ssh协议实现相关工具(telnet-server, dropbear(嵌入式), openssh-server)
openssh-clients相关的工具(scp, ssh, dbclient, sftp)
<Windows: xshell, scurecrt, putty,sshsecureshellclient>
openssh-server配置文件的安全配置
免密码登陆openssh-server
配置文件
/etc/ssh/ssh_config
/etc/ssh/sshd_config
SSH(Secure Socket Handler)协议的实现: telnet, dropbear,openssh
sshd使用
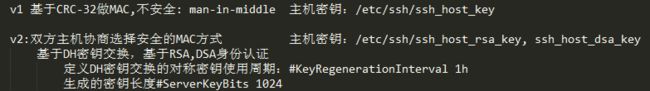
生成主机密钥 # ssh-keygen -t rsa1 -f /etc/ssh/ssh_host_key -N '' # ssh-keygen -t rsa -f /etc/ssh/ssh_host_rsa_key -N '' # ssh-keygen -t dsa -f /etc/ssh/ssh_host_dsa_key -N '' # ssh-keygen -t ecdsa -f /etc/ssh/ssh_host_ecdsa_key -N '' 启动服务 # sshd
telnet使用<明文协议>
1、相关程序 telnet.i686 客户端 telnet-server.i686 服务端 The telnet server serves telnet sessions; it uses unencrypted username/password pairs for authentication. 2、安装服务端 # yum -y -q install telnet-server 3、启动telnet服务 # chkconfig telnet on # service xinetd start 4、查看是否监听 # ss -tunlp | fgrep 23 5、创建普通用户 # openssl passwd -1 -salt $(openssl rand -hex 4) nuni $1$5c636cc0$ADetN0NrDemfAUxtvvSFR1 # useradd -p '$1$5c636cc0$ADetN0NrDemfAUxtvvSFR1' centos 6、在Windows主机上访问(xshell中) [c:\~]$ telnet NAME telnet - connects to a host using the TELNET protocol. SYNOPSYS telnet [user@]host [port] [centos@localhost ~]$ pwd /home/centos 切换root方法: 在root的/etc/sudoer文件中添加如下行 [root@localhost ~]# visudo User_Alias ADMINS = centos Cmnd_Alias SWITCH = /bin/su ADMINS ALL=(root) SWITCH 切换root [centos@localhost /]$ sudo su - 7、查看在登陆过程抓包的内容 # tcpdump -i-nn -vv -A A ASCII nn 端口为 numeric vv 详细
dropbear使用
1、安装开发包组
# yum -y groupinstall "Development Tools" "Server Platform Development"
# yum install automake autoconf make gcc glibc
automake --> ./configure
autoconf --> Makefile.in
./configure + Makefile.in --> Makefile
make + Makefile
2、获取源码
dropbear-2017.75.tar.bz2
3、展开
# tar xf dropbear-2017.75.tar.bz2
# cd dropbear-2017.75
4、查看文件
# less INSTALL
./configure (optionally with --disable-zlib or --disable-syslog,
or --help for other options)
Now compile:
make PROGRAMS="dropbear dbclient dropbearkey dropbearconvert scp"
And install (/usr/local/bin is usual default):
make PROGRAMS="dropbear dbclient dropbearkey dropbearconvert scp" install
5、编译
[root@localhost dropbear-2017.75]# ./configure --prefix=/usr/local/dropbear
--prefix 方便卸载:默认安装在/usr目录对应的bin,sbin,lib,share,include中
checking for deflate in -lz... no //deflate 压缩过滤器
configure: error: *** zlib missing - install first or check config.log ***
# yum install zlib-devel
[root@localhost dropbear-2017.75]# ./configure --prefix=/usr/local/dropbear
# make PROGRAMS="dropbear dbclient dropbearkey scp"
# make PROGRAMS="dropbear dbclient dropbearkey scp" install
# ls /usr/local/dropbear/
bin sbin share
# cat > /etc/profile.d/dropbear.sh << EOF
export PATH=/usr/local/dropbear/bin:/usr/local/dropbear/sbin:$PATH
EOF
# . /etc/profile.d/dropbear.sh
6、生成主机密钥
# install -d /etc/dropbear
# dropbear -h //获取-r后的文件路径
# dropbearkey -h //获取不同类型对应的字节大小
# dropbearkey -t rsa -f /etc/dropbear/dropbear_rsa_host_key -s 2048
# dropbearkey -t dss -f /etc/dropbear/dropbear_dss_host_key -s 1024
# dropbearkey -t ecdsa -f /etc/dropbear/dropbear_ecdsa_host_key -s 521
7、启动服务
# dropbear -F -E -p 0.0.0.0:9999
# killall -0 dropbear //运行中不会返回任何值
# ps axu | grep -v grep | fgrep 9999
root dropbear -F -E -p 0.0.0.0:9999
以root用户身份运行
##检查Pid对就的命令是dropbear
# ps -p `cat /var/run/dropbear.pid` --no-headers -o comm
##检查端口
# ss -tunlp | fgrep 9999
tcp LISTEN *:9999 users:(("dropbear",1389,3))
8、测试连接
[c:\~]$ ssh
NAME
ssh - connects to a host using the SSH protocol.
SYNOPSYS
ssh [user@]host[ port][;host[ port]]
[c:\~]$ ssh [email protected] 9999
172.16.100.1:ssh 172.16.0.1:63058 timer:(keepalive,31min,0)
1、启动后台进程: # dropbear -p 0.0.0.0:8888 2、连接 [root@localhost ~]# dbclient -p 9999 -l root 172.16.100.1 Host '172.16.100.1' is not in the trusted hosts file. (ecdsa-sha2-nistp521 fingerprint md5 6f:4a:f9:26:ef:e7:ed:4b:33:17:ce:6b:ef:d8:20:03) Do you want to continue connecting? (y/n) y [email protected]'s password: [root@localhost ~]# [root@localhost ~]# pwd /root
服务脚本dropbear
[root@localhost ~]# vim /etc/rc.d/init.d/dropbear
#!/bin/bash
#
# dropbear is an implementation of SSH(Secure Socket Handler)
#
# chkconfig: - 13 87
#
. /etc/rc.d/init.d/functions
start() {
echo -n "Start dropbear:"
[ -r /etc/dropbear/dropbear_dss_host_key ] || /usr/local/dropbear/bin/dropbearkey -t dss -f /etc/dropbear/dropbear_dss_host_key -s 1024
[ -r /etc/dropbear/dropbear_rsa_host_key ] || /usr/local/dropbear/bin/dropbearkey -t rsa -f /etc/dropbear/dropbear_rsa_host_key -s 2048
[ -r /etc/dropbear/dropbear_ecdsa_host_key ] || /usr/local/dropbear/bin/dropbearkey -t ecdsa -f /etc/dropbear/dropbear_ecdsa_host_key -s 521
/usr/local/dropbear/sbin/dropbear -p 0.0.0.0:9999
success
echo
}
stop() {
echo -n "Stop dropbear:"
kill `pidof -o %PPID dropbear` &> /dev/null
success
echo
}
reload() {
if [ -r /var/run/dropbear.pid ] && [ `ps -p $(/bin/cat /var/run/dropbear.pid) --no-headers -o comm` == "dropbear" ]; then
kill -1 `/bin/cat /var/run/dropbear.pid`
fi
}
restart() {
stop
start
}
status() {
if [ -r /var/run/dropbear.pid ] && [ `ps -p $(/bin/cat /var/run/dropbear.pid) --no-headers -o comm` == "dropbear" ]; then
echo "dropbear is running...."
else
echo "dropbear is stopped yet..."
fi
}
case $1 in
start)
start
;;
stop)
stop
;;
restart)
restart
;;
status)
status
;;
*)
echo "Usage: dropbear {start|stop|status|restart}"
;;
esac
# chmod +x /etc/rc.d/init.d/dropbear
# chkconfig --add dropbear
# chkconfig --list dropbear
dropbear 0:off 1:off 2:off 3:off 4:off 5:off 6:off
# chkconfig --levels 345 dropbear on
# chkconfig --list dropbear
dropbear 0:off 1:off 2:off 3:on 4:on 5:on 6:off
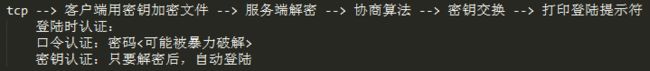
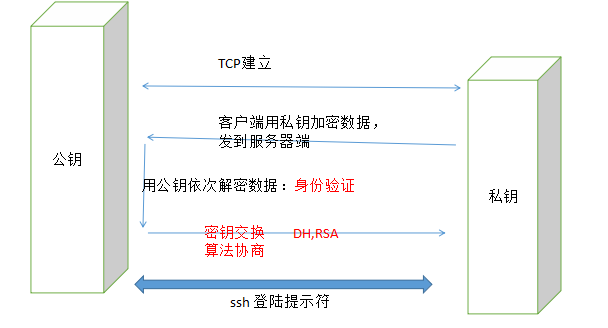
OpenSSH(Secure Socket Handler)密钥认证流程
ssh协议
OpenSSH相关的工具
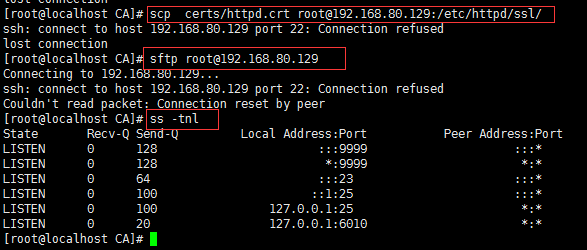
# rpm -qi openssh-clients An open source SSH client applications # rpm -qi openssh-server An open source SSH server daemon [root@localhost ~]# rpm -ql openssh-clients /etc/ssh/ssh_config /usr/bin/scp //基于ssh协议的复制工具 /usr/bin/sftp //基于ssh协议的ftp工具 /usr/bin/ssh //基于ssh协议的Linux客户端命令 /usr/bin/ssh-copy-id /usr/bin/ssh-keyscan [root@localhost ~]# rpm -ql openssh-server /etc/ssh/sshd_config /usr/sbin/.sshd.hmac /usr/sbin/sshd Windows客户端: xshell(XFTP), putty(XFTP), securecrt, sshsecureshellclient
openssh-clients相关配置
配置文件<读取配置完成特性设置>
/etc/ssh/ssh_config Host * //Host PATTERN即表示连接Host的范围 Port 22 //默认连接端口 ForwardX11 no //默认X11协议关闭,要使用远端的图形程序必须要开启,ssh -X即可
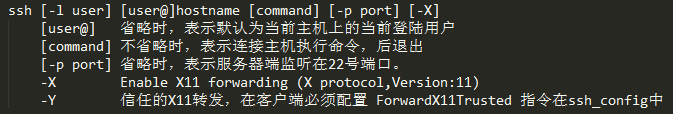
ssh命令 以ssh连接远程主机
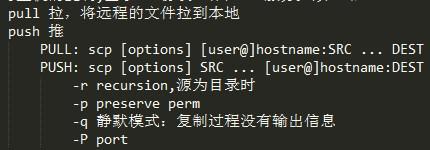
scp命令 跨主机的复制,只有基于ssh协议工作
sftp命令 安全的ftp工作,只有基于ssh协议工作
Openssh-server相关的配置
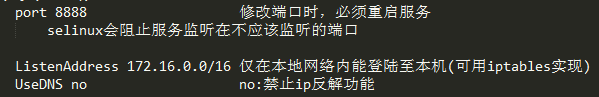
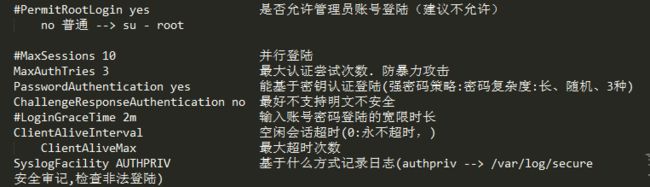
配置文件 /etc/ssh/sshd_config
登陆认证
必须确定
必须修改
安全相关的选项
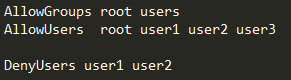
限制可登陆用户
使用示例
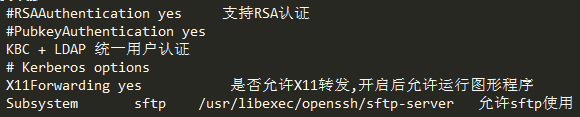
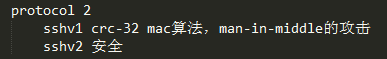
PasswordAuthentication yes //密码认证 ChallengeResponseAuthentication no //挑战式认证 GSSAPIAuthentication yes GSSAPICleanupCredentials yes UsePAM yes AcceptEnv LANG LC_CTYPE LC_NUMERIC LC_TIME LC_COLLATE LC_MONETARY LC_MESSAGES AcceptEnv LC_PAPER LC_NAME LC_ADDRESS LC_TELEPHONE LC_MEASUREMENT AcceptEnv LC_IDENTIFICATION LC_ALL LANGUAGE AcceptEnv XMODIFIERS X11Forwarding yes //支持X11 Subsystem sftp /usr/libexec/openssh/sftp-server //支持sftp Protocol 2 port 22022 ListenAddress 192.168.206.0 UseDNS no PermitRootLogin yes MaxSession 10 MaxAuthTries 3 LoginGraceTime 10s ClientAliveInterval 10s ClientAliveMax 1 SyslogFacility AUTHPRIV AllowUsers root
基于密钥认证登陆openssh-server
生成一对密钥,公钥放在服务器端的对应用户账号的对应家目录下的.ssh目录中authorized_keys文件中
# openssl genrsa -out scretkey 768 # openssl rsa -in scretkey -out pubkey -pubout # cat pubkey >> ~/.ssh/authorized_keys 不能登陆....
# ssh-keygen -f ~/.ssh/id_rsa -P '' -t rsa -b 768 # # cat .ssh/id_rsa.pub >> .ssh/authorized_keys 登陆成功....