动应用到新的容器Host如果是hosts模式,启动容
- 实时预览功能问题
GISer_Jinger
项目javascript开发语言ecmascript
你遇到的问题是:“B端修改配置后无法实时出现在previewiframe中,而必须点击刷新才能生效”。主要原因与以下几方面有关:❗为什么需要手动刷新:iFrame与主页面之间缺少实时通信机制:原本仅靠刷新重新加载iframe,而没有通过postMessage等方式同步状态;Valtio的proxy状态不能跨文件热刷新持久保存:当你修改包含proxy定义的文件,热重载会导致object被替换,监听丢
- 树莓派 5 - Raspberry Pi OS 新版本 Bookworm(书虫)
kuan_li_lyg
树莓派&Jetson教程机器人stm32嵌入式硬件自动驾驶ROS树莓派raspberrypi
文章目录在这里插入图片描述版本说明前言二、PipeWire三、Networking四、Firefox五、Documentation六、What’smissing? 新版本下载地址为:https://www.raspberrypi.com/software/operating-systems/版本说明 2023-10-10:基于Debianbookworm版本支持树莓派5在RaspberryPi4和
- 苦练Python第5天:字符串从入门到格式化
python后端人工智能前端
苦练Python第5天:字符串从入门到格式化原文链接:https://dev.to/therahul_gupta/day-5100-working-with-strings-basics-to-formatting-2kkn作者:RahulGupta译者:倔强青铜三前言大家好,我是倔强青铜三。是一名热情的软件工程师,我热衷于分享和传播IT技术,致力于通过我的知识和技能推动技术交流与创新,欢迎关注我
- 基于TCP/UDP的应用层协议
huangxy10
面试专题——网络知识
1,基于TCP的有:Telnet(TeletypeovertheNetwork,网络电传),通过一个终端(terminal)登陆到网络
- CNN 猫狗识别:从理论到实战的深度解析
爱熬夜的小古
cnn深度学习人工智能
在计算机视觉领域,卷积神经网络(ConvolutionalNeuralNetwork,CNN)凭借其强大的特征提取和模式识别能力,成为图像分类任务的主流技术。猫狗识别作为经典的图像分类问题,不仅能帮助我们理解CNN的工作原理,还能为实际应用提供技术支持。本文将深入探讨CNN在猫狗识别中的应用,从理论基础到实战代码,带你全面掌握这项技术。一、CNN基础理论概述(一)CNN的核心组件卷积层:是CNN的
- SPGAN: Siamese projection Generative Adversarial Networks
这张生成的图像能检测吗
优质GAN模型训练自己的数据集人工智能生成对抗网络计算机视觉深度学习神经网络算法
简介简介:该论文针对传统GANs中鉴别器采用硬边际分类导致的误分类问题,提出了基于Siameseprojection网络的SPGAN方法。主要创新点包括:(1)设计Siameseprojection网络来测量特征相似性;(2)提出相似特征对抗学习框架,将相似性测量融入生成器和鉴别器的损失函数;(3)通过相似特征对抗学习,鉴别器能最大化真实图像和生成图像特征的差异性,生成器能合成包含更多真实图像特征
- 强化学习之 DQN、Double DQN、PPO
JNU freshman
强化学习强化学习
文章目录通俗理解DQNDoubleDQNPPO结合公式理解通俗理解DQN一个简单的比喻和分步解释来理解DQN(DeepQ-Network,深度Q网络),就像教小朋友学打游戏一样:先理解基础概念:Q学习(Q-Learning)想象你在教一只小狗玩电子游戏(比如打砖块)。小狗每做一个动作(比如“向左移动”或“发射球”),游戏会给出一个奖励(比如得分增加)或惩罚(比如球掉了)。小狗的目标是通过不断尝试,
- go语言因为前端跨域导致无法访问到后端解决方案
雪花凌落的盛夏
Golang学习目录golang前端开发语言
前端服务8080访问后端8081这端口显示跨域了ERRORNetworkErrorAxiosError:NetworkErroratXMLHttpRequest.handleError(webpack-internal:///./node_modules/axios/lib/adapters/xhr.js:116:14)atAxios.request(webpack-internal:///./n
- LGTM? 那些迷之缩写
路先生的杂货铺
杂七杂八笔记
就像你可能不知道现充其实是现实生活很充实的人生赢家的缩写一样,我们经常看到Github上的码农们在codereview时,把乱七八糟的缩写写得到处都是——娴熟的司机们都会使用缩写来达到提高逼格的效果——我们第一次看到时还是会出现一脸懵逼的状况,这里整理一下这些缩写都是什么含义,以后我们也可以欢快地装逼了。PR:PullRequest.拉取请求,给其他项目提交代码LGTM:LooksGoodToMe
- 【论文阅读】【IEEE TCYB 2023】Edge-Guided Recurrent Positioning Network forSalient Object Detection in Opt
引言任务:光学遥感图像中显著目标检测论文地址:Edge-GuidedRecurrentPositioningNetworkforSalientObjectDetectioninOpticalRemoteSensingImages|IEEEJournals&Magazine|IEEEXplore代码地址:前置知识一、摘要目前由于光学rsi中目标类型多样、目标尺度多样、目标方向众多以及背景杂乱,现有S
- 微信直播回访视频下载方法
tianyatest
网页视频提取M3U8
今天在网上看2024制冷展大会直播回放,对于两个讲的比较好的视频,想下载下,发现居然不能直接下载,后来从调试模式抓到网址,进行了下载。操作流程:(1)将视频网页用Edge打开,F12进入调试模式;(2)找到网络,或者Network,然后在筛选器内填入M3U8;(3)这步最简单,也很关键,就是刷新网页;(4)就会看到一条记录,然后找到那个记录里面的地址。(5)此时,有两个选择:方法1:采用迅雷下载该
- LINUX710 MYSQL
czhc1140075663
Mysqlmysqladb数据库
[email protected]'spassword:┌────────────────────────────────────────────────────────────────────┐│•MobaXterm20.0•││(SSHclient,X-serverandnetworkingtools)││││➤
[email protected]││•SSH
- 5g信号频率是多少赫兹_我家WiFi也有“5G”,这是5G信号吗?
大家都知道5G吧?5G是最近很火热的名词,大家都知道它和手机有关系,有些小伙伴在用手机和电脑连WiFi的时候,也能看到一些WiFi名字后面跟着一个“5G”。这个“5G”是平时说的那个5G吗?答案是“否”。5G是“5thgenerationmobilenetworks”的缩写,是最新一代蜂窝移动通信技术,5G中的这G是英文generation的缩写。简单来说就是5G网速更快、时延更小。无线通信技术是
- Ubuntu network is unreachable解决方法
wangchaoqi1985
\N
Ubuntunetworkisunreachable解决方法参考文章:(1)Ubuntunetworkisunreachable解决方法(2)https://www.cnblogs.com/Qi-gege/p/10634956.html备忘一下。
- android 无线调试_Android 11的无线调试
weixin_26739079
androiddebugpython安卓
android无线调试Android11developerpreviewhaslotsofnewfeaturestolookbutoneofthecoolestisWirelessdebugging.ItisanewmethodfordeveloperstopairtheirAndroiddeviceswithacomputerwirelessly.Beforewedivemoreintothis
- 命令绑定非默认事件
lph1972
c#
导入NuGet包必须Install-PackageMicrosoft.Xaml.Behaviors.Wpfxmlns:i="http://schemas.microsoft.com/xaml/自己的命名空间一般clr-namespace:系统的一般就是类似网址这里必须用隧道事件preview用冒泡没反应就记住mvvm绑定非默认事件只能用隧道
- java工厂模式
3213213333332132
java抽象工厂
工厂模式有
1、工厂方法
2、抽象工厂方法。
下面我的实现是抽象工厂方法,
给所有具体的产品类定一个通用的接口。
package 工厂模式;
/**
* 航天飞行接口
*
* @Description
* @author FuJianyong
* 2015-7-14下午02:42:05
*/
public interface SpaceF
- nginx频率限制+python测试
ronin47
nginx 频率 python
部分内容参考:http://www.abc3210.com/2013/web_04/82.shtml
首先说一下遇到这个问题是因为网站被攻击,阿里云报警,想到要限制一下访问频率,而不是限制ip(限制ip的方案稍后给出)。nginx连接资源被吃空返回状态码是502,添加本方案限制后返回599,与正常状态码区别开。步骤如下:
- java线程和线程池的使用
dyy_gusi
ThreadPoolthreadRunnabletimer
java线程和线程池
一、创建多线程的方式
java多线程很常见,如何使用多线程,如何创建线程,java中有两种方式,第一种是让自己的类实现Runnable接口,第二种是让自己的类继承Thread类。其实Thread类自己也是实现了Runnable接口。具体使用实例如下:
1、通过实现Runnable接口方式 1 2
- Linux
171815164
linux
ubuntu kernel
http://kernel.ubuntu.com/~kernel-ppa/mainline/v4.1.2-unstable/
安卓sdk代理
mirrors.neusoft.edu.cn 80
输入法和jdk
sudo apt-get install fcitx
su
- Tomcat JDBC Connection Pool
g21121
Connection
Tomcat7 抛弃了以往的DBCP 采用了新的Tomcat Jdbc Pool 作为数据库连接组件,事实上DBCP已经被Hibernate 所抛弃,因为他存在很多问题,诸如:更新缓慢,bug较多,编译问题,代码复杂等等。
Tomcat Jdbc P
- 敲代码的一点想法
永夜-极光
java随笔感想
入门学习java编程已经半年了,一路敲代码下来,现在也才1w+行代码量,也就菜鸟水准吧,但是在整个学习过程中,我一直在想,为什么很多培训老师,网上的文章都是要我们背一些代码?比如学习Arraylist的时候,教师就让我们先参考源代码写一遍,然
- jvm指令集
程序员是怎么炼成的
jvm 指令集
转自:http://blog.csdn.net/hudashi/article/details/7062675#comments
将值推送至栈顶时 const ldc push load指令
const系列
该系列命令主要负责把简单的数值类型送到栈顶。(从常量池或者局部变量push到栈顶时均使用)
0x02 &nbs
- Oracle字符集的查看查询和Oracle字符集的设置修改
aijuans
oracle
本文主要讨论以下几个部分:如何查看查询oracle字符集、 修改设置字符集以及常见的oracle utf8字符集和oracle exp 字符集问题。
一、什么是Oracle字符集
Oracle字符集是一个字节数据的解释的符号集合,有大小之分,有相互的包容关系。ORACLE 支持国家语言的体系结构允许你使用本地化语言来存储,处理,检索数据。它使数据库工具,错误消息,排序次序,日期,时间,货
- png在Ie6下透明度处理方法
antonyup_2006
css浏览器FirebugIE
由于之前到深圳现场支撑上线,当时为了解决个控件下载,我机器上的IE8老报个错,不得以把ie8卸载掉,换个Ie6,问题解决了,今天出差回来,用ie6登入另一个正在开发的系统,遇到了Png图片的问题,当然升级到ie8(ie8自带的开发人员工具调试前端页面JS之类的还是比较方便的,和FireBug一样,呵呵),这个问题就解决了,但稍微做了下这个问题的处理。
我们知道PNG是图像文件存储格式,查询资
- 表查询常用命令高级查询方法(二)
百合不是茶
oracle分页查询分组查询联合查询
----------------------------------------------------分组查询 group by having --平均工资和最高工资 select avg(sal)平均工资,max(sal) from emp ; --每个部门的平均工资和最高工资
- uploadify3.1版本参数使用详解
bijian1013
JavaScriptuploadify3.1
使用:
绑定的界面元素<input id='gallery'type='file'/>$("#gallery").uploadify({设置参数,参数如下});
设置的属性:
id: jQuery(this).attr('id'),//绑定的input的ID
langFile: 'http://ww
- 精通Oracle10编程SQL(17)使用ORACLE系统包
bijian1013
oracle数据库plsql
/*
*使用ORACLE系统包
*/
--1.DBMS_OUTPUT
--ENABLE:用于激活过程PUT,PUT_LINE,NEW_LINE,GET_LINE和GET_LINES的调用
--语法:DBMS_OUTPUT.enable(buffer_size in integer default 20000);
--DISABLE:用于禁止对过程PUT,PUT_LINE,NEW
- 【JVM一】JVM垃圾回收日志
bit1129
垃圾回收
将JVM垃圾回收的日志记录下来,对于分析垃圾回收的运行状态,进而调整内存分配(年轻代,老年代,永久代的内存分配)等是很有意义的。JVM与垃圾回收日志相关的参数包括:
-XX:+PrintGC
-XX:+PrintGCDetails
-XX:+PrintGCTimeStamps
-XX:+PrintGCDateStamps
-Xloggc
-XX:+PrintGC
通
- Toast使用
白糖_
toast
Android中的Toast是一种简易的消息提示框,toast提示框不能被用户点击,toast会根据用户设置的显示时间后自动消失。
创建Toast
两个方法创建Toast
makeText(Context context, int resId, int duration)
参数:context是toast显示在
- angular.identity
boyitech
AngularJSAngularJS API
angular.identiy 描述: 返回它第一参数的函数. 此函数多用于函数是编程. 使用方法: angular.identity(value); 参数详解: Param Type Details value
*
to be returned. 返回值: 传入的value 实例代码:
<!DOCTYPE HTML>
- java-两整数相除,求循环节
bylijinnan
java
import java.util.ArrayList;
import java.util.List;
public class CircleDigitsInDivision {
/**
* 题目:求循环节,若整除则返回NULL,否则返回char*指向循环节。先写思路。函数原型:char*get_circle_digits(unsigned k,unsigned j)
- Java 日期 周 年
Chen.H
javaC++cC#
/**
* java日期操作(月末、周末等的日期操作)
*
* @author
*
*/
public class DateUtil {
/** */
/**
* 取得某天相加(减)後的那一天
*
* @param date
* @param num
*
- [高考与专业]欢迎广大高中毕业生加入自动控制与计算机应用专业
comsci
计算机
不知道现在的高校还设置这个宽口径专业没有,自动控制与计算机应用专业,我就是这个专业毕业的,这个专业的课程非常多,既要学习自动控制方面的课程,也要学习计算机专业的课程,对数学也要求比较高.....如果有这个专业,欢迎大家报考...毕业出来之后,就业的途径非常广.....
以后
- 分层查询(Hierarchical Queries)
daizj
oracle递归查询层次查询
Hierarchical Queries
If a table contains hierarchical data, then you can select rows in a hierarchical order using the hierarchical query clause:
hierarchical_query_clause::=
start with condi
- 数据迁移
daysinsun
数据迁移
最近公司在重构一个医疗系统,原来的系统是两个.Net系统,现需要重构到java中。数据库分别为SQL Server和Mysql,现需要将数据库统一为Hana数据库,发现了几个问题,但最后通过努力都解决了。
1、原本通过Hana的数据迁移工具把数据是可以迁移过去的,在MySQl里面的字段为TEXT类型的到Hana里面就存储不了了,最后不得不更改为clob。
2、在数据插入的时候有些字段特别长
- C语言学习二进制的表示示例
dcj3sjt126com
cbasic
进制的表示示例
# include <stdio.h>
int main(void)
{
int i = 0x32C;
printf("i = %d\n", i);
/*
printf的用法
%d表示以十进制输出
%x或%X表示以十六进制的输出
%o表示以八进制输出
*/
return 0;
}
- NsTimer 和 UITableViewCell 之间的控制
dcj3sjt126com
ios
情况是这样的:
一个UITableView, 每个Cell的内容是我自定义的 viewA viewA上面有很多的动画, 我需要添加NSTimer来做动画, 由于TableView的复用机制, 我添加的动画会不断开启, 没有停止, 动画会执行越来越多.
解决办法:
在配置cell的时候开始动画, 然后在cell结束显示的时候停止动画
查找cell结束显示的代理
- MySql中case when then 的使用
fanxiaolong
casewhenthenend
select "主键", "项目编号", "项目名称","项目创建时间", "项目状态","部门名称","创建人"
union
(select
pp.id as "主键",
pp.project_number as &
- Ehcache(01)——简介、基本操作
234390216
cacheehcache简介CacheManagercrud
Ehcache简介
目录
1 CacheManager
1.1 构造方法构建
1.2 静态方法构建
2 Cache
2.1&
- 最容易懂的javascript闭包学习入门
jackyrong
JavaScript
http://www.ruanyifeng.com/blog/2009/08/learning_javascript_closures.html
闭包(closure)是Javascript语言的一个难点,也是它的特色,很多高级应用都要依靠闭包实现。
下面就是我的学习笔记,对于Javascript初学者应该是很有用的。
一、变量的作用域
要理解闭包,首先必须理解Javascript特殊
- 提升网站转化率的四步优化方案
php教程分享
数据结构PHP数据挖掘Google活动
网站开发完成后,我们在进行网站优化最关键的问题就是如何提高整体的转化率,这也是营销策略里最最重要的方面之一,并且也是网站综合运营实例的结果。文中分享了四大优化策略:调查、研究、优化、评估,这四大策略可以很好地帮助用户设计出高效的优化方案。
PHP开发的网站优化一个网站最关键和棘手的是,如何提高整体的转化率,这是任何营销策略里最重要的方面之一,而提升网站转化率是网站综合运营实力的结果。今天,我就分
- web开发里什么是HTML5的WebSocket?
naruto1990
Webhtml5浏览器socket
当前火起来的HTML5语言里面,很多学者们都还没有完全了解这语言的效果情况,我最喜欢的Web开发技术就是正迅速变得流行的 WebSocket API。WebSocket 提供了一个受欢迎的技术,以替代我们过去几年一直在用的Ajax技术。这个新的API提供了一个方法,从客户端使用简单的语法有效地推动消息到服务器。让我们看一看6个HTML5教程介绍里 的 WebSocket API:它可用于客户端、服
- Socket初步编程——简单实现群聊
Everyday都不同
socket网络编程初步认识
初次接触到socket网络编程,也参考了网络上众前辈的文章。尝试自己也写了一下,记录下过程吧:
服务端:(接收客户端消息并把它们打印出来)
public class SocketServer {
private List<Socket> socketList = new ArrayList<Socket>();
public s
- 面试:Hashtable与HashMap的区别(结合线程)
toknowme
昨天去了某钱公司面试,面试过程中被问道
Hashtable与HashMap的区别?当时就是回答了一点,Hashtable是线程安全的,HashMap是线程不安全的,说白了,就是Hashtable是的同步的,HashMap不是同步的,需要额外的处理一下。
今天就动手写了一个例子,直接看代码吧
package com.learn.lesson001;
import java
- MVC设计模式的总结
xp9802
设计模式mvc框架IOC
随着Web应用的商业逻辑包含逐渐复杂的公式分析计算、决策支持等,使客户机越
来越不堪重负,因此将系统的商业分离出来。单独形成一部分,这样三层结构产生了。
其中‘层’是逻辑上的划分。
三层体系结构是将整个系统划分为如图2.1所示的结构[3]
(1)表现层(Presentation layer):包含表示代码、用户交互GUI、数据验证。
该层用于向客户端用户提供GUI交互,它允许用户