Keycloak 初步 学习了解
docker 部署 keycloak
//下载 keycloak
docker pull jboss/keycloak
需要一个Keycloak实例,启动Jboss提供的Docker容器:
docker run -d \
--name springboot-security-keycloak-integration \
-e KEYCLOAK_USER=admin \
-e KEYCLOAK_PASSWORD=admin \
-p 9001:8080 \
jboss/keycloak
[root@localhost ~]# docker ps -a
CONTAINER ID IMAGE COMMAND CREATED STATUS PORTS NAMES
bacd6972eca7 jboss/keycloak "/opt/jboss/tools/do?? 35 seconds ago Up 33 seconds 0.0.0.0:9001->8080/tcp springboot-security-keycloak-integration
登录到容器并导航到bin文件夹
docker exec -it springboot-security-keycloak-integration /bin/bash
cd keycloak/bin/
通过 admin 登录
[jboss@bacd6972eca7 bin]$ ./kcadm.sh config credentials --server http://localhost:8080/auth --realm master --user admin --password admin
Logging into http://localhost:8080/auth as user admin of realm master
1.创建一个realm:
[jboss@bacd6972eca7 bin]$ ./kcadm.sh create realms -s realm=springboot-security-keycloak-integration -s enabled=true
Created new realm with id 'springboot-security-keycloak-integration'
2.创建2个客户端
curl客户端 为后续 获取 token 值 :
[jboss@bacd6972eca7 bin]$ ./kcadm.sh create clients -r springboot-security-keycloak-integration -s clientId=curl -s enabled=true -s publicClient=true -s baseUrl=http://localhost:8080 -s adminUrl=http://localhost:8080 -s directAccessGrantsEnabled=true
Created new client with id '05cab00c-36ba-4ab4-bcf5-4e1a3a223794'
publicClient=true和 directAccessGrantsEnabled=true
publicClient 使这个客户端公开,这意味着我们的 curl 客户端可以在不提供任何秘密的情况下启动登录。
directAccessGrantsEnabled 使我们能够使用用户名和密码直接登录
springboot-security-keycloak-integration-client 客户端 拦截 REST服务:
[jboss@bacd6972eca7 bin]$ ./kcadm.sh create clients -r springboot-security-keycloak-integration -s clientId=springboot-security-keycloak-integration-client -s enabled=true -s baseUrl=http://localhost:8080 -s bearerOnly=true
Created new client with id '8f78f0ff-86a0-4c3d-be85-e692ae2b9c2b'
bearerOnly=true。这告诉Keycloak客户端永远不会启动登录过程,
但是当它收到Bearer令牌时,它将检查所述令牌的有效性。
3.为 应用 创建角色 两个角色
admin 角色
[jboss@bacd6972eca7 bin]$ ./kcadm.sh create clients/8f78f0ff-86a0-4c3d-be85-e692ae2b9c2b/roles -r springboot-security-keycloak-integration -s name=admin -s 'description=Admin role'
Created new role with id 'admin'
user 角色
[jboss@bacd6972eca7 bin]$ ./kcadm.sh create clients/8f78f0ff-86a0-4c3d-be85-e692ae2b9c2b/roles -r springboot-security-keycloak-integration -s name=user -s 'description=User role'
Created new role with id 'user'
获取客户端的配置,以便稍后提供给我们的应用程序:
[jboss@bacd6972eca7 bin]$ ./kcadm.sh get clients/8f78f0ff-86a0-4c3d-be85-e692ae2b9c2b/installation/providers/keycloak-oidc-keycloak-json -r springboot-security-keycloak-integration
{
"realm" : "springboot-security-keycloak-integration",
"bearer-only" : true,
"auth-server-url" : "http://localhost:8080/auth",
"ssl-required" : "external",
"resource" : "springboot-security-keycloak-integration-client",
"verify-token-audience" : true,
"use-resource-role-mappings" : true,
"confidential-port" : 0
}
4.为 角色 创建用户
创建2个具有2个不同角色的用户,以便我们验证授权是否有效
创建 admin 用户:
[jboss@bacd6972eca7 bin]$ ./kcadm.sh create users -r springboot-security-keycloak-integration -s username=admin -s enabled=true
Created new user with id '07b8a748-d192-4503-9b60-8d42a1affd31'
设置 admin 密码: 密码为 admin
[jboss@bacd6972eca7 bin]$ ./kcadm.sh update users/07b8a748-d192-4503-9b60-8d42a1affd31/reset-password -r springboot-security-keycloak-integration -s type=password -s value=admin -s temporary=false -n
追加到 admin 角色中 (注意:从不在生产中使用此方法,它仅用于演示目的!)
[jboss@bacd6972eca7 bin]$ ./kcadm.sh add-roles -r springboot-security-keycloak-integration --uusername=admin --cclientid springboot-security-keycloak-integration-client --rolename admin
创建 user 用户:
[jboss@bacd6972eca7 bin]$ ./kcadm.sh create users -r springboot-security-keycloak-integration -s username=user -s enabled=true
Created new user with id 'cd9c40c3-c179-41cb-b367-34508ddd1551'
设置 user 密码: 密码为 user
[jboss@bacd6972eca7 bin]$ ./kcadm.sh update users/cd9c40c3-c179-41cb-b367-34508ddd1551/reset-password -r springboot-security-keycloak-integration -s type=password -s value=user -s temporary=false -n
追加到 user 角色中 (注意:从不在生产中使用此方法,它仅用于演示目的!)
[jboss@bacd6972eca7 bin]$ ./kcadm.sh add-roles -r springboot-security-keycloak-integration --uusername=user --cclientid springboot-security-keycloak-integration-client --rolename user
5.使用curl我们创建的客户端进行身份验证,以获取访问令牌:
获取的 admin 的token
获取的user 的 token
写一个简单的 springboot 测试项目
@RestController
public class TestController {
@GetMapping(value = "/test")
public String test() {
return "test";
}
@GetMapping(value = "/admin")
@Secured("ROLE_ADMIN")
public String admin() {
return "Admin";
}
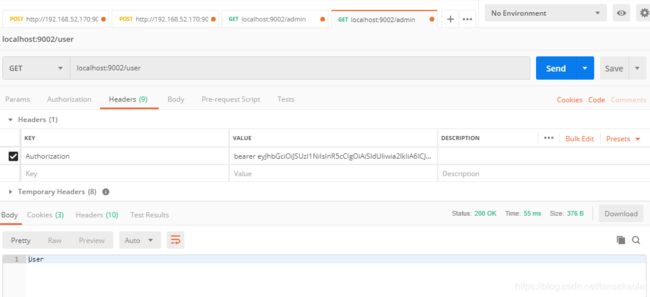
@GetMapping("/user")
@Secured("ROLE_USER")
public String user() {
return "User";
}
}测试结果:
感谢 : https://blog.csdn.net/weixin_34255055/article/details/88278682