为k8s集群搭建私有仓库------Harbor
Harbor简史
Harbor是由VMware公司开源的容器镜像仓库, 事实上, Harbor是在Docker Registry上进行了相应的企业级拓展,
从而获得了更加广泛的应用, 这些企业级拓展包括: 管理用户界面、基于角色访问控制、AD/LDAP集成以及审计日志, 足以满足基本企业需求.
Harbor主要功能
- 基于角色访问控制
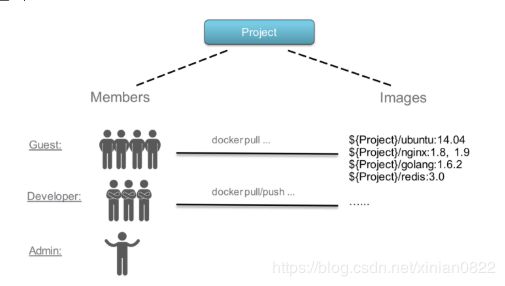
在企业中, 通常有不同的开发团队负责不同的项目, 镜像像代码一样, 每个人角色不同需求也不同, 因此就需要访问权限控制,
根据角色分配相应的权限.比如: 开发人员需要对项目构建这就用到读写权限(pull/push), 测试人员只需要读权限(pull), 运维一般管理镜像仓库,
具备权限分配能力, 项目经理具备所有权限
Guest: 对指定项目只读权限
Developer: 开发人员, 读写项目权限
Admin: 项目管理, 所有权限
Anonymous: 当用户未登陆时,该用户视为匿名, 不能访问私有项目, 只能访问公开项目
2.镜像复制
可以将仓库中的镜像同步到远程Harbor, 类似于MySQL的主从复制功能
3.镜像删除和空间回收
Harbor支持在web界面删除镜像, 回收无用的镜像, 释放磁盘空间
4.审计
对仓库的所有操作都有记录
1.REST API
2.具备完整的API, 方便与外部集成
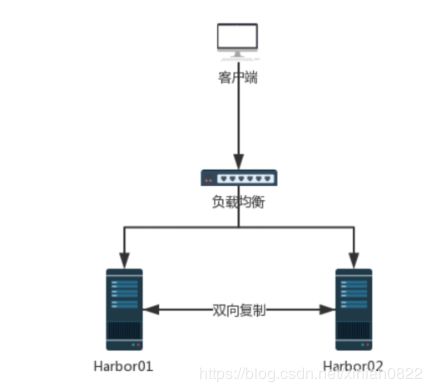
Harbor高可用方案
方案一: 共享存储
方案二: 复制同步
Harbor组件
组件 功能
harbor-adminserver 配置管理中心
harbor-db MySQL数据库
harbor-jobservice 负责镜像复制
harbor-log 记录操作日志
harbor-UI Web管理页面和API
nginx 前端代理, 负责前端页面和镜像的上传/下载/转发
redis 会话
registry 镜像
Harbor部署
1、环境准备
192.168.1.175 harbor
192.168.1.205 master 只安装docker 仅供测试使用
2、Harbor部署:https方式
wget https://storage.googleapis.com/harbor-releases/harbor-offline-installer-v1.5.3.tgz
(下载此软件包需要, 请自行安装Google浏览器插件,但是我在做的时候直接是wget下来的,大概一分钟到两分钟作用)
3、部署docker
# curl -o /etc/yum.repos.d/docker-ce.repo https://mirrors.aliyun.com/docker-ce/linux/centos/docker-ce.repo
# yum -y install docker-ce
# curl -sSL https://get.daocloud.io/daotools/set_mirror.sh | sh -s http://bc437cce.m.daocloud.io
4、部署docker-compose1.22
方案一、
GitHub:docker-compose1.22
# curl -L https://github.com/docker/compose/releases/download/1.22.0/docker-compose-`uname -s`-`uname -m` -o /usr/local/bin/docker-compose
# chmod a+x /usr/local/bin/docker-compose
方案二、
aliyun:docker-compose1.21
# curl -L https://mirrors.aliyun.com/docker-toolbox/linux/compose/1.21.2/docker-compose-Linux-x86_64 -o /usr/local/bin/docker-compose
# chmod a+x /usr/local/bin/docker-compose
5、自签发TLS证书(可不做)
# mkdir /ca
# cd /ca
# openssl req \
-newkey rsa:4096 -nodes -sha256 -keyout ca.key \
-x509 -days 365 -out ca.crt
Country Name (2 letter code) [XX]:CN
State or Province Name (full name) []:BJ
Locality Name (eg, city) [Default City]:BJ
Organization Name (eg, company) [Default Company Ltd]:qianfeng
Organizational Unit Name (eg, section) []:yunjisuan
Common Name (eg, your name or your server's hostname) []:harbor
Email Address []:[email protected]
# openssl req -newkey rsa:4096 -nodes -sha256 -keyout harbor.io.key -out harbor.io.csr
Country Name (2 letter code) [XX]:CN
State or Province Name (full name) []:BJ
Locality Name (eg, city) [Default City]:BJ
Organization Name (eg, company) [Default Company Ltd]:qianfeng
Organizational Unit Name (eg, section) []:yunjisuan
Common Name (eg, your name or your server's hostname) []:harbor
Email Address []:[email protected]
Please enter the following 'extra' attributes
to be sent with your certificate request
A challenge password []:直接回车
An optional company name []:直接回车
# openssl x509 -req -days 365 -in harbor.io.csr -CA ca.crt -CAkey ca.key -CAcreateserial -out harbor.io.crt
7、部署配置
# tar xf harbor-offline-installer-v1.5.3.tgz
# cd harbor
方案一、
# vim harbor.cfg //其他的不要改
hostname = harbor.io
ui_url_protocol = https
ssl_cert = /ca/harbor.io.crt
ssl_cert_key = /ca/harbor.io.key
方案二、
# vim harbor.cfg //其他的不要改
hostname = 主机域名或IP
customize_crt = false
# ./prepare
# ./install.sh
//如果重新安装,需要删除/data,删除已经load的docker镜像,然后重启docker
8、查看运行状态
# docker-compose ps
看到 harbor-adminserver、harbor-db、harbor-jobservice、harbor-log、harbor-ui、nginx、redis、registry都启动起来了就代表成功了
9、 修改 /etc/docker/daemon.json 添加下列信息
"insecure-registries": ["http://10.3.138.254:80"]
否则harbor通过http的方式无法连接Docker Registry 的https
客户端测试
# docker login -u admin -p Harbor12345 http://10.3.131.2
登录报错:显示连接被拒绝
原因:docker版本的问题
登录报错解决方案:
客户端
# cat /etc/docker/daemon.conf
{
"insecure-registries": ["http://10.3.131.2"]
}
# cat /usr/lib/systemd/system/docker.service |grep ExecStart
ExecStart=/usr/bin/dockerd -H fd:// --insecure-registry 10.3.131.2 --containerd=/run/containerd/containerd.sock
# systemctl daemon-reload
# systemctl restart docker
server端:
[root@docker1 harbor]# cat /etc/docker/daemon.conf
{
"insecure-registries": ["http://10.3.131.2"]
}
[root@docker1 harbor]# cat /usr/lib/systemd/system/docker.service |grep ExecStart
ExecStart=/usr/bin/dockerd -H fd:// --insecure-registry 10.3.131.2:5000 --containerd=/run/containerd/containerd.sock
# systemctl daemon-reload
# systemctl restart docker
# docker-compose down -v
# docker-compose up -d
# docker login -u admin -p Harbor12345 http://192.168.254.138
WARNING! Using --password via the CLI is insecure. Use --password-stdin.
WARNING! Your password will be stored unencrypted in /root/.docker/config.json.
Configure a credential helper to remove this war
Harbor使用
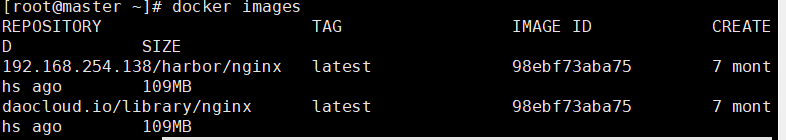
docker tag daocloud.io/library/nginx 192.168.254.138/harbor/nginx
docker push 192.168.254.138/harbor/nginx
定期清理
存储库删除分为两步:
- 第一步: 在web中删除, 这是标记删除, 存储库中还存在
- 第二步: 确保所有人都没有用仓库的情况下, 执行以下指令, 若有人上传/下载镜像可能会出现错误
docker-compose stop
# docker run -it --name gc --rm --volumes-from registry vmware/registry:2.6.2-photon garbage-collect /etc/registryconfig.yml
# docker-compose start