创建基于ovs的vxlan隧道
1.1 安装openvswitch
$ sudo apt install openvswitch-switch
1.2 查看进程
$ ps -ef | grep ovs
1.3 查看ovs的版本
$ ovs-appctl --version
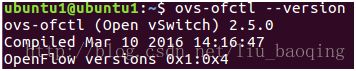
1.4 查看ovs支持的OpenFlow协议的版本
$ ovs-ofctl --version
2.在两台虚拟机上配置网桥
2.1 在ubuntu1上添加名为br0和br1的两个网桥:
$ sudo ovs-vsctl add-br br0
$ sudo ovs-vsctl add-br br1
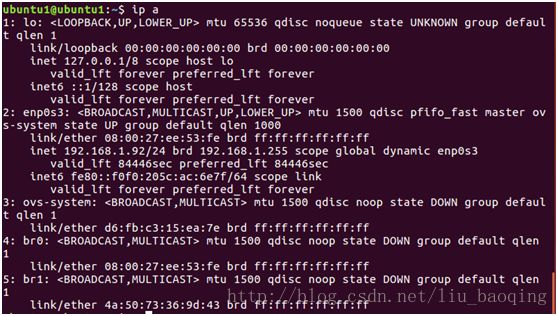
查看网卡:$ ip a
在br0上添加一个端口,将enp0s3挂载到br0上:
$ sudo ovs-vsctl add-port br0 enp0s3
这样做的目的是方便我们在虚拟网桥上添加多个端口供我们使用,不必受限于enp0s3的有限端口。
此时我们将原先enp0s3分配的ip清除并指定给br0,让虚拟机网络能通过br0继续工作:
$ sudo ifconfig enp0s3 0 up && sudo ifconfig br0 192.168.1.92/24 up
根据实际情况配置一下br0的网关:
$ sudo route add default gw 192.168.1.1 br0
给br1网桥分配一个ip:
$ sudo ifconfig br1 10.20.30.1/24 up
查看网卡:$ ip a

2.2 在ubuntu2上也添加名为br0和br1的两个网桥:
$ sudo ovs-vsctl add-br br0
$ sudo ovs-vsctl add-br br1
$ sudo ovs-vsctl add-port br0 enp0s3
$ sudo ifconfig enp0s3 0 up && sudo ifconfig br0 192.168.1.198/24 up
$ sudo route add default gw 192.168.1.1 br0
$ sudo ifconfig br1 10.20.31.2/24 up
3.在两台虚拟机之间搭建vxlan隧道
3.1在搭建隧道之前先看下ubuntu1上网络之间通信情况:
$ ping 192.168.1.198
PING 192.168.1.198 (192.168.1.198) 56(84) bytes of data.
64 bytes from 192.168.1.198: icmp_seq=1 ttl=64 time=1.71 ms
64 bytes from 192.168.1.198: icmp_seq=2 ttl=64 time=0.468 ms
64 bytes from 192.168.1.198: icmp_seq=3 ttl=64 time=0.548 ms
$ ping 10.20.31.2
PING 10.20.31.3 (10.20.30.2) 56(84) bytes of data.
From 10.20.30.2 icmp_seq=1 Destination Host Unreachable
说明ubuntu1的br1和ubuntu2的br1不能通信,现在创建隧道就是让其通信。
3.2在ubuntu1上设置VXLAN,远端ip设置为ubuntu2能对外通信的br0的ip:
$ sudo ovs-vsctl add-port br1 vx1 -- set interface vx1 type=vxlan option:remote_ip=192.168.1.198
$ sudo ovs-vsctl show
bd2e5468-4888-45bc-a60e-fc25418bb165
Bridge "br0"
Port "enp0s3"
Interface "enp0s3"
Port "br0"
Interface "br0"
type: internal
Bridge "br1"
Port "br1"
Interface "br1"
type: internal
Port "vx1"
Interface "vx1"
type: vxlan
options: {remote_ip="192.168.1.198"}
ovs_version: "2.5.0"
在ubuntu2上设置VXLAN,远端ip设置为ubuntu1能对外通信的br0的ip:
$ sudo ovs-vsctl add-port br1 vx1 -- set interface vx1 type=vxlan option:remote_ip=192.168.1.92
$ sudo ovs-vsctl show
3a9bc51a-be25-434c-9641-7016277d2d6e
Bridge "br1"
Port "br1"
Interface "br1"
type: internal
Port "vx1"
Interface "vx1"
type: vxlan
options: {remote_ip="192.168.1.92"}
Bridge "br0"
Port "br0"
Interface "br0"
type: internal
Port "enp0s3"
Interface "enp0s3"
ovs_version: "2.5.0"
3.3在ubuntu1上验证VXLAN隧道:ping 10.20.30.2
PING 10.20.30.2 (10.20.30.2) 56(84) bytes of data.
64 bytes from 10.20.30.2: icmp_seq=1 ttl=64 time=1.97 ms
64 bytes from 10.20.30.2: icmp_seq=2 ttl=64 time=0.491 ms
说明ovs建立的vxlan隧道成功了。
$ sudo tcpdump -i br0 -ennvv udp(vxlan是通过udp封装的,所以过滤udp包)
192.168.1.92.60937 > 192.168.1.198.4789: [no cksum] VXLAN, flags [I] (0x08), vni 0
aa:70:47:91:b9:41 > a6:56:46:f8:c6:4e, ethertype IPv4 (0x0800), length 98: (tos 0x0, ttl 64, id 62137, offset 0, flags [DF], proto ICMP (1), length 84)
10.20.30.1 > 10.20.30.2: ICMP echo request, id 2820, seq 3663, length 64
17:58:28.803580 08:00:27:ee:53:fe > 08:00:27:66:a5:43, ethertype IPv4 (0x0800), length 148: (tos 0x0, ttl 64, id 38326, offset 0, flags [DF], proto UDP (17), length 134)
192.168.1.198.53730 > 192.168.1.92.4789: [no cksum] VXLAN, flags [I] (0x08), vni 0
a6:56:46:f8:c6:4e > aa:70:47:91:b9:41, ethertype IPv4 (0x0800), length 98: (tos 0x0, ttl 64, id 59840, offset 0, flags [none], proto ICMP (1), length 84)
10.20.30.2 > 10.20.30.1: ICMP echo reply, id 2820, seq 3663, length 64
17:58:28.849481 fc:aa:14:44:26:ea > 01:00:5e:00:00:fb, ethertype IPv4 (0x0800), length 107: (tos 0x0, ttl 255, id 57863, offset 0, flags [DF], proto UDP (17), length 93)
$ sudo tcpdump -i br1 -ennvv icmp(出了隧道就是icmp包了,所以过滤icmp)
10.20.30.1 > 10.20.30.2: ICMP echo request, id 2820, seq 3695, length 64
17:59:00.803537 a6:56:46:f8:c6:4e > aa:70:47:91:b9:41, ethertype IPv4 (0x0800), length 98: (tos 0x0, ttl 64, id 63690, offset 0, flags [none], proto ICMP (1), length 84)
10.20.30.2 > 10.20.30.1: ICMP echo reply, id 2820, seq 3695, length 64
17:59:01.802820 aa:70:47:91:b9:41 > a6:56:46:f8:c6:4e, ethertype IPv4 (0x0800), length 98: (tos 0x0, ttl 64, id 654, offset 0, flags [DF], proto ICMP (1), length 84)
