Snort is network intrusion detection system (NIDS) which is a type of open-source software to detect attacks, anomaly traffic in the network. It is written in C language and works on multiplatform. It is themost widely deployed intrusion prevention system in the world (With over 4 million downloads and nearly 500,000 registered users)
There are not enough resource how to configure Snort in linux. So I wrote this post.
Before snort installation, some package should be installed. So we wrote this command in terminal screen.
sudo apt-get install flex bison build-essential checkinstall libpcap-dev libnet1-dev libpcre3-dev libmysqlclient15-dev libnetfilter-queue-dev iptables-dev
After that, libnet-1.12 is downloaded and unpacked.
wget https://libdnet.googlecode.com/files/libdnet-1.12.tgz
tar xvfz libdnet-1.12.tgz
Then, you should go to this library packet folder.(When downloading file from net, your file is downloaded in /home/downloads folder). In the file directory,
./configure “CFLAGS=-fpic”
this configuration for 64 bit machine.
make
for compilation
sudo checkinstall
Then,
sudo dpkg -i libdnet_1.12-1_i386.deb
sudo ln -s /usr/local/lib/libdnet.1.0.1 /usr/lib/libdnet.1
(above) command is to create symbolic link.
After all, you should go to snort site (http://snort.org). Download snort and daq (snort-2.9.6.1.tar.gz anddaq-2.0.2.tar.gz ). In this example, firstly, I download snort-2.9.7.0.tar.gz and daq-2.0.4.tar.gz. However, I encountered a problem, so I used older versions of softwares.
Problem message:
checking for daq_load_modules in -ldaq_static… no
ERROR! daq_static library not found, go get it from
http://www.snort.org/.
Then, (used older version)
tar xvfvz daq-2.0.2.tar.gz
./configure
make
sudo checkinstall
After that, snort file is configured
tar xvfvz snort-2.9.6.1.tar.gz
./configure
make
sudo checkinstall
sudo dpkg -i snort_2.9.6.1-1_i386.deb
sudo ln -s /usr/local/bin/snort /usr/sbin/snort
After installation,
sudo ldconfig -v // to view version
After all, you should go to snort site to download snort rules (snortrules-snapshot-2970.tar.gz). Then it is unpacked. Create snort folder under etc folder. You can configure your snort.conf file. (/etc/snort)
ipvar HOME_NET 192.168.1.110/24 // or default mode (eg: any) can be used
ipvar EXTERNAL_NET !$HOME_NET // or default mode (eg: any) can be used
Also, you should write rule in folder (/etc/snort/rules) or append new rules to the other rules.
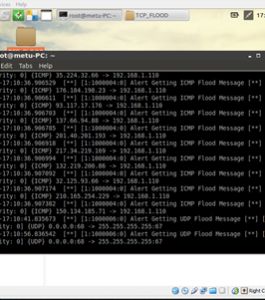
alert icmp any any -> any any (msg:”Alert Getting ICMP Flood Message”;sid:1000004;)
alert tcp any any -> any any (msg:”Alert Getting TCP Flood Message”;sid:1000005;)
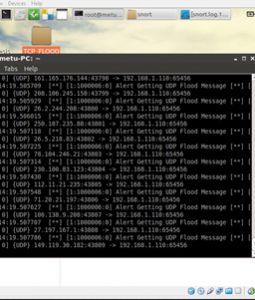
alert udp any any -> any any (msg:”Alert Getting UDP Flood Message”;sid:1000006;)
alert tcp $EXTERNAL_NET any -> any any (msg:”Alert HTTP GET DDos”;pcre:”/GET.*\htm/i”;classtype:web-application-activity;sid:1000007;)
After all, you can run snort using this command:
snort -i eth0 -l /var/log/snort -c /etc/snort/snort.conf -A console
This command says: your network input port is eth0, snort is working IDS mode (-i), your log file is/var/log/snort (-l), your configuration /etc/snort/snort.conf (-c) and you can see all process on the terminal screen (-A console).
I also encountered another problem when I entered this command;
snort -i 5 -l /var/log/snort -c /etc/snort/snort.conf -A console
Also, my network input is configured as eth2.
Problem Message:
ERROR: Can’t start DAQ (-1) – SIOCGIFHWADDR: No such device!
I solved it when I changed eth2 to eth0 and enter eth0 instead of 5
After that, you can test it by sending hping3 / ping to other machine (snort host).
(Pictures below; TCP, ICMP and UDP packets are catched)