ModSecurity简介
ModSecurity是一个开源的、跨平台的Web应用防火墙(WAF),被称为WAF界的“瑞士军刀”。它可以通过检查Web服务接收到的数据,以及发送出去的数据来对网站进行安全防护。
ModSecurity有以下作用:
- SQL Injection (SQLi):阻止SQL注入
- Cross Site Scripting (XSS):阻止跨站脚本攻击
- Local File Inclusion (LFI):阻止利用本地文件包含漏洞进行攻击
- Remote File Inclusione(RFI):阻止利用远程文件包含漏洞进行攻击
- Remote Code Execution (RCE):阻止利用远程命令执行漏洞进行攻击
- PHP Code Injectiod:阻止PHP代码注入
- HTTP Protocol Violations:阻止违反HTTP协议的恶意访问
- HTTPoxy:阻止利用远程代理感染漏洞进行攻击
- Sshllshock:阻止利用Shellshock漏洞进行攻击
- Session Fixation:阻止利用Session会话ID不变的漏洞进行攻击
- Scanner Detection:阻止黑客扫描网站
- Metadata/Error Leakages:阻止源代码/错误信息泄露
- Project Honey Pot Blacklist:蜜罐项目黑名单
- GeoIP Country Blocking:根据判断IP地址归属地来进行IP阻断
安装配置 Nginx
安装Nginx
yum install gcc-c++
yum install -y pcre pcre-devel
yum install -y zlib zlib-devel
yum install -y openssl openssl-devel
如果出现以下错误:
No match for argument: pcre-devel
使用以下命令后重新安装即可
yum install https://dl.fedoraproject.org/pub/epel/epel-release-latest-8.noarch.rpm
继续安装
wget http://nginx.org/download/nginx-1.16.1.tar.gz
tar -xvf nginx-1.16.1.tar.gz -C /usr/local/src/
cd /usr/local/src/nginx-1.16.1
./configure
make && make install
编写Nginx启动脚本
vim /usr/lib/systemd/system/nginx.service
[Unit]
Description=nginx - high performance web server
After=network-online.target remote-fs.target nss-lookup.target
[Service]
Type=forking
PIDFile=/usr/local/nginx/logs/nginx.pid
ExecStart=/usr/local/nginx/sbin/nginx -c /usr/local/nginx/conf/nginx.conf
ExecReload=/bin/kill -s HUP $MAINPID
ExecStop=/bin/kill -s TERM $MAINPID
[Install]
WantedBy=multi-user.target
修改环境PATH
vim /etc/profile.d/nginx.sh
PATH=/usr/local/nginx/sbin:$PATH
source /etc/profile
安装libmodsecurity
安装依赖
yum -y install gcc-c++ flex bison yajl yajl-devel curl-devel curl GeoIP-devel doxygen zlib-devel libtool git autoconf automake libxml2-devel zlib-devel libgo-devel openssl-devel
cd /usr/local/src
# --depth用于指定克隆深度,为1即表示只克隆最近一次commit
# 克隆指定的分支: git clone -b 分支名 仓库地址
# --single-branch, 只检查一个branch,要么是默认的master,要么是-b new_branch指定的new_branch
git clone --depth 1 -b v3/master --single-branch https://github.com/SpiderLabs/ModSecurity
cd ModSecurity
git submodule init
git submodule update
./build.sh
./configure
make && make install
配置ModSecurity
下载ModSecurity和Nginx的连接器
cd /usr/local/src/
git clone --depth 1 https://github.com/SpiderLabs/ModSecurity-nginx.git
cd nginx-1.16.1/
./configure --add-dynamic-module=/usr/local/src/ModSecurity-nginx
make modules
make install
cp objs/ngx_http_modsecurity_module.so '/usr/local/nginx/modules/ngx_http_modsecurity_module.so'
加载Nginx ModSecurity
vim /usr/local/nginx/conf/nginx.conf
# 在顶级区间内加上
load_module /usr/local/nginx/modules/ngx_http_modsecurity_module.so;
nginx -t
下载默认的配置文件
cd /usr/local/src
wget https://raw.githubusercontent.com/SpiderLabs/ModSecurity/v3/master/modsecurity.conf-recommended
mv modsecurity.conf-recommended /usr/local/nginx/conf/modsecurity.conf
vim /usr/local/nginx/conf/modsecurity.conf
# 修改SecRuleEngine
SecRuleEngine On
配置核心规则
git clone https://github.com/SpiderLabs/owasp-modsecurity-crs.git
cp -R owasp-modsecurity-crs/rules /usr/local/nginx/conf/
cp owasp-modsecurity-crs/crs-setup.conf.example /usr/local/nginx/conf/crs-setup.conf
vim /usr/local/nginx/conf/modsecurity.conf
# 在文件最上添加内容
include crs-setup.conf
include rules/*.conf
修改nginx的配置文件
vim /usr/local/nginx/conf/nginx.conf
# 放在server下的话,就是全局,如果只要某一个的话,可以放在location中
modsecurity on;
modsecurity_rules_file /usr/local/nginx/conf/modsecurity.conf;
nginx -t
部分报错
# 报错:
nginx: [emerg] "modsecurity_rules_file" directive Rules error. File: /usr/local/nginx/conf/modsecurity.conf. Line: 2. Column: 20. rules/*.conf: Not able to open file. Looking at: 'rules/*.conf', 'rules/*.conf', '/usr/local/nginx/conf/rules/*.conf', '/usr/local/nginx/conf/rules/*.conf'. in /usr/local/nginx/conf/nginx.conf:41
# 重新执行,输入yes后回车
cp owasp-modsecurity-crs/crs-setup.conf.example /usr/local/nginx/conf/crs-setup.conf
nginx -t
systemctl restart nginx
# 报错:
nginx: [emerg] "modsecurity_rules_file" directive Rules error. File: /usr/local/nginx/conf/rules/REQUEST-910-IP-REPUTATION.conf. Line: 75. Column: 22. This version of ModSecurity was not compiled with GeoIP or MaxMind support. in /usr/local/nginx/conf/nginx.conf:39
nginx: configuration file /usr/local/nginx/conf/nginx.conf test failed
# 这里需要查看具体错误的配置文件,然后删除,简单粗暴
rm -f REQUEST-910-IP-REPUTATION.conf
nginx -t
systemctl restart nginx
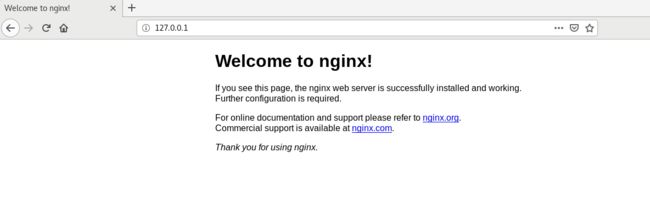
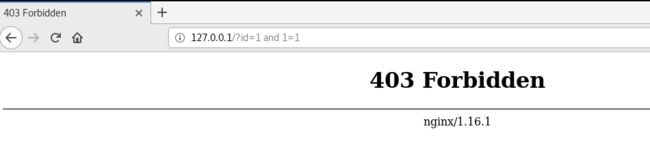
结果
正常情况没有拦截
添加参数/?id =1 and 1=1, 成功拦截
至此环境搭键完成,学习于互联网,但是教程略有报错,解决后记录在此
更多操作可移步www.modsecurity.org 或 www.modsecurity.cn