DVWA靶场-JavaScript Attacks JS 攻击
往期博文:
DVWA靶场-Brute Force Source 暴力破解
DVWA靶场-Command Injection 命令注入
DVWA靶场-CSRF 跨站请求伪造
DVWA靶场-File Inclusion 文件包含
DVWA靶场-File Upload 文件上传
DVWA靶场-SQL Injection SQL注入
DVWA靶场-Weak Session IDs 脆弱的Session
DVWA靶场-XSS(DOM型、反射型、存储型)
DVWA靶场-Content Security Policy (CSP) Bypass
靶场环境搭建
https://github.com/ethicalhack3r/DVWA
[网络安全学习篇附]:DVWA 靶场搭建
目录
JavaScript Attacks
Low JavaScript
核心代码
Medium JavaScript
核心代码
High JavaScript
核心代码
Impossible JavaScript
JavaScript Attacks
Low JavaScript
核心代码
/*
MD5 code from here
https://github.com/blueimp/JavaScript-MD5
*/
!function(n){"use strict";function t(n,t){var r=(65535&n)+(65535&t);return(n>>16)+(t>>16)+(r>>16)<<16|65535&r}function r(n,t){return n<>>32-t}function e(n,e,o,u,c,f){return t(r(t(t(e,n),t(u,f)),c),o)}function o(n,t,r,o,u,c,f){return e(t&r|~t&o,n,t,u,c,f)}function u(n,t,r,o,u,c,f){return e(t&o|r&~o,n,t,u,c,f)}function c(n,t,r,o,u,c,f){return e(t^r^o,n,t,u,c,f)}function f(n,t,r,o,u,c,f){return e(r^(t|~o),n,t,u,c,f)}function i(n,r){n[r>>5]|=128<>>9<<4)]=r;var e,i,a,d,h,l=1732584193,g=-271733879,v=-1732584194,m=271733878;for(e=0;e>5]>>>t%32&255);return r}function d(n){var t,r=[];for(r[(n.length>>2)-1]=void 0,t=0;t>5]|=(255&n.charCodeAt(t/8))<16&&(o=i(o,8*n.length)),r=0;r<16;r+=1)u[r]=909522486^o[r],c[r]=1549556828^o[r];return e=i(u.concat(d(t)),512+8*t.length),a(i(c.concat(e),640))}function g(n){var t,r,e="";for(r=0;r>>4&15)+"0123456789abcdef".charAt(15&t);return e}function v(n){return unescape(encodeURIComponent(n))}function m(n){return h(v(n))}function p(n){return g(m(n))}function s(n,t){return l(v(n),v(t))}function C(n,t){return g(s(n,t))}function A(n,t,r){return t?r?s(t,n):C(t,n):r?m(n):p(n)}"function"==typeof define&&define.amd?define(function(){return A}):"object"==typeof module&&module.exports?module.exports=A:n.md5=A}(this);
function rot13(inp) {
return inp.replace(/[a-zA-Z]/g,function(c){return String.fromCharCode((c<="Z"?90:122)>=(c=c.charCodeAt(0)+13)?c:c-26);});
}
function generate_token() {
var phrase = document.getElementById("phrase").value;
document.getElementById("token").value = md5(rot13(phrase));
}
generate_token();
EOF;
?> 再来看一下index.html
$message = "";
// Check whwat was sent in to see if it was what was expected
if ($_SERVER['REQUEST_METHOD'] == "POST") {
if (array_key_exists ("phrase", $_POST) && array_key_exists ("token", $_POST)) {
$phrase = $_POST['phrase'];
$token = $_POST['token'];
if ($phrase == "success") {
switch( $_COOKIE[ 'security' ] ) {
case 'low':
if ($token == md5(str_rot13("success"))) {
$message = "Well done!
";
} else {
$message = "Invalid token.
";
}
}
}
}
}这里通过Post 方式获取变量phrase 和token 的值,if(phrase == "success") 且token值正确的话,就输出well done!
直接输入success 发现无效
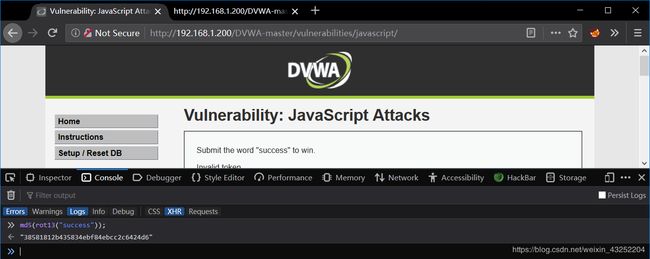
检查页面源代码,发现token的值由md5(rot13(phrase))决定的
通过console 控制台直接拿到token值
token:38581812b435834ebf84ebcc2c6424d6
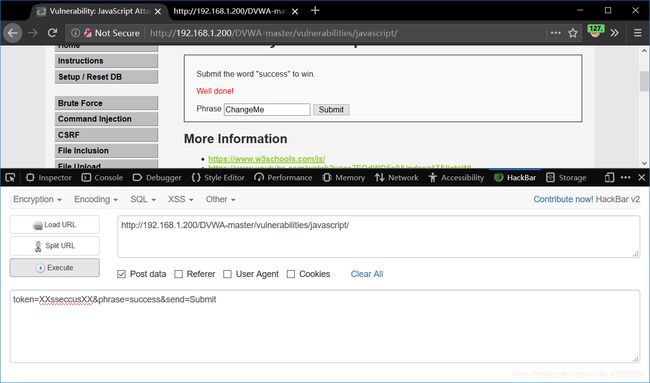
接下来直接post请求提交,即可成功
token=38581812b435834ebf84ebcc2c6424d6&phrase=success&send=Submit
Medium JavaScript
核心代码
';
?>我们继续跟进查看medium.js
function do_something(e) {
for (var t = "", n = e.length - 1; n >= 0; n--) t += e[n];
return t
}
setTimeout(function () {
do_elsesomething("XX")
}, 300);
function do_elsesomething(e) {
document.getElementById("token").value = do_something(e + document.getElementById("phrase").value + "XX")
}这里我们分析代码发现这段代码就是将phrase变量的值逆序,也就是sseccus;生成的token值=XXsseccusXX
这里我们直接提交
High JavaScript
核心代码
';
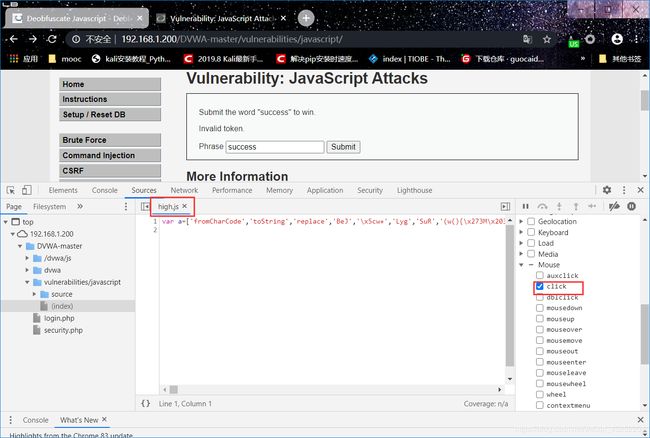
?>跟进查看high.js,这里的代码明显被加密混淆了,我们可以使用在线解码工具http://deobfuscatejavascript.com/#
核心代码
function do_something(e) {
for (var t = "", n = e.length - 1; n >= 0; n--) t += e[n];
return t
}
function token_part_3(t, y = "ZZ") {
document.getElementById("token").value = sha256(document.getElementById("token").value + y)
}
function token_part_2(e = "YY") {
document.getElementById("token").value = sha256(e + document.getElementById("token").value)
}
function token_part_1(a, b) {
document.getElementById("token").value = do_something(document.getElementById("phrase").value)
}
document.getElementById("phrase").value = "";
setTimeout(function() {
token_part_2("XX")
}, 300);
document.getElementById("send").addEventListener("click", token_part_3);
token_part_1("ABCD", 44);
代码的执行顺序是这样的
首先将phrase 的值清空
document.getElementById("phrase").value = "";
token_part_1("ABCD", 44);
调用函数
function token_part_1(a, b) {
document.getElementById("token").value = do_something(document.getElementById("phrase").value)
}
接着自动延时300 执行
setTimeout(function() {
token_part_2("XX")
}, 300);
调用函数
function token_part_2(e = "YY") {
document.getElementById("token").value = sha256(e + document.getElementById("token").value)
}
即生成的"XX"的sha256值
接着当我们点击提交的时候,就会触发 click 事件:
document.getElementById("send").addEventListener("click", token_part_3);
然后调用token_part_3()函数
function token_part_3(t, y = "ZZ") {
document.getElementById("token").value = sha256(document.getElementById("token").value + y)
}
问题就出在这里
document.getElementById("phrase").value = "";
我们输入的success并没有被函数读取到
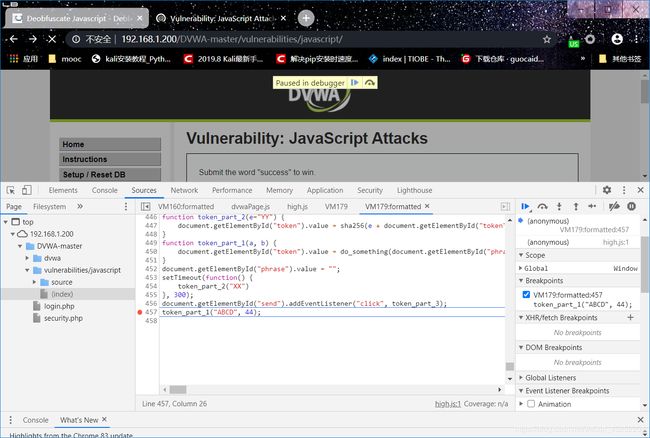
转到调试器
选择high.js 文件,设置在mouse下的click 事件断点
浏览器会帮我们自动解码,设置断点
现在已经停止在我们设置的断点处,同时取消mouse 中我们刚才设置的click
这个时候我们在控制台中输入
document.getElementById("phrase").value = "success";
放行,即可登录成功
如果第一次没有成功的话 ,缓存了之前操作,一般第二次就会成功了
Impossible JavaScript
You can never trust anything that comes from the user or prevent them from messing with it and so there is no impossible level.
这个级别有点幽默,防护的方法就是直接删掉了用户可以输入的地方,简直了。
https://www.sqlsec.com/2020/05/dvwa.html#toc-heading-31