kubernetes-----安全机制
一.kubernetes的安全框架
- 管理kubernetes的有kubectl、api、UI界面
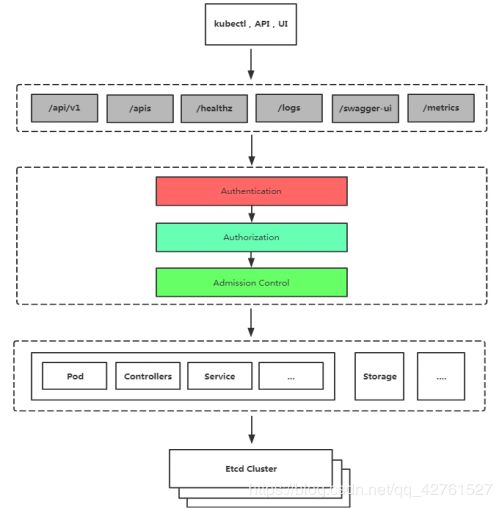
- 如下是k8s的安全框架图
安全认证流程:kubectl请求api资源,然后通过三层安全机制。
第一层是认证(Authentication),验证身份、用户名和密码或者token;
第二层是授权(Authorization)角色绑定(RBAC),以获得权限;
第三层是准入控制(Admission Control,资源使用限定)。
请求只有通过这三层安全机制,才会被k8s响应请求,创建资源。
-
k8s的安全控制框架主要由以上3个阶段进行控制,每一个阶段都支持插件方式,通过APIServer配置来启用插件方式,通过APiserver配置来启用插件。
-
普通用户想要安全的访问集群APIServer,往往需要证书、token或者是用户名+密码
-
pod访问需要ServiceAccount
[root@master ~]# kubectl get serviceaccount
NAME SECRETS AGE
default 1 26d
[root@master ~]#
-
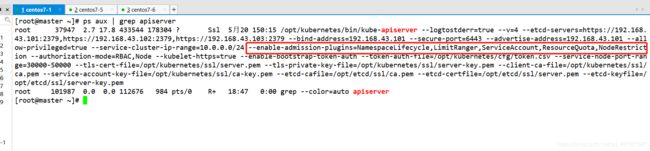
apiserver内部使用8080端口,默认8080端口监听本地,通过master以及其他组件连接使用
[root@master ~]# netstat -natp | grep LISTEN | grep 8080
tcp 0 0 127.0.0.1:8080 0.0.0.0:* LISTEN 37947/kube-apiserve
-
apiserver外部使用6443端口
[root@master ~]# netstat -natp | grep LISTEN | grep 6443
tcp 0 0 192.168.43.101:6443 0.0.0.0:* LISTEN 37947/kube-apiserve
[root@master ~]#
二.Authentication,认证
- 认证有三种客户端身份认证
HTTPS证书认证,基于CA证书签名的数字证书认证
- CA认证如下
cat > server-csr.json <HTTP Token认证,通过一个Token来识别用户(生产环境中使用广泛)
- httpd的令牌认证如下
[root@master ~]# cat /opt/kubernetes/cfg/token.csv
978741334e39eb21d1c13050d6e8bb79,kubelet-bootstrap,10001,"system:kubelet-bootstrap"
[root@master ~]#
HTTP Base认证,用户名+密码的方式认证
三.Authorization,授权
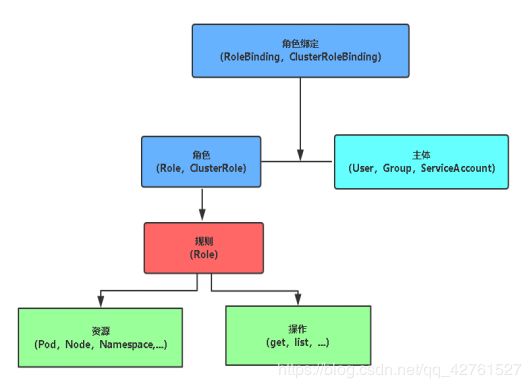
- RBAC(Role-Based Access Control,基于角色的访问控制),负责完成授权(Authorization)工作。
- 以下是授权模块的相关概念
user:身份验证期间提供的用户字符串;
group:已验证用户所属的组名列表;
extra:任意字符串键到字符串值得映射,由身份验证层提供;
API:指示请求是否针对API资源;
request path:到其他非资源端点得路径;
api request verb:api动作(get、list、create、update、patch、watch、proxy、redirect、delete和deletecollection)等,用于
资源请求。
http request verb:http动作(get、post和delete用于非资源请求);
resource:正在访问得资源的ID或者名称(仅仅用于资源请求),对于使用get、update、patch和delete谓词的资源请求,必须提供资源名称;
subresource:正在访问的资源(仅仅用于资源请求);
namespace:正在访问的子资源(仅用于资源请求);
api group:被访问的api组(仅用于资源请求),一个空字符串指定核心api组
- 由于RBAC是基于角色进行控制的,所以首先需要创建角色、然后创建绑定的资源、最后将角色与目标甚至api和请求等绑定。绑定api模式适用于二次开发。
四.admission contorl,准入控制
- 准入控制实际上是一个准入控制器插件列表,发送到API server的请i去都需要经过这个列表中的每个准入控制器插件的检查,检查不通过,
NamespaceLifecycle:命令空间回收
LimitRanger:配额管理
ServiceAccount:每个pod中导入方便访问apiserver
ResourceQuota:基于命名空间的高级配额管理
NodeRestriction:node加入到k8s群集中以最小的权限运行
- 以下是官方推荐的插件(用于1.11版本以上)
--enable-admission-plugins= \ NamespaceLifecycle,LimitRanger,ServiceAccount,DefaultStorageClass,DefaultTolerationSeconds, ResourceQuota五.基于授权机制创建新的用户
-
使用RBAC(基于角色的访问控制)授权,允许通过kubernetes API动态配置策略
主体:user(用户)、Group(用户组)、ServiceAccount(服务账号)
角色:Role(授权特定命名空间的访问权限)、ClusterRole(授权所有命名空间访问权限)
角色绑定:RoleBinding(将角色绑定到主体,即subject)、ClusterRoleBinding(将集群角色绑定到主体)
- 创建命名空间
[root@master ~]# kubectl create ns kgc
namespace/kgc created
[root@master ~]# kubectl get ns
NAME STATUS AGE
default Active 27d
kgc Active 2s
kube-public Active 27d
kube-system Active 27d
[root@master ~]#
- 创建nginx的pod资源
[root@master demo]# kubectl run nginx --image=nginx -n kgc
kubectl run --generator=deployment/apps.v1beta1 is DEPRECATED and will be removed in a future version. Use kubectl create instead.
deployment.apps/nginx created
[root@master demo]# kubectl get pods -n kgc
NAME READY STATUS RESTARTS AGE
nginx-dbddb74b8-lsz2g 1/1 Running 0 25s
- 扩容成三个副本
[root@master demo]# kubectl scale deploy/nginx --replicas=3 -n kgc
deployment.extensions/nginx scaled
[root@master demo]# kubectl get pods -n kgc
NAME READY STATUS RESTARTS AGE
nginx-dbddb74b8-g2qd5 1/1 Running 0 25m
nginx-dbddb74b8-lsz2g 1/1 Running 0 26m
nginx-dbddb74b8-v6mbd 1/1 Running 0 25m
[root@master demo]#
- 创建角色
[root@master demo]# cat rbac-role.yaml
apiVersion: rbac.authorization.k8s.io/v1
kind: Role ##指定控制器为Role
metadata:
namespace: kgc
name: pod-reader
rules: ##定义规则
- apiGroups: [""] # "" indicates the core API group
resources: ["pods"]
verbs: ["get", "watch", "list"] ##定义动作
[root@master demo]# kubectl apply -f rbac-role.yaml
role.rbac.authorization.k8s.io/pod-reader created
[root@master demo]# kubectl get role -n kgc
NAME AGE
pod-reader 14s
[root@master demo]#
- 创建角色绑定
[root@master demo]# cat rbac-rolebinding.yaml
apiVersion: rbac.authorization.k8s.io/v1
kind: RoleBinding
metadata:
name: read-pods
namespace: kgc
subjects: ##指定主体
- kind: User ##指定主体类型,为用户
name: zhangsan
apiGroup: rbac.authorization.k8s.io ##给定的权限
roleRef:
kind: Role ##指定张三用户对pod-reader的读的权限
name: pod-reader
apiGroup: rbac.authorization.k8s.io
[root@master demo]# kubectl create -f rbac-rolebinding.yaml
rolebinding.rbac.authorization.k8s.io/read-pods created
[root@master demo]# kubectl get role,rolebinding -n kgc
NAME AGE
role.rbac.authorization.k8s.io/pod-reader 5m27s
NAME AGE
rolebinding.rbac.authorization.k8s.io/read-pods 58s
[root@master demo]# - 设置张三用户仅可以访问pod资源
##创建zhangsan用户的目录
[root@master demo]# mkdir zhangsan
[root@master demo]# cd zhangsan/
##复制证书到目录下
[root@master zhangsan]# cp /root/k8s/k8s-cert/ca* ./
[root@master zhangsan]# ls
ca-config.json ca.csr ca-csr.json ca-key.pem ca.pem
##安装格式化工具,基本上从Windows拖到Linux上的文件都要用一下dos2unix
[root@master zhangsan]# yum install dos2unix -y &> /dev/null
##从本机上传rbac-user.sh和rbac.yaml文件到服务器
[root@master zhangsan]# ls
ca-config.json ca.csr ca-csr.json ca-key.pem ca.pem rbac-user.sh rbac.yaml
[root@master zhangsan]# cat rbac-user.sh
kubectl config set-cluster kubernetes \
--certificate-authority=ca.pem \
--embed-certs=true \
--server=https://192.168.43.100:6443 \
--kubeconfig=zhangsan-kubeconfig
[root@master zhangsan]# cat rbac-user.sh.0
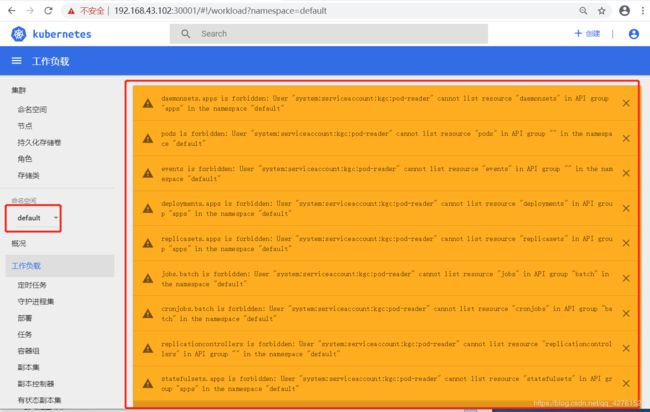
cat > zhangsan-csr.json <- 对于UI界面的访问控制,创建对于kgc的命名空间里的资源才能看见的令牌
[root@master zhangsan]# cat sa.yaml
apiVersion: v1
kind: ServiceAccount
metadata:
name: pod-reader
namespace: kgc
---
kind: RoleBinding
apiVersion: rbac.authorization.k8s.io/v1
metadata:
name: sa-read-pods
namespace: kgc
subjects:
- kind: ServiceAccount
name: pod-reader
roleRef:
kind: Role
name: pod-reader
apiGroup: rbac.authorization.k8s.io
[root@master zhangsan]# kubectl apply -f sa.yaml
serviceaccount/pod-reader created
rolebinding.rbac.authorization.k8s.io/sa-read-pods created
[root@master zhangsan]# kubectl get sa -n kgc
NAME SECRETS AGE
default 1 133m
pod-reader 1 13s
[root@master zhangsan]# kubectl describe secret pod-reader -n kgc
Name: pod-reader-token-jdbnp
Namespace: kgc
Labels:
Annotations: kubernetes.io/service-account.name: pod-reader
kubernetes.io/service-account.uid: 7518bf18-9dcf-11ea-bb1a-000c29ce5f24
Type: kubernetes.io/service-account-token
Data
====
ca.crt: 1359 bytes
namespace: 3 bytes
token: eyJhbGciOiJSUzI1NiIsImtpZCI6IiJ9.eyJpc3MiOiJrdWJlcm5ldGVzL3NlcnZpY2VhY2NvdW50Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9uYW1lc3BhY2UiOiJrZ2MiLCJrdWJlcm5ldGVzLmlvL3NlcnZpY2VhY2NvdW50L3NlY3JldC5uYW1lIjoicG9kLXJlYWRlci10b2tlbi1qZGJucCIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VydmljZS1hY2NvdW50Lm5hbWUiOiJwb2QtcmVhZGVyIiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9zZXJ2aWNlLWFjY291bnQudWlkIjoiNzUxOGJmMTgtOWRjZi0xMWVhLWJiMWEtMDAwYzI5Y2U1ZjI0Iiwic3ViIjoic3lzdGVtOnNlcnZpY2VhY2NvdW50OmtnYzpwb2QtcmVhZGVyIn0.wdidxNwgYjSzAKMJEZKzebnQ-ZwRRhs80DT-DpKo49TTmiyFDZfOFxixKOSMjDDEXd0Fl3x2XDU0DMvmDUcRsdgcSg6CA_Bl-cDtDDx9sptF8r7s5deyeHfxgjb66PTvIapeyvLI-hGurmPnwLHc9A2omfG2B8MQTHAR0eR2Ouhlv1nGYRzdYoCVo2xmw5jR_URT_dx5Zz01ncdCUzmNUdqTpjDel5s76gWVXgiBYEuOgVoxHGMz-dIlZ2i0BHJSFAlttI3rH4EBGZl79pwVs6MSn7ag_KndcjcUzlkWkCb6V1imD1inR4L2fMwkdSvq9Cm40Ez1Q5ooHrODseLshA
[root@master zhangsan]#