TLS协商 wireshark 抓包分析
分析环境在 windows 下,使用 windows 版本的nginx部署自签服务器,使用 openssl s_client 命令测试双向认证。
准备工具:
1. wireshark: 从腾讯软件中心搜索wireshark并下载64位版本:https://pc.qq.com/
https://dl.softmgr.qq.com/original/System/Wireshark-win64-3.2.2.exe
2. npcap程序:https://nmap.org/download.html
最新版本:https://nmap.org/npcap/dist/npcap-0.9991.exe
注意:
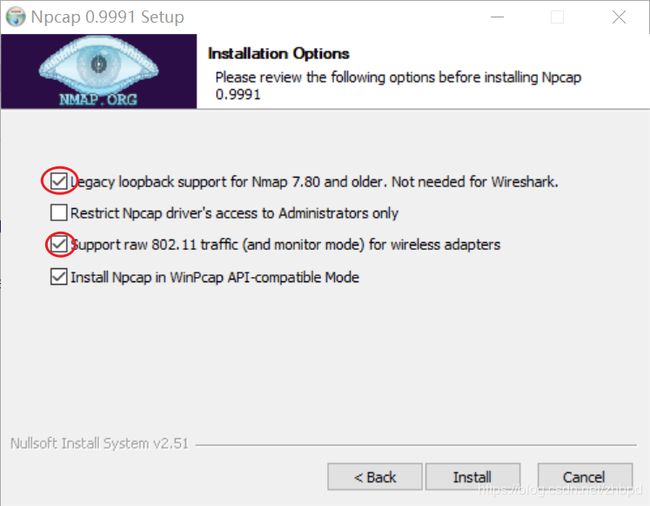
因为我是在同一台服务器上启动服务器并且抓包,所以整个操作都是在loop地址127.0.0.1上进行。wireshark默认不支持loopback抓包,所以安装 wireshark 时,不要安装其自带的 npcap程序,如果安装了先卸载老版本,再安装独立版本。
安装 npcap 独立版本时,注意勾选第一个(loopback)和第三个(802.11)方框。
然后启动 wireshark, 选择第一个 npcap loopback 设备就开始抓 localhost 的包了。
开始抓包:
1. 启动 nginx
2. 启动wireshark,选择抓loopback设备的数据包
3. 使用 openssl s_client 启动测试命令
openssl s_client -connect localhost:443 -cert client.crt -key client.key -CAfile root.crt如下是输出内容:
C:\nginx-1.16.1\ssl\CA2>openssl s_client -connect localhost:443 -cert client.crt -key client.key -CAfile root.crt
CONNECTED(000003DC)
Can't use SSL_get_servername
depth=1 C = cn, ST = sh, L = sh, O = bt, OU = test, CN = root
verify return:1
depth=0 C = cn, ST = sh, L = sh, O = bt, OU = test, CN = localhost
verify return:1
---
Certificate chain
0 s:C = cn, ST = sh, L = sh, O = bt, OU = test, CN = localhost
i:C = cn, ST = sh, L = sh, O = bt, OU = test, CN = root
---
Server certificate
-----BEGIN CERTIFICATE-----
MIIDHTCCAgUCAQEwDQYJKoZIhvcNAQELBQAwUjELMAkGA1UEBhMCY24xCzAJBgNV
BAgMAnNoMQswCQYDVQQHDAJzaDELMAkGA1UECgwCYnQxDTALBgNVBAsMBHRlc3Qx
DTALBgNVBAMMBHJvb3QwHhcNMjAwNTExMDg1MDQ1WhcNMjEwNTExMDg1MDQ1WjBX
MQswCQYDVQQGEwJjbjELMAkGA1UECAwCc2gxCzAJBgNVBAcMAnNoMQswCQYDVQQK
DAJidDENMAsGA1UECwwEdGVzdDESMBAGA1UEAwwJbG9jYWxob3N0MIIBIjANBgkq
hkiG9w0BAQEFAAOCAQ8AMIIBCgKCAQEAvKhPBeQUERKSAiiy/Y5z1V6fLiss/ZiG
tLF7dOKvrtaqzGL6lGs2ybY5p1v7wtIw3AqTwup63YDyYtghnacu26DHMlsYDIaa
tamP3+uTvDKlCTnw57ShTPhkPukIKZevv0SFyt+lEAeVM0S+zdOTlb2anA5pbOjB
eoA79LB6iVR1Ltp6nvKShBfRMk4JEp6fjPdhMwN+mX42PPkWHwHBLiRjVvRWYbFD
+g4wHjXutZ1iRWxOJe/vC+QFKCldKo19pp3S8O3WgHixTsIoJW//7q+hRMvvd6Em
3VB+rYTpd4/76O+Blp+QZJ4SvfeHX702p+2ik+6/5M7YlnlQCGmCfwIDAQABMA0G
CSqGSIb3DQEBCwUAA4IBAQBqyJ1ZflMqy5QLwCEP8CZvD+SqGJpGUQCZjiZs/v1h
BepuKVrolQCPm55NVIuEAj6xZnysjG4wpY6I+brFcUB7I9MVXyg+pKwAVEBm6tvz
kG90w1zk/0lNmC+Eyi8ElbI8/+kVGLeFQyoIjMt3EEsCqX87wVBWyUdFwKZuCEJs
UvSDjTaL50T+6DXzshU1n4UcWq2dirZ8D3g8DnS/5T+AwdiDv9xqe7cuFyxB7ajA
/5bECrgKsFnebf/3xlgoQgMwGvUUEPVlT8AgX/NxGMFwV0m63s8PXz1PAGRfkUZn
fiPbxoP5mUxNndvQha3PB07Zb+WwESuNXeJERNW4WLEp
-----END CERTIFICATE-----
subject=C = cn, ST = sh, L = sh, O = bt, OU = test, CN = localhost
issuer=C = cn, ST = sh, L = sh, O = bt, OU = test, CN = root
---
Acceptable client certificate CA names
C = cn, ST = sh, L = sh, O = bt, OU = test, CN = root
Client Certificate Types: RSA sign, DSA sign, ECDSA sign
Requested Signature Algorithms: ECDSA+SHA256:ECDSA+SHA384:ECDSA+SHA512:Ed25519:Ed448:RSA-PSS+SHA256:RSA-PSS+SHA384:RSA-PSS+SHA512:RSA-PSS+SHA256:RSA-PSS+SHA384:RSA-PSS+SHA512:RSA+SHA256:RSA+SHA384:RSA+SHA512:ECDSA+SHA224:ECDSA+SHA1:RSA+SHA224:RSA+SHA1:DSA+SHA224:DSA+SHA1:DSA+SHA256:DSA+SHA384:DSA+SHA512
Shared Requested Signature Algorithms: ECDSA+SHA256:ECDSA+SHA384:ECDSA+SHA512:Ed25519:Ed448:RSA-PSS+SHA256:RSA-PSS+SHA384:RSA-PSS+SHA512:RSA-PSS+SHA256:RSA-PSS+SHA384:RSA-PSS+SHA512:RSA+SHA256:RSA+SHA384:RSA+SHA512:ECDSA+SHA224:ECDSA+SHA1:RSA+SHA224:RSA+SHA1:DSA+SHA224:DSA+SHA1:DSA+SHA256:DSA+SHA384:DSA+SHA512
Peer signing digest: SHA256
Peer signature type: RSA-PSS
Server Temp Key: X25519, 253 bits
---
SSL handshake has read 2407 bytes and written 2289 bytes
Verification: OK
---
New, TLSv1.2, Cipher is ECDHE-RSA-AES256-GCM-SHA384
Server public key is 2048 bit
Secure Renegotiation IS supported
Compression: NONE
Expansion: NONE
No ALPN negotiated
SSL-Session:
Protocol : TLSv1.2
Cipher : ECDHE-RSA-AES256-GCM-SHA384
Session-ID: 494AAA15B6D90E318A4E274D92F8AF875B30B882854E76438367D7323830250E
Session-ID-ctx:
Master-Key: 2F7CF73C11F77697DF9EFE4CEB59EF6D649BB66387F4444D7435C360B94A241F04833FD24A666751147578676F522EAF
PSK identity: None
PSK identity hint: None
SRP username: None
TLS session ticket lifetime hint: 300 (seconds)
TLS session ticket:
0000 - 91 67 91 07 f1 5c 29 83-8e 6a 41 9b 13 41 9f a7 .g...\)..jA..A..
0010 - 41 68 37 ca 0a 69 02 2e-34 16 9c 8a 59 13 60 a7 Ah7..i..4...Y.`.
0020 - 49 0a 6d dd 12 a5 4f 1a-33 8d 24 a7 e1 a4 a4 c9 I.m...O.3.$.....
0030 - 36 36 aa 61 94 dd 03 ef-71 5d 63 84 25 c2 77 c6 66.a....q]c.%.w.
0040 - 4b 87 b4 26 ef 9d af b8-c4 c0 0b a4 0c 7b a2 38 K..&.........{.8
0050 - cf ac 33 eb 3e 6a 6d cc-19 4b fc ec 40 9e 6b 1b ..3.>[email protected].
0060 - cc 82 55 08 42 5e eb 63-4d 39 5e fd 47 fb 2d 56 ..U.B^.cM9^.G.-V
0070 - 01 c9 3e ce cd e3 4f f2-ba 34 41 3b 11 c8 3f c6 ..>...O..4A;..?.
0080 - 09 47 30 39 b6 b8 24 74-09 ed be 02 80 26 1a cc .G09..$t.....&..
0090 - 2c 1a 54 fc 53 9d 31 ed-30 70 27 f6 19 ab 57 e2 ,.T.S.1.0p'...W.
00a0 - e3 d6 ce ec 1a 5f 3e 02-32 ed 9e 9c 38 f0 9e b3 ....._>.2...8...
00b0 - 90 a1 46 97 78 23 2d 5a-fb 3e 2c f2 5b ae 01 ef ..F.x#-Z.>,.[...
00c0 - 2d 25 84 78 e7 6f ef 88-74 b5 fc 33 bb e6 66 6b -%.x.o..t..3..fk
00d0 - 71 9d 21 96 32 f5 45 e8-f3 e8 f4 6e 31 03 4f 1e q.!.2.E....n1.O.
00e0 - 43 b8 25 60 85 20 08 25-11 ae 6e 03 f2 47 38 82 C.%`. .%..n..G8.
00f0 - d6 7a dd d1 21 45 29 67-75 9d 47 8d ad 84 d8 e4 .z..!E)gu.G.....
0100 - fe 68 54 22 74 76 b9 b1-90 37 62 81 54 88 3e 3b .hT"tv...7b.T.>;
0110 - 9a 19 f0 fa 7b 28 47 0e-79 0c bd 31 1b da 48 9d ....{(G.y..1..H.
0120 - b2 9c c3 58 75 a2 9d 5a-0c 5d 4b c1 27 8b 48 87 ...Xu..Z.]K.'.H.
0130 - a9 62 db 8d bb 9b 2f 17-27 50 0f f9 bb 9f 8a f1 .b..../.'P......
0140 - 77 17 0c a9 4c 9b 95 54-f7 bd 90 86 db 76 8f 93 w...L..T.....v..
0150 - ce 57 f3 87 94 f5 6f 45-f1 8b 05 4b c2 2c 22 ba .W....oE...K.,".
0160 - 14 ae 1f b9 a7 b3 af 3c-2a 25 82 ee 01 01 82 a0 .......<*%......
0170 - 02 c5 48 8e dc 52 08 73-c3 1d e7 1f 0d 94 6a f1 ..H..R.s......j.
0180 - 6a be 10 57 e5 1f 2e 44-a0 be 15 54 b8 5f df d4 j..W...D...T._..
0190 - 9c c2 d3 61 cb d1 16 86-db dc c4 7c 26 2a 6e 80 ...a.......|&*n.
01a0 - f0 b9 ad 2c d6 c2 70 12-10 a0 d1 4a 47 1c 07 48 ...,..p....JG..H
01b0 - 69 23 f0 62 43 89 11 79-05 93 7c 8c 85 f6 b5 fe i#.bC..y..|.....
01c0 - b9 b2 1a 26 cb 0e 71 21-a8 af d9 e5 60 ba db d8 ...&..q!....`...
01d0 - 67 72 7d 76 64 af c1 70-4e ac dd 97 7d 26 5a 63 gr}vd..pN...}&Zc
01e0 - 69 12 01 83 de 10 fc 7d-ad 0a 55 bf 24 9f f6 63 i......}..U.$..c
01f0 - 03 03 e8 42 48 6a 5e fd-78 63 0b aa 46 b9 a7 e1 ...BHj^.xc..F...
0200 - b6 9e ea cc e5 1d e0 09-99 49 b3 de 59 22 aa 4d .........I..Y".M
0210 - ee 9e 0e a1 ed 49 11 1d-e0 c2 d6 07 ad f1 01 02 .....I..........
0220 - b5 0e f0 9e 09 3f 21 ed-8b bf cf 88 6c e8 e2 8f .....?!.....l...
0230 - 3b 85 66 37 f3 24 bb e0-3b 40 17 b2 ac 9d 00 2f ;.f7.$..;@...../
0240 - ec 09 73 88 92 65 84 75-53 e7 67 da 84 f4 6a 0d ..s..e.uS.g...j.
0250 - 8e 52 9e 65 43 d5 66 65-e5 98 09 0a 8b a0 74 b7 .R.eC.fe......t.
0260 - d4 e7 96 e6 5c 04 a7 2a-59 83 22 7b f8 bc f1 13 ....\..*Y."{....
0270 - ae a5 b1 93 a4 05 8c 18-5a db 38 54 28 72 94 47 ........Z.8T(r.G
0280 - 5d 97 48 f0 de d2 df b0-42 6b 5d c6 6f 9d 33 a4 ].H.....Bk].o.3.
0290 - 86 52 24 8f a3 65 8c c1-64 97 8b 4f b0 55 3d 2f .R$..e..d..O.U=/
02a0 - a9 f7 20 d3 28 de 7b 70-7f de 46 61 fa 2d c9 c8 .. .(.{p..Fa.-..
02b0 - 1b 0c 40 4a cf 5e ee c3-3e 16 16 3e fc aa 2e 5a ..@J.^..>..>...Z
02c0 - f6 99 de 17 74 0d 30 76-2e 7d fc cc ff 6c 2e 37 ....t.0v.}...l.7
02d0 - d0 da ba e7 41 89 db 51-33 14 d3 b0 d8 41 73 aa ....A..Q3....As.
02e0 - 65 bd 90 2a 79 59 45 fa-0a fe 3d 91 d9 fa 03 67 e..*yYE...=....g
02f0 - e8 40 fe 56 5c 1f 00 7b-82 fb a8 0d c8 49 c3 e9 [email protected]\..{.....I..
0300 - aa bd d7 91 85 b9 c8 b5-07 a5 b0 89 78 98 e7 f2 ............x...
0310 - d5 39 43 a4 14 7f f9 d0-d0 7e f3 fb 88 06 70 85 .9C......~....p.
0320 - 47 42 47 92 1c 1e 06 85-74 5b 4c 3e f3 3f 3b 4b GBG.....t[L>.?;K
0330 - 9f 5e 12 f2 4d 2d d1 f3-e0 fd 5a 2c dd 23 d6 f8 .^..M-....Z,.#..
0340 - ee 96 c3 ee 7c 3f 57 d8-e5 d9 81 2f 62 0e 37 cd ....|?W..../b.7.
0350 - 6b f5 03 87 af de d6 c9-f1 d6 28 82 84 aa c4 fc k.........(.....
0360 - 44 72 c7 82 3c 7b 3b 79-8b 32 51 b8 ef be 2d 79 Dr..<{;y.2Q...-y
0370 - c8 e6 8a 9a d5 0a 0a 5b-ce 2a dd 01 dd 30 06 2c .......[.*...0.,
0380 - 6b 31 13 b4 9c 49 47 ea-07 62 b8 8a 4b 13 88 55 k1...IG..b..K..U
0390 - 34 e0 bd 66 0b 37 6b 28-78 73 3e 96 f7 1a d4 0c 4..f.7k(xs>.....
03a0 - 32 b5 27 29 c8 56 08 1e-35 04 ba da 79 8d b3 b2 2.').V..5...y...
03b0 - 96 24 18 eb 10 1a 43 59-38 0c aa fb 6b 47 a6 83 .$....CY8...kG..
03c0 - 14 0f e2 fb 22 bf 73 42-c0 72 15 f9 da dc 3f 7a ....".sB.r....?z
03d0 - 6b a6 0d 27 3f b2 7b e8-ff 7e d1 5b 87 49 e2 fa k..'?.{..~.[.I..
Start Time: 1589336593
Timeout : 7200 (sec)
Verify return code: 0 (ok)
Extended master secret: yes
---
因为咱们是用的TCP协议连接的,所以到这一步会停下来,然后要手动输入GET /才会输出html内容。
GET /
Welcome to nginx!
Welcome to nginx!
If you see this page, the nginx web server is successfully installed and
working. Further configuration is required.
For online documentation and support please refer to
nginx.org.
Commercial support is available at
nginx.com.
Thank you for using nginx.
closed
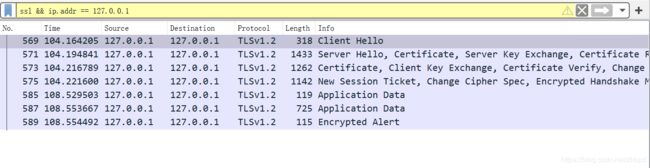
C:\nginx-1.16.1\ssl\CA2>这时候 wireshark 已经抓到 TLS 协商流程的数据包了。在 wireshark filter输入框输入 ssl && ip.addr == 127.0.0.1 过滤显示。
结果如下:
由上图可以看到,TLS协商基本上按三大步实现,没一大步可能包含若干小步。
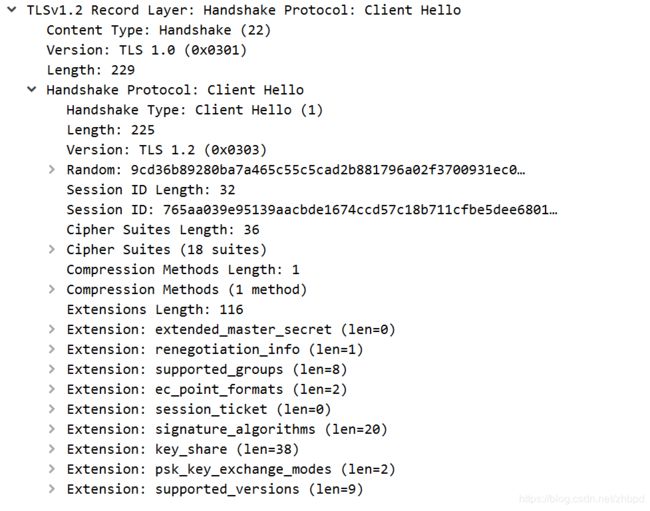
1. Client Hello
告诉服务器我要进行TLS协商了,提供自己的版本、随机数、加密套件列表、session id、压缩算法等。
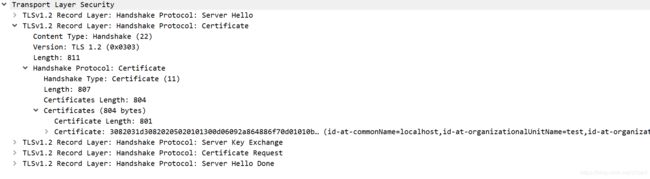
2. Server Hello, Certificate, Server Key Exchange, Certificate Request, Server Hello Done
告诉客户端服务器的版本、随机数、选定的加密套件、扩展参数信息;提供EC参数和签名公钥;并且要求客户端提供证书;
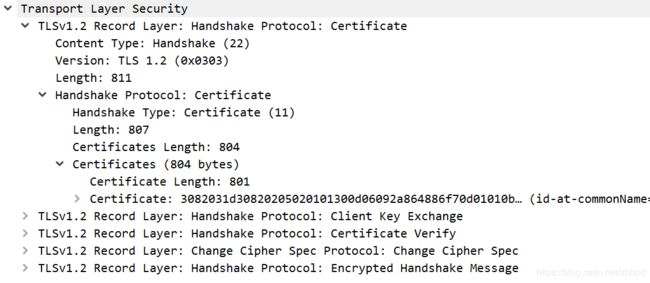
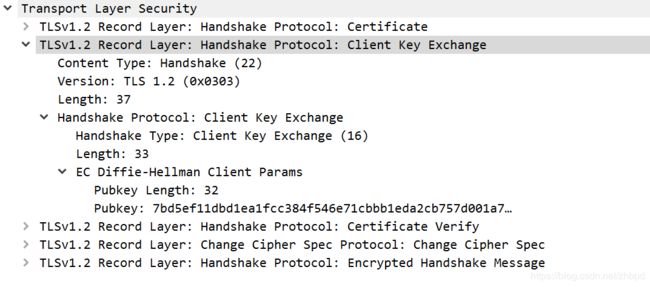
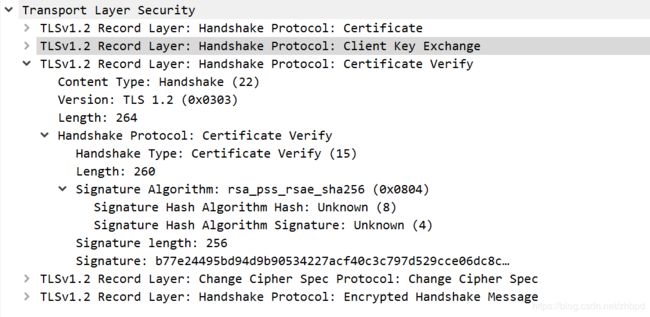
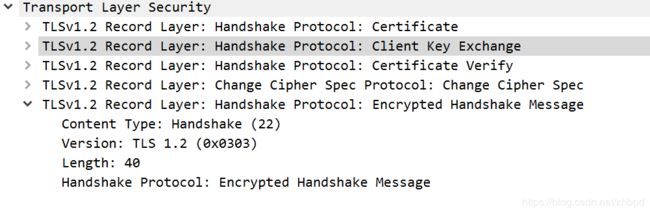
3. Certificate,Client Key Exchange, Certificate Verify, Change Cipher Spec, Encrypted Handshake Message
告诉服务器我的证书,我的EC参数和签名公钥,我的证书是可信的,使用协商密钥加密握手消息;
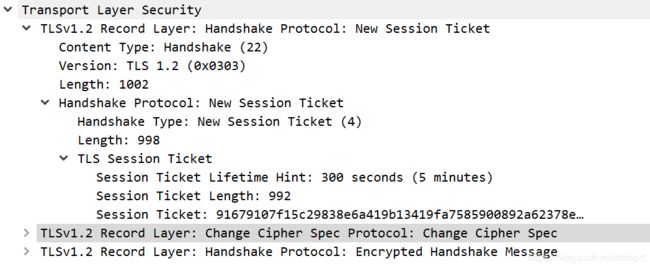
4. New Session Ticket, Change Cipher Spec, Encrypted Handshake Message
告诉客户端确认的Session Ticket时常和id,确认协商密码,使用协商密钥加密握手消息;
到这一步就协商就完成了,后续就可以用协商密钥加密数据通道了。
下面分析每一步的 wireshark 抓包:
Client Hello
Server Hello
 Certificate
Certificate
New Session Ticket