CentOS7下配置opessl
| server1 | 10.10.10.1 |
|---|---|
| server2 | 10.10.10.2 |
server1
[root@localhosot server1]# cd /etc/pki/CA
certs crl newcerts pricvate
[root@localhosot CA]# touch index.txt
[root@localhosot CA]#echo 01 > serial
[root@localhosot CA]#(umask 077; openssl genrsa -out /etc/pki/private/cakey.pem 2048)
Generating RSA private key ,2048 bit long modulus
.......+++
...................................+++
e is 65507 (0x10001)
[root@localhosot CA]#cd /etc/pki
[root@localhosot CA]#ls
CA ca-trust java nssdb rpm-gpg rsyrlog tls
[root@localhosot CA]#ls private/
cakey.pem
- 生成秘钥
#(umask 077; openssl genrsa -out /etc/pki/CA/private/cakey.pem 2048 )
#whatis req
[root@localhosot CA]#openssl req -new-x509 -key private/cakey.pem -days 365-out cacert.pem
You are about to be asked to enter information that will be incorporated
into your certificate request .
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter the field will be left blank
Country Name (2 letter code) [XX] :CM
State or Province Name (full name) [ ] :Shanxi
Ocality Name (eg, City) [Default City] : Taiyuan
Organization Name (eg, company) [Default Company Ltd] :gao
Organizational Unit Name (eg, section) [ ] :xiao
Common Name (eg, your name or your server's hostname)ca.gao.com
Email Address [email protected]
-
#opensll req -new -x509 -key /etc/pki/CA/private/cakey.pem -days 7300 -out /etc/pki/CA/cacert.pem
-new:生成新证书签署请求
-x509:专用于CA生成自签证书
-key:生成请求时用到的私钥文件
-days n:证书是有效期限
-out:证书的保存路径country name 国家名(必须使用两个字母大写表示) state or province name 省会名 locality name 城市名 organization name 公司名 organizantion unit name 部门名 common name 服务器名 email -
server2 10.10.10.2
-
使用证书的主句生成证书请求
[root@localhost~]#cd /etc/httpd
[root@localhost httpd]#mkdir ssl
[root@localhost ssl]#(umask 077; openssl genrsa -out httpd.key 2048)
Generating RSA private key, 2048 bit long modulus
.+++
.........................+++
e is 65537 (0x10001)
[root@localhost ssl]#ll
-rs-------. 1 root root 1679 3月 20 15:30 httpd.key
-把请求文件传输给CA
[root@localhost ssl]#openssl req -nre -key httpd.key -days 365 -out httpd.csr
[ root@localhost SSI] # openssl req - new - key httpd. key - days 7300 - out httpd. csr
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter the field will be left blank.
Country Name (2 letter code XX] : CM
State or Province Name (full name) Shanxi
ocality Name (eg, city) [Default City] : Taiyuan
Organization Name (eg, company) [Default Company Ltd] : gao
Organizational Unit Name (eg, section) i] : xlao
Common Name (eg, your name or your server' s hostname)www. gao. com
Email Address web@gao. com
Please enter the following ext ral attributes
to be sent with your certificate request
A challenge password[] : //可以为空格
An optional company name[] : //可以为空格
[ root@localhost SSI] # Is
httpd. csr httpd. key
- CA签署证书文件,并将证书发还给请求者
[ root@localhost ssl] #ls
httpd.csr httpd.key
[ root@localhost ssl] #scp httpd.csr [email protected]:/tmp
plese type 'yes' or 'no' :yes
[email protected]'s passwd:
- server1 10.10.10.1
[root@localhosot CA]#openssl ca -in /tmp/httpd.csr -out /tmp/httpd.crt -day 365
[root@localhosot CA]#ls /tmp
httpd.crt
httpd.csr
[root@localhosot CA]#scp /tmp/http.crt 10.10.10.2:/etc/httpd/ssl
- server2 10.10.10.2
[ root@localhost ssl] #ls
httpd.csr httpd.crt htttpd.key
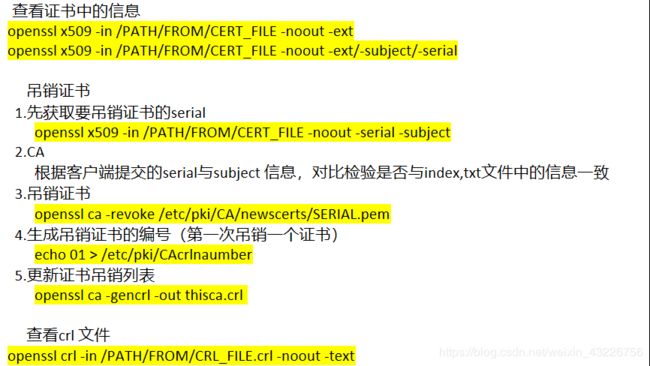
- 查看证书中的信息
openssl x509 -in /PATH/FROM/CERT_FILE -noout -ext
openssl x509 -in /PATH/FROM/CERT_FILE -noout -ext/-subject/-serial
- ** 吊销证书**
1.先获取要吊销证书的serial
openssl x509 -in /PATH/FROM/CERT_FILE -noout -serial -subject
2. CA
根据客户端提交的serial与subject 信息,对比检验是否与index,txt文件中的信息一致
3.吊销证书
openssl ca -revoke /etc/pki/CA/newscerts/SERIAL.pem
4.生成吊销证书的编号(第一次吊销一个证书)
echo 01 > /etc/pki/CAcrlnaumber
5.更新证书吊销列表
openssl ca -gencrl -out thisca.crl
- 查看crl文件