Linux PAM 验证
-
- 一、什么是PAM验证
- 二、PAM层次结构
- 三、PAM工作原理
- 四、PAM配置
- 4.1 PAM配置文件格式
- 4.2 PAM的模块类型
- 4.3 PAM的控制标记
- 4.4 模块路径及模块参数
- 五、PAM应用程序开发
- 5.1 预备知识
- 5.1.1 头文件
- 5.1.2 struct pam_conv
- 5.1.3 相关函数
- 5.2 利用已有的PAM模块编写登陆验证
- 5.3 自定义PAM模块编写登陆验证
- 5.1 预备知识
一、什么是PAM验证
Linux-PAM(linux可插入认证模块)是一套共享库,使本地系统管理员可以随意选择程序的认证方式。换句话说,不用重新编译一个包含PAM功能的应用程序,就可以改变它使用的认证机制。应用程序只需调用API就可方便的使用PAM提供的各种认证功能,而无需了解底层的实现。这种方式下,就算升级本地认证机制,也不用修改程序。
像我们使用su命令时,系统会提示你输入root用户的密码,这就是su命令通过调用PAM模块实现的。
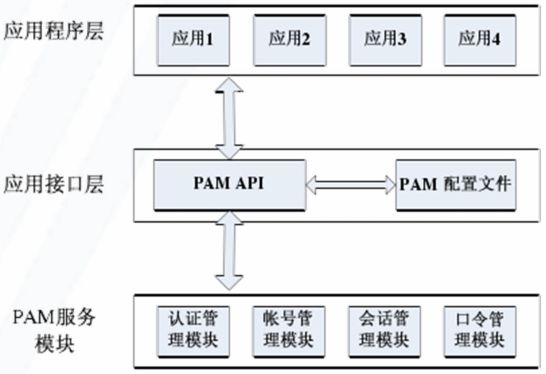
二、PAM层次结构
PAM API是应用程序层与PAM服务模块之间联系的纽带,起着承上启下的作用。系统管理员通过PAM配置文件来制定不同应用程序的不同认证策略。
当应用程序调用PAM API时,应用接口层按照配置文件pam.conf的规定,加载相应的PAM服务模块。当PAM服务模块完成相应的认证操作之后,将结果返回给应用接口层。
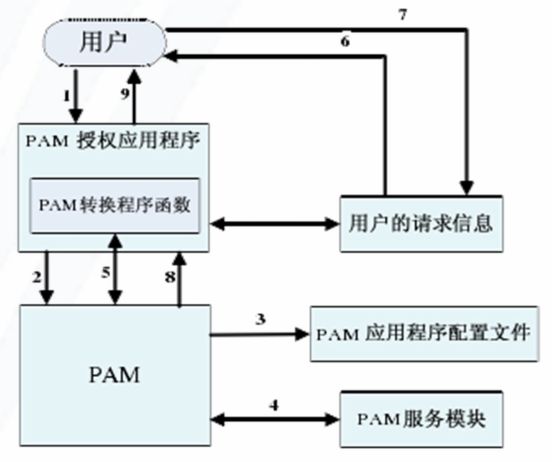
三、PAM工作原理
1.用户调用某个应用程序,以得到某种服务
2.PAM应用程序调用后台的PAM库进行认证工作
3.PAM库到/etc/pam.d/目录查找有关程序配置来确定认证机制
4.PAM库装载所需的认证模块
5.上述装载的认证模块让PAM与应用程序中的会话函数进行通信
6.会话函数向用户要求有关信息
7.用户对这些要求做出回应,提供所需信息
8.PAM认证模块通过PAM库将认证信息提供给应用程序
9.认证完成后,应用程序做出两种选择:
认证成功:将所需权限赋予用户,并通知用户
认证失败:通知用户
四、PAM配置
4.1 PAM配置文件格式
PAM配置文件有两种写法,第一种是写在/etc/pam.conf文件中,但这种方法现在已被废弃,不再介绍。
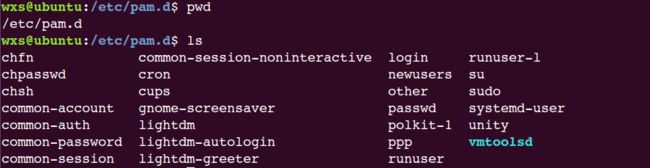
第二种是在/etc/pam.d目录中,使用应用程序名作为配置文件名:
配置格式形如:
auth required pam_stack.so service=system-auth其中:
auth 模块类型
required 控制标记
pam_stack.so 模块路径
service=system-auth 模块参数
4.2 PAM的模块类型
Linux PAM有以下四种模块类型,分别代表四种不同的任务:
| 管理方式 | 说明 |
|---|---|
| auth | 用来对用户的身份进行识别.如:提示用户输入密码,或判断用户是否为root等 |
| account | 对帐号的各项属性进行检查.如:是否允许登录,是否达到最大用户数,或是root用户是否允许在这个终端登录等 |
| session | 这个模块用来定义用户登录前的,及用户退出后所要进行的操作.如:登录连接信息,用户数据的打开与关闭,挂载文件系统等 |
| password | 使用用户信息来更新。如修改用户密码 |
4.3 PAM的控制标记
PAM使用控制标记来处理和判断各个模块的返回值:
| 控制标记 | 说明 |
|---|---|
| required | 表示即使某个模块对用户的验证失败,也要等所有的模块都执行完毕后,PAM才返回错误信息。这样做是为了不让用户知道被哪个模块拒绝。如果对用户验证成功,所有的模块都会返回成功信息。 |
| requisite | 与required相似,但是如果这个模块返回失败,则立刻向应用程序返回失败,表示此类型失败。不再进行同类型后面的操作 |
| sufficient | 表示如果一个用户通过这个模块的验证,PAM结构就立刻返回验证成功信息(即使前面有模块fail了,也会把 fail结果忽略掉),把控制权交回应用程序。后面的层叠模块即使使用requisite或者required 控制标志,也不再执行。如果验证失败,sufficient 的作用和 optional 相同 |
| optional | 示即使本行指定的模块验证失败,也允许用户接受应用程序提供的服务,一般返回PAM_IGNORE(忽略) |
4.4 模块路径及模块参数
(1)模块路径
即要调用模块的位置。 对于64为Ubuntu,一般保存在/lib/x86_64-linux-gnu/security,如: pam_unix.so。
同一个模块,可以出现在不同的类型中。每个模块针对不同的模块类型,编制了不同的执行函数。
(2)模块参数
即传递给模块的参数.参数可以有多个,之间用空格分隔开。
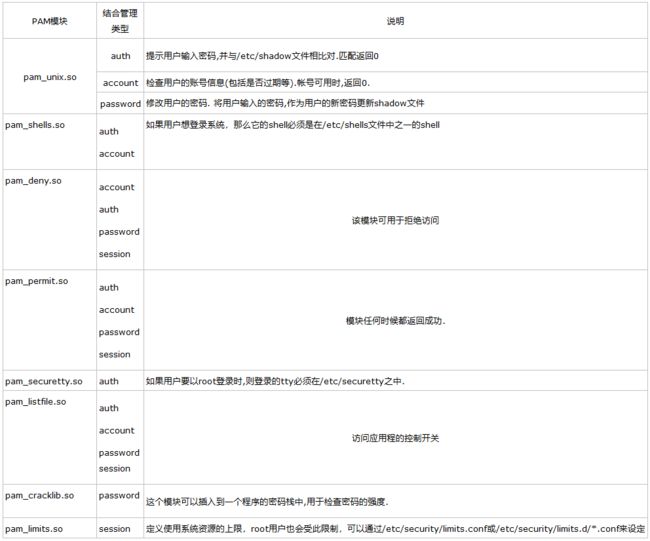
(3)常用的PAM模块
五、PAM应用程序开发
5.1 预备知识
5.1.1 头文件
#include 如果提示找不到头文件,需要先安装一下:
sudo apt-get install libpam0g-dev
5.1.2 struct pam_conv
这个结构体用于与PAM通信,因为其中比较复杂,我们只列出我们要用到的:
static struct pam_conv conv = {
misc_conv,
NULL
};5.1.3 相关函数
以下函数具有相同的返回值,这里先说明下:
PAM_SUCCESS: Successful completion
PAM_ABORT: Genaral failure
PAM_SYSTEM_ERR: System error
PAM_BUF_ERR: Memort buffer error
/*
service_name: /etc/pam.d中注册的服务名
user: 要验证的用户名
*/
int pam_start(const char *service_name, const char *user,
const struct pam_conv *pam_conversation,
pam_handle_t **pamh);
/*
flags: 一般为0
*/
int pam_authenticate(pam_handle_t *pamh, int flags);
/*
flags: 一般为0
*/
int pam_acct_mgmt(pam_handle_t *pamh, int flags);
/*
pam_status:为验证函数的返回值,即pam_authenticate或pam_acct_mgmt的返回值
*/
int pam_end(pam_handle_t *pamh, int pam_status);
/*
errnum: 错误值
*/
const char *pam_strerror(pam_handle_t *pamh, int errnum);5.2 利用已有的PAM模块编写登陆验证
首先在/etc/pam.d中注册服务,服务名为my_pam,我们利用已有的模块pam_unix.so:
wxs@ubuntu:/etc/pam.d$ vim my_pam
wxs@ubuntu:/etc/pam.d$ cd /etc/pam.d/
wxs@ubuntu:/etc/pam.d$ sudo vim my_pam
wxs@ubuntu:/etc/pam.d$
wxs@ubuntu:/etc/pam.d$ cat my_pam
auth required /lib/x86_64-linux-gnu/security/pam_unix.so
account required /lib/x86_64-linux-gnu/security/pam_unix.so编写test.c文件来测试:
#include 生成可执行文件:
gcc test.c -lpam -lpam_misc -ldl -o test
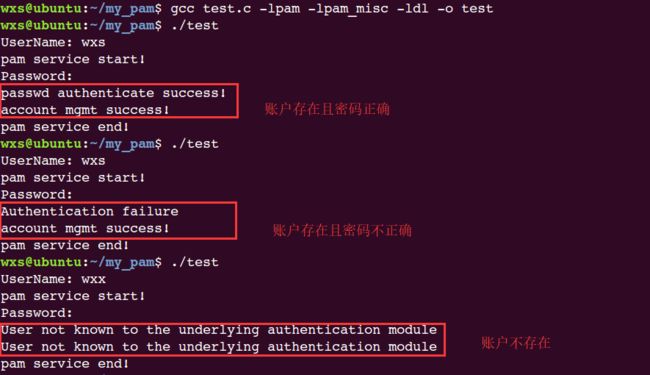
因为该程序要查询/etc/passwd和/etc/shadow文件,因此要么执行时加上sudo,要么sudo chown root.root test,不然可能会出现错误。运行结果如下:
5.3 自定义PAM模块编写登陆验证
引入头文件pam_private.h:
/*
* pam_private.h
*
* This is the Linux-PAM Library Private Header. It contains things
* internal to the Linux-PAM library. Things not needed by either an
* application or module.
*
* Please see end of file for copyright.
*
* Creator: Marc Ewing.
* Maintained: CVS
*/
#ifndef _PAM_PRIVATE_H
#define _PAM_PRIVATE_H
//#include "config.h"
#include 编写验证模块pam_test_auth.c:
#include "pam_private.h"
#include 生成动态库:
gcc -o pam_test_auth.so -shared -fPIC pam_test_auth.c -lpam -lcrypt
将其放到/lib/x86_64-linux-gnu/security中:
sudo mv pam_test_auth.so /lib/x86_64-linux-gnu/security
因为这里我们只编写登陆验证,因此去掉账户有效性的验证,修改test.c代码如下:
#include 重新编译test.c:
gcc test.c -lpam -lpam_misc -ldl -o test
别忘了/etc/pam.d中的服务配置信息还要修改为我们自己写的动态库:
wxs@ubuntu:~/my_pam$ sudo cat /etc/pam.d/my_pam
auth required /lib/x86_64-linux-gnu/security/pam_test_auth.so
account required /lib/x86_64-linux-gnu/security/pam_test_auth.so一切就绪,我们准备一个账号来测试:
用户名:mdzz
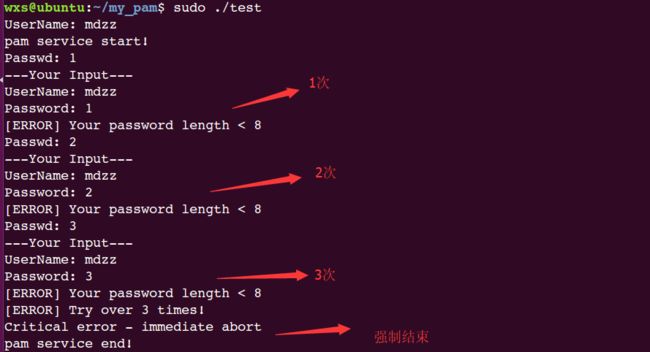
密码:mdzzMDZZ123此时运行程序:
因为我们代码逻辑是先判断密码强度再验证正确(这个逻辑并不正确,只是为了演示使用),因此当密码强度不够时:
当尝试次数超过三次时:
正确输入时: