nginx过appscan默认扫描和绿盟扫描
最近刚用上appscan,报了不少漏洞,在这里进行一一解决,同时记录一下自己的参考资料,以备后人。
使用环境,phpstudy8.1
1、 Content-Security-Policy(禁止外链资源)、X-Content-Type-Options(固定安全值)、X-XSS-Protection(固定安全值)这三个文件头缺失。
由于报js也是文件头缺失(adminlte),phpstudy的apache不知道为啥加不进去文件头,老报格式错误。所以索性直接改了nginx。
nginx.conf增加
server {
listen 1024;
server_name thinkphp.lo;
root D:/phpstudy_pro/WWW/xxxxxx/public;
index index.html index.htm index.php;
location ~ \.php(.*)$ {
fastcgi_pass 127.0.0.1:9000;
fastcgi_index index.php;
#下面两句是给fastcgi权限,可以支持 ?s=/module/controller/action的url访问模式
fastcgi_split_path_info ^((?U).+\.php)(/?.+)$;
fastcgi_param SCRIPT_FILENAME $document_root$fastcgi_script_name;
#下面两句才能真正支持 index.php/index/index/index的pathinfo模式
fastcgi_param PATH_INFO $fastcgi_path_info;
fastcgi_param PATH_TRANSLATED $document_root$fastcgi_path_info;
include fastcgi_params;
}
location / {
index index.html index.htm index.php;
#autoindex on;
if (!-e $request_filename) {
rewrite ^(.*)$ /index.php?s=/$1 last;
break;
}
}
add_header Content-Security-Policy "default-src 'self' 'unsafe-eval' 'unsafe-inline' fonts.gstatic.com data:;img-src 'self' 'unsafe-eval' 'unsafe-inline' data: blob: ;";
add_header X-Content-Type-Options: nosniff;
add_header X-XSS-Protection "1; mode=block";
#add_header Access-Control-Allow-Origin: http://www.one.site.com;
#add_header X-Frame-Options: deny;
#add_header Strict-Transport-Security: max-age=3600; includeSubDomains;
}
参考资料:
最全实例(推荐度高,apache【虽然我配置失败了】,nginx,tomcat都有)
https://www.cnblogs.com/weiwei-python/p/11233649.html
## CSP
add_header Content-Security-Policy: default-src 'self'; img-src 'self' https://i.imgur.com; object-src 'none'; script-src 'self'; style-src 'self'; frame-ancestors 'self'; base-uri 'self'; form-action 'self';
## 通用的安全响应报头
add_header X-XSS-Protection: 1; mode=block;
add_header Access-Control-Allow-Origin: http://www.one.site.com;
add_header X-Frame-Options: deny;
add_header X-Content-Type-Options: nosniff;
add_header Strict-Transport-Security: max-age=3600; includeSubDomains;
## 缓存策略
** 默认不使用缓存 **
add_header Cache-Control no-cache;
add_header Expires: 0;
** 设置静态资产缓存 1 天 **
location ~* \.(?:ico|css|js|gif|jpe?g|png|svg|woff|ttf|eot)$ {
try_files $uri @rewriteapp;
add_header Cache-Control "max-age=86400, public";
}
Content-Security-Policy(csp)参数表(推荐度高)
https://www.cnblogs.com/heyuqing/p/6215761.html

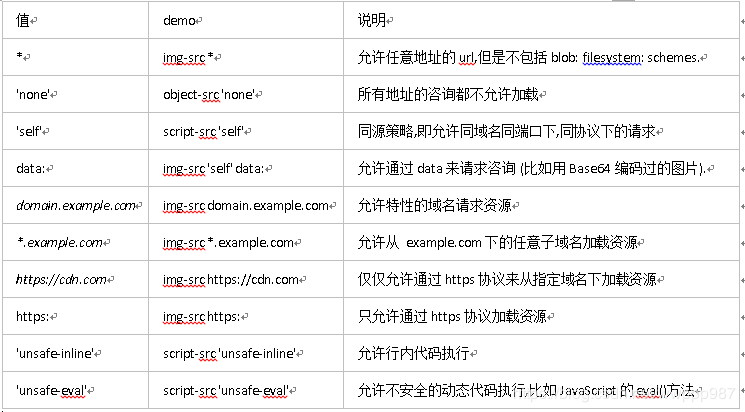
注意参数有没有单引号,这点很重要。
Content Security Policy 入门教程(主要讲参数意义和优先级的)
http://www.ruanyifeng.com/blog/2016/09/csp.html
AppScan安全扫描:常见header头安全问题处理(推荐度:中)
(从nginx、java后台、html前台三个地方去处理header缺失问题)
https://blog.csdn.net/niuch1029291561/article/details/86705141
排查过程(推荐度:低)
https://blog.csdn.net/tornadojava/article/details/55191981
apache .htaccess文件详解和配置技巧总结(排版垃圾,不过内容还不错,我喜欢,虽然没搞通,但是有用,所以记下)
https://www.cnblogs.com/wumingcong/p/5044713.html
IBM AppScan 安全扫描:Missing Content-Security-Policy ;X-Content-Type-Options ;X-XSS-Protection响应头(各种响应头和参数介绍,大神自留地,因为没有完整示例,所以小白勿入)
https://blog.csdn.net/u013310119/article/details/84861900
X-XSS-Protection头部深入理解(这个可能是我没看懂,除了必须用1 block之外。。。)
https://www.freebuf.com/articles/web/138769.html
2、Web 服务器访问控制文件不正确的许可权设置
AppScan 在测试请求中更改了哪些内容?
已将路径设置为“/.htaccess” (变体标识:176)
AppScan 为何报告该问题?
响应的内容类型(text/plain、application/octet-stream 或 application/x-trash)和 HTTP 状态(200 OK)表明可能检索 .htaccess、.htpasswd 或 .htgroup 文件内容。
解决方法:
由于采用了nginx,所以apache的配置文件.htaccess删掉。
3、检测到目标URL存在http host头攻击漏洞(中风险)
由于对java不熟悉,所以暂留此方案。
https://blog.csdn.net/weixin_43922510/article/details/99657007
我参考的解决方案(这个解决方案报错)
https://blog.csdn.net/baishuhui123/article/details/89216646
另,多域名访问解决方案
https://blog.csdn.net/woshizhangliang999/article/details/51701327/
(多域名参考方案语法解释)
http://www.04007.cn/article/541.html
最后的解决方案:(nginx)
在server下(listen、servername后面)插入
if ($http_Host != '10.XX.XX.XX:XXXX')
{
return 403;
}
另:最终记录一下nginx.cfg的全文:(ip、二级目录信息已经被屏蔽)
#user nobody;
worker_processes 4;
#error_log logs/error.log;
#error_log logs/error.log notice;
#error_log logs/error.log info;
#pid logs/nginx.pid;
events {
worker_connections 40960;
}
http {
include mime.types;
default_type application/octet-stream;
#log_format main '$remote_addr - $remote_user [$time_local] "$request" '
# '$status $body_bytes_sent "$http_referer" '
# '"$http_user_agent" "$http_x_forwarded_for"';
#access_log logs/access.log main;
sendfile on;
keepalive_timeout 65;
server {
# 注意:请改这里端口号、ip、访问目录、默认访问文件名--------------------------
listen 8081;
server_name 10.XX.XX.XX;
#这里改目录(二级目录访问)
root D:/phpstudy_pro/WWW/XXXXXXX/public;
index index.html index.htm index.php;
if ($http_Host != '10.XX.XX.XX:8081')
{
return 403;
}
# end注意:请改这里端口号、ip、访问目录、默认访问文件名--------------------------
location ~ \.php(.*)$ {
fastcgi_pass 127.0.0.1:9000;
fastcgi_index index.php;
#下面两句是给fastcgi权限,可以支持 ?s=/module/controller/action的url访问模式
fastcgi_split_path_info ^((?U).+\.php)(/?.+)$;
fastcgi_param SCRIPT_FILENAME $document_root$fastcgi_script_name;
#下面两句才能真正支持 index.php/index/index/index的pathinfo模式
fastcgi_param PATH_INFO $fastcgi_path_info;
fastcgi_param PATH_TRANSLATED $document_root$fastcgi_path_info;
include fastcgi_params;
}
#这里改目录(二级目录访问)
location /XXXXXXX/ {
index index.html index.htm index.php;
#autoindex on;
if (!-e $request_filename) {
#这里改目录(二级目录访问)
rewrite ^/XXXXXXX/(.*)$ /XXXXXXX/index.php?s=/$1 last;
break;
}
}
location ~ .*\.(css|js|gif|jpg|jpeg|png|bmp|swf)$ {
#这里改目录(二级目录访问)
root D:/phpstudy_pro/WWW/XXXXXXX/public;
expires 30d;
}
add_header Content-Security-Policy "default-src 'self' 123.134.28.24 'unsafe-eval' 'unsafe-inline' fonts.gstatic.com data:;img-src 'self' 123.134.28.24 'unsafe-eval' 'unsafe-inline' data: blob: ;style-src * 'self' 123.134.28.24 'unsafe-eval' 'unsafe-inline' fonts.gstatic.com data:";
add_header X-Content-Type-Options: nosniff;
add_header X-XSS-Protection "1; mode=block";
#add_header Access-Control-Allow-Origin: http://www.one.site.com;
#add_header X-Frame-Options: deny;
#add_header Strict-Transport-Security: max-age=3600; includeSubDomains;
}
#include vhosts.conf;
map $time_iso8601 $logdate {
'~^(?\\d{4}-\\d{2}-\\d{2})' $ymd;
default 'date-not-found';
}
include vhosts/*.conf;
client_max_body_size 50m;
client_body_buffer_size 60k;
client_body_timeout 60;
client_header_buffer_size 64k;
client_header_timeout 60;
error_page 400 error/400.html;
error_page 403 error/403.html;
error_page 404 error/404.html;
error_page 500 error/500.html;
error_page 501 error/501.html;
error_page 502 error/502.html;
error_page 503 error/503.html;
error_page 504 error/504.html;
error_page 505 error/505.html;
error_page 506 error/506.html;
error_page 507 error/507.html;
error_page 509 error/509.html;
error_page 510 error/510.html;
keepalive_requests 100;
large_client_header_buffers 4 64k;
reset_timedout_connection on;
send_timeout 60;
sendfile_max_chunk 512k;
server_names_hash_bucket_size 256;
}
worker_rlimit_nofile 100000;
error_log D:/phpstudy_pro/WWW crit;