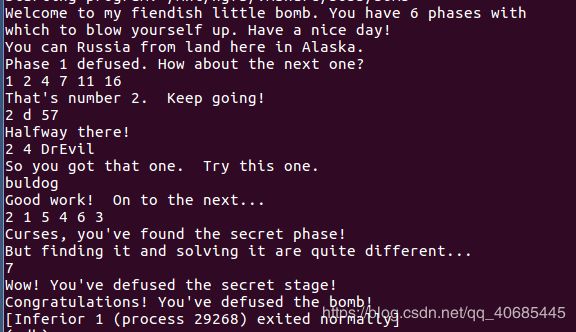
深入理解计算机系统bomb炸弹实验
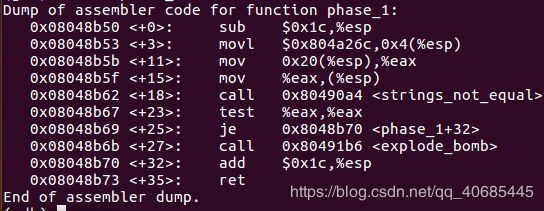
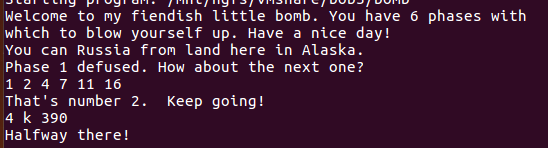
1. You can Russia from land here in Alaska.
x /s 0x804a26c
0x804a26c: "You can Russia from land here in Alaska.”
You can Russia from land here in Alaska.
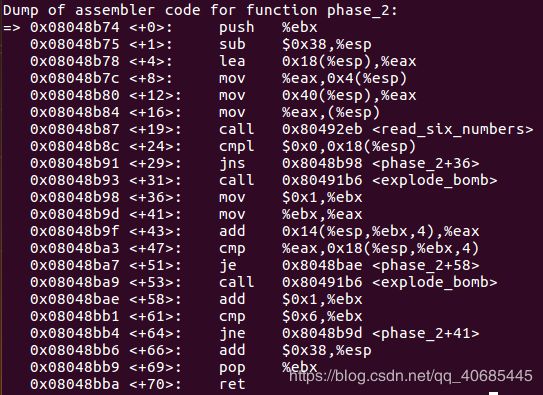
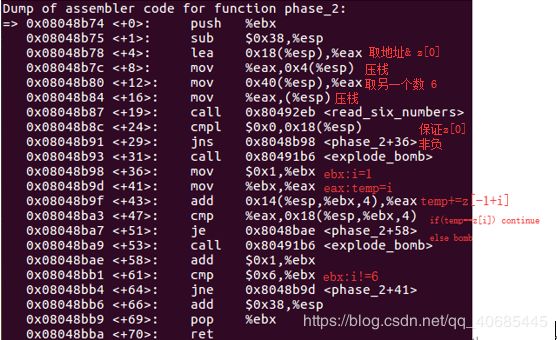
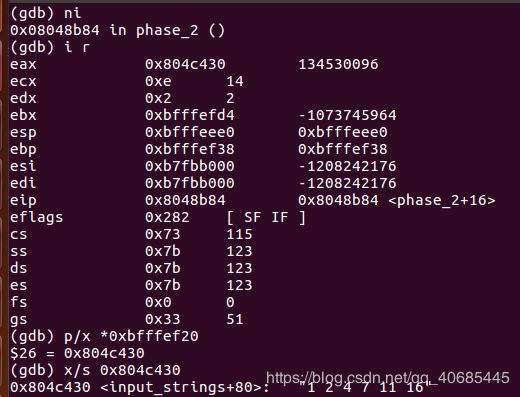
2. 1 2 4 7 11 16
(黑框为取readline()中读取的字符串的地址)
得到关系式子 z[i]=z[i-1]+i(i=1,2,3,4,5) z[0]>=0
满足该式的即为答案
1 2 4 7 11 16
3. 2 d 57
输入格式为:int i char int a
0x08048bbb <+0>: sub $0x3c,%esp //开辟空间
0x08048bbe <+3>: lea 0x28(%esp),%eax //一个输入地址
0x08048bc2 <+7>: mov %eax,0x10(%esp) //压入esp+16
0x08048bc6 <+11>: lea 0x2f(%esp),%eax //与0x28差八个字节,1个 int
0x08048bca <+15>: mov %eax,0xc(%esp) //压入esp+12
0x08048bce <+19>: lea 0x24(%esp),%eax //esp+24<=7 否则bomb
0x08048bd2 <+23>: mov %eax,0x8(%esp) //压入esp+8
0x08048bd6 <+27>: movl $0x804a2be,0x4(%esp) //“%d %c %d” 对应esp+24、+2f、+28
0x08048bde <+35>: mov 0x40(%esp),%eax //此为readline输入
0x08048be2 <+39>: mov %eax,(%esp) //压入五个参数
0x08048be5 <+42>: call 0x8048870 <__isoc99_sscanf@plt> //读入函数 i为非int时返回eax为0 a为非int时返回2
0x08048bea <+47>: cmp $0x2,%eax //不大于2则爆炸
0x08048bed <+50>: jg 0x8048bf4
0x08048bef <+52>: call 0x80491b6
0x08048bf4 <+57>: cmpl $0x7,0x24(%esp) //大于7则跳+317爆炸 ja无符号,所以限定i非负
0x08048bf9 <+62>: ja 0x8048cf8
0x08048bff <+68>: mov 0x24(%esp),%eax
0x08048c03 <+72>: jmp *0x804a2d0(, %eax,4) //跳到*(0x80..+4i)
0x08048c0a <+79>: mov $0x69,%eax
0x08048c0f <+84>: cmpl $0x23c,0x28(%esp)
0x08048c17 <+92>: je 0x8048d02
0x08048c1d <+98>: call 0x80491b6
0x08048c22 <+103>: mov $0x69,%eax
0x08048c27 <+108>: jmp 0x8048d02
0x08048c2c <+113>: mov $0x64,%eax
0x08048c31 <+118>: cmpl $0x1b0,0x28(%esp)
0x08048c39 <+126>: je 0x8048d02
0x08048c3f <+132>: call 0x80491b6
0x08048c44 <+137>: mov $0x64,%eax
0x08048c49 <+142>: jmp 0x8048d02
0x08048c4e <+147>: mov $0x64,%eax
0x08048c53 <+152>: cmpl $0x39,0x28(%esp) //比较esp+28与0x39
0x08048c58 <+157>: je 0x8048d02
0x08048c5e <+163>: call 0x80491b6
0x08048c63 <+168>: mov $0x64,%eax
0x08048c68 <+173>: jmp 0x8048d02
0x08048c6d <+178>: mov $0x65,%eax
0x08048c72 <+183>: cmpl $0x15c,0x28(%esp)
0x08048c7a <+191>: je 0x8048d02
0x08048c80 <+197>: call 0x80491b6
0x08048c85 <+202>: mov $0x65,%eax
0x08048c8a <+207>: jmp 0x8048d02
0x08048c8c <+209>: mov $0x6b,%eax
0x08048c91 <+214>: cmpl $0x186,0x28(%esp)
0x08048c99 <+222>: je 0x8048d02
0x08048c9b <+224>: call 0x80491b6
0x08048ca0 <+229>: mov $0x6b,%eax
0x08048ca5 <+234>: jmp 0x8048d02
0x08048ca7 <+236>: mov $0x6d,%eax
0x08048cac <+241>: cmpl $0x330,0x28(%esp)
0x08048cb4 <+249>: je 0x8048d02
0x08048cb6 <+251>: call 0x80491b6
0x08048cbb <+256>: mov $0x6d,%eax
0x08048cc0 <+261>: jmp 0x8048d02
0x08048cc2 <+263>: mov $0x77,%eax
0x08048cc7 <+268>: cmpl $0x1bf,0x28(%esp)
0x08048ccf <+276>: je 0x8048d02
0x08048cd1 <+278>: call 0x80491b6
0x08048cd6 <+283>: mov $0x77,%eax
0x08048cdb <+288>: jmp 0x8048d02
0x08048cdd <+290>: mov $0x6a,%eax
0x08048ce2 <+295>: cmpl $0x1f4,0x28(%esp)
0x08048cea <+303>: je 0x8048d02
0x08048cec <+305>: call 0x80491b6
0x08048cf1 <+310>: mov $0x6a,%eax
0x08048cf6 <+315>: jmp 0x8048d02
0x08048cf8 <+317>: call 0x80491b6
0x08048cfd <+322>: mov $0x65,%eax
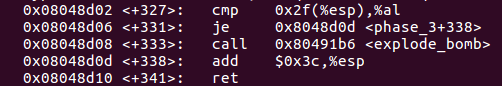
0x08048d02 <+327>: cmp 0x2f(%esp),%al
0x08048d06 <+331>: je 0x8048d0d
0x08048d08 <+333>: call 0x80491b6
0x08048d0d <+338>: add $0x3c,%esp
0x08048d10 <+341>: ret
一个case语句i取值为0~7:
0 i 572
1 d 432
2 d 57
3 e 348
4 k 390
5 m 816
6 w 447
7 j 500
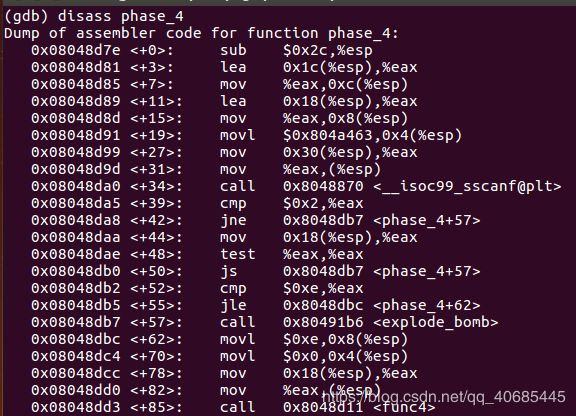
4. 2 4 DrEvil(隐藏关卡条件)
读入数据:int a int b =4
0x08048d7e <+0>: sub $0x2c,%esp
0x08048d81 <+3>: lea 0x1c(%esp),%eax //存入一个int b
0x08048d85 <+7>: mov %eax,0xc(%esp)
0x08048d89 <+11>: lea 0x18(%esp),%eax //存入一个int a
0x08048d8d <+15>: mov %eax,0x8(%esp)
0x08048d91 <+19>: movl $0x804a463,0x4(%esp) //%d %d
0x08048d99 <+27>: mov 0x30(%esp),%eax //readline读入
0x08048d9d <+31>: mov %eax,(%esp)
0x08048da0 <+34>: call 0x8048870 <__isoc99_sscanf@plt> //读入函数 均为int时返回2
0x08048da5 <+39>: cmp $0x2,%eax //不为2则跳+57爆炸
0x08048da8 <+42>: jne 0x8048db7
0x08048daa <+44>: mov 0x18(%esp),%eax //eax=a
0x08048dae <+48>: test %eax,%eax //测试寄存器是否为空
0x08048db0 <+50>: js 0x8048db7
0x08048db2 <+52>: cmp $0xe,%eax //a<=14,否则bomb
0x08048db5 <+55>: jle 0x8048dbc
0x08048db7 <+57>: call 0x80491b6
0x08048dbc <+62>: movl $0xe,0x8(%esp) //传参14
0x08048dc4 <+70>: movl $0x0,0x4(%esp) //传参0
0x08048dcc <+78>: mov 0x18(%esp),%eax //eax=a
0x08048dd0 <+82>: mov %eax,(%esp) //传参
0x08048dd3 <+85>: call 0x8048d11
0x08048dd8 <+90>: cmp $0x4,%eax //返回值不为4则bomb
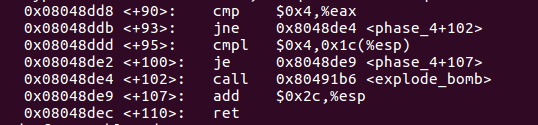
0x08048ddb <+93>: jne 0x8048de4
0x08048ddd <+95>: cmpl $0x4,0x1c(%esp) //b=4,否则bomb
0x08048de2 <+100>: je 0x8048de9
0x08048de4 <+102>: call 0x80491b6
0x08048de9 <+107>: add $0x2c,%esp
0x08048dec <+110>: ret
猜想1:是个二分查找的函数。返回值为查找到该数所需要的调用次数
实际上是个在0到14中二分查找a的一个函数。其中当向小查找时有eax=2eax,向大查找时有eax=2eax+1。且初始值eax=0
(gdb) disass func4
Dump of assembler code for function func4:
0x08048d11 <+0>: sub $0x1c,%esp
0x08048d14 <+3>: mov %ebx,0x14(%esp)
0x08048d18 <+7>: mov %esi,0x18(%esp)
0x08048d1c <+11>: mov 0x20(%esp),%edx //等价于phase_4中的esp
0x08048d20 <+15>: mov 0x24(%esp),%eax //等价于esp+4
0x08048d24 <+19>: mov 0x28(%esp),%ebx //等价于esp+8
故edx=a eax=0 ebx=14
0x08048d28 <+23>: mov %ebx,%ecx //ecx=14
0x08048d2a <+25>: sub %eax,%ecx //ecx=14-0 ecx存放长度
0x08048d2c <+27>: mov %ecx,%esi //esi=14
0x08048d2e <+29>: shr $0x1f,%esi //取esi最后一位 此时esi=0 为是否奇偶数
0x08048d31 <+32>: add %esi,%ecx //ecx=14+0
0x08048d33 <+34>: sar %ecx //默认是右移1位 ecx=7
0x08048d35 <+36>: add %eax,%ecx //ecx=7+0 ecx存放中间位置
0x08048d37 <+38>: cmp %edx,%ecx //edx=a ecx=7
0x08048d39 <+40>: jle 0x8048d52
0x08048d3b <+42>: sub $0x1,%ecx
0x08048d3e <+45>: mov %ecx,0x8(%esp) //7-1
0x08048d42 <+49>: mov %eax,0x4(%esp) //0
0x08048d46 <+53>: mov %edx,(%esp) //a
0x08048d49 <+56>: call 0x8048d11
0x08048d4e <+61>: add %eax,%eax //2eax
0x08048d50 <+63>: jmp 0x8048d72
0x08048d52 <+65>: mov $0x0,%eax //eax=0
0x08048d57 <+70>: cmp %edx,%ecx //edx=a ecx=7
0x08048d59 <+72>: jge 0x8048d72
0x08048d5b <+74>: mov %ebx,0x8(%esp) //14
0x08048d5f <+78>: add $0x1,%ecx
0x08048d62 <+81>: mov %ecx,0x4(%esp) //7+1
0x08048d66 <+85>: mov %edx,(%esp) //a
0x08048d69 <+88>: call 0x8048d11
0x08048d6e <+93>: lea 0x1(%eax,%eax,1),%eax //2eax+1
0x08048d72 <+97>: mov 0x14(%esp),%ebx //ebx存终止值
0x08048d76 <+101>: mov 0x18(%esp),%esi //esi存开始值
0x08048d7a <+105>: add $0x1c,%esp
0x08048d7d <+108>: ret
2 4
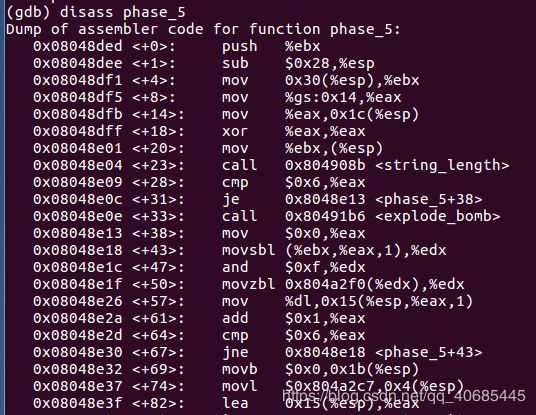
5.buldog
0x08048ded <+0>: push %ebx
0x08048dee <+1>: sub $0x28,%esp
0x08048df1 <+4>: mov 0x30(%esp),%ebx
0x08048df5 <+8>: mov %gs:0x14,%eax //将某个int写入eax
0x08048dfb <+14>: mov %eax,0x1c(%esp)
0x08048dff <+18>: xor %eax,%eax //将eax赋值为0,因为xor效率比mov高
0x08048e01 <+20>: mov %ebx,(%esp) //将esp+30 readline地址传参
0x08048e04 <+23>: call 0x804908b
0x08048e09 <+28>: cmp $0x6,%eax
0x08048e0c <+31>: je 0x8048e13
0x08048e0e <+33>: call 0x80491b6
0x08048e13 <+38>: mov $0x0,%eax //eax=0
0x08048e18 <+43>: movsbl (%ebx,%eax,1),%edx //edx=*(ebx+eax) char所以乘1 猜测eax是计数器i
0x08048e1c <+47>: and $0xf,%edx //只要edx低4位
0x08048e1f <+50>: movzbl 0x804a2f0(%edx),%edx // maduiersnfotvbyl 0x804a2f0里面存的16个字符
0x08048e26 <+57>: mov %dl,0x15(%esp,%eax,1) //将之存起来
0x08048e2a <+61>: add $0x1,%eax
0x08048e2d <+64>: cmp $0x6,%eax
0x08048e30 <+67>: jne 0x8048e18
//该循环依据输入字符的低4位二进制选出另外的字符,然后比较是否一致
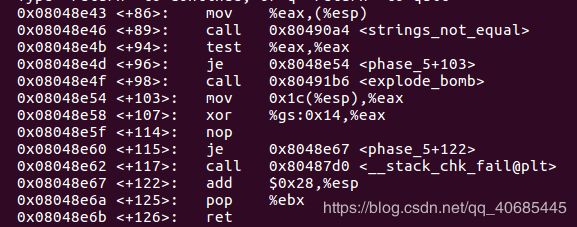
0x08048e32 <+69>: movb $0x0,0x1b(%esp)
0x08048e37 <+74>: movl $0x804a2c7,0x4(%esp) //devils
0x08048e3f <+82>: lea 0x15(%esp),%eax
0x08048e43 <+86>: mov %eax,(%esp)
0x08048e46 <+89>: call 0x80490a4
0x08048e4b <+94>: test %eax,%eax
0x08048e4d <+96>: je 0x8048e54
0x08048e4f <+98>: call 0x80491b6
0x08048e54 <+103>: mov 0x1c(%esp),%eax
0x08048e58 <+107>: xor %gs:0x14,%eax
0x08048e5f <+114>: nop
0x08048e60 <+115>: je 0x8048e67
0x08048e62 <+117>: call 0x80487d0 <__stack_chk_fail@plt>
0x08048e67 <+122>: add $0x28,%esp
0x08048e6a <+125>: pop %ebx
0x08048e6b <+126>: ret
分析:
0x804a2f0地址中所存的字符数组
| 0 |
1 |
2 |
3 |
4 |
5 |
6 |
7 |
| m |
a |
d |
u |
i |
e |
r |
s |
| 8 |
9 |
a |
b |
c |
d |
e |
f |
| n |
f |
o |
t |
v |
b |
y |
l |
字母a到z对应的16进制数范围是0x61~0x7a
| 需要翻译出的字符串 |
d |
e |
v |
i |
l |
s |
| 对应上表所需的序号 |
2 |
5 |
c |
4 |
f |
7 |
| 可以的字符 |
b |
e/u |
l |
d/t |
o |
g |
最后一栏的任意字符组合均可即:
beldog
beltog
buldog
bultog
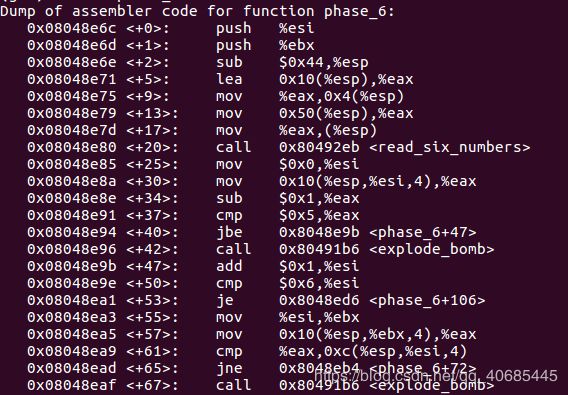
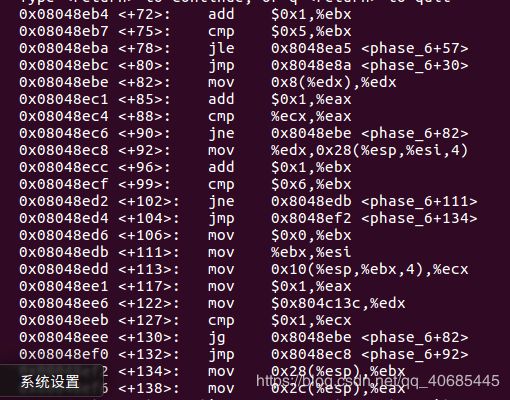
6.2 1 5 4 6 3
0x08048e6c <+0>: push %esi
0x08048e6d <+1>: push %ebx
0x08048e6e <+2>: sub $0x44,%esp
0x08048e71 <+5>: lea 0x10(%esp),%eax
0x08048e75 <+9>: mov %eax,0x4(%esp)
0x08048e79 <+13>: mov 0x50(%esp),%eax //readline()
0x08048e7d <+17>: mov %eax,(%esp)
0x08048e80 <+20>: call 0x80492eb
0x08048e85 <+25>: mov $0x0,%esi //esi做计数器i 遍历六个数字
以下两重循环确保每个数在1~6的范围且均不相同
0x08048e8a <+30>: mov 0x10(%esp,%esi,4),%eax
0x08048e8e <+34>: sub $0x1,%eax //z[i]减1,即每个数在1~6的范围
0x08048e91 <+37>: cmp $0x5,%eax
0x08048e94 <+40>: jbe 0x8048e9b
0x08048e96 <+42>: call 0x80491b6
0x08048e9b <+47>: add $0x1,%esi
0x08048e9e <+50>: cmp $0x6,%esi
0x08048ea1 <+53>: je 0x8048ed6
0x08048ea3 <+55>: mov %esi,%ebx //相当于另一个计数器j=i 两重循环
0x08048ea5 <+57>: mov 0x10(%esp,%ebx,4),%eax //还是z[i]
0x08048ea9 <+61>: cmp %eax,0xc(%esp,%esi,4) //z[i+1]与z[i]相等则bomb
0x08048ead <+65>: jne 0x8048eb4
0x08048eaf <+67>: call 0x80491b6
0x08048eb4 <+72>: add $0x1,%ebx
0x08048eb7 <+75>: cmp $0x5,%ebx //j<=5
0x08048eba <+78>: jle 0x8048ea5
0x08048ebc <+80>: jmp 0x8048e8a
0x08048ebe <+82>: mov 0x8(%edx),%edx //edx=*(edx+8) //0x804c148 0x804c154 0x804c160 0x804c16c 0x804c178
0x08048ec1 <+85>: add $0x1,%eax //eax+=1
0x08048ec4 <+88>: cmp %ecx,%eax //eax与z[i]相等才跳出
0x08048ec6 <+90>: jne 0x8048ebe
0x08048ec8 <+92>: mov %edx,0x28(%esp,%esi,4) //把这个数补到输入的数后面 若z[i]为1后面直接是0x804c13c
0x08048ecc <+96>: add $0x1,%ebx
0x08048ecf <+99>: cmp $0x6,%ebx
0x08048ed2 <+102>: jne 0x8048edb
0x08048ed4 <+104>: jmp 0x8048ef2
0x08048ed6 <+106>: mov $0x0,%ebx //esi=6
0x08048edb <+111>: mov %ebx,%esi //esi=0
0x08048edd <+113>: mov 0x10(%esp,%ebx,4),%ecx //取z[i]
0x08048ee1 <+117>: mov $0x1,%eax
0x08048ee6 <+122>: mov $0x804c13c,%edx
0x08048eeb <+127>: cmp $0x1,%ecx //若z[i]>1 则跳
0x08048eee <+130>: jg 0x8048ebe
0x08048ef0 <+132>: jmp 0x8048ec8
猜测是一个数组赋值给另一个数组
0x08048ef2 <+134>: mov 0x28(%esp),%ebx //z[6+0]
0x08048ef6 <+138>: mov 0x2c(%esp),%eax //z[6+1]
0x08048efa <+142>: mov %eax,0x8(%ebx)
0x08048efd <+145>: mov 0x30(%esp),%edx //z[6+2]
0x08048f01 <+149>: mov %edx,0x8(%eax)
0x08048f04 <+152>: mov 0x34(%esp),%eax //z[6+3]
0x08048f08 <+156>: mov %eax,0x8(%edx)
0x08048f0b <+159>: mov 0x38(%esp),%edx //z[6+4]
0x08048f0f <+163>: mov %edx,0x8(%eax)
0x08048f12 <+166>: mov 0x3c(%esp),%eax //z[6+5]
0x08048f16 <+170>: mov %eax,0x8(%edx)
0x08048f19 <+173>: movl $0x0,0x8(%eax)
0x08048f20 <+180>: mov $0x5,%esi
0x08048f25 <+185>: mov 0x8(%ebx),%eax //ebx=z[6+0] eax=z[6+1]
0x08048f28 <+188>: mov (%eax),%edx //edx=*z[6+1]
0x08048f2a <+190>: cmp %edx,(%ebx) //(ebx)=*z[6+0] 即*z[6+i-1]<=*z[6+i],否则bomb
0x08048f2c <+192>: jle 0x8048f33
0x08048f2e <+194>: call 0x80491b6
0x08048f33 <+199>: mov 0x8(%ebx),%ebx
0x08048f36 <+202>: sub $0x1,%esi //esi由5到1
0x08048f39 <+205>: jne 0x8048f25
0x08048f3b <+207>: add $0x44,%esp
0x08048f3e <+210>: pop %ebx
0x08048f3f <+211>: pop %esi
0x08048f40 <+212>: ret
| 16进制地址 |
0x804c13c |
0x804c148 |
0x804c154 |
0x804c160 |
0x804c16c |
0x804c178 |
| 排序 |
1 |
2 |
3 |
4 |
5 |
6 |
| 地址下的数值 |
272 |
68 |
914 |
503 |
421 |
887 |
| 前一个应小于后一个 |
2 |
1 |
5 |
4 |
6 |
3 |
2 1 5 4 6 3
7. 7
0x0804933b <+0>: sub $0x8c,%esp
0x08049341 <+6>: mov %gs:0x14,%eax //传了一个int给eax
0x08049347 <+12>: mov %eax,0x7c(%esp) //将上面的int存入esp+0x7c
0x0804934b <+16>: xor %eax,%eax //eax=0
0x0804934d <+18>: cmpl $0x6,0x804c3cc //这个地址存的是$6才可进入关卡
0x08049354 <+25>: jne 0x80493c8
0x08049356 <+27>: lea 0x2c(%esp),%eax
0x0804935a <+31>: mov %eax,0x10(%esp)
0x0804935e <+35>: lea 0x28(%esp),%eax
0x08049362 <+39>: mov %eax,0xc(%esp)
0x08049366 <+43>: lea 0x24(%esp),%eax
0x0804936a <+47>: mov %eax,0x8(%esp)
0x0804936e <+51>: movl $0x804a469,0x4(%esp) //“%d %d %s”
0x08049376 <+59>: movl $0x804c4d0,(%esp) //传参
0x0804937d <+66>: call 0x8048870 <__isoc99_sscanf@plt>
0x08049382 <+71>: cmp $0x3,%eax
0x08049385 <+74>: jne 0x80493bc
0x08049387 <+76>: movl $0x804a472,0x4(%esp) //%s要为“DrEvil”
0x0804938f <+84>: lea 0x2c(%esp),%eax
0x08049393 <+88>: mov %eax,(%esp) //将输入的字符串传入
0x08049396 <+91>: call 0x80490a4
0x0804939b <+96>: test %eax,%eax //字符串相同返回值为0
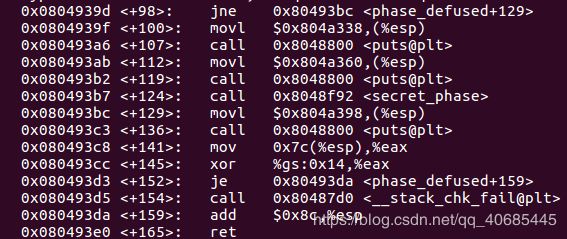
0x0804939d <+98>: jne 0x80493bc
0x0804939f <+100>: movl $0x804a338,(%esp) //“curses,you’ve found the secret phase”
0x080493a6 <+107>: call 0x8048800
0x080493ab <+112>: movl $0x804a360,(%esp) //”But finding it and solving it are quite different...”
0x080493b2 <+119>: call 0x8048800
0x080493b7 <+124>: call 0x8048f92
0x080493bc <+129>: movl $0x804a398,(%esp) //” "Congratulations! You've defused the bomb!”
0x080493c3 <+136>: call 0x8048800
0x080493c8 <+141>: mov 0x7c(%esp),%eax
0x080493cc <+145>: xor %gs:0x14,%eax //比较这int与eax是否相等,相等则正常退出,否则bomb
0x080493d3 <+152>: je 0x80493da
0x080493d5 <+154>: call 0x80487d0 <__stack_chk_fail@plt>
0x080493da <+159>: add $0x8c,%esp
0x080493e0 <+165>: ret
Dump of assembler code for function secret_phase:
0x08048f92 <+0>: push %ebx
0x08048f93 <+1>: sub $0x18,%esp
0x08048f96 <+4>: call 0x80491dd
0x08048f9b <+9>: movl $0xa,0x8(%esp) //传参10
0x08048fa3 <+17>: movl $0x0,0x4(%esp) //传参0
0x08048fab <+25>: mov %eax,(%esp) //传参输入的内容
0x08048fae <+28>: call 0x80488e0
0x08048fb3 <+33>: mov %eax,%ebx
0x08048fb5 <+35>: lea -0x1(%eax),%eax
0x08048fb8 <+38>: cmp $0x3e8,%eax //eax-1<=1000
0x08048fbd <+43>: jbe 0x8048fc4
0x08048fbf <+45>: call 0x80491b6
0x08048fc4 <+50>: mov %ebx,0x4(%esp)
0x08048fc8 <+54>: movl $0x804c088,(%esp) //该地址的值为36
0x08048fcf <+61>: call 0x8048f41
0x08048fd4 <+66>: cmp $0x4,%eax //返回值要等于4
0x08048fd7 <+69>: je 0x8048fde
0x08048fd9 <+71>: call 0x80491b6
0x08048fde <+76>: movl $0x804a298,(%esp) //”Wow! You've defused the secret stage!"
0x08048fe5 <+83>: call 0x8048800
0x08048fea <+88>: call 0x804933b
0x08048fef <+93>: add $0x18,%esp
0x08048ff2 <+96>: pop %ebx
0x08048ff3 <+97>: ret
Dump of assembler code for function fun7:
0x08048f41 <+0>: push %ebx
0x08048f42 <+1>: sub $0x18,%esp
0x08048f45 <+4>: mov 0x20(%esp),%edx //该地址值为36
0x08048f49 <+8>: mov 0x24(%esp),%ecx //另一个参数
0x08048f4d <+12>: test %edx,%edx
0x08048f4f <+14>: je 0x8048f88
0x08048f51 <+16>: mov (%edx),%ebx //ebx=36
0x08048f53 <+18>: cmp %ecx,%ebx //36<=另一个参数
0x08048f55 <+20>: jle 0x8048f6a
0x08048f57 <+22>: mov %ecx,0x4(%esp)
0x08048f5b <+26>: mov 0x4(%edx),%eax //地址加1*4
0x08048f5e <+29>: mov %eax,(%esp)
0x08048f61 <+32>: call 0x8048f41
0x08048f66 <+37>: add %eax,%eax //eax=2eax
0x08048f68 <+39>: jmp 0x8048f8d
0x08048f6a <+41>: mov $0x0,%eax
0x08048f6f <+46>: cmp %ecx,%ebx //36等于另一个参数 跳出,返回值为0
0x08048f71 <+48>: je 0x8048f8d
0x08048f73 <+50>: mov %ecx,0x4(%esp) //36>另一个参数
0x08048f77 <+54>: mov 0x8(%edx),%eax //地址加2*4
0x08048f7a <+57>: mov %eax,(%esp)
0x08048f7d <+60>: call 0x8048f41
0x08048f82 <+65>: lea 0x1(%eax,%eax,1),%eax //eax=2eax+1
0x08048f86 <+69>: jmp 0x8048f8d
0x08048f88 <+71>: mov $0xffffffff,%eax //为空 相等返回-1
0x08048f8d <+76>: add $0x18,%esp
0x08048f90 <+79>: pop %ebx
0x08048f91 <+80>: ret
小于 乘2加1 地址加8
大于 乘2 地址加4
0<=1<=2<=4
小于 大于 大于
0x804c088地址 +4 取值
0x804c094地址 +4 取值
0x804c0c4地址 +8 取值
0x80c410c地址 该值为7