快速入门openldap
1. 简单的目录
1.slapd.conf文件
- 这是一个示例slapd.conf,它将让我们开始使用Oracle Berkeley数据库(BDB)后端(OpenLDAP过去推荐的数据库——目前是mdb):
#
###### SAMPLE 1 - SIMPLE DIRECTORY ############
#
# NOTES: inetorgperson picks up attributes and objectclasses
# from all three schemas
#
# NB: RH Linux schemas in /etc/openldap
#
include /usr/local/etc/openldap/schema/core.schema
include /usr/local/etc/openldap/schema/cosine.schema
include /usr/local/etc/openldap/schema/inetorgperson.schema
# NO SECURITY - no access clause
# defaults to anonymous access for read
# only rootdn can write
# NO REFERRALS
# DON'T bother with ARGS file unless you feel strongly
# slapd scripts stop scripts need this to work
pidfile /var/run/openldap/slapd.pid
# enable a lot of logging - we might need it
# but generates huge logs
loglevel -1
# MODULELOAD definitions
# not required (comment out) before version 2.3
moduleload back_bdb.la
# NO TLS-enabled connections
# backend definition not required
#######################################################################
# bdb database definitions
#
# replace example and com below with a suitable domain
#
# If you don't have a domain you can leave it since example.com
# is reserved for experimentation or change them to my and inc
#
#######################################################################
database bdb
suffix "dc=example, dc=com"
# root or superuser
rootdn "cn=jimbob, dc=example, dc=com"
rootpw dirtysecret
# The database directory MUST exist prior to running slapd AND
# change path as necessary
directory /var/lib/ldap
# Indices to maintain for this directory
# unique id so equality match only
index uid eq
# allows general searching on commonname, givenname and email
index cn,gn,mail eq,sub
# allows multiple variants on surname searching
index sn eq,sub
# sub above includes subintial,subany,subfinal
# optimise department searches
index ou eq
# if searches will include objectClass uncomment following
# index objectClass eq
# shows use of default index parameter
index default eq,sub
# indices missing - uses default eq,sub
index telephonenumber eq
# other database parameters
# read more in slapd.conf reference section
cachesize 10000
checkpoint 128 15
- 使用命令检查配置是否有问题
slaptest -f /etc/openldap/slapd.conf
- 可能问题1
could not stat config file "/usr/local/etc/openldap/schema/core.schema解决: cp -r /etc/openldap/schema /usr/local/etc/openldap/schema
2. LDIF File
- 这个文件中有基础的用户信息。
## DEFINE DIT ROOT/BASE/SUFFIX ####
## uses RFC 2377 format
## replace example and com as necessary below
## or for experimentation leave as is
## dcObject is an AUXILLIARY objectclass and MUST
## have a STRUCTURAL objectclass (organization in this case)
# this is an ENTRY sequence and is preceded by a BLANK line
dn: dc=example,dc=com
dc: example
description: My wonderful company as much text as you want to place
in this line up to 32K continuation data for the line above must
have or i.e. ENTER works
on both Windows and *nix system - new line MUST begin with ONE SPACE
objectClass: dcObject
objectClass: organization
o: Example, Inc.
## FIRST Level hierarchy - people
## uses mixed upper and lower case for objectclass
# this is an ENTRY sequence and is preceded by a BLANK line
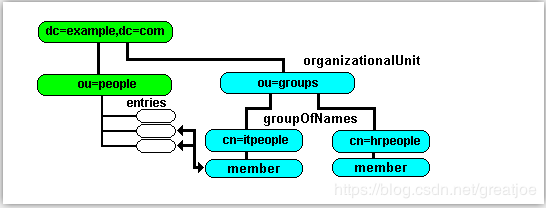
dn: ou=people, dc=example,dc=com
ou: people
description: All people in organisation
objectclass: organizationalunit
## SECOND Level hierarchy
## ADD a single entry under FIRST (people) level
# this is an ENTRY sequence and is preceded by a BLANK line
# the ou: Human Resources is the department name
dn: cn=Robert Smith,ou=people,dc=example,dc=com
objectclass: inetOrgPerson
cn: Robert Smith
cn: Robert J Smith
cn: bob smith
sn: smith
uid: rjsmith
userpassword: rJsmitH
carlicense: HISCAR 123
homephone: 555-111-2222
mail: [email protected]
mail: [email protected]
mail: [email protected]
description: swell guy
ou: Human Resources 3. 加载LDIF file文件
- 启动服务
systemctl start slapd- 通过命令添加ldif文件
ldapadd -x -D "cn=jimbob,dc=example,dc=com" -f /tmp/createdit.ldif -w dirtysecret4. 添加新的条目
- 下面的LDIF显示了如何使用LDIF添加其他条目。
version: 1
## ADD a single entry to people level
dn: cn=John Smith,ou=people,dc=example,dc=com
objectclass: inetOrgPerson
cn: John Smith
cn: John J Smith
sn: Smith
uid: jsmith
userpassword: jSmitH
carlicense: HISCAR 124
homephone: 555-111-2223
mail: [email protected]
mail: [email protected]
mail: [email protected]
ou: Sales
## ADD another single entry to people level
dn: cn=Sheri Smith,ou=people,dc=example,dc=com
objectclass: inetOrgPerson
cn: Sheri Smith
sn: smith
uid: ssmith
userpassword: sSmitH
carlicense: HERCAR 125
homephone: 555-111-2225
mail: [email protected]
mail: [email protected]
mail: [email protected]
ou: IT- 我们将上面的LDIF保存为addentry。在我们的/tmp目录中,我们使用ldapadd加载ldif文件,命令如下:
ldapadd -x -D "cn=jimbob,dc=example,dc=com" -f /tmp/addentry.ldif -w dirtysecret
5.修改条目
- 下面的LDIF显示了我们如何使用LDIF修改条目——使用LDAP浏览器通常更快,但是如果您有批量更改,LDIF会更快。
version: 1
## MODIFY the Robert Smith entry
dn: cn=Robert Smith,ou=people,dc=example,dc=com
changetype: modify
add: telephonenumber
telephonenumber: 555-555-1212
telephonenumber: 212
-
replace: uid
uid: rjosmith
-
replace: mail
mail: [email protected]
mail: [email protected]
-
# adds using URL format
add: jpegphoto
jpegphoto: < file://path/to/jpeg/file.jpg
-
delete: description- 我们将上面的LDIF保存为modentry。在我们的/tmp目录中,我们使用ldapadd加载ldif文件,命令如下:
ldapadd -x -D "cn=jimbob,dc=example,dc=com" -f /tmp/modentry.ldif -w dirtysecret
2.目录权限
1. 安全策略
现在,我们将使用slapd.conf中的access指令为我们的目录添加一些简单的安全性。
我们将根据公司政策(哇)建立一个访问控制策略(ACP aka ACL),该政策规定:
- 目录条目所有者能够查看和更新所有目录属性,包括密码。
- 人力资源必须能够更新任何条目,但必须无法读取或写入用户密码。
- 除人力资源和目录条目的所有者之外,任何人都不得读取目录条目carlicence,homepostaddress和homephone。
- 所有用户都必须进行身份验证(不允许匿名访问)。
- IT部门必须能够更新或更改所有目录条目上的密码条目
2. 添加组
- 以下LDIF显示了我们如何添加组。
version: 1
# create FIRST Level groups branch
dn: ou=groups,dc=example,dc=com
objectclass:organizationalunit
ou: groups
description: generic groups branch
# create the itpeople entry under groups
dn: cn=itpeople,ou=groups,dc=example,dc=com
objectclass: groupofnames
cn: itpeople
description: IT security group
member: cn=Sheri Smith,ou=people,dc=example,dc=com
# create the hrpeople entry under groups
dn: cn=hrpeople,ou=groups,dc=example,dc=com
objectclass: groupofnames
cn: hrpeople
description: Human Resources group
member: cn=Robert Smith,ou=people,dc=example,dc=com- 添加命令
ldapadd -x -D "cn=jimbob,dc=example,dc=com" -f /tmp/addgroups.ldif -w dirtysecret
3. ACL slapd.conf访问定义
- 下面的文本展示了完整的slapd.conf的配置
###### SAMPLE 1 - SIMPLE DIRECTORY ############
##
## NOTES: inetorgperson picks up attributes and objectclasses
## from all three schemas
##
## NB: RH Linux schemas in /etc/openldap
##
include /usr/local/etc/openldap/schema/core.schema
include /usr/local/etc/openldap/schema/cosine.schema
include /usr/local/etc/openldap/schema/inetorgperson.schema
#
#
## NO SECURITY - no access clause
## defaults to anonymous access for read
## only rootdn can write
#
## NO REFERRALS
#
## DON'T bother with ARGS file unless you feel strongly
## slapd scripts stop scripts need this to work
pidfile /var/run/openldap/slapd.pid
#
## enable a lot of logging - we might need it
## but generates huge logs
loglevel -1
#
## MODULELOAD definitions
## not required (comment out) before version 2.3
#moduleload back_bdb.la
#
## NO TLS-enabled connections
#
## backend definition not required
#
########################################################################
## bdb database definitions
##
## replace example and com below with a suitable domain
##
## If you don't have a domain you can leave it since example.com
## is reserved for experimentation or change them to my and inc
##
########################################################################
#
database bdb
suffix "dc=example, dc=com"
#ACL1
access to attrs=userpassword
by self write
by anonymous auth
by group.exact="cn=itpeople,ou=groups,dc=example,dc=com"
write
by * none
#ACL2
access to attrs=carlicense,homepostaladdress,homephone
by self write
by group.exact="cn=hrpeople,ou=groups,dc=example,dc=com"
write
by * none
#ACL3
access to *
by self write
by group.exact="cn=hrpeople,ou=groups,dc=example,dc=com"
write
by users read
by * none
#
## root or superuser
rootdn "cn=jimbob, dc=example, dc=com"
rootpw dirtysecret
## The database directory MUST exist prior to running slapd AND
## change path as necessary
directory /var/lib/ldap
#
## Indices to maintain for this directory
## unique id so equality match only
index uid eq
## allows general searching on commonname, givenname and email
index cn,gn,mail eq,sub
## allows multiple variants on surname searching
index sn eq,sub
## sub above includes subintial,subany,subfinal
## optimise department searches
index ou eq
## if searches will include objectClass uncomment following
## index objectClass eq
## shows use of default index parameter
#index default eq,sub
## indices missing - uses default eq,sub
index telephonenumber eq
#
## other database parameters
## read more in slapd.conf reference section
cachesize 10000
#checkpoint 128 15- 修改完服务后我们需要重启slapd服务
systemctl restart slapd
4. 测试ACL
- 配置LDAP浏览器绑定或验证,使用dn: cn=Robert Smith, ou=people, dc=example, dc=com ,密码 : rJsmitH(区分大小写),因为这个条目有hrpeople特权,并能够修改所有条目,包括carlicense, homepostaladdress 和 homephone,但不能修改userpassword(除了他自己的)
- 配置LDAP浏览器绑定或验证,使用 dn: cn=Sheri Smith, ou=people, dc=example, dc=com ,密码 : sSmitH(区分大小写),因为这个条目有itpeople特权,并能够将修改所有条目的userpassword属性,但看不到 carlicense, homepostaladdress and homephone ,除了她自己的外.
- 配置LDAP浏览器绑定或验证,使用 dn: cn=John Smith,ou=people,dc=example,dc=com ,密码:jSmitH ,由于这个条目没有特权,所以除了他自己的条目(他也可以修改自己的条目),其他任何条目都不能看到
- 为匿名访问配置LDAP浏览器,并确认访问被拒绝。
- 最后验证为我们的rootdn或超级用户(在slapd.conf中定义为 cn=jimbob,dc=example,dc=com, password dirtysecret),并确认这将覆盖我们的所有特权,并且可以查看和修改所有内容。
3. 扩展的层次结构
1. 扩展实施
- 当我们细分需求时,我们需要实现以下内容:
1. 将新的销售人员组添加到现有的组分支。
2. 在我们的DIT中添加一个新的设备分支。这将使用设备对象。
3.将新客户分支添加到我们的DIT。这将使用标准的inetorgperson对象类。
4. 在每个人的条目下添加一个新的地址薄分支。
2. 扩展LDIF
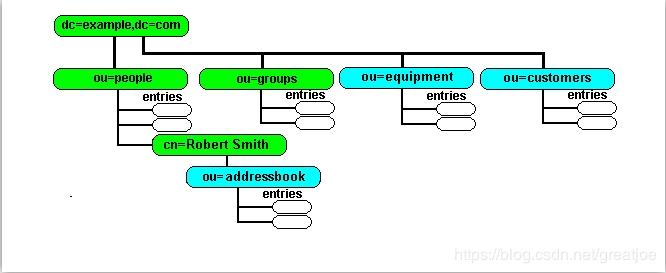
# create FIRST level customers branch
dn: ou=customers,dc=example,dc=com
objectclass: organizationalunit
ou: customers
description: customer address book branch
# create FIRST level equipment branch
dn: ou=equipment,dc=example,dc=com
objectclass: organizationalunit
ou: equipment
description: IT assets branch
# create an entry under equipment entry under groups
dn: cn=LP1,ou=equipment,dc=example,dc=com
objectclass: device
cn: LP1
description: Some brand of printer
serialnumber: 1-77-23-15
l: Room 17
owner: cn=John Smith,ou=people,dc=example,dc=com
ou: printers
# create the salespeople entry under groups
dn: cn=salespeople,ou=groups,dc=example,dc=com
objectclass: groupofnames
cn: salespeople
description: Sales group
member: cn=John Smith,ou=people,dc=example,dc=com
# create the addressbook entry for each person
dn: ou=addressbook,cn=John Smith,ou=people,dc=example,dc=com
objectclass: organizationalunit
ou: addressbook
description: Personal Address Book
dn: ou=addressbook,cn=Sheri Smith,ou=people,dc=example,dc=com
objectclass: organizationalunit
ou: addressbook
description: Personal Address Book
dn: ou=addressbook,cn=Robert Smith,ou=people,dc=example,dc=com
objectclass: organizationalunit
ou: addressbook
description: Personal Address Book- 执行命令添加ldif文件.
ldapadd -x -D "cn=jimbob,dc=example,dc=com" -f /tmp/enhance.ldif -w dirtysecre3. ACL - slapd.conf的配置
ACL4
# allows creation of entries in own addressbook; no-one else can
# access it, needs write access to the ENTRY attribute (ACL5 or ACL6A)
# and the entries CHILDREN (ACL4)
access to dn.regex="ou=addressbook,cn=([^,]+),ou=people,dc=example,dc=com$"
attrs=children
by dn.exact,expand="cn=$1,ou=people,dc=example,dc=com" write
by users none
# ACL5 - only required prior to 2.2
# allow creation of entries in own addressbook; no-one else can
# access it, needs write access to the ENTRY attribute (ACL5 or ACL6A)
# and the entries CHILDREN (ACL4)
#access to dn.regex="ou=addressbook,cn=([^,]+),ou=people,dc=example,dc=com$"
# attrs=entry
# by dn.exact,expand="cn=$1,ou=people,dc=example,dc=com" write
# by users none
# ACL6 - only required prior to 2.2
# allow creation of entries in own addressbook; no-one else can
# access it
#access to dn.regex="ou=addressbook,cn=([^,]+),ou=people,dc=example,dc=com$"
# filter=(objectclass=inetorgperson)
# by dn.exact,expand="cn=$1,ou=people,dc=example,dc=com" write
# by users none
# ACL6A - 2.2+ replace both ACL5 and ACL6 with this ACL
access to dn.regex="ou=addressbook,cn=([^,]+),ou=people,dc=example,dc=com$"
attrs=entry,@inetorgperson
by dn.exact,expand="cn=$1,ou=people,dc=example,dc=com" write
by users none
# ACL7
# allows sales to create entries in customers
# authenticated user can only read
access to dn.one="ou=customers,dc=example,dc=com"
attrs=children
by group.exact="cn=salespeople,ou=groups,dc=example,dc=com" write
by users read
# ACL8
access to attrs=carlicense,homepostaladdress,homephone
by self write
by group.exact="cn=hrpeople,ou=groups,dc=example,dc=com" write
by * none
# ACL8A - control access to equipment
access to dn.one="ou=equipment,dc=example,dc=com"
by group.exact="cn=itpeople,ou=groups,dc=example,dc=com" write
by users read
by * none
# ACL9
access to *
by self write
by group.exact="cn=hrpeople,ou=groups,dc=example,dc=com" write
by users read
by * none- 重启服务
systemctl restart slapd.service
4. 测试ACL
-
dc=com ,密码: rJsmitH.也因为这个项目有hrpeople权限,能够看到并修改carlicense,homepostaladdress和homephone,并且可以读取客户和设备条目但不能写入它们。Robert Smith也可以查看并添加他自己的地址簿条目.
-
配置LDAP浏览器绑定DN验证: cn=Sheri Smith, ou=people, dc=example, dc=com ,密码: sSmitH ,也因为这个项目有itpeople权限将看到并能够修改所有条目的userpassword属性.但除了她自己的条目外,无法查看carlicense,homepostaladdress和homephone,此条目可以读取客户条目,但不能写入它们,但可以读取和写入设备条目。Sheri Smith还可以查看并添加自己的地址簿条目,并可以查看地址簿每个人(但不是条目)。她还可以删除每个条目的地址簿
-
配置LDAP浏览器绑定DN验证:cn=John Smith, ou=people, dc=example, dc=com ,密码: jSmitH.因为该条目没有特权,所以不能看到carlicense,homepostaladdress,homephone和userpassword这些属性。此条目因为它是salespeople组的成员可以读取和写入customers条目,但只能读取设备条目。
4. 创建新的对象以及属性结构
1. 要求
- 一个dohicky属性。此属性是布尔值。它只能由所有者和hrpeople组的任何成员查看和更新。
- 一个ageAtBirth属性。它只能由所有者和hrpeople组的任何成员查看和更新。
- gobbledegook。此属性是字符串值,对所有经过身份验证的用户公开可见。它只能由所有者和hrpeople组的任何成员更新.它将允许 <= or >= search filters.
- 作为我们转向单点登录(SSO)的一部分,我们将为每个用户添加标准的posixAccount对象类。该记录仅对itpeople组可见。
2. 实施
cat > /usr/local/etc/openldap/schema/ourco.schema <
3. 修改slapd.conf文件
- 添加以下语句到slapd.conf文件中.
include /usr/local/etc/openldap/schema/ourco.schema- 重新启动服务
systemctl restart slapd
4. 添加LDIF
cat > /tmp/modify.ldif <
- 执行修改语句
ldapmodify -x -D "cn=jimbob,dc=example,dc = com" -f /tmp/modify.ldif -w dirtysecret你可以发现已经添加成功。新的属性已经建好.
该文章大部分翻译于:
http://www.zytrax.com/books/ldap/ch5/index.html#step1