- discuz discuz_admincp.php 讲解,Discuz! 1.5-2.5 命令执行漏洞分析(CVE-2018-14729)
weixin_39740419
discuz讲解
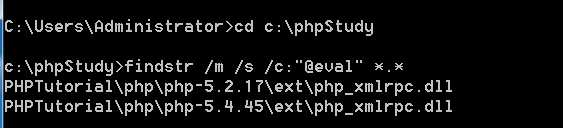
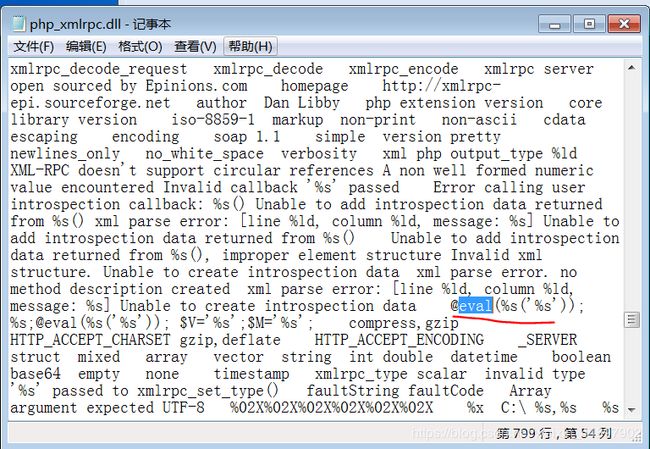
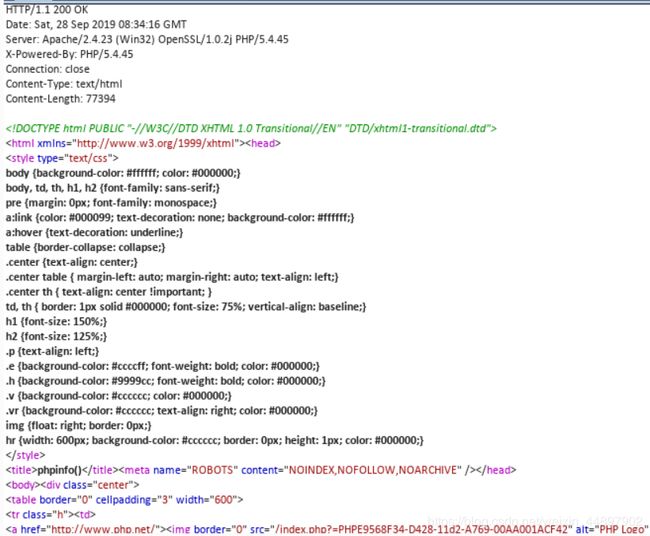
0x00漏洞简述漏洞信息8月27号有人在GitHub上公布了有关Discuz1.5-2.5版本中后台数据库备份功能存在的命令执行漏洞的细节。漏洞影响版本Discuz!1.5-2.50x01漏洞复现官方论坛下载相应版本就好。0x02漏洞分析需要注意的是这个漏洞其实是需要登录后台的,并且能有数据库备份权限,所以比较鸡肋。我这边是用Discuz!2.5完成漏洞复现的,并用此进行漏洞分析的。漏洞点在:so
- 【漏洞复现】2023HVV WPS Office 远程代码执行漏洞(RCE)
李火火安全阁
漏洞复现应用安全WPSOffice
文章目录前言声明一、漏洞描述二、影响范围三、漏洞复现服务端的功能客户端的功能四、修复建议前言2023HVV期间曝出的WPSOffice存在RCE漏洞,攻击者可通过该漏洞执行任意命令,获取服务器控制权限。声明请勿利用文章内的相关技术从事非法测试,由于传播、利用此文所提供的信息或者工具而造成的任何直接或者间接的后果及损失,均由使用者本人负责,所产生的一切不良后果与文章作者无关。该文章仅供学习用途使用。
- aspcms webshell漏洞复现
青衫木牛马
aspaspcmsgetshell
1.【ip】/admin_aspcms/login.asp访问后台,admin123456登录2.点击【扩展功能】【幻灯片设置】点击【保存】开启代理进行抓包3.在抓取的数据包中修改slideTextStatus字段的值为以下代码并进行发包访问影响文件字段值1%25><%25密码是a影响文件/config/AspCms_Config.asp4.蚁剑连接
- Nginx越界读取缓存漏洞 CVE-2017-7529 漏洞复现
ADummy_
vulhub_Writeup网络安全渗透测试安全漏洞
Nginx越界读取缓存漏洞(CVE-2017-7529)byADummy0x00利用路线POC验证—>读取到缓存文件中位于“http返回包体”前的“文件头”、“http返回包头”等内容0x01漏洞介绍Nginx在反向代理站点的时候,通常会将一些文件进行缓存,特别是静态文件。缓存的部分存储在文件中,每个缓存文件包括“文件头”+“HTTP返回包头”+“HTTP返回包体”。如果二次请求命中了该缓存文件,
- 【漏洞复现】华三 H3C IMC 智能管理中心 /byod/index.xhtml RCE
凝聚力安全团队
漏洞复现xhtml前端htmlweb渗透web网络安全渗透测试
免责声明:本文内容旨在提供有关特定漏洞或安全漏洞的信息,以帮助用户更好地了解可能存在的风险。公布此类信息的目的在于促进网络安全意识和技术进步,并非出于任何恶意目的。阅读者应该明白,在利用本文提到的漏洞信息或进行相关测试时,可能会违反某些法律法规或服务协议。同时,未经授权地访问系统、网络或应用程序可能导致法律责任或其他严重后果。作者不对读者基于本文内容而产生的任何行为或后果承担责任。读者在使用本文所
- 「漏洞复现」契约锁电子签章平台 add 远程命令执行漏洞
鲨鱼辣椒丶D
漏洞复现web安全
0x01免责声明请勿利用文章内的相关技术从事非法测试,由于传播、利用此文所提供的信息而造成的任何直接或者间接的后果及损失,均由使用者本人负责,作者不为此承担任何责任。工具来自网络,安全性自测,如有侵权请联系删除。本次测试仅供学习使用,如若非法他用,与平台和本文作者无关,需自行负责!!!0x02产品介绍契约锁电子签章平台是上海亘岩网络科技有限公司推出的一套数字签章解决方案。契约锁为中大型组织提供“数
- weblogic-SSRF漏洞复现(SSRF原理、利用与防御)
不想当脚本小子的脚本小子
中间件漏洞复现SSRF安全
一、SSRF概念服务端请求伪造(Server-SideRequestForgery),是一种由攻击者构造形成由服务端发起请求的一个安全漏洞。一般情况下,SSRF攻击的目标是从外网无法访问的内部系统。SSRF形成的原因大都是由于服务端提供了从其他服务器应用获取数据的功能,且没有对目标地址做过滤与限制。比如从指定URL地址获取网页文本内容,加载指定地址的图片、文档等等。首先,我们要对目标网站的架构了解
- fastbee物联网管理系统download接口任意文件下载漏洞
抠脚大汉在网络
漏洞复现漏洞
fastbee物联网管理系统download接口任意文件下载漏洞文章目录fastbee物联网管理系统download接口任意文件下载漏洞免责申明搜索语法漏洞描述漏洞复现修复建议免责申明本文章仅供学习与交流,请勿用于非法用途,均由使用者本人负责,文章作者不为此承担任何责任搜索语法fofaicon_hash="-307138793"&&title=="FastBee物联网系统"漏洞描述FastBee是
- 某云彩SRM2.0后台绕过漏洞
抠脚大汉在网络
漏洞复现漏洞
文章目录免责申明搜索语法漏洞描述漏洞复现修复建议免责申明本文章仅供学习与交流,请勿用于非法用途,均由使用者本人负责,文章作者不为此承担任何责任搜索语法fofaicon_hash="1665918155"漏洞描述某云采SRM2.0是一款先进的供应链管理系统,旨在优化企业的采购流程和供应商管理。该系统通过云端技术,提供实时的数据分析和智能决策支持,帮助企业提高采购效率和降低成本。该系统在autolog
- 【漏洞复现】蜂信物联 FastBee 开源物联网平台 download 任意文件读取漏洞
炫彩@之星
漏洞复现漏洞复现网络安全安全性测试安全
【漏洞复现】蜂信物联FastBee开源物联网平台download任意文件读取漏洞、01漏洞描述蜂信物联FastBee开源物联网平台download接口存在任意文件读取漏洞,未经身份验证攻击者可通过该漏洞读取系统重要文件(如数据库配置文件、系统配置文件),导致网站处于极度不安全状态。02漏洞环境FOFA语法:body=“FastBee物联网系统”||icon_hash=“-307138793”03漏
- CVE-2024-25852 Linksys RE7000无线扩展器 RCE漏洞
抠脚大汉在网络
漏洞复现漏洞漏洞
文章目录免责声明漏洞描述漏洞原理影响版本漏洞复现修复建议免责声明本文章仅供学习与交流,请勿用于非法用途,均由使用者本人负责,文章作者不为此承担任何责任漏洞描述RE7000是Linksys推出的一款具有无缝漫游功能的双频AC1900无线扩展器,重点是withseamlessroaming(无缝漫游)漏洞原理RE7000无线扩展器在访问/goform/AccessControl功能接口时在Access
- 用友U8 Cloud RepAddToTaskAction SQL注入漏洞复现
天官赐福万无禁忌
漏洞复现安全web安全
1产品简介用友U8Cloud是用友推出的新一代云ERP,主要聚焦成长型、创新型企业,提供企业级云ERP整体解决方案。2漏洞概述用友U8CloudRepAddToTaskAction接口处存在SQL注入漏洞,未经身份验证的远程攻击者除了可以利用SQL注入漏洞获取数据库中的信息(例如,管理员后台密码、站点的用户个人信息)之外,甚至在高权限的情况可向服务器中写入木马,进一步获取服务器系统权限。3影响范围
- 用友U8-CRM exportdictionary.php SQL注入
iSee857
漏洞复现安全
0x01漏洞描述:用友U8-CRM的/devtools/tools/exportdictionary.php接口处存在SQL注入漏洞。这可能导致泄露敏感数据、破坏数据库完整性,甚至获取对数据库的完全控制。0x02影响版本:V16.1,V16.0,V15.1,V15.0,V130x03搜索语句:Fofa:title="用友U8CRM"0x04漏洞复现:GET/devtools/tools/expor
- 用友U8 CRM exportdictionary.php SQL注入漏洞复现
0xSecl
漏洞复现安全web安全
0x01产品简介用友U8CRM客户关系管理系统是一款专业的企业级CRM软件,旨在帮助企业高效管理客户关系、提升销售业绩和提供优质的客户服务。0x02漏洞概述用友U8CRM客户关系管理系统exportdictionary.php文件存在SQL注入漏洞,未经身份验证的攻击者通过漏洞执行任意SQL语句,调用xp_cmdshell写入后门文件,执行任意代码,从而获取到服务器权限。<
- 【系统安全】Windows内核权限提升漏洞(CVE-2024-30088)
李火火安全阁
漏洞复现系统安全系统安全windows
文章目录前言一、漏洞概述二、影响范围三、漏洞复现四、修复建议前言CVE-2024-30088是Windows内核提权漏洞,由越南安全研究员@BùiQuangHiếu详细分析。漏洞发生在AuthzBasepCopyoutInternalSecurityAttributes函数中,该函数在复制SecurityAttributesList时会使用用户提供的指针,在校验及复制期间存在时间差,导致存在TOC
- 福建科立讯通信 指挥调度管理平台 SQL注入漏洞复现(CVE-2024-2620、CVE-2024-2621)
OidBoy_G
漏洞复现安全web安全
0x01产品简介福建科立讯通信指挥调度管理平台是一个专门针对通信行业的管理平台。该产品旨在提供高效的指挥调度和管理解决方案,以帮助通信运营商或相关机构实现更好的运营效率和服务质量。该平台提供强大的指挥调度功能,可以实时监控和管理通信网络设备、维护人员和工作任务等。用户可以通过该平台发送指令、调度人员、分配任务,并即时获取现场反馈和报告。0x02漏洞概述福建科立讯通信指挥调度管理平台down_fil
- WordPress Plugin NotificationX插件 SQL注入漏洞复现(CVE-2024-1698)
OidBoy_G
漏洞复现sqlweb安全安全
0x01产品简介WordPress和WordPressplugin都是WordPress基金会的产品。WordPress是一套使用PHP语言开发的博客平台。该平台支持在PHP和MySQL的服务器上架设个人博客网站。0x02漏洞概述WordPresspluginNotificationX是一个应用插件。2.8.2版本及之前存在安全漏洞,该漏洞源于对用户提供的参数转义不充分以及对现有SQL查询缺乏充分
- 友点CMS GetSpecial SQL注入漏洞复现
OidBoy_G
漏洞复现安全web安全
0x01产品简介友点CMS是一款高效且灵活的网站管理系统,它为用户提供了简单易用的界面和丰富的功能。无论是企业还是个人,都能通过友点CMS快速搭建出专业且美观的网站。该系统支持多种内容类型和自定义模板,方便用户按需调整。同时,它具备强大的SEO功能,能提升网站在搜索引擎中的排名。友点CMS还支持多语言设置,适应国际化需求。总的来说,友点CMS是网站建设的理想选择,既高效又易用。0x02漏洞概述友点
- 友点CMS image_upload.php 文件上传漏洞复现
OidBoy_G
漏洞复现phpweb安全安全
0x01产品简介友点CMS是一款高效且灵活的网站管理系统,它为用户提供了简单易用的界面和丰富的功能。无论是企业还是个人,都能通过友点CMS快速搭建出专业且美观的网站。该系统支持多种内容类型和自定义模板,方便用户按需调整。同时,它具备强大的SEO功能,能提升网站在搜索引擎中的排名。友点CMS还支持多语言设置,适应国际化需求。总的来说,友点CMS是网站建设的理想选择,既高效又易用。0x02漏洞概述友点
- JeePlus快速开发平台 validateMobile SQL注入漏洞复现
OidBoy_G
漏洞复现sqlweb安全安全
0x01产品简介JeePlus(洁普斯)是一个软件快速开发平台,使用多种现代Web技术,包括SpringCloud/SpringBoot、MyBatisPlus、SpringSecurity、Redis、Vue3、ElementPlus等。该平台支持多种数据库,如MySQL、Oracle、sqlserver、postgresql等。JeePlus采用标准的SOA架构,依托优秀的前台富客户端框架(如
- F5漏洞复现[CVE-2020-5902]与[CVE_2021_22986]
Coder_preston
计算机安全pytorchgitbranch
引言 F5BIG-IP广泛应用于大型企业,数据中心、云计算平台中,可以实现应用加速、负载均衡、SLL过载、web应用防火墙等功能。这篇文章主要是复现F5的漏洞,包括其被远程代码执行的过程,以及探究以下我们可以在F5上远程执行代码之后可以做哪些事情。环境搭建 F5的环境搭建教程在网上可以查到很多,这里大概介绍以下流程与心得。首先搭建环境需要使用vmware软件运行F5的镜像来实现,需要下载并安装相关
- 【漏洞复现】F5 BIG-IP 远程代码执行漏洞(CVE-2023-46747)
webQD153
tcp/ip网络协议网络
F5BIG-IP远程代码执行漏洞(CVE-2023-46747)漏洞描述F5BIG-IP远程代码执行漏洞(CVE-2023-46747),未经授权的远程攻击者通过管理端口或自身IP地址访问BIG-IP系统,利用此漏洞可能绕过身份认证,导致在暴露流量管理用户界面(TMUI)的F5BIG-IP实例上执行任意代码。影响版本F5BIG-IP<=17.1.016.1.0<=F5BIG-IP<=16.1.41
- 命令执行漏洞超详细讲解
摆烂阳
网络安全服务器网络安全
博主昵称:摆烂阳博主主页跳转链接博主研究方向:web渗透测试、python编程博主寄语:希望本篇文章能给大家带来帮助,有不足的地方,希望友友们给予指导————————————————目录一、原理二、利用条件三、漏洞分类1、远程命令执行漏洞2、远程代码执行漏洞四、认识命令连接符1、window层面2、linux层面五、漏洞的产生原因六、漏洞的危害七、漏洞复现1、log4j命令执行2、向日葵命令执行
- [旧文系列] Struts2历史高危漏洞系列-part2:S2-007/S2-008/S2-009
xc8qanAFenlka@x1
struts安全web安全java
文章目录关于前言S2-007漏洞复现与分析可回显PoC漏洞修复S2-008漏洞复现与分析Vuln-1:RemotecommandexecutioninCookieInterceptorVuln-2:RemotecommandexecutioninDebuggingInterceptorVuln-2:可回显PoC漏洞修复S2-009漏洞复现与分析可回显PoC漏洞修复Reference关于系列是笔者将
- Struts2 S2-045漏洞复现
你能拿我咋的
渗透测试漏洞复现strutsjavaweb安全
1.漏洞概述OGNL是ObjectGraphicNavigationLanguage(对象图导航语言)的缩写,它是一个开源项目。Struts框架使用OGNL作为默认的表达式语言。struts2的rce本质都是一样的(除了S2-052以外),都是Struts2框架执行了恶意用户传进来的OGNL表达式,造成远程代码执行。可以造成“命令执行、服务器文件操作、打印回显、获取系统属性、危险代码执行”等,只不
- XMall 开源商城 SQL注入漏洞复现(CVE-2024-24112)
OidBoy_G
漏洞复现web安全安全sql
0x01产品简介XMall开源电商商城是开发者Exrick的一款基于SOA架构的分布式电商购物商城前后端分离前台商城:Vue全家桶后台管理:Dubbo/SSM/Elasticsearch/Redis/MySQL/ActiveMQ/Shiro/Zookeeper等。0x02漏洞概述XMall开源商城/item/list、/item/listSearch、/sys/log、/order/list、/m
- threehit漏洞复现以及防御
凌晨五点的星
网络安全安全web安全
说白了跟sql-liql靶场二次注入一样,也是一个转义函数而这次是,入库的时候不转义,出库的时候会转义导致这个漏洞出现开始测试:这是我注册完test刚登录的情况找注入点更新数据的update,很容易找到在age段这次我注册的时候用户还是test,但是年龄我对后面进行了省略可以看到我直接登录到管理员上了防御:可以进行强转这样无法闭合漏洞也就无法实现了
- 【漏洞复现】H3C 路由器多系列信息泄露漏洞
晚风不及你ღ
【漏洞复现】安全服务器web安全网络
Nx01产品简介H3C路由器是一款高性能的路由器产品,具有稳定的性能和丰富的功能。它采用了先进的路由技术和安全机制,可以满足不同用户的需求,广泛应用于企业、运营商和数据中心等领域。Nx02漏洞描述H3C路由器多系列存在信息泄露漏洞,攻击者可以利用该漏洞获取备份文件中的管理员账户及密码等敏感信息。Nx03产品主页hunter-query:app.name="H3CRouterManagement"N
- vulhub中Apache Log4j Server 反序列化命令执行漏洞复现(CVE-2017-5645)
余生有个小酒馆
vulhub漏洞复现apachelog4j
ApacheLog4j是一个用于Java的日志记录库,其支持启动远程日志服务器。ApacheLog4j2.8.2之前的2.x版本中存在安全漏洞。攻击者可利用该漏洞执行任意代码。1.我们使用ysoserial生成payload,然后直接发送给`your-ip:4712`端口即可。java-jarysoserial-master-v0.0.5-gb617b7b-16.jarCommonsCollect
- 【漏洞复现-通达OA】通达OA getcallist存在前台SQL注入漏洞
xiaokp7
漏洞复现sql数据库
一、漏洞简介通达OA(OfficeAnywhere网络智能办公系统)是由北京通达信科科技有限公司自主研发的协同办公自动化软件,是与中国企业管理实践相结合形成的综合管理办公平台。通达OA为各行业不同规模的众多用户提供信息化管理能力,包括流程审批、行政办公、日常事务、数据统计分析、即时通讯、移动办公等,帮助广大用户降低沟通和管理成本,提升生产和决策效率。通达OAgetcallist存在前台SQL注入漏
- 书其实只有三类
西蜀石兰
类
一个人一辈子其实只读三种书,知识类、技能类、修心类。
知识类的书可以让我们活得更明白。类似十万个为什么这种书籍,我一直不太乐意去读,因为单纯的知识是没法做事的,就像知道地球转速是多少一样(我肯定不知道),这种所谓的知识,除非用到,普通人掌握了完全是一种负担,维基百科能找到的东西,为什么去记忆?
知识类的书,每个方面都涉及些,让自己显得不那么没文化,仅此而已。社会认为的学识渊博,肯定不是站在
- 《TCP/IP 详解,卷1:协议》学习笔记、吐槽及其他
bylijinnan
tcp
《TCP/IP 详解,卷1:协议》是经典,但不适合初学者。它更像是一本字典,适合学过网络的人温习和查阅一些记不清的概念。
这本书,我看的版本是机械工业出版社、范建华等译的。这本书在我看来,翻译得一般,甚至有明显的错误。如果英文熟练,看原版更好:
http://pcvr.nl/tcpip/
下面是我的一些笔记,包括我看书时有疑问的地方,也有对该书的吐槽,有不对的地方请指正:
1.
- Linux—— 静态IP跟动态IP设置
eksliang
linuxIP
一.在终端输入
vi /etc/sysconfig/network-scripts/ifcfg-eth0
静态ip模板如下:
DEVICE="eth0" #网卡名称
BOOTPROTO="static" #静态IP(必须)
HWADDR="00:0C:29:B5:65:CA" #网卡mac地址
IPV6INIT=&q
- Informatica update strategy transformation
18289753290
更新策略组件: 标记你的数据进入target里面做什么操作,一般会和lookup配合使用,有时候用0,1,1代表 forward rejected rows被选中,rejected row是输出在错误文件里,不想看到reject输出,将错误输出到文件,因为有时候数据库原因导致某些column不能update,reject就会output到错误文件里面供查看,在workflow的
- 使用Scrapy时出现虽然队列里有很多Request但是却不下载,造成假死状态
酷的飞上天空
request
现象就是:
程序运行一段时间,可能是几十分钟或者几个小时,然后后台日志里面就不出现下载页面的信息,一直显示上一分钟抓取了0个网页的信息。
刚开始已经猜到是某些下载线程没有正常执行回调方法引起程序一直以为线程还未下载完成,但是水平有限研究源码未果。
经过不停的google终于发现一个有价值的信息,是给twisted提出的一个bugfix
连接地址如下http://twistedmatrix.
- 利用预测分析技术来进行辅助医疗
蓝儿唯美
医疗
2014年,克利夫兰诊所(Cleveland Clinic)想要更有效地控制其手术中心做膝关节置换手术的费用。整个系统每年大约进行2600例此类手术,所以,即使降低很少一部分成本,都可以为诊 所和病人节约大量的资金。为了找到适合的解决方案,供应商将视野投向了预测分析技术和工具,但其分析团队还必须花时间向医生解释基于数据的治疗方案意味着 什么。
克利夫兰诊所负责企业信息管理和分析的医疗
- java 线程(一):基础篇
DavidIsOK
java多线程线程
&nbs
- Tomcat服务器框架之Servlet开发分析
aijuans
servlet
最近使用Tomcat做web服务器,使用Servlet技术做开发时,对Tomcat的框架的简易分析:
疑问: 为什么我们在继承HttpServlet类之后,覆盖doGet(HttpServletRequest req, HttpServetResponse rep)方法后,该方法会自动被Tomcat服务器调用,doGet方法的参数有谁传递过来?怎样传递?
分析之我见: doGet方法的
- 揭秘玖富的粉丝营销之谜 与小米粉丝社区类似
aoyouzi
揭秘玖富的粉丝营销之谜
玖富旗下悟空理财凭借着一个微信公众号上线当天成交量即破百万,第七天成交量单日破了1000万;第23天时,累计成交量超1个亿……至今成立不到10个月,粉丝已经超过500万,月交易额突破10亿,而玖富平台目前的总用户数也已经超过了1800万,位居P2P平台第一位。很多互联网金融创业者慕名前来学习效仿,但是却鲜有成功者,玖富的粉丝营销对外至今仍然是个谜。
近日,一直坚持微信粉丝营销
- Java web的会话跟踪技术
百合不是茶
url会话Cookie会话Seession会话Java Web隐藏域会话
会话跟踪主要是用在用户页面点击不同的页面时,需要用到的技术点
会话:多次请求与响应的过程
1,url地址传递参数,实现页面跟踪技术
格式:传一个参数的
url?名=值
传两个参数的
url?名=值 &名=值
关键代码
- web.xml之Servlet配置
bijian1013
javaweb.xmlServlet配置
定义:
<servlet>
<servlet-name>myservlet</servlet-name>
<servlet-class>com.myapp.controller.MyFirstServlet</servlet-class>
<init-param>
<param-name>
- 利用svnsync实现SVN同步备份
sunjing
SVN同步E000022svnsync镜像
1. 在备份SVN服务器上建立版本库
svnadmin create test
2. 创建pre-revprop-change文件
cd test/hooks/
cp pre-revprop-change.tmpl pre-revprop-change
3. 修改pre-revprop-
- 【分布式数据一致性三】MongoDB读写一致性
bit1129
mongodb
本系列文章结合MongoDB,探讨分布式数据库的数据一致性,这个系列文章包括:
数据一致性概述与CAP
最终一致性(Eventually Consistency)
网络分裂(Network Partition)问题
多数据中心(Multi Data Center)
多个写者(Multi Writer)最终一致性
一致性图表(Consistency Chart)
数据
- Anychart图表组件-Flash图转IMG普通图的方法
白糖_
Flash
问题背景:项目使用的是Anychart图表组件,渲染出来的图是Flash的,往往一个页面有时候会有多个flash图,而需求是让我们做一个打印预览和打印功能,让多个Flash图在一个页面上打印出来。
那么我们打印预览的思路是获取页面的body元素,然后在打印预览界面通过$("body").append(html)的形式显示预览效果,结果让人大跌眼镜:Flash是
- Window 80端口被占用 WHY?
bozch
端口占用window
平时在启动一些可能使用80端口软件的时候,会提示80端口已经被其他软件占用,那一般又会有那些软件占用这些端口呢?
下面坐下总结:
1、web服务器是最经常见的占用80端口的,例如:tomcat , apache , IIS , Php等等;
2
- 编程之美-数组的最大值和最小值-分治法(两种形式)
bylijinnan
编程之美
import java.util.Arrays;
public class MinMaxInArray {
/**
* 编程之美 数组的最大值和最小值 分治法
* 两种形式
*/
public static void main(String[] args) {
int[] t={11,23,34,4,6,7,8,1,2,23};
int[]
- Perl正则表达式
chenbowen00
正则表达式perl
首先我们应该知道 Perl 程序中,正则表达式有三种存在形式,他们分别是:
匹配:m/<regexp>;/ (还可以简写为 /<regexp>;/ ,略去 m)
替换:s/<pattern>;/<replacement>;/
转化:tr/<pattern>;/<replacemnt>;
- [宇宙与天文]行星议会是否具有本行星大气层以外的权力呢?
comsci
举个例子: 地球,地球上由200多个国家选举出一个代表地球联合体的议会,那么现在地球联合体遇到一个问题,地球这颗星球上面的矿产资源快要采掘完了....那么地球议会全体投票,一致通过一项带有法律性质的议案,既批准地球上的国家用各种技术手段在地球以外开采矿产资源和其它资源........
&
- Oracle Profile 使用详解
daizj
oracleprofile资源限制
Oracle Profile 使用详解 转
一、目的:
Oracle系统中的profile可以用来对用户所能使用的数据库资源进行限制,使用Create Profile命令创建一个Profile,用它来实现对数据库资源的限制使用,如果把该profile分配给用户,则该用户所能使用的数据库资源都在该profile的限制之内。
二、条件:
创建profile必须要有CREATE PROFIL
- How HipChat Stores And Indexes Billions Of Messages Using ElasticSearch & Redis
dengkane
elasticsearchLucene
This article is from an interview with Zuhaib Siddique, a production engineer at HipChat, makers of group chat and IM for teams.
HipChat started in an unusual space, one you might not
- 循环小示例,菲波拉契序列,循环解一元二次方程以及switch示例程序
dcj3sjt126com
c算法
# include <stdio.h>
int main(void)
{
int n;
int i;
int f1, f2, f3;
f1 = 1;
f2 = 1;
printf("请输入您需要求的想的序列:");
scanf("%d", &n);
for (i=3; i<n; i
- macbook的lamp环境
dcj3sjt126com
lamp
sudo vim /etc/apache2/httpd.conf
/Library/WebServer/Documents
是默认的网站根目录
重启Mac上的Apache服务
这个命令很早以前就查过了,但是每次使用的时候还是要在网上查:
停止服务:sudo /usr/sbin/apachectl stop
开启服务:s
- java ArrayList源码 下
shuizhaosi888
ArrayList源码
版本 jdk-7u71-windows-x64
JavaSE7 ArrayList源码上:http://flyouwith.iteye.com/blog/2166890
/**
* 从这个列表中移除所有c中包含元素
*/
public boolean removeAll(Collection<?> c) {
- Spring Security(08)——intercept-url配置
234390216
Spring Securityintercept-url访问权限访问协议请求方法
intercept-url配置
目录
1.1 指定拦截的url
1.2 指定访问权限
1.3 指定访问协议
1.4 指定请求方法
1.1 &n
- Linux环境下的oracle安装
jayung
oracle
linux系统下的oracle安装
本文档是Linux(redhat6.x、centos6.x、redhat7.x) 64位操作系统安装Oracle 11g(Oracle Database 11g Enterprise Edition Release 11.2.0.4.0 - 64bit Production),本文基于各种网络资料精心整理而成,共享给有需要的朋友。如有问题可联系:QQ:52-7
- hotspot虚拟机
leichenlei
javaHotSpotjvm虚拟机文档
JVM参数
http://docs.oracle.com/javase/6/docs/technotes/guides/vm/index.html
JVM工具
http://docs.oracle.com/javase/6/docs/technotes/tools/index.html
JVM垃圾回收
http://www.oracle.com
- 读《Node.js项目实践:构建可扩展的Web应用》 ——引编程慢慢变成系统化的“砌砖活”
noaighost
Webnode.js
读《Node.js项目实践:构建可扩展的Web应用》
——引编程慢慢变成系统化的“砌砖活”
眼里的Node.JS
初初接触node是一年前的事,那时候年少不更事。还在纠结什么语言可以编写出牛逼的程序,想必每个码农都会经历这个月经性的问题:微信用什么语言写的?facebook为什么推荐系统这么智能,用什么语言写的?dota2的外挂这么牛逼,用什么语言写的?……用什么语言写这句话,困扰人也是阻碍
- 快速开发Android应用
rensanning
android
Android应用开发过程中,经常会遇到很多常见的类似问题,解决这些问题需要花时间,其实很多问题已经有了成熟的解决方案,比如很多第三方的开源lib,参考
Android Libraries 和
Android UI/UX Libraries。
编码越少,Bug越少,效率自然会高。
但可能由于 根本没听说过、听说过但没用过、特殊原因不能用、自己已经有了解决方案等等原因,这些成熟的解决
- 理解Java中的弱引用
tomcat_oracle
java工作面试
不久之前,我
面试了一些求职Java高级开发工程师的应聘者。我常常会面试他们说,“你能给我介绍一些Java中得弱引用吗?”,如果面试者这样说,“嗯,是不是垃圾回收有关的?”,我就会基本满意了,我并不期待回答是一篇诘究本末的论文描述。 然而事与愿违,我很吃惊的发现,在将近20多个有着平均5年开发经验和高学历背景的应聘者中,居然只有两个人知道弱引用的存在,但是在这两个人之中只有一个人真正了
- 标签输出html标签" target="_blank">关于标签输出html标签
xshdch
jsp
http://back-888888.iteye.com/blog/1181202
关于<c:out value=""/>标签的使用,其中有一个属性是escapeXml默认是true(将html标签当做转移字符,直接显示不在浏览器上面进行解析),当设置escapeXml属性值为false的时候就是不过滤xml,这样就能在浏览器上解析html标签,
&nb