实验anyconnect 4.2;ASA55059.2(4)
ASA版本如下:
System p_w_picpath file is "disk0:/asa924-k8.bin"
实验需求:
1.远程PC使用SSL×××拨入访问内网server
2.使用用户A和用户B拨入后的IP不在同一网段。
配置步骤如下:
第一步:配置×××书
在这里我们生成一个名为ssl***keypair的自签名证书,并将这个自答名证书应用在“outside”接口上面。默认情况下,我们的安全设备每次重新启动以后,都全重新生成我们的证书,这个证书我们也可以从厂商购买自己的证书,这个证书即使我们的网络设备重启了它仍然存在。//生成一个RSA密钥的证书,该名称是是唯一的。
CISCOASA(config)# crypto key generatersa label ssl***keypair
INFO: The namefor the keys will be: ssl***keypair
Keypairgeneration process begin. Please wait...
//建立一个自我信任点颁发的证书
CISCOASA(config)#crypto catrustpoint localtrust
CISCOASA(config-ca-trustpoint)# enrollment self
CISCOASA(config-ca-trustpoint)#fqdn ssl***.luxshare.com
CISCOASA(config-ca-trustpoint)#subject-nameCN=ssl***.luxshare.com
CISCOASA(config-ca-trustpoint)#keypair ssl***keypair
CISCOASA(config-ca-trustpoint)#crypto caenroll localtrust noconfirm
% Thefully-qualified domain name in the certificate will be: ssl***.cisco.com
CISCOASA(config)#ssltrust-point localtrust outside
第二步:将SSL ×××客户端映象上传到ASA
用户可以从思科的网站(cisco.com)获得客户端映象。在选择要下载哪个映象给TFTP服务器时,记住你需要为用户所使用的每种操作系统下载单独的映象。在选择并下载客户端软件后,就可以将其TFTP到ASA。
CISCOASA(config)# copy tftp://192.168. 1.50/anyconnect-win-4.2.00096-k9.pkg flash:/
我这里用的anconnect是-4.2.00096版本。
在将文件上传到ASA之后,配置一下这个文件,使其可用作Web ×××会话.注意,如果你有多个客户端,就应当配置最常用的客户,使其拥有最高的优先权。在本文中,我们将仅使用一个客户端并为其设置优先权为1:当mac和linux访问时使用2 3
CISCOASA(config)# web***
CISCOASA(config-web***)#anyconnect p_w_picpathdisk0:/anyconnect-win-4.2.00096-k9.pkg 1
INFO: Imagedoes not contain head-end configuration.
CISCOASA(config-web***)#anyconnect p_w_picpathdisk0:/anyconnect-macosx-i386-4.2.00096-k9.pkg 2
CISCOASA(config-web***)#anyconnect p_w_picpathdisk0:/anyconnect-linux-64-4.2.00096-k9.pkg 3
第三步:启用SSL ×××访问
如何不启用的话,那么我们输入网址将打不开该SSL ×××的页面。
CISCOASA(config-web***)# enable outside
CISCOASA(config-web***)#anyconnect enable
CISCOASA(config-web***)#exit
第四步:建立SSL ×××拨号地址池
远程访问客户端需要在登录期间分配一个IP地址,所以我们还需要为这些客户端建立一个DHCP地址池,不过如果你有DHCP服务器,还可以使用DHCP服务器。
CISCOASA(config)# ip local pool SSLClientPool 192.168.254.10-192.168.254.100 mask 255.255.255.0
第五步:创建组策略
组策略用于指定应用于所连接客户端的参数。在本文中,我们将创建一个称之为SSLCLientPolicy的组策略。
CISCOASA(config)# group-policy SSLClientPolicy internal //打完此命令才有下面的属性设置命令
CISCOASA(config)#group-policy SSLClientPolicy attributes
CISCOASA(config-group-policy)#dns-servervalue 192.168.1.20 //内网DNSServer IP
CISCOASA(config-group-policy)# ***-tunnel-protocol ssl-client
CISCOASA(config-group-policy)#group-lock value SSLClientProfile
//组锁定tunel-group SSLClientProfile,创建后才能敲。选配;
CISCOASA(config-group-policy)#default-domainvalue luxshare.com
CISCOASA(config-group-policy)#split-dns value luxshare.com
//启用了spilt-dns后 只有luxshare.com的域名送往内部dns服务器解析。选配;
CISCOASA(config-group-policy)# address-pools valueSSLClientPool
CISCOASA(config-group-policy)# exit
第六步:配置访问列表旁路
通过使用sysoptconnect命令,我们告诉ASA准许SSL/IPsec客户端绕过接口的访问列表
CISCOASA(config)# sysopt connection permit-***
第七步:创建连接配置文件和隧道组
在远程访问客户端连接到ASA时,也就连接到了connection profile连接配置文件,也称为隧道组。我们将用这个隧道组来定义其使用的特定连接参数。在本文中,我们将配置这些远程访问客户端使用Cisco SSL ×××客户端,不过,你还可以配置隧道组使用IPsec、L2L等。
首先,创建隧道组SSL 客户端:CISCOASA(config)# tunnel-group SSLClientProfile type remote-access
下一步就是给这个SSL×××隧道分配特定的属性CISCOASA(config)# tunnel-groupSSLClientProfile general-attributes
CISCOASA(config-tunnel-general)#default-group-policy SSLCLientPolicy
CISCOASA(config-tunnel-general)# tunnel-groupSSLClientProfile web***-attributes
CISCOASA(config-tunnel-web***)# group-alias SSL×××Client enable
CISCOASA(config-tunnel-web***)# exit
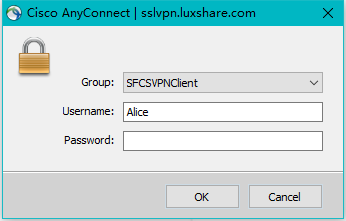
在上在group-alias后面的SSL×××Client这个就是我们在登陆页面提示进行登录时看见的组。(如下图:)
第八步:将隧道组列表在web***中开启
开启之后,在我们登录的时候才会有“GROUP”,如果没有开启的话,在上图就没有“GROUP”这个列表。
CISCOASA(config)# web***
CISCOASA(config-web***)#tunnel-group-list enable
CISCOASA(config-web***)# exit
第九步:配置NAT免除
现在,我们需要告诉ASA不要对远程访问客户端和要访问的内部网络之间的通信进行网络地址转换
(NAT)。首先,我们要创建定义通信的object ,然后,我们将这两个object互访时自己转换成自己:
ciscoasa(config)# object network SSL×××-Pool
ciscoasa(config-network-object)# subnet 192.168.254.0 255.255.255.0
ciscoasa(config)# object network Internal
ciscoasa(config-network-object)# subnet 192.168.1.0 255.255.255.0
ciscoasa(config)# nat (inside,any) source static Internal Internal destination static SSL×××-Pool SSL×××-Pool no-proxy-arp route-lookup
第十步:配置用户账户
现在我们已经为配置用户账户做好了准备。在此,我们要创建一个用户并且将此用户指派给我们的SSLClientPolicy中:
CISCOASA(config)# username tom password 123456
CISCOASA(config)# username tom attributes
CISCOASA(config-username)#service-typeremote-access
CISCOASA(config-username)# ***-group-policy SSLClientPolicy
CISCOASA(config-username)# exit
第十一步:保存CISCOASA(config)#writememory
隧道分离技术:
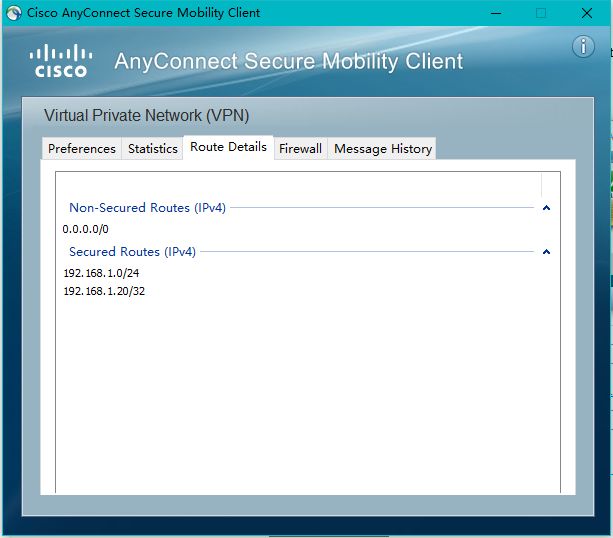
从这里我们可以看见,我们所有的数据都走向我们SSL ×××服务端去了。所以我们现在就只能访问SSL ×××服务端的网络了。但是我自己这边的网络以及互联网都不能访问,这样我们就非常不方便。那么我们如何来解决这个问题呢?我们在这里就必须使用隧道分离技术了。那么下面我们来看看隧道分离如何配置呢?
CISCOASA(config)# access-list ***client_splitTunnelAcl standard permit192.168.1.0 255.255.255.0
CISCOASA(config)# group-policy SSLClientPolicy attributes
CISCOASA(config-group-policy)#split-tunnel-policytunnelspecified
CISCOASA(config-group-policy)#split-tunnel-network-list value ***client_splitTunnelAcl
CISCOASA(config-group-policy)#exit
如法炮制创建组另一个组:
CISCOASA(config)# ip local pool SFCSClientPool 192.168.253.10-192.168.253.100 mask 255.255.255.0
CISCOASA(config)# group-policy SFCSClientPolicy internal //打完此命令才有下面的属性设置命令
CISCOASA(config)#group-policy SFCSClientPolicy attributes
CISCOASA(config-group-policy)#dns-server value 192.168.1.20 //内网DNSServer IP
CISCOASA(config-group-policy)# ***-tunnel-protocol ssl-client
CISCOASA(config-group-policy)#group-lock value SFCSClientProfile
//组锁定tunel-group SSLClientProfile,创建后才能敲。选配;
CISCOASA(config-group-policy)#default-domain value luxshare.com
CISCOASA(config-group-policy)#split-dns value luxshare.com
//启用了spilt-dns后 只有luxshare.com的域名送往内部dns服务器解析。选配;
CISCOASA(config-group-policy)# address-pools value SFCSClientPool
CISCOASA(config-group-policy)# exit
首先,创建隧道组SSL 客户端:CISCOASA(config)# tunnel-group SFCSClientProfile type remote-access
下一步就是给这个SSL×××隧道分配特定的属性CISCOASA(config)# tunnel-group SFCSClientProfile general-attributes
CISCOASA(config-tunnel-general)#default-group-policy SFCSClientPolicy
CISCOASA(config-tunnel-general)# tunnel-group SFCSClientProfile web***-attributes
CISCOASA(config-tunnel-web***)# group-alias SFCS×××Client enable
CISCOASA(config-tunnel-web***)# exit
ciscoasa(config)# object network SFCS×××-Pool
ciscoasa(config-network-object)# subnet 192.168.253.0 255.255.255.0
ciscoasa(config)# nat (inside,any) source static Internal Internal destination static SFCS×××-Pool SFCS×××-Pool no-proxy-arp route-lookup
CISCOASA(config)# username Alice password 123456
CISCOASA(config)# username Alice attributes
CISCOASA(config-username)#service-type remote-access
CISCOASA(config-username)# ***-group-policy SFCSClientPolicy
CISCOASA(config-username)# exit
CISCOASA(config)# group-policy SFCSClientPolicy attributes
CISCOASA(config-group-policy)#split-tunnel-policy tunnelspecified
CISCOASA(config-group-policy)#split-tunnel-network-list value ***client_splitTunnelAcl
CISCOASA(config-group-policy)#exit
ciscoasa(config)# show run
: Saved
:
: Serial Number: JMX150240F0
: Hardware: ASA5505, 512 MB RAM, CPU Geode 500 MHz
:
ASA Version 9.2(4)
!
hostname ciscoasa
enable password 8Ry2YjIyt7RRXU24 encrypted
names
ip local pool SSLClientPool 192.168.254.10-192.168.254.100 mask 255.255.255.0
ip local pool SFCSClientPool 192.168.253.10-192.168.253.100 mask 255.255.255.0
!
interface Ethernet0/0
switchport access vlan 2
!
interface Ethernet0/1
!
interface Ethernet0/2
!
interface Ethernet0/3
!
interface Ethernet0/4
!
interface Ethernet0/5
!
interface Ethernet0/6
!
interface Ethernet0/7
!
interface Vlan1
nameif inside
security-level 100
ip address 192.168.1.1 255.255.255.0
!
interface Vlan2
nameif outside
security-level 0
ip address 210.100.1.1 255.255.255.0
!
ftp mode passive
object network obj_any
subnet 0.0.0.0 0.0.0.0
object network SSL×××-Pool
subnet 192.168.254.0 255.255.255.0
object network Internal
subnet 192.168.1.0 255.255.255.0
object network SFCS×××-Pool
subnet 192.168.253.0 255.255.255.0
access-list ***client_splitTunnelAcl standard permit 192.168.1.0 255.255.255.0
pager lines 24
logging asdm informational
mtu outside 1500
mtu inside 1500
no failover
icmp unreachable rate-limit 1 burst-size 1
no asdm history enable
arp timeout 14400
no arp permit-nonconnected
nat (inside,any) source static Internal Internal destination static SSL×××-Pool SSL×××-Pool no-proxy-arp route-lookup
nat (inside,any) source static Internal Internal destination static SFCS×××-Pool SFCS×××-Pool no-proxy-arp route-lookup
!
object network obj_any
nat (inside,outside) dynamic interface
timeout xlate 3:00:00
timeout pat-xlate 0:00:30
timeout conn 1:00:00 half-closed 0:10:00 udp 0:02:00 icmp 0:00:02
timeout sunrpc 0:10:00 h323 0:05:00 h225 1:00:00 mgcp 0:05:00 mgcp-pat 0:05:00
timeout sip 0:30:00 sip_media 0:02:00 sip-invite 0:03:00 sip-disconnect 0:02:00
timeout sip-provisional-media 0:02:00 uauth 0:05:00 absolute
timeout tcp-proxy-reassembly 0:01:00
timeout floating-conn 0:00:00
dynamic-access-policy-record DfltAccessPolicy
user-identity default-domain LOCAL
http server enable
http 192.168.1.0 255.255.255.0 inside
no snmp-server location
no snmp-server contact
crypto ipsec security-association pmtu-aging infinite
crypto ca trustpoint localtrust
enrollment self
fqdn ssl***.luxshare.com
subject-name CN=ssl***.luxshare.com
keypair ssl***keypair
crl configure
crypto ca trustpool policy
crypto ca certificate chain localtrust
certificate 27669d57
308201fb 30820164 a0030201 02020427 669d5730 0d06092a 864886f7 0d010105
05003042 311c301a 06035504 03131373 736c7670 6e2e6c75 78736861 72652e63
6f6d3122 30200609 2a864886 f70d0109 02161373 736c7670 6e2e6c75 78736861
72652e63 6f6d301e 170d3136 30373331 30333338 35305a17 0d323630 37323930
33333835 305a3042 311c301a 06035504 03131373 736c7670 6e2e6c75 78736861
72652e63 6f6d3122 30200609 2a864886 f70d0109 02161373 736c7670 6e2e6c75
78736861 72652e63 6f6d3081 9f300d06 092a8648 86f70d01 01010500 03818d00
30818902 818100a8 608f2a05 043616c4 4fde0f8c 57894bd2 5a511ff3 b92277bd
999f43e3 3cf2a8a1 7ff3e711 15ddb56d d470d076 ac2ae29b c5721fd8 dde60a20
6d77a182 26371456 025a4194 3e9451d3 5a83e996 751ee819 f702f9ae ca4b5b9c
3af36d09 51f46799 133667da 20ee235c 97cf3efd 4b9e7c75 822caf7a 16111d36
297916bc 85fe1302 03010001 300d0609 2a864886 f70d0101 05050003 81810079
1b92650e aba652f1 cdddfbe5 0a34c075 1ff2a800 d77c7637 dbc854a9 e4fb388d
fef10435 fbc2a405 58a0e810 bcbb0bdc ea13b71f 7477afd8 ec3db084 cc06a7e9
2e6c0085 2a46f680 48f93004 6bdfbe1b 1ec29d89 d2865d9f 2bf59166 ceeba146
a4db435a 43ec3ce0 e2d43dda 45d458ca 1840f294 a39e23ba c436ec84 0223b4
quit
telnet timeout 5
no ssh stricthostkeycheck
ssh timeout 5
ssh key-exchange group dh-group1-sha1
console timeout 0
dhcpd auto_config outside
!
dhcpd address 192.168.1.5-192.168.1.254 inside
dhcpd enable inside
!
threat-detection basic-threat
threat-detection statistics access-list
no threat-detection statistics tcp-intercept
ssl trust-point localtrust outside
web***
enable outside
anyconnect-essentials
anyconnect p_w_picpath disk0:/anyconnect-win-4.2.00096-k9.pkg 1
anyconnect p_w_picpath disk0:/anyconnect-macosx-i386-4.2.00096-k9.pkg 2
anyconnect p_w_picpath disk0:/anyconnect-linux-64-4.2.00096-k9.pkg 3
anyconnect enable
tunnel-group-list enable
group-policy SSLClientPolicy internal
group-policy SSLClientPolicy attributes
dns-server value 192.168.1.20
***-tunnel-protocol ssl-client
group-lock value SSLClientProfile
split-tunnel-policy tunnelspecified
split-tunnel-network-list value ***client_splitTunnelAcl
default-domain value luxshare.com
split-dns value luxshare.com
address-pools value SSLClientPool
group-policy SFCSClientPolicy internal
group-policy SFCSClientPolicy attributes
dns-server value 192.168.1.20
***-tunnel-protocol ssl-client
group-lock value SFCSClientProfile
split-tunnel-policy tunnelspecified
split-tunnel-network-list value ***client_splitTunnelAcl
default-domain value luxshare.com
split-dns value luxshare.com
address-pools value SFCSClientPool
username Tom password Gb9qBdJ.1ZiNu0PP encrypted
username Tom attributes
***-group-policy SSLClientPolicy
service-type remote-access
username Alice password AyuXtm3EUBFJa8Bf encrypted
username Alice attributes
***-group-policy SFCSClientPolicy
service-type remote-access
tunnel-group SSLClientProfile type remote-access
tunnel-group SSLClientProfile general-attributes
default-group-policy SSLClientPolicy
tunnel-group SSLClientProfile web***-attributes
group-alias SSL×××Client enable
tunnel-group SFCSClientProfile type remote-access
tunnel-group SFCSClientProfile general-attributes
default-group-policy SFCSClientPolicy
tunnel-group SFCSClientProfile web***-attributes
group-alias SFCS×××Client enable
!
class-map inspection_default
match default-inspection-traffic
!
!
policy-map type inspect dns preset_dns_map
parameters
message-length maximum client auto
message-length maximum 512
policy-map global_policy
class inspection_default
inspect dns preset_dns_map
inspect ftp
inspect h323 h225
inspect h323 ras
inspect rsh
inspect rtsp
inspect esmtp
inspect sqlnet
inspect skinny
inspect sunrpc
inspect xdmcp
inspect sip
inspect netbios
inspect tftp
inspect ip-options
!
service-policy global_policy global
prompt hostname context
Cryptochecksum:c01161c90e01103ffcd05efce0be2346
: end