Fabric CA 用户指南
Fabric CA 用户指南
证书颁发机构
提供的功能如下:
- 身份的注册 :或连接到LDAP(Lightweight Directory Access Protocol,轻量目录访问协议)作为用户注册表;
- 签发登记证书(ECerts)(Enrollment Certificates)
- 签发交易证书(TCerts)(Transaction Certificates) :在Hyperledger Fabric blockchain上交易时提供匿名性和不可链接性。
- 证书续期和撤销
- Fabric CA 用户指南
- 架构
- 文件格式
- 1 ca server 配置文件
- 2 ca client 配置文件
- 配置设置
- Fabric CA Server
- 1 初始化server
- 2 启动server
- 3 设置server集群和使用LDAP
- 31 设置数据库
- 311 PostgreSQL
- 312 PostgreSQL SSL Configuration
- 313 MySQL
- 314 MySQL SSL Configuration
- 在MySQL server中配置SSL的基本操作
- 请求客户端证书
- 32 Configuring LDAP
- 33 设置一个集群
- 34 设置多个CAs
- 341 cacount
- 342 cafiles
- 35 enroll一个intermediate CA
- 31 设置数据库
- Fabric CA Client
- 1 enroll the bootstrap identity
- 2 register a new identity
- 3 register and enroll a peer identity
- 4 从另一个CA server上拿到CA证书链
- 5 Reenroll an identity
- 5 撤销一个证书或一个identity
- 使用TLS
- 和特定CA contact
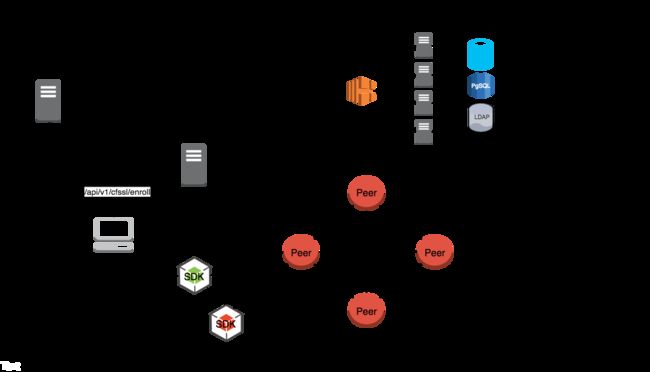
1. 架构
有两种与fabric-CA server交互的方式:
- fabric-CA client
- fabric SDK
HA代理端点:调节流量负载平衡
2. 文件格式
2.1 ca server 配置文件
# Server's listening port (default: 7054)
port: 7054
# Enables debug logging (default: false)
debug: false
#############################################################################
# TLS section for the server's listening port
#
# The following types are supported for client authentication: NoClientCert,
# RequestClientCert, RequireAnyClientCert, VerifyClientCertIfGiven,
# and RequireAndVerifyClientCert.
#
# Certfiles is a list of root certificate authorities that the server uses
# when verifying client certificates.
#############################################################################
tls:
# Enable TLS (default: false)
enabled: false
# TLS for the server's listening port
certfile: ca-cert.pem
keyfile: ca-key.pem
clientauth:
type: noclientcert
certfiles:
#############################################################################
# The CA section contains information related to the Certificate Authority
# including the name of the CA, which should be unique for all members
# of a blockchain network. It also includes the key and certificate files
# used when issuing enrollment certificates (ECerts) and transaction
# certificates (TCerts).
# The chainfile (if it exists) contains the certificate chain which
# should be trusted for this CA, where the 1st in the chain is always the
# root CA certificate.
#############################################################################
ca:
# Name of this CA
name:
# Key file (default: ca-key.pem)
keyfile: ca-key.pem
# Certificate file (default: ca-cert.pem)
certfile: ca-cert.pem
# Chain file (default: chain-cert.pem)
chainfile: ca-chain.pem
#############################################################################
# The registry section controls how the fabric-ca-server does two things:
# 1) authenticates enrollment requests which contain a username and password
# (also known as an enrollment ID and secret).
# 2) once authenticated, retrieves the identity's attribute names and
# values which the fabric-ca-server optionally puts into TCerts
# which it issues for transacting on the Hyperledger Fabric blockchain.
# These attributes are useful for making access control decisions in
# chaincode.
# There are two main configuration options:
# 1) The fabric-ca-server is the registry
# 2) An LDAP server is the registry, in which case the fabric-ca-server
# calls the LDAP server to perform these tasks.
#############################################################################
registry:
# Maximum number of times a password/secret can be reused for enrollment
# (default: -1, which means there is no limit)
maxenrollments: -1
# Contains identity information which is used when LDAP is disabled
identities:
- name: <<>>
pass: <<>>
type: client
affiliation: ""
maxenrollments: -1
attrs:
hf.Registrar.Roles: "client,user,peer,validator,auditor"
hf.Registrar.DelegateRoles: "client,user,validator,auditor"
hf.Revoker: true
hf.IntermediateCA: true
#############################################################################
# Database section
# Supported types are: "sqlite3", "postgres", and "mysql".
# The datasource value depends on the type.
# If the type is "sqlite3", the datasource value is a file name to use
# as the database store. Since "sqlite3" is an embedded database, it
# may not be used if you want to run the fabric-ca-server in a cluster.
# To run the fabric-ca-server in a cluster, you must choose "postgres"
# or "mysql".
#############################################################################
db:
type: sqlite3
datasource: fabric-ca-server.db
tls:
enabled: false
certfiles:
- db-server-cert.pem
client:
certfile: db-client-cert.pem
keyfile: db-client-key.pem
#############################################################################
# LDAP section
# If LDAP is enabled, the fabric-ca-server calls LDAP to:
# 1) authenticate enrollment ID and secret (i.e. username and password)
# for enrollment requests;
# 2) To retrieve identity attributes
#############################################################################
ldap:
# Enables or disables the LDAP client (default: false)
enabled: false
# The URL of the LDAP server
url: ldap://:@:/>>
names:
- C: US
ST: "North Carolina"
L:
O: Hyperledger
OU: Fabric
hosts:
- <<>>
- localhost
ca:
expiry: 131400h
pathlength: <<>>
#############################################################################
# BCCSP (BlockChain Crypto Service Provider) section is used to select which
# crypto library implementation to use
#############################################################################
bccsp:
default: SW
sw:
hash: SHA2
security: 256
filekeystore:
# The directory used for the software file-based keystore
keystore: msp/keystore
#############################################################################
# Multi CA section
#
# Each Fabric CA server contains one CA by default. This section is used
# to configure multiple CAs in a single server.
#
# 1) --cacount
# Automatically generate non-default CAs. The names of these
# additional CAs are "ca1", "ca2", ... "caN", where "N" is
# This is particularly useful in a development environment to quickly set up
# multiple CAs.
#
# 2) --cafiles
# For each CA config file in the list, generate a separate signing CA. Each CA
# config file in this list MAY contain all of the same elements as are found in
# the server config file except port, debug, and tls sections.
#
# Examples:
# fabric-ca-server start -b admin:adminpw --cacount 2
#
# fabric-ca-server start -b admin:adminpw --cafiles ca/ca1/fabric-ca-server-config.yaml
# --cafiles ca/ca2/fabric-ca-server-config.yaml
#
### ##########################################################################
cacount:
cafiles:
#############################################################################
# Intermediate CA section
#
# The relationship between servers and CAs is as follows:
# 1) A single server process may contain or function as one or more CAs.
# This is configured by the "Multi CA section" above.
# 2) Each CA is either a root CA or an intermediate CA.
# 3) Each intermediate CA has a parent CA which is either a root CA or another intermediate CA.
#
# This section pertains to configuration of #2 and #3.
# If the "intermediate.parentserver.url" property is set,
# then this is an intermediate CA with the specified parent
# CA.
#
# parentserver section
# url - The URL of the parent server
# caname - Name of the CA to enroll within the server
#
# enrollment section used to enroll intermediate CA with parent CA
# profile - Name of the signing profile to use in issuing the certificate
# label - Label to use in HSM operations
#
# tls section for secure socket connection
# certfiles - PEM-encoded list of trusted root certificate files
# client:
# certfile - PEM-encoded certificate file for when client authentication
# is enabled on server
# keyfile - PEM-encoded key file for when client authentication
# is enabled on server
#############################################################################
intermediate:
parentserver:
url:
caname:
enrollment:
hosts:
profile:
label:
tls:
certfiles:
client:
certfile:
keyfile: server配置文件主要包括以下几个部分:
- ca:设置ca的名字,公私钥、证书和chainfile的存储文件名
- registry:设置账户名密码的最大重复数,注册用的账户名和密码,以及其他信息(类型、从属关系等)
- LDAP:可以有两种registry选择:sever和LDAP,若LDAP设置enabled则server调用LDAP去授权获得账户名密码和检索用户信息。
- db:支持三种数据库: “sqlite3”(内置数据库)、”postgres”(cluster)、”mysql”(cluster)
- affiliation:设置组织关系
- signing:
- default:用于签发登记证书ECert,设置截止期
- “ca” profile:用于签发中级证书,设置截止期、中级CA能否签发其他中级证书。
- csr(Certificate Signing Request):控制根证书的创建
- bccsp:加密方式
- multi CA section:设置一个server多个CA
- cacount:几个CA
- cafiles:CA的配置文件列表
- intermediate:设置中级CA
2.2 ca client 配置文件
#############################################################################
# Client Configuration
#############################################################################
# URL of the Fabric CA server (default: http://localhost:7054)
URL: http://localhost:7054
# Membership Service Provider (MSP) directory
# When the client is used to enroll a peer or an orderer, this field must be
# set to the MSP directory of the peer/orderer
MSPDir:
#############################################################################
# TLS section for secure socket connection
#############################################################################
tls:
# Enable TLS (default: false)
enabled: false
certfiles:
client:
certfile:
keyfile:
#############################################################################
# Certificate Signing Request section for generating the CSR for
# an enrollment certificate (ECert)
#############################################################################
csr:
cn: <<>>
names:
- C: US
ST: North Carolina
L:
O: Hyperledger
OU: Fabric
hosts:
- <<>>
ca:
pathlen:
pathlenzero:
expiry:
#############################################################################
# Registration section used to register a new identity with Fabric CA server
#############################################################################
id:
name:
type:
affiliation:
attributes:
- name:
value:
#############################################################################
# Enrollment section used to enroll an identity with Fabric CA server
#############################################################################
enrollment:
profile:
label:
# Name of the CA to connect to within the fabric-ca server
caname: client配置文件主要包括如下内容:
- MSPDir:设置要enroll的peer/orderer的MSP文件夹
- csr:为一个ECert生成一个CSR
- registration section(id):register一个新的identity
- enrollment section(enrollment):enroll一个identity
- caname:连接的ca的名字
3. 配置设置
有三种对配置进行设置的方法(优先级由大到小):
- CLI
- 环境变量
- 配置文件配置文件进行设置的内容可以通过CLI或环境变量进行更改。
假如配置文件如下所示:
tls:
# Enable TLS (default: false)
enabled: false
# TLS for the client's listenting port (default: false)
certfiles:
client:
certfile: cert.pem
keyfile:可以通过环境变量更改:
export FABRIC_CA_CLIENT_TLS_CLIENT_CERTFILE=cert2.pem继而使用CLI更改:
fabric-ca-client enroll --tls.client.certfile cert3.pem4. Fabric CA Server
fabric-ca-server init -b admin:adminpwhome directory优先级如下:
- FABRIC_CA_SERVER_HOME
- FABRIC_CA_HOME
- CA_CFG_PATH
- 当前工作目录
4.1 初始化server
初始化会生成ca-cert.pem和ca-key.pem文件,也会生成一个默认的配置文件,可以在启动前对其进行更改。(若这些文件本身就存在则不用重新生成)
LDAP是disabled的时候,bootstrap identity 可以用来初始化server
fabric-ca-server init -b admin:adminpw配置文件包括一个CSR,以下是一个CSR的样例:
cn: fabric-ca-server
names:
- C: US //国家
ST: "North Carolina" //state
L: //城市或location
O: Hyperledger //组织名字
OU: Fabric //组织单位
hosts:
- host1.example.com
- localhost
ca:
expiry: 131400h
pathlength: 1如果-u 没有被指明, fabric-ca-server init命令生成一个自签名的CA证书,如果-u被指定,服务器的CA证书会被其父CA server进行签发。为了授权给父CA server,URL必须是hf. IntermediateCA值为true。fabric-ca-server init命令也会生成一个名为fabric-ca-server-config.yaml的默认配置文件在home directory中。
如果想要CA server用一个你提供的证书和密钥,必须把自己提供的文件放到属性ca.certfile和ca.keyfile所指向的位置中。
CSR可以用来定制化生成X.509证书和密钥,支持ECDSA,可以有以下几种key size的选择:
| size | ASN1 OID | Signature Algorithm |
|---|---|---|
| 256 | prime256v1 | ecdsa-with-SHA256 |
| 384 | secp384r1 | ecdsa-with-SHA384 |
| 521 | secp521r1 | ecdsa-with-SHA512 |
设置如下:
key:
algo: ecdsa
size: 2564.2 启动server
命令如下
fabric-ca-server start -b : 除非CA server被设置使用LDAP,否则它必须至少有一个pre-registered bootstrap identity用来register和enroll其他identities,上述命令中的admin和adminpw就是默认bootstrap identity的用户名和密码。
为了使CA server监听https而不是https,设置tls.enabled为true。
registry.maxenrollments用来设置相同的密码可以被重复用几次来enroll,若设置为1,则对每个enrollment ID 密码只能用一次;若设置为-1,则没有限制;若设置为0,CA server将不允许所有的identity去enroll和register。
CA server监听7054端口。
4.3 设置server集群和使用LDAP
4.3.1 设置数据库
- SQLite (default)
- PostgreSQL: 9.5.5 or later
- MySQL: 5.17.16 or later
4.3.1.1 PostgreSQL
db:
type: postgres
datasource: host=localhost port=5432 user=Username password=Password dbname=fabric_ca sslmode=verify-full其中对dbname有一些字符限制,具体可参考https://www.postgresql.org/docs/current/static/sql-syntax-lexical.html#SQL-SYNTAX-IDENTIFIERS
sslmode设置了SSL认证的类型,包括的类型,如下表所示:
| mode | description |
|---|---|
| disable | No SSL |
| require | Always SSL (skip verification) |
| verify-ca | Always SSL (verify that the certificate presented by the server was signed by a trusted CA) |
| verify-full | Same as verify-ca AND verify that the certificate presented by the server was signed by a trusted CA and the server hostname matches the one in the certificate |
如果要使用TLS,CA server配置文件中的db.tls必须被设置,如果在PostgreSQL服务器中SSL客户端认证是enabled,那么客户端的证书和密钥文件必须在db.tls.client中被指明,如下:
db:
...
tls:
enabled: true
certfiles:
- db-server-cert.pem
client:
certfile: db-client-cert.pem
keyfile: db-client-key.pem- certfiles:一个PEM编码的可信根证书文件
- certfile和keyfile:PEM编码的证书和密钥文件,用来保证CA server和PostgreSQL server的安全通信。
4.3.1.2 PostgreSQL SSL Configuration
在PostgreSQL server中配置SSL的基本操作:
- 在postgresql.conf文件中取消SSL的注释,并设置为“on”(SSL=on)。
- 将证书和密钥文件放到PostgreSQL的数据文件夹中生成自签名证书的指令https://www.postgresql.org/docs/9.5/static/ssl-tcp.html,自签名只是为了测试用,在生产环境中不能使用。
请求客户端证书:
- 将信任的CA证书放在PostgreSQL的数据文件夹的文件root.crt中。
- 在postgresql.conf中设置ssl_ca_file指向客户端的根证书。
- 在pg_hba.conf中的appropriate hostssl line,设置clientcert参数为1。
更多设置细节见https://www.postgresql.org/docs/9.4/static/libpq-ssl.html
4.3.1.3 MySQL
db:
type: mysql
datasource: root:rootpw@tcp(localhost:3306)/fabric_ca?parseTime=true&tls=custom设置参考https://dev.mysql.com/doc/refman/5.7/en/identifiers.html
若想让服务器接受’0000-00-00’为有效的日期,需要在my.cnf中找到配置选项sql_mode,并且删除NO_ZERO_DATE,并重启服务器
具体的设置选择可参考https://dev.mysql.com/doc/refman/5.7/en/sql-mode.html
若要通过TLS连接MySQL服务器,db.tls的设置参考上文PostgreSQL的设置。
4.3.1.4 MySQL SSL Configuration
在MySQL server中配置SSL的基本操作
- 打开或创建服务器的my.cnf文件,增加[mysqid] section或取消该行注释。应该指向服务器的密钥和证书,以及根CA证书。
[mysqld] ssl-ca=ca-cert.pem ssl-cert=server-cert.pem ssl-key=server-key.pem
创建服务器和客户端证书的指令如下:http://dev.mysql.com/doc/refman/5.7/en/creating-ssl-files-using-openssl.html
执行如下命令可以证实SSL是否可用:mysql> SHOW GLOBAL VARIABLES LIKE ‘have_%ssl’;
应该可以看到:
| variable_name | Value |
|---|---|
| have_openssl | YES |
| have_ssl | YES |
- 在服务器端SSL配置完成之后,下一步是创建一个有通过SSL接入MySQL服务器特权的用户。
mysql> GRANT ALL PRIVILEGES ON . TO ‘ssluser’@’%’ IDENTIFIED BY ‘password’ REQUIRE SSL; mysql> FLUSH PRIVILEGES
如果想要使用户从一个特定的IP地址接入server,可以把“%”变为特定的IP地址。
请求客户端证书
安全连接的选项和用于服务器端的选项是相似的
- ssl-ca识别CA证书,如果用到,必须和服务器端用相同的证书。
- ssl-cert识别MySQL服务器的证书。
- ssl-key识别MySQL服务器的私钥。
假设你想要用一个账户来连接,这个账户没有特殊的加密要求或是被一个包括REQUIRE SSL的GRANT statement创建的,启动MySQL服务至少需要-ssl-cert和-ssl-key选项。然后在服务设置文件中设置db.tls.certfiles属性并启动CA服务。
为了要求一个客户端证书也是被指定的,创建一个用REQUIRE X509选项的账户。然后客户端也必须明确客户端密钥和证书文件;否则,MySQL server将会拒绝连接。为了给CA server指定客户端密钥和证书文件,设置db.tls.client.certfile和db.tls.client.keyfile
4.3.2 Configuring LDAP
CA server可以从LDAP server中读取。
特别地,CA server可以和一个LDAP server连接做如下事情:
- 认证一个identity去enrollment的优先级
- 检索一个identity用于认证的属性
修改CA server配置文件的LDAP部分来配置CA server连接LDAP服务器
ldap:
# Enables or disables the LDAP client (default: false)
enabled: false
# The URL of the LDAP server
url: ://:/
userfilter: filter 其中:
- scheme: LDAP或LDAPS中的一个。
- adminDN:admin用户的名字。
- pass:admin用户的密码。
- host:LDAP服务器的hostname或IP地址。
- port:可选的端口号,ldap默认的端口号是389,ldaps默认的端口号是636。
- base:LDAP树的根,用来搜索。
- filter:登录名的过滤器,例如:(uid=%s)用来搜索用用户名登陆的用户,(email=%s)用来搜索用邮箱登陆的用户。
以下是一个配置样例:
ldap:
enabled: true
url: ldap://cn=admin,dc=example,dc=org:admin@localhost:10389/dc=example,dc=org
userfilter: (uid=%s)OpenLDAP server的docker镜像在https://github.com/osixia/docker-openldap中。FABRIC_CA/scripts/run-ldap-tests中的脚本是用来启动OpenLDAP的docker镜像的,对它进行配置,并运行FABRIC_CA/cli/server/ldap/ldap_test.go这个LDAP测试脚本,并停止OpenLDAP服务器。
当LDAP被配置好之后,enrollment过程如下:
- CA client或client SDK发送一个enrollment请求,这个请求带一个basic authorization header。
- CA server接收了这个enrollment请求,对authorization header中的identity name和password进行解码,用配置文件中的“userfilter”来从identity name中查找DN(Distinquished Name),然后用identity的密码请求一个LDAP bind,如果LDAP bind成功了,enrollment过程就被授权了,可以执行了。
当LDAP被配置好之后,提取属性(attribute retrieval)的过程如下:
- client SDK给CA server发送一个对一批tcerts的请求用一个或多个attributes。
- CA server接收这个tcert请求,并做如下:
- 从authorization header的token(验证过token之后)中提取enrollment ID。
- 向LDAP服务器发起一个LDAP搜索,查找tcert请求中的所有属性名。
- 将属性值放在tcert中。
4.3.3 设置一个集群
配置Haproxy去平衡CA server集群中各个server的负载。确保更改hostname和port来对应CA server的设置。
haproxy.conf
global
maxconn 4096
daemon
defaults
mode http
maxconn 2000
timeout connect 5000
timeout client 50000
timeout server 50000
listen http-in
bind *:7054
balance roundrobin
server server1 hostname1:port
server server2 hostname2:port
server server3 hostname3:port如果要用TLS,需要用mode tcp
4.3.4 设置多个CAs
fabric-ca server默认是一个单独的CA。可以通过cafiles和cacount配置选项来增加其他的CA,每一个CA都有他自己的home directory。
4.3.4.1 cacount:
cacount可以直接设置additional CAs,他们的home directory和server directory相关,如下:
--<Server Home>
|--ca
|--ca1
|--ca2每个额外的CA将会在他的home directory里生成一个默认的配置文件,其中包括唯一的CA name。
如下命令来启动2个CA:
fabric-ca-server start -b admin:adminpw --cacount 24.3.4.2 cafiles:
配置的优先级如下:
- CA Configuration file
- Default CA CLI flags
- Default CA Environment variables
- Default CA Configuration file
一个CA的配置文件至少包括下述内容:
ca:
# Name of this CA
name:
csr:
cn: 可以设置文档结构如下:
--<Server Home>
|--ca
|--ca1
|-- fabric-ca-config.yaml
|--ca2
|-- fabric-ca-config.yaml如下命令可以启动两个定制化CA实例:
fabric-ca-server start -b admin:adminpw --cafiles ca/ca1/fabric-ca-config.yaml
--cafiles ca/ca2/fabric-ca-config.yaml4.3.5 enroll一个intermediate CA
为了给intermediate CA创建一个CA签名证书,intermediate CA必须enroll with一个父CA,就像一个fabric-ca-client必须enroll with一个CA。通过使用 -u指定父CA的URL来做这件事,如下所示:
fabric-ca-server start -b admin:adminpw -u http://:@: 与这个identity相关的enrollment ID的”hf.intermediateCA”属性值一定为“true”,颁发证书的CN(common name)必须设置为enrollment ID。
5. Fabric CA Client
home directory设置的优先级如下所示:
- 环境变量FABRIC_CA_CLIENT_HOME
- 环境变量FABRIC_CA_HOME
- 环境变量CA_CFG_PATH
-$HOME/.fabric-ca-client
5.1 enroll the bootstrap identity
可定制化CSR部分,其中csr.cn必须是bootstrap identity的ID。
csr:
cn: <>
key:
algo: ecdsa
size: 256
names:
- C: US
ST: North Carolina
L:
O: Hyperledger Fabric
OU: Fabric CA
hosts:
- <>
ca:
pathlen:
pathlenzero:
expiry: 然后运行fabric-ca-client enroll命令去enroll这个identity。如下命令向运行在本地端口7054的CA server enroll一个ID为admin密码为adminpw的identity。
export FABRIC_CA_CLIENT_HOME=$HOME/fabric-ca/clients/admin
fabric-ca-client enroll -u http://admin:adminpw@localhost:7054这个enroll命令存储一个ECert、相应的私钥和CA证书链PEM文件在CA Client的msp子文件夹中。
5.2 register a new identity
在register期间,CA server会做两个授权检查:
- 调用者要register的身份必须是其“hf.Registrar.Roles”属性中所指明的身份中的一个。例如调用者的“hf.Registrar.Roles”属性值为“peer,app,user”,那么他不能register orderer类型的identity。
- 调用者identity的从属关系必须等于要register时候的从属关系的前缀。例如,一个调用者的从属关系是“a.b”,那么他可以register一个拥有”a.b.c”的identity,但不能是“a.c”。
下文的命令用admin identity去register一个新的identity,他的enrollment id是admin2,类型是user,从属关系是org1.department1,hf.Revoker属性的值为true,foo属性的值为bar。
export FABRIC_CA_CLIENT_HOME=$HOME/fabric-ca/clients/admin
fabric-ca-client register --id.name admin2 --id.type user --id.affiliation org1.department1 --id.attrs 'hf.Revoker=true,foo=bar'CA server会返回一个密码,用于这个identity去enroll。也允许一个管理员去register一个identity,然后将这个identity对应的enrollment ID和密码给其他人去enroll。
对多个属性进行设置(感觉原文写错了)
fabric-ca-client register -d --id.name admin2 --id.type user --id.affiliation org1.department1 --id.attrs '"hf.Registrar.Roles=peer,user",hf.Revoker=true'或
fabric-ca-client register -d --id.name admin2 --id.type user --id.affiliation org1.department1 --id.attrs '"hf.Registrar.Roles=peer,user"' --id.attrs hf.Revoker=true若配置文件如下所示:
id:
name:
type: user
affiliation: org1.department1
maxenrollments: -1
attributes:
- name: hf.Revoker
value: true
- name: anotherAttrName
value: anotherAttrValue使用命令:
export FABRIC_CA_CLIENT_HOME=$HOME/fabric-ca/clients/admin
fabric-ca-client register --id.name admin3则会register一个name是admin3、其他属性由配置文件决定的identity。
正在注册的identity的maxenrollments的值一定小于等于这个CA的maxenrollments。如果将其设置为0或不设置,则和CA的maxenrollments值一样。
5.3 register and enroll a peer identity
- register
export FABRIC_CA_CLIENT_HOME=$HOME/fabric-ca/clients/admin
fabric-ca-client register --id.name peer1 --id.type peer --id.affiliation org1.department1 --id.secret peer1pwenrollment ID=peer1 password会打印在屏幕上。
- enroll
export FABRIC_CA_CLIENT_HOME=$HOME/fabric-ca/clients/peer1
fabric-ca-client enroll -u http://peer1:peer1pw@localhost:7054 -M $FABRIC_CA_CLIENT_HOME/msp-M选项指明密钥和证书的存放路径。
5.4 从另一个CA server上拿到CA证书链
一般地,MSP文件夹中的证书文件夹必须包含其他证书认证中心的证书认证链,来代表这个peer是可信的。以下命令启动了另一个CA server,这个代表完全分开的一个根信任,并且被区块链中的不同成员管理。
export FABRIC_CA_SERVER_HOME=$HOME/ca2
fabric-ca-server start -b admin:ca2pw -p 7055 -n CA2以下命令将安装CA2的证书链到peer1的MSP文件夹中:
export FABRIC_CA_CLIENT_HOME=$HOME/fabric-ca/clients/peer1
fabric-ca-client getcacert -u http://localhost:7055 -M $FABRIC_CA_CLIENT_HOME/msp5.5 Reenroll an identity
假如你的证书期满终止了,可以重新enroll一个:
export FABRIC_CA_CLIENT_HOME=$HOME/fabric-ca/clients/peer1
fabric-ca-client reenroll5.5 撤销一个证书或一个identity
- 撤销一个identity会撤销他的所有证书,并阻止他再得到新的证书,撤销一个证书只是使一个证书无效。
- 撤销者的从属关系是orgs.org1可以撤销从属关系是orgs.org1和orgs.org1.department1的identity,但不能撤销orgs.org1的identity。
命令如下:
fabric-ca-client revoke -e <enrollment_id> -r <reason>-r标志可以有如下选择:
- unspecified
- keycompromise
- cacompromise
- affiliationchange
- superseded
- cessationofoperation
- certificatehold
- removefromcrl
- privilegewithdrawn
- aacompromise
例子:超级用户可以撤销peer1这个identity
export FABRIC_CA_CLIENT_HOME=$HOME/fabric-ca/clients/admin
fabric-ca-client revoke -e peer1
一个属于某个identity的证书可以通过指定他的AKI(Authority Key Identifier)和序列号来撤销。
fabric-ca-client revoke -a xxx -s yyy -r <reason>例如,可以用openssl 命令来得到AKI和序列号,然后将他们传入revoke命令来撤销证书:
serial=$(openssl x509 -in userecert.pem -serial -noout | cut -d "=" -f 2)
aki=$(openssl x509 -in userecert.pem -text | awk '/keyid/ {gsub(/ *keyid:|:/,"",$1);print tolower($0)}')
fabric-ca-client revoke -s $serial -a $aki -r affiliationchange6. 使用TLS
在fabric-ca-client-config.yaml中有如下配置:
tls:
# Enable TLS (default: false)
enabled: true
certfiles:
- root.pem
client:
certfile: tls_client-cert.pem
keyfile: tls_client-key.pemcertfiles选项中是被客户端信任的根证书,其实就是server的home directory中ca-cert.pem中的根证书。( This will typically just be the root Fabric CA server’s certificate found in the server’s home directory in the ca-cert.pem file.)
client选项只有在server中配置了相同的TLS才用。
7. 和特定CA contact
客户端请求若没有指明CA的名字,那么就直接发往默认CA,CA名字可以通过如下命令指明:
fabric-ca-client enroll -u http://admin:adminpw@localhost:7054 --caname ================================================================
转载请说明出处
原文链接