阿里云ECS部署L2TP/IPSEC,访问服务器内网
阿里云ECS部署L2TP/IPSEC,访问服务器内网
- 准备工作
- 自建NAT网关
- 添加路由
- 地址转换
- 部署xd
- 安装服务
- 修改配置
- 将v和p谐n网段添加到白名单
- win10连接v和p谐n
- 完成
- 参考链接
准备工作
三台阿里云ECS服务器,操作系统CentOS7
| 服务器名称 | 内网ip | 公网 |
|---|---|---|
| 服务器A | 172.26.245.47 | 有 |
| 服务器B | 172.26.245.48 | 无 |
| 服务器C | 172.26.245.49 | 无 |
服务器A有弹性公网ip可以上网,在这个服务器上部署L2TP/IPSEC服务,服务器B和服务器C没有公网ip,需要通过服务器A上网
自建NAT网关
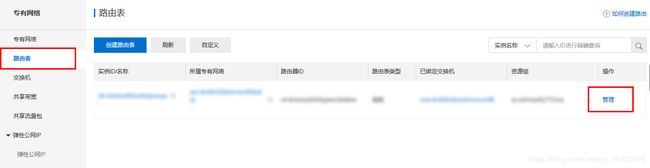
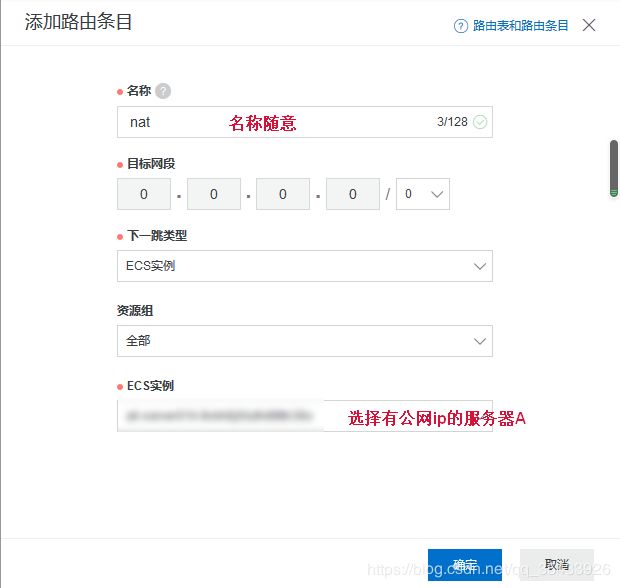
添加路由
按一下顺序打开路由表页面
阿里云控制台 - 专有网络管理控制台 - 路由表
地址转换
登录服务器A,依次执行以下命令
- 阿里云ECS的防火墙默认没有开启,先开启防火墙
systemctl enable firewalldsystemctl start firewalld
- 地址转换
firewall-cmd --add-masquerade --permanentfirewall-cmd --reload
- ip转发
cat "net.ipv4.ip_forward=1" >> /etc/sysctl.confsysctl -p
- 内网添加白名单(三台服务器都需要添加)
firewall-cmd --permanent --add-rich-rule="rule family='ipv4' source address='172.26.245.1/24' port protocol='tcp' port='0-65535' accept"firewall-cmd --reload
部署xd
以下在服务器A操作
安装服务
- 安装EPEL源(CentOS7官方源中已经去掉了xd):
yum install -y epel-release - 安装xd和libreswan(openswan已经停止维护):
yum install -y xd libreswan lsof
修改配置
- xd配置文件
vim /etc/xd/xd.conf,内容如下
# ip range是分配给v和p谐n客户端的ip范围
# local ip是本机内网ip
[lns default]
ip range = 172.26.243.100-172.26.243.110 # 分配给v和p谐n客户端的ip范围
local ip = 172.26.245.47 # 本机内网ip
require chap = yes
refuse pap = yes
require authentication = yes
name = LinuxV河P蟹Nserver
ppp debug = yes
pppoptfile = /etc/ppp/options.xd
length bit = yes
- pppoptfile文件
vim /etc/ppp/options.xd,内容如下
ipcp-accept-local
ipcp-accept-remote
ms-dns 8.8.8.8
ms-dns 114.114.114.114
name xd
auth
idle 1800
mtu 1410
mru 1410
nodefaultroute
debug
proxyarp
connect-delay 5000
refuse-pap
refuse-mschap
require-mschap-v2
persist
logfile /var/log/xd.log
- ipsec配置文件
vim /etc/ipsec.conf,内容如下
# config setup下的protostack=netkey和dumpdir=/var/run/pluto/为新增项
# 其他保持默认即可
# 缩进使用TAB
config setup
plutodebug=none
protostack=netkey # 此项新增
dumpdir=/var/run/pluto/ # 此项新增
virtual_private=%v4:10.0.0.0/8,%v4:192.168.0.0/16,%v4:172.16.0.0/12,%v4:25.0.0.0/8,%v4:100.64.0.0/10,%v6:fd00::/8,%v6:fe80::/10
include /etc/ipsec.d/*.conf
- 新建
/etc/ipsec.d/-ipsec.conf
内容如下
# left=172.26.245.47是本机内网ip
# 缩进使用TAB
conn L2TP-PSK-NAT
rightsubnet=0.0.0.0/0
dpddelay=10
dpdtimeout=20
dpdaction=clear
forceencaps=yes
also=L2TP-PSK-noNAT
conn L2TP-PSK-noNAT
authby=secret
pfs=no
auto=add
keyingtries=3
rekey=no
ikelifetime=8h
keylife=1h
type=transport
left=172.26.245.47 # 本机内网ip
leftprotoport=17/1701
right=%any
rightprotoport=17/%any
- 设置用户名密码
vim /etc/ppp/chap-secrets,追加用户名密码
# 格式为:用户名 类型 密码 允许访问的ip
v和p谐nuser * v和p谐npassword *
- 设置预共享密钥PSK
vim /etc/ipsec.d/default.secrets,内容如下
# 将MyPSK替换为自己的秘钥
: PSK "MyPSK"
- 防火墙配置
firewall-cmd --permanent --add-service=ipsec # 放行ipsec服务,安装时会自定生成此服务
firewall-cmd --permanent --add-port=1701/udp # x的端口,默认1701
firewall-cmd --permanent --add-port=4500/udp # ipsec的端口
firewall-cmd --permanent --add-port=500/udp # ipsec的端口
firewall-cmd --permanent --add-masquerade # 启用NAT转发功能,自建NAT网关时已经配置过
firewall-cmd --reload # 重载配置
- 修改内核参数
vim /etc/sysctl.conf,追加以下内容
net.ipv4.ip_forward = 1 # ip转发,自建NAT网关时已经配置过
net.ipv4.conf.all.accept_redirects = 0
net.ipv4.conf.all.rp_filter = 0
net.ipv4.conf.all.send_redirects = 0
net.ipv4.conf.default.accept_redirects = 0
net.ipv4.conf.default.rp_filter = 0
net.ipv4.conf.default.send_redirects = 0
net.ipv4.conf.eth0.accept_redirects = 0
net.ipv4.conf.eth0.rp_filter = 0
net.ipv4.conf.eth0.send_redirects = 0
net.ipv4.conf.lo.accept_redirects = 0
net.ipv4.conf.lo.rp_filter = 0
net.ipv4.conf.lo.send_redirects = 0
- 启动ipsec和xd
systemctl enable ipsec
systemctl start ipsec
systemctl enable xd
systemctl start xd
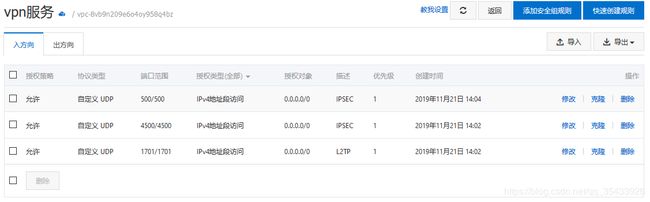
- 安全组规则
按照下图配置,并将服务器A添加到此安全组
将v和p谐n网段添加到白名单
分别在三台服务器执行以下命令
firewall-cmd --permanent --add-rich-rule="rule family='ipv4' source address='172.26.243.1/24' port protocol='tcp' port='0-65535' accept
firewall-cmd --reload
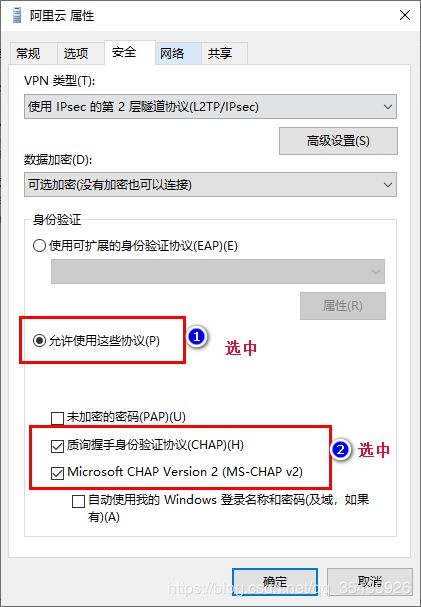
win10连接v和p谐n
- 打开网络和Internet设置,选择v和p谐n选项卡,点添加v和p谐n连接
- 适配器设置
- 开启服务
IPsec Policy Agent、Routing and Remote Access、Remote Access Connection Manager
启动以上三个服务,并改为自动启动
- 修改注册表
注册表路径:HKEY_LOCAL_MACHINE\System\CurrentControlSet\Services\Rasman\Parameters
新建ProhibitIpSec项,DWORD类型,值设置为1
新建AllowL2TPWeakCrypto项,DWORD类型,值设置为1
重启电脑
完成
连接v和p谐n,即可通过内网访问访问服务器A、B、C
参考链接
centos7 搭建xd 服务
win10系统 L2TP连接尝试失败
centos7 阿里云专有网络利用firewalld自建NAT网关