流量分析练习-2014-11-16-traffic-analysis-exercise.pcap
pcap包来自https://www.malware-traffic-analysis.net/2014/11/16/index.html
问题与回答
LEVEL 1 QUESTIONS:
1) What is the IP address of the Windows VM that gets infected?
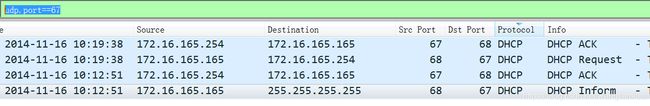
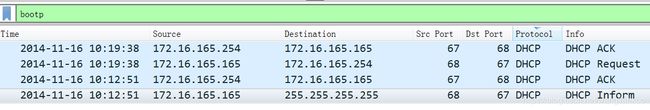
通过查询语句“bootp”or“udp.port==67”查询到了DHCP通信流量。被感染Windows VM IP地址为172.16.165.165
DHCP知识点
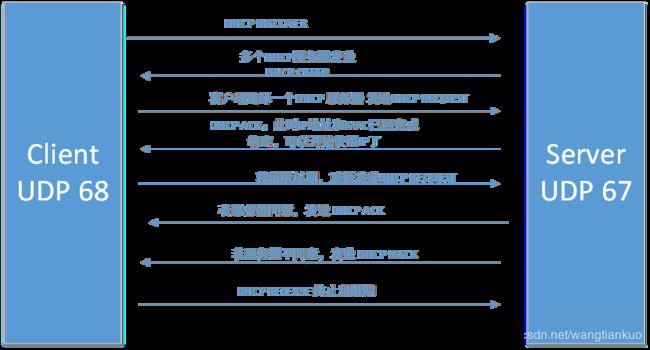
DHCP报文是UDP用户数据包的数据。
DHCP客户使用的UDP端口是68,服务器使用的UDP端口是67
根据Info or port or (source and destination)都可以判断出来本机IP。
2) What is the host name of the Windows VM that gets infected?
3) What is the MAC address of the infected VM?
4) What is the IP address of the compromised web site?
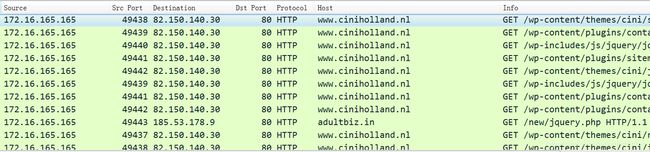
使用http.request过滤流量,得到5个站点,除必应外还剩www*ciniholland.nl、adultbiz*in、24corp-shop*com、stand.trustandprobaterealty*com。
根据Info信息,判断被攻陷的网站IP为82.150.140.30
5) What is the domain name of the compromised web site?
www*ciniholland.nl
6) What is the IP address and domain name that delivered the exploit kit and malware?
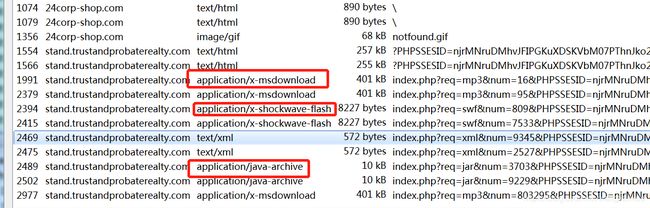
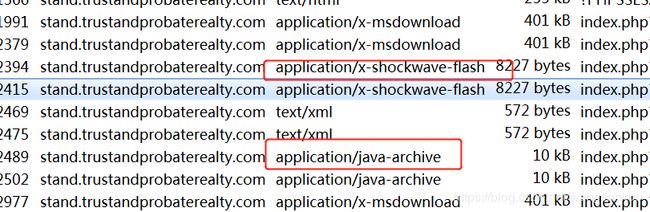
File->导出对象->HTTP
分别代表dll文件,swf文件,jar文件,因此为stand.trustandprobaterealty*com 37.200.69.143
LEVEL 2 QUESTIONS:
1) What is the redirect URL that points to the exploit kit (EK) landing page?
保存成txt文件后,查看内容,发现
因此指向EK的导向(redirect,这里没有翻译成重定向,因为只是网页内容中包含指向网址而已,并未重定向)URL为http: 24corp-shop*com/
2) Besided the landing page (which contains the CVE-2013-2551 IE exploit), what other exploit(s) sent by the EK?
3) How many times was the payload delivered?
3次
4) Submit the pcap to VirusTotal and find out what snort alerts triggered. What are the EK names are shown in the Suricata alerts?
在https*//www.virustotal.com/en提交文件,可以查看到Suricata alerts信息。
ET CURRENT_EVENTS RIG EK Landing URI Struct (A Network Trojan was Detected) [2019072]
ET CURRENT_EVENTS Goon/Infinity URI Struct EK Landing May 05 2014 (A Network Trojan was Detected) [2018441]
ET CURRENT_EVENTS GoonEK encrypted binary (3) (A Network Trojan was Detected) [2018297]
LEVEL 3 QUESTIONS:
1) Checking my website, what have I (and others) been calling this exploit kit?
RIG
2) What file or page from the compromised website has the malicious script with the URL for the redirect?
http*//www.ciniholland.nl/的请求返回的数据中显示包含http://24corp-shop*com/
扩展知识
Request头
Accept-Encoding:gzip、compress、deflate、br、identity、*。
代表不同的加密算法。详见https*/developer.mozilla.org/en-US/docs/Web/HTTP/Headers/Accept-Encoding
Referer:URL
Referer请求头包含前一个web页面的地址,从该页面可以链接到当前请求的页面。
Response头
| Set-Cookie: |
用于将cookie从服务器发送到用户代理 |
| Expires: |
Expires头包含过期响应的日期/时间。 |
| Last-Modified |
资源最后修改的日期和时间 |
| Transfer-Encoding: chunked/ compress/ deflate/ gzip/ identity |
Transfer-Encoding标头指定用于将实体安全地传输给用户的编码形式。 |
content-type:
application: 任何类型的二进制数据,尤其是将以某种方式执行或解释的数据。
MIME类型:
http*/www.w3school.com.cn/media/media_mimeref.asp
| 类型/子类型 |
扩展名 |
| application/x-msdownload |
dll |
| application/x-shockwave-flash |
swf |
| application/java-archive |
.jar |