[问题已处理]-阿里云服务器种了挖矿病毒aliyun.one
小伙伴服务器现象 是cpu爆高.但是从top itop等看不出系统哪有问题.
登录如下
top
查看crontab 发现种了木马 通过redis植入(没设置密码)
hosts crontab等 都被修改的一塌糊涂.尝试修改crontab 任务,还没有修改完 就被覆盖了.无法清空crontab.到处都有这个脚本的影子,应该无时无刻在更新脚本 同步脚本吧.
就算侥幸注释掉 过一会还是会被覆盖成新的
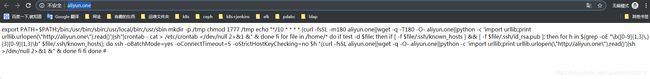
病毒木马如下
刚刚热乎的帖子 别人也种了一个一样的.国内帖子 好像几乎没有
在肉鸡里面执行crontab,这样的话如果用户里存在信任的主机,并且有密匙的话,这样就连信任的主机也会变成肉鸡了。
虽然现在看上去他只是定时去拉取了脚本,但是当他准备发动攻击,修改了脚本内容以后性质就不同了
论坛新鲜的帖子
https://www.v2ex.com/t/624351
搜到一个隐藏文件~/.viminfo 感觉像是源头,但是如果要清理得一次性 删干净,难度太大.
| # This viminfo file was generated by Vim 7.4. # You may edit it if you're careful!
# Value of 'encoding' when this file was written *encoding=utf-8
# hlsearch on (H) or off (h): ~H # Command Line History (newest to oldest): :q :wq ://aliyun.one/ ::q :w
# Search String History (newest to oldest):
# Expression History (newest to oldest):
# Input Line History (newest to oldest):
# Input Line History (newest to oldest):
# Registers: ""1 LINE 0
"2 LINE 0 0.0.0.0 nicehash.com "3 LINE 0 0.0.0.0 nicehash.com "4 LINE 0 0.0.0.0 f2pool.com "5 LINE 0 0.0.0.0 pastebin.com "6 LINE 0 0.0.0.0 onion.to "7 LINE 0 0.0.0.0 onion.glass "8 LINE 0 0.0.0.0 civiclink.network "9 LINE 0 0.0.0.0 onion.mn
# File marks: '0 222 0 ~/.viminfo '1 1 0 /usr/local/sbin/d118cec4f2e457 '2 20 48 /etc/crontab '3 4 0 /etc/crontab '4 1 0 /etc/hosts '5 1 0 /etc/cron.d/root '6 1 0 /etc/cron.d/www-data '7 1 0 /etc/cron.d/user '8 2 0 /etc/cron.d/sysstat '9 1 0 /etc/cron.d/redis
# Jumplist (newest first): -' 222 0 ~/.viminfo -' 1 0 ~/.viminfo -' 1 0 /usr/local/sbin/d118cec4f2e457 -' 20 48 /etc/crontab -' 4 0 /etc/crontab -' 1 0 /etc/hosts -' 1 0 /etc/cron.d/root -' 1 0 /etc/cron.d/www-data -' 1 0 /etc/cron.d/user -' 2 0 /etc/cron.d/sysstat -' 1 0 /etc/cron.d/sysstat -' 1 0 /etc/cron.d/redis -' 1 0 /etc/cron.d/nobody -' 1 0 /etc/cron.d/nginx -' 1 0 /etc/cron.d/admin -' 5 0 /etc/cron.d/0hourly -' 1 0 /etc/cron.d/0hourly -' 1 0 /etc/cron.deny -' 1 0 /etc/crontab -' 1 0 /etc/cron.daily/man-db.cron -' 1 0 /etc/cron.daily/logrotate -' 1 0 /var/spool/cron/crontabs/root -' 1 0 /var/spool/cron/root -' 1 0 /var/spool/cron/root -' 1 0 /var/spool/cron/root -' 1 0 /var/spool/cron/root -' 1 0 /var/spool/cron/root -' 1 0 /var/spool/cron/root -' 1 0 /var/spool/cron/root -' 1 0 /var/spool/cron/root -' 1 0 /var/spool/cron/root -' 1 0 /var/spool/cron/root -' 1 0 /var/spool/cron/root -' 1 0 /var/spool/cron/root -' 1 0 /var/spool/cron/root -' 1 0 /var/spool/cron/root -' 1 0 /var/spool/cron/root -' 1 0 /var/spool/cron/root -' 1 0 /var/spool/cron/root -' 1 0 /var/spool/cron/root -' 1 0 /var/spool/cron/root -' 1 0 /var/spool/cron/root -' 1 0 /var/spool/cron/root -' 1 0 /var/spool/cron/root -' 1 0 /var/spool/cron/root -' 1 0 /var/spool/cron/root -' 1 0 /var/spool/cron/root -' 1 0 /var/spool/cron/root -' 1 0 /var/spool/cron/root -' 1 0 /var/spool/cron/root -' 1 0 /var/spool/cron/root -' 1 0 /var/spool/cron/root -' 1 0 /var/spool/cron/root -' 1 0 /var/spool/cron/root -' 1 0 /etc/cron.daily/logrotate -' 1 0 /var/spool/cron/root -' 1 0 /var/spool/cron/root -' 1 0 /var/spool/cron/root -' 1 0 /var/spool/cron/root -' 1 0 /var/spool/cron/root -' 1 0 /var/spool/cron/root -' 1 0 /var/spool/cron/root -' 1 0 /var/spool/cron/root -' 1 0 /var/spool/cron/root -' 1 0 /var/spool/cron/root -' 1 0 /var/spool/cron/root -' 1 0 /var/spool/cron/root -' 1 0 /var/spool/cron/root -' 1 0 /var/spool/cron/root -' 1 0 /var/spool/cron/root -' 1 0 /var/spool/cron/root -' 1 0 /var/spool/cron/root -' 1 0 /var/spool/cron/root -' 1 0 /var/spool/cron/root -' 1 0 /var/spool/cron/root -' 1 0 /var/spool/cron/root -' 1 0 /var/spool/cron/root -' 1 0 /var/spool/cron/root -' 1 0 /var/spool/cron/root -' 1 0 /var/spool/cron/root -' 1 0 /var/spool/cron/root -' 1 0 /var/spool/cron/root -' 1 0 /var/spool/cron/root -' 1 0 /var/spool/cron/root -' 1 0 /var/spool/cron/root -' 1 0 /var/spool/cron/root -' 1 0 /var/spool/cron/root -' 1 0 /etc/cron.daily/man-db.cron -' 1 0 /etc/cron.daily/logrotate -' 1 0 /var/spool/cron/root -' 1 0 /var/spool/cron/root -' 1 0 /var/spool/cron/root -' 1 0 /var/spool/cron/root -' 1 0 /var/spool/cron/root -' 1 0 /var/spool/cron/root -' 1 0 /var/spool/cron/root -' 1 0 /var/spool/cron/root -' 1 0 /var/spool/cron/root -' 1 0 /var/spool/cron/root
# History of marks within files (newest to oldest):
> ~/.viminfo " 222 0
> /usr/local/sbin/d118cec4f2e457 " 1 0
> /etc/crontab " 20 48 ^ 20 49 . 20 0 + 4 0 + 20 0
> /etc/hosts " 1 0 ^ 1 10 . 1 9 + 1 0 + 1 9
> /etc/cron.d/root " 1 0 ^ 1 1 . 1 0 + 1 0
> /etc/cron.d/www-data " 1 0
> /etc/cron.d/user " 1 0
> /etc/cron.d/sysstat " 2 0
> /etc/cron.d/redis " 1 0
> /etc/cron.d/nobody " 1 0
> /etc/cron.d/nginx " 1 0
> /etc/cron.d/admin " 1 0
> /etc/cron.d/0hourly " 5 0
> /etc/cron.deny " 1 0
> /etc/cron.daily/man-db.cron " 1 0
> /etc/cron.daily/logrotate " 1 0
> /var/spool/cron/crontabs/root " 1 0 . 1 0 + 1 0
> /var/spool/cron/root " 1 0 . 1 0 + 1 0 |
find了一下 发现到处都是这种类型的脚本.这几个文件在上面还没有.
因为是root账号中毒 没法删除root账号,不能铲掉机子. (小伙伴删除了wget和curl 好像并不能解决cpu负载高的问题)
我目前想到的办法 只能把crontab stop掉.然后禁止开机启动.或者直接删除crontab文件. host文件修改一下aliyun.one的地址,避免脚本被更新.如果可以的话 还是重装一下.
恢复使用是可以的 但是还是不安全

![[问题已处理]-阿里云服务器种了挖矿病毒aliyun.one_第1张图片](http://img.e-com-net.com/image/info8/df009ff2d3144464b596f5ba40862b13.jpg)
![[问题已处理]-阿里云服务器种了挖矿病毒aliyun.one_第2张图片](http://img.e-com-net.com/image/info8/10916db18b1c4a90b796400537256559.png)
![[问题已处理]-阿里云服务器种了挖矿病毒aliyun.one_第3张图片](http://img.e-com-net.com/image/info8/57412f6dd2d643e7aa9a86e6ba20046c.png)


![[问题已处理]-阿里云服务器种了挖矿病毒aliyun.one_第4张图片](http://img.e-com-net.com/image/info8/bdca2161d8234eb0b5467108a991f0f5.png)

![[问题已处理]-阿里云服务器种了挖矿病毒aliyun.one_第5张图片](http://img.e-com-net.com/image/info8/89041056baa942d5996d7504fddbca52.jpg)

![[问题已处理]-阿里云服务器种了挖矿病毒aliyun.one_第6张图片](http://img.e-com-net.com/image/info8/06266e21b33c4b9d953da7814b93cea5.jpg)
![[问题已处理]-阿里云服务器种了挖矿病毒aliyun.one_第7张图片](http://img.e-com-net.com/image/info8/e6f5ccf784c84b59bc2cc86dd357da41.jpg)