PHP 功能木马 webshell
MSG
特征:
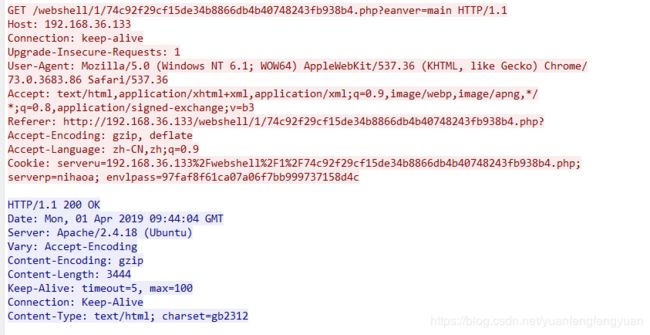
Cookie: envlpass=97faf8f61ca07a06f7bb999737158d4c; serveru=192.168.36.133%2Fwebshell%2F1%2F74c92f29cf15de34b8866db4b40748243fb938b4.php; serverp=nihaoa
后门:qyvc.com
检测:
alert http any any -> any any (msg:"Webshell.PHP.Success.Exec.Threat.A"; flow:established,to_server; content:"envlpass="; http_cookie; nocase; fast_pattern; content:"serveru="; http_cookie; nocase; content:"serverp="; http_cookie; nocase; reference:url,https://mp.csdn.net/mdeditor/88943927; classtype:web-application-attack; sid:80000012; rev:1; metadata:created_at 2019_04_01, updated_at 2019_04_01;)
pcre:"/Cookie\x3a\x20envlpass=[a-z0-9]{32}(.*?)serveru=/i"
PCAP:https://github.com/Fate9091/fate/blob/master/webshell-pass.rar
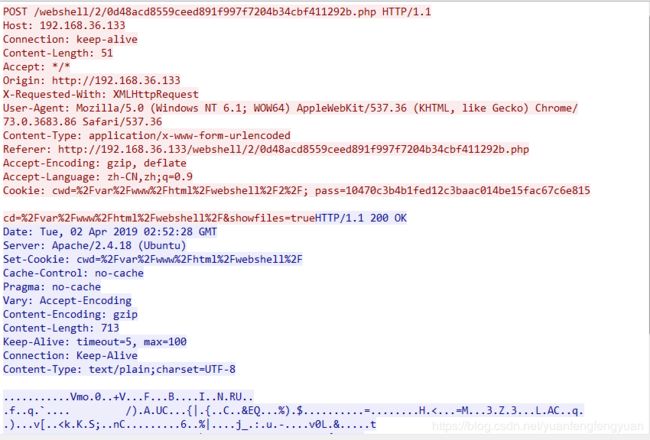
Cookie: cwd=%2Fvar%2Fwww%2Fhtml%2Fwebshell%2F2%2F; pass=10470c3b4b1fed12c3baac014be15fac67c6e815
Cookie: pass=10470c3b4b1fed12c3baac014be15fac67c6e815
检测
Http_header
pcre:"/Cookie\x3a\x20(cwd=[\S]*\x3b\x20)?pass=[a-z0-9]{40}/i"
http_response_body
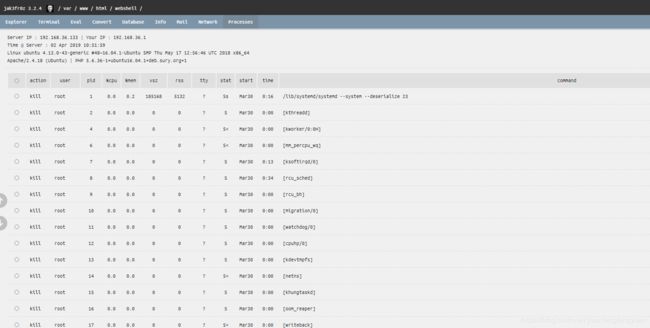
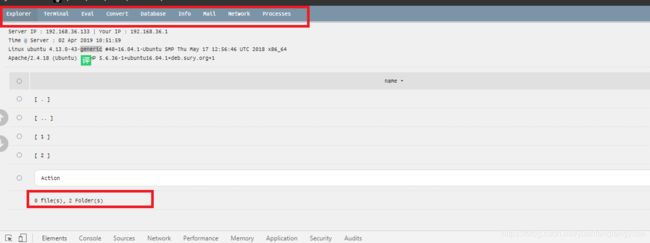
pcre:"/\x22menuterminal\x22[\s\S]*\x22menueval\x22[\s\S]*\x22menuprocesses\x22[\S\s]*\d+\x20Folder\x28s\x29/i"
alert http any any -> any any (msg:"Webshell.PHP.jak3fr0z.Success.Folder.Threat.A"; flow:established,to_server; content:"POST"; http_method; content:"cwd="; http_cookie; nocase; pcre:"/pass=[a-z0-9]{40}$/RCi"; reference:url,https://mp.csdn.net/mdeditor/88943927; classtype:web-application-attack; sid:80000013; rev:1; metadata:created_at 2019_04_01, updated_at 2019_04_01;)
PCAP:https://github.com/Fate9091/fate/blob/master/jak3fr0z-pass.rar
login=b374k&submitlogin=Go+%21
Cookie: s_self=%3F; b374k=fb621f5060b9f65acf8eb4232e3024140dea2b34; s_python=Python+2.7.12%0A; s_perl=5.022001; s_gcc=gcc+%28Ubuntu+5.4.0-6ubuntu1%7E16.04.10%29+5.4.0+20160609; s_tar=tar+%28GNU+tar%29+1.28; s_wget=GNU+Wget+1.17.1+built+on+linux-gnu.; s_lwpdownload=%2Fusr%2Fbin%2Flwp-download+version+%5Bunknown%5D+calling+Getopt%3A%3AStd%3A%3Agetopts+%28version+1.11+%5Bparanoid%5D%29%2C; s_curl=curl+7.47.0+%28x86_64-pc-linux-gnu%29+libcurl%2F7.47.0+GnuTLS%2F3.4.10+zlib%2F1.2.8+libidn%2F1.32+librtmp%2F2.3
检测
pcre:"/Cookie\x3a.*?b374k=[a-z0-9]{40}\x3b/"
alert http any any -> any any (msg:"Webshell.b374k.Cookies.A"; flow:established,to_server; pcre:"/b374k=[a-z0-9]{40}\x3b/Ci";reference:url,https://mp.csdn.net/mdeditor/88943927; classtype:web-application-attack; sid:80000016; rev:1; metadata:created_at 2019_04_09, updated_at 2019_04_08;)
PCAP:https://github.com/Fate9091/fate/blob/master/b374k.pcap
检测
pcre:"/form\x20method=\x27GET\x27[\s\S]*value=\x27Files\x27\x20size=\x27[\S\s]*value=\x27Bruteforce\x27\x20size=\x27/i"
alert http any any -> any any (msg:"Webshell.PHP.Gaza.Http_Response_Body.Threat.A"; flow:established,from_server; file_data; content:"value=|27|Change-Admin|27 20|size="; nocase; content:"value=|27|Server-Info|27 20|size="; distance:0; nocase; reference:url,https://mp.csdn.net/mdeditor/88943927; classtype:web-application-attack; sid:80000017; rev:1; metadata:created_at 2019_04_01, updated_at 2019_04_01;)
开源:
alert http $HOME_NET any -> $EXTERNAL_NET any (msg:"ET WEB_SERVER WebShell - Generic - c99shell based header"; flow:established,to_client; file_data; content:"Uname
User
Php
Hdd
Cwd"; classtype:attempted-user; sid:2015918; rev:2; metadata:created_at 2012_11_21, updated_at 2012_11_21;)
alert tcp $HTTP_SERVERS any -> $EXTERNAL_NET any (msg:"ET ATTACK_RESPONSE Output of id command from HTTP server"; flow:established; content:"uid="; pcre:"/^\d+[^\r\n\s]+/R"; content:" gid="; within:5; pcre:"/^\d+[^\r\n\s]+/R"; content:" groups="; within:8; classtype:bad-unknown; sid:2019284; rev:3; metadata:created_at 2014_09_26, updated_at 2014_09_26;)
alert http any any -> any any (msg:"WebShell.PHP.AnonGhost.Response-Body.C"; flow:established,to_client; file_data; content:"
PCAP:https://github.com/Fate9091/fate/blob/master/8-AnonGhost.rar
7.PIC
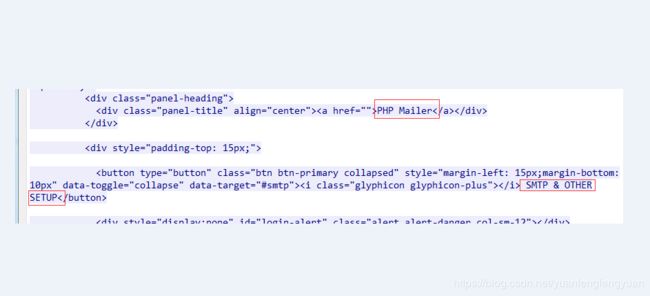
FSID_00020134,HTTP,HTTP_Response_Body,FLOW,IMPORT,IMPORT,3,WebShell,WebShell.PHP.PHP_Mailer.Response-Body.A,NOCASE,0,181,pcre:"/PHP\x20Mailer\x3c[\S\s]*?\x20SMTP\x20\x26\x20OTHER\x20SETUP\x3c[\S\s]*?\x22\x20If\x20you\x20dont\x20have\x20SMTP\x20login\x2c\x20leave\x20blank\x20queries\x20above\x20\x22/i",NA,NA,NA,NA,NA,NA,NA,iDomeK-00000936,iDomeT-00008504:PHP_Mailer WebShell;iDomeT-00008371:WebShell控制行为,2019/4/12
alert http any any -> any any (msg:"WebShell.PHP.PHP_Mailer.Response-Body.A"; flow:established,to_client; file_data; content:""; fast_pattern; pcre:"/PHP\x20Mailer\x3c[\S\s]*?\x20SMTP\x20\x26\x20OTHER\x20SETUP\x3c[\S\s]*?\x22\x20If\x20you\x20dont\x20have\x20SMTP\x20login\x2c\x20leave\x20blank\x20queries\x20above\x20\x22/Ri"; reference:md5,26fda294b2c808784b8f0ee4767288e4; classtype:web-application-attack; sid:7070151; rev:3; metadata:create_at 2018_7_13, updated_at 2018_7_13;)
PCAP:https://github.com/Fate9091/fate/blob/master/9-pass—.rar
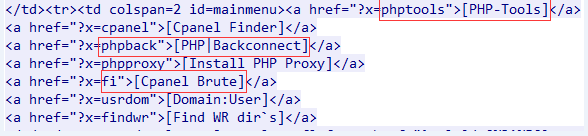
alert http any any -> any any (msg:"WebShell.PHP.Response-Body.G"; flow:established,to_client; file_data; content:"id=mainmenu>
PCAP:https://github.com/Fate9091/fate/blob/master/10-pass.rar
9.PIC
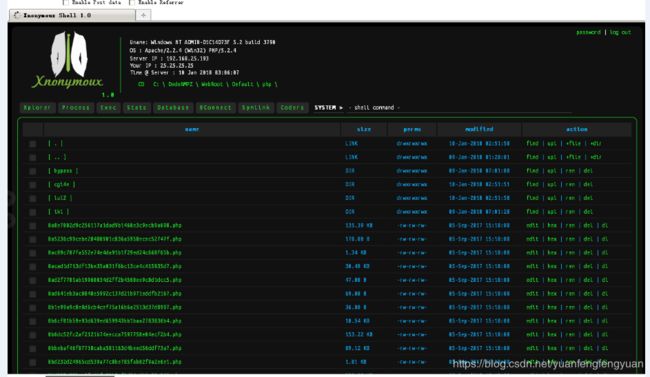
alert http any any -> any any (msg:"WebShell.PHP.Xnonymoux.Response-Body.A"; flow:established,to_client; content:"title=|27|File|20|Explorer|27|>
PCAP:https://github.com/Fate9091/fate/blob/master/12-pass.rar