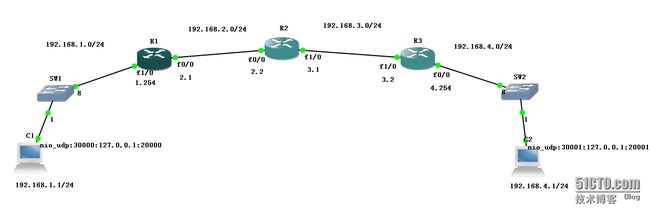
前言:IPSec ×××配置基本步骤:
第一步 配置IKE协商
R1(config)#crypto isakmp policy1建立IKE协商策略
R1(config-isakmap)#hashmd5 设置密钥验证所用的算法
R1(config-isakmap)#authentication pre-share设置路由要使用的预先共享的密钥
R1(config)#crypto isakmp key 0 123 address 192.168.1.2设置共享密钥和对端地址123是密钥
第二步 配置IPSEC相关参数
R1(config)#crypto ipsec transform-set transformset_name esp-des配置传输模式以及验证的算法和加密的的算法cfanhome这里是给这个传输模式取个名字
R1(config)#access-list 101 permit ip 192.168.1.0 0.0.0.255 192.168.3.0 0.0.0.255配置ACL列表,允许加密隧道的IP,注意是反掩码
这里是定义访问控制列表
R2(config)#crypto ipsec transform-set transformset_nme ah-md5-hmacesp-des两边的传输模式的名字要一样
R2(config)#access-list101 permit ip 192.168.1.0 0.0.0.255 192.168.3.0 0.0.0.255
第三步 应用配置到端口假设2个端口都是F0/0
R1(config)#crypto map ×××-Map 1 ipsec-isakmp采用IKE协商,优先级为1这里的cfanhomemap是一个表的名字
R1(config-crypto-map)#set peer 192.168.1.2指定×××链路对端的IP地址
R1(config-crypto-map)#set transform-set transformset_name调用先前所定义的传输模式
R1(config-crypto-map)#match address 101调用ACL列表这里的MATCH是匹配感兴趣流
R1(config)#int s0/0
R1(config-if)#crypto map ×××-Map应用此表到端口
R2和R1的配置及路由器型号需要完全一样
配置
R1:
R1#config t
R1(config)#interf f1/0
R1(config-if)#ip add 192.168.1.254 255.255.255.0
R1(config-if)#no sh
R1(config-if)#interf f0/0
R1(config-if)#ip add 192.168.2.1 255.255.255.0
R1(config-if)#exit
R1(config)#crypto isakmp policy 1
R1(config-isakmp)#authentication pre-share
R1(config-isakmp)#encryption 3des
R1(config-isakmp)#hash md5
R1(config-isakmp)#exi
R1(config)#crypto isakmp key 0 123 address 192.168.3.2
R1(config)#crypto ipsec transform-set transform1 ah-md5-hmac esp-3des
R1(cfg-crypto-trans)#exit
R1(config)#$ 101 permit ip 192.168.1.0 0.0.0.255 192.168.4.0 0.0.0.255
R1(config)#crypto map ×××-Map 1 ipsec-isakmp
% NOTE: This new crypto map will remain disabled until a peer
and a valid access list have been configured.
R1(config-crypto-map)#set peer 192.168.3.2
R1(config-crypto-map)#set transform-set transform1
R1(config-crypto-map)#match address 101
R1(config)#ip route 0.0.0.0 0.0.0.0 192.168.2.2
R1(config)#interf f0/0
R1(config-if)#crypto map ×××-Map
R1(config-if)#
*Mar 1 00:22:32.199: %CRYPTO-6-ISAKMP_ON_OFF: ISAKMP is ON
R2:
R2#config t
Enter configuration commands, one per line. End with CNTL/Z.
R2(config)#interf f0/0
R2(config-if)#ip add 192.168.2.2 255.255.255.0
R2(config-if)#no sh
R2(config-if)#interf f1/0
R2(config-if)#ip add 192.168.3.1 255.255.255.0
R2(config-if)#no sh
R2(config-if)#end
R2#ping
*Mar 1 00:09:28.431: %SYS-5-CONFIG_I: Configured from console by console
R2#ping 192.168.2.1
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 192.168.2.1, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 16/32/48 ms
R2#ping 192.168.3.2
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 192.168.3.2, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 32/43/60 ms
R2#
R3:
R3#config t
Enter configuration commands, one per line. End with CNTL/Z.
R3(config)#interf f1/0
R3(config-if)#ip add 192.168.3.2 255.255.255.0
R3(config-if)#no sh
R3(config-if)#interf f0/0
R3(config-if)#ip add 192.168.4.254 255.255.255.0
R3(config-if)#no sh
R3(config-if)#end
R3#config t
Enter configuration commands, one per line. End with CNTL/Z.
R3(config)#crypto isakmp policy 1
R3(config-isakmp)#authentication pre-share
R3(config-isakmp)#encryption 3des
R3(config-isakmp)#hash md5
R3(config-isakmp)#exit
R3(config)#crypto isakmp key 0 123 address 192.168.2.1
R3(config)#crypto ipsec transform-set transform1 ah-md5-hmac esp-3des
R3(cfg-crypto-trans)#exi
R3(config)#$ 101 permit ip 192.168.4.0 0.0.0.255 192.168.1.0 0.0.0.255
R3(config)#crypto map ×××-Map 1 ipsec-isakmp
% NOTE: This new crypto map will remain disabled until a peer
and a valid access list have been configured.
R3(config-crypto-map)#set peer 192.168.2.1
R3(config-crypto-map)#set transform-set transform1
R3(config-crypto-map)#match address 101
R3(config-crypto-map)#end
R3#ping 192.168.2.1
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 192.168.2.1, timeout is 2 seconds:
.....
Success rate is 0 percent (0/5)
R3#config t
Enter configuration commands, one per line. End with CNTL/Z.
R3(config)#ip route 0.0.0.0 0.0.0.0 192.168.3.1
R3(config)#end
R3#ping 192.168.2.1
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 192.168.2.1, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 64/91/108 ms
R3#ping 192.168.1.254
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 192.168.1.254, timeout is 2 seconds:
UUUUU
Success rate is 0 percent (0/5)
R3#config t
Enter configuration commands, one per line. End with CNTL/Z.
R3(config)#interf f1/0
R3(config-if)#crypto map ×××-Map
R3(config-if)#
*Mar 1 00:22:46.599: %CRYPTO-6-ISAKMP_ON_OFF: ISAKMP is ON
验证:
1、C1访问C2
没问题访问成功!!!
补充
当初在未配置IPSec的时候我为了确定不是走的默认路由,我进行了这样的检查:
1、配置完ip结果是这样的
R1#ping 192.168.1.254
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 192.168.1.254, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 1/2/4 ms
R1#ping 192.168.2.2
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 192.168.2.2, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 1/2/4 ms
R1#ping 192.168.3.1
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 192.168.3.1, timeout is 2 seconds:
.....
Success rate is 0 percent (0/5)
显然,网络是不通的,后来配置了默认路由R1(config)#ip route 0.0.0.0 0.0.0.0 192.168.2.2
配置完默认路由,再看
R1(config)#end
R1#ping 192.168.3.2
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 192.168.3.2, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 80/87/96 ms
R1#ping 192.168.4.254
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 192.168.4.254, timeout is 2 seconds:
UUUUU
Success rate is 0 percent (0/5)
注意:其他网段通了,为了证明流量确实走的是×××,我们即便配置了默认路由也是无法访问4.0网段的,返回的结果是“UUUUU”如果我们在端口启用×××,可以ping通的话说明肯定走的×××隧道(这也就是为什么大家在做×××实验的时候最好用3台以上路由器模拟出来更真实)
这里我们看下上面的返回的”UUUUU”是什么意思:
! 成功
. 等待
U 目的不可达
C 数据包拥塞
I 被中断
? 数据包类型未知
& 超过数据包生存时间
如果你还不相信我们这样,先在R1路由器端口删除加密图
R1(config-if)#no cry
R1(config-if)#no crypto ma
R1(config-if)#no crypto map ×××-Map
R1(config-if)#
*Mar 1 00:23:21.755: %CRYPTO-6-ISAKMP_ON_OFF: ISAKMP is OFF
结果是这样的
VPCS[1]> ping 192.168.4.1
192.168.4.1 icmp_seq=1 timeout
192.168.4.1 icmp_seq=2 timeout
192.168.4.1 icmp_seq=3 timeout
192.168.4.1 icmp_seq=4 timeout
192.168.4.1 icmp_seq=5 timeout
然后启用:
R1(config-if)#crypto map ×××-Map
R1(config-if)#
*Mar 1 00:23:39.667: %CRYPTO-6-ISAKMP_ON_OFF: ISAKMP is ON
R1(config-if)#
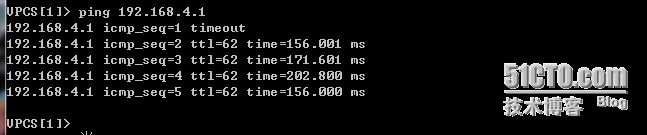
这样可以证明确实是×××起作用了。
VPCS[1]> ping 192.168.4.1
192.168.4.1 icmp_seq=1 timeout
192.168.4.1 icmp_seq=2 ttl=62 time=156.001 ms
192.168.4.1 icmp_seq=3 ttl=62 time=171.601 ms
192.168.4.1 icmp_seq=4 ttl=62 time=202.800 ms
192.168.4.1 icmp_seq=5 ttl=62 time=156.000 ms
排错
相关验证结果的查看命令
显示ISAKMP协商策略的结果
· R2#sh crypto isakmp policy
查看管理连接SA的状态
· R2#sh crypto isakmp sa
显示IPSEC变换集
· R2#sh crypto ipsec transform-set
显示数据数据连接SA的细节信息
· R2#sh crypto ipsec sa
显示Crypto Map的信息
· R2#sh crypto map